Search
Content type: Press release
Privacy International Executive Director Dr Gus Hosein said:
“If today’s leaks are authenticated, they demonstrate what we’ve long been warning about government hacking powers — that they can be extremely intrusive, have enormous security implications, and are not sufficiently regulated. Insufficient security protections in the growing amount of devices connected to the internet or so-called “smart” devices, such as Samsung Smart TVs, only compound the problem, giving governments easier…
Content type: News & Analysis
This guest piece was written by Elonnai Hickok, Amber Sinha and Vanya Rakesh of the Centre for Internet and Society. It does not necessarily reflect the views or position of Privacy International.
In 2009, the Government of India set up the Unique Identification Authority of India (UIDAI) as an attached office of the erstwhile Planning Commission of India via an executive order. The mandate of the UIDAI was to assign a 12-digit unique identification (UID) number (…
Content type: Long Read
Introduction
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. Yet hacking presents unique and grave threats to our privacy and security. It is far more intrusive than any other surveillance technique, capable of accessing information sufficient to build a detailed profile of a person, as well as altering or deleting that information. At the same time, hacking not only undermines the security of targeted systems, but also has…
Content type: Long Read
This piece was orignally published in Slate in February 2017
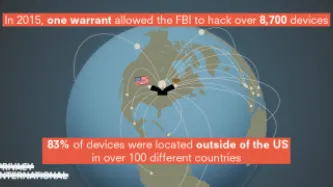
In 2015, the FBI obtained a warrant to hack the devices of every visitor to a child pornography website. On the basis of this single warrant, the FBI ultimately hacked more than 8,700 computers, resulting in a wave of federal prosecutions. The vast majority of these devices—over 83 percent—were located outside the United States, in more than 100 different countries. Now, we are in the midst of the first cases…
Content type: News & Analysis
Technologists hoped the “Crypto Wars” of the 1990s – which ended with cryptographers gaining the right to legally develop strong encryption that governments could not break – was behind them once and for all. Encryption is a fundamental part of our modern life, heavily relied on by everything from online banking and online shopping services to the security our energy infrastructure.
However, from comments by the French and German governments about creating a European initiative to circumvent…
Content type: News & Analysis
In our latest report “Who’s that knocking at my door? Understanding surveillance in Thailand”, we highlighted various methods of surveillance that the Thai Government employs. Included in these methods was the finding that Microsoft was the only technology company which by default trusts the Thai Government’s root certificate. Root certificates ensure the validity of a website, and protect users from being tricked into visiting a fake, insecure website. Most technology companies including Apple…
Content type: News & Analysis
An investigation released by Privacy International this week reveals the Facebook shut-down Thailand experienced in May 2014, at the height of the military coup, may have had more to do with attempting to surveil online communications, rather than censoring Facebook users. This revelation indicates there could be more to other previous internet shutdowns that have happened during times of political unrest.
In May 2014, following months of protest, the Thai military overthrew the…
Content type: Report
This investigation looks at how surveillance is being conducted in Thailand. The first part of the investigation focuses on the ties between telecommunication companies and the state, and the second part of the investigation focuses on attacks conducted in order to attempt to circumvent encryption.
Content type: Long Read
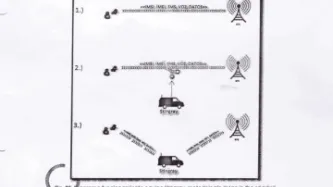
The use of IMSI catchers[1] to arrest individuals is rarely documented — as IMSI catchers are used secretively in most countries. The arrest of Colombian drug lord Henry López Londoño in Argentina is therefore a rare opportunity to understand both how IMSI catchers are used, and also the complexity of their extraterritorial use.
In October 2012, Londoño — also known as Mi Sangre (“My Blood”) — was arrested in Argentina. His arrest was the result of cooperation between the Dirección de…