
Privacy shouldn't be a luxury
Maddie Stone, formally a Senior reverse engineer and tech lead on the Android security team, shockingly revealed a number of examples of how pre-installed apps on Android devices can undermine users privacy and security in her BlackHat USA talk in August 2019. The video of the talk only recently became available to the public in late December 2019.
Privacy International is currently running a campaign on pre-installed apps. If you believe that Google should stop allowing manufacturers and vendors from exploiting our devices, take a look at our petition.

Privacy shouldn't be a luxury
Maddie Stone, formally a Senior reverse engineer and tech lead on the Android security team, shockingly revealed a number of examples of how pre-installed apps on Android devices can undermine users privacy and security in her BlackHat USA talk in August 2019. The video of the talk only recently became available to the public in late December 2019.
The apps in question come preloaded on a device when it is purchased and often can't be removed. Stone reveals a litany of abuses carried out by smartphone manufacturers around the world, discovered following analysis by Google of devices to be distributed by their Android partner. Some of the findings demonstrate the contempt that some manufacturers hold their users privacy and security in.
Almost every manufacturer, including Google, disabled Google Play Protect without warning the user in order to bypass an issue in provisioning devices, a feature in newer versions of Android that is supposed to stop apps behaving maliciously and ultimately protect user privacy and security. Other manufacturers left code on their devices that would allow anyone to execute code remotely - allowing any malicious actor aware of this able to read the contents of your phone without ever needing to physically access to it and without the user knowing. Some manufacturers even modified the Android OS and API’s to allow them to get access to every URL that was accessed on the devices, for unclear purposes, a clear breach of users trust and privacy.
Stone even explains how, astonishingly, pre-installed apps are used via supply chain interference from malware developers to distribute their code. There is no need to trick a user into installing malware if it already comes packaged and pre-installed on a phone.
Most disappointing of all is the fact that this presentation shows Google has known about this problem for some time, brought to light by one of its own respected engineers, but has yet to act. We cannot find a single reason why Google continues to enable an ecosystem that exploits people who own Android phones when the dangers have been so clearly articulated.
Privacy International along with 50 other NGO’s around the world demand Google adopt better practices and stop manufacturers from exploiting people. We have reasonable asks and believe it is absolutely within Google's power to make these positive changes. If you believe that Google should curtail the exploitative practices of manufacturers, you should sign our petition.
The disabling of Google Play Protect makes it possible for known malicious apps to be installed and provides no warning to the user, it also means that pre-installed apps aren’t being held to the same standards as those which are available through Google Play, Google’s app store.
“Just about everyone was doing this, disabling [Google Play Protect] silently”, “[including] GMScore, Google had done [disabled Google Play Protect] as well”
Stone states “just about everyone was doing this, disabling it silently”, she continues “[including] GMScore, Google had done it as well” (GMScore is Googles Play Service itself). While there are detections in place for the disabling of Google Play Protect, they don’t apply in the same way to pre-installed apps due to the apps already privileged status and ability to communicate using API’s above those which would trip the detection.
Some manufacturers left the setting disabled, however Stone states “while most tried to re-enable this setting, it wasn’t all the time, and there was also sometimes a race condition which meant it couldn’t be re-enabled” making it impossible for Google Play Protect to be turned back on. The problem was resolved in the Android Open Source Project (AOSP) security update January 2019 (CVE-2018-9586) however this doesn’t acknowledge the long tail of Android devices, hundreds of thousands of devices will be in the wild with owners unaware that there device doesn’t have even the most basic malware protection enabled.
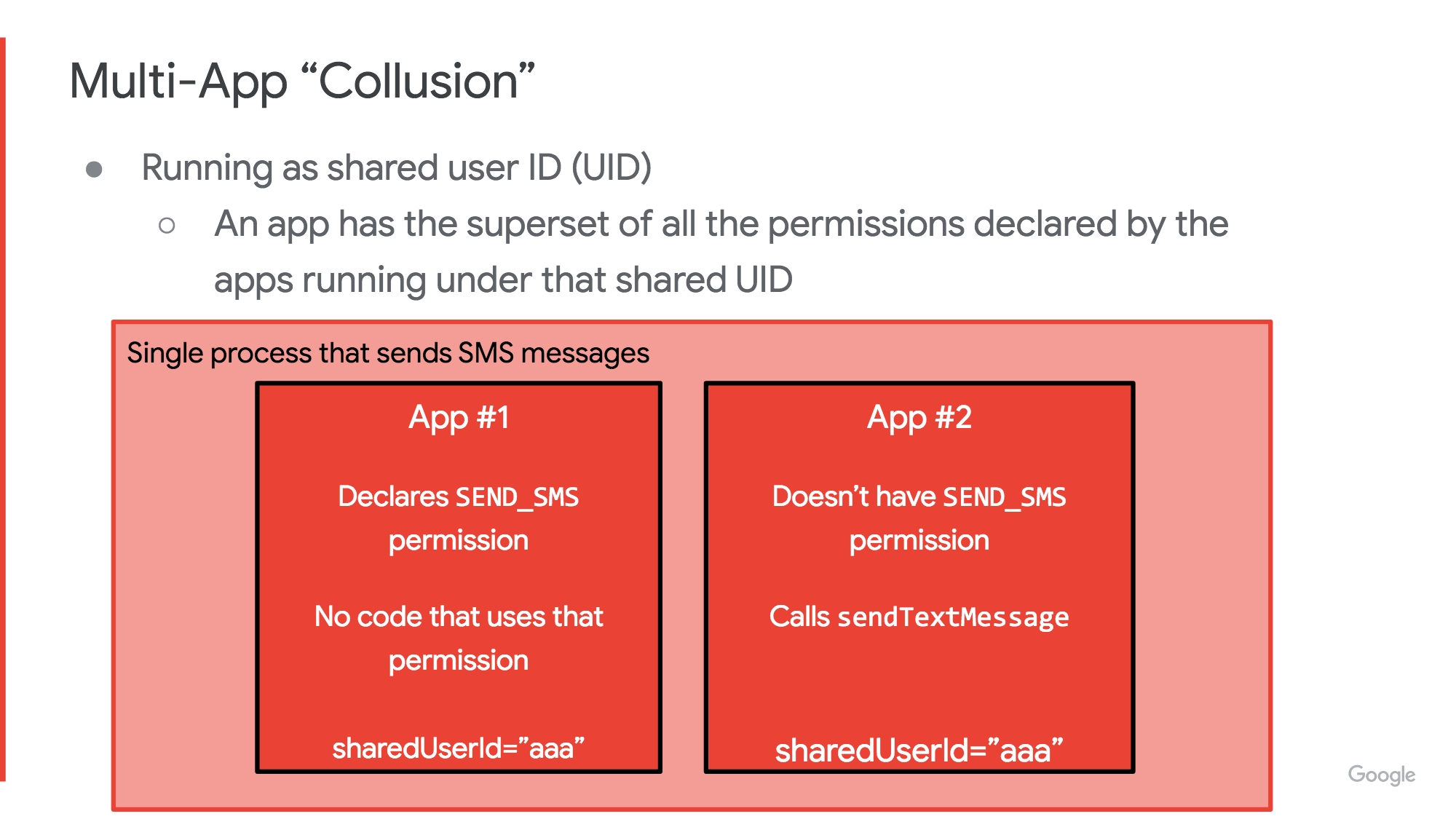
One of the issues highlighted by Stone is known as "multi-app" collusion, something which is relatively unique to pre-installed apps. This is when two apps work in concert to do things they can't do on their own.
Stone uses the example of two apps that have a shared context, one which has permissions to send text messages, but doesn’t contain any code to do so, and another which has the code to send text messages to a number (for example a premium rate one), but doesn’t have the permissions to send texts. Its the ability of these apps to use their shared context, and to work in harmony that allows them to exploit the user, in this case to perpetrate message fraud.
Stone examines the Remote Code Execution (RCE) through backdoors, these are bits of code that exist (or were destined to exist) on the device, both examples stem from oversight on the part of the integrator rather than deliberate malice, for example leaving diagnostic and remote management software on the device in a unprotected manner allowing for remote code execution.
URL Logging is where a manufacturer has modified the Android OS and API’s to allow them to get access to every URL that was accessed on the devices, a clear breach of users trust and privacy. This kind of behaviour, according to Stone's slides, would of been detected by Google Play Protect as Spyware. However as stated previously Google Play Protect could be disabled silently.
Stone discusses supply chain issues with regards to pre-installed apps. Unlike conventional malware where the developer has to convince the user to install their app (generally through deception, e.g Phishing or imitation attacks), a malware developer only needs to convince a the device manufacture to include their code, and it will be automatically shipped to thousands of users. As stated previously, it will also gain many of the benefits of being pre-installed, such as having privileged access and being included on a read-only file system making it impossible for a user to delete.
“Chamois” botnet, which masqueraded as a “mobile payment solution” or an “advertising SDK”
In her example Stone talks about “Chamois” botnet, which masqueraded as a “mobile payment solution” or an “advertising SDK” (see [Privacy International’s other work on SDKs](https://privacyinternational.org/appdata)). She goes on to discuss the diversity of Android OEM’s and how some are “longtail” selling devices for “$30, $40 devices and have almost a negative margin”. She explains that the inclusion of a free advertising SDK can be alluring to these OEM’s and the malware developers “threat actors” as Stone puts it, know this.
Stone's revelations about the scale of malpractice amongst manufacturers raises serious concerns about Google's certification process. If you think it's time Google took it's responsibility to users seriously and enforce that manufacturers behave better, sign our petition.