Advanced Search
Content Type: Long Read
On the basis of a year of legal research by PI as well as documents obtained by other civil society organisations, and evidence provided by legal representatives fighting these automated systems on behalf of their clients, on the 18th August 2025, we issued a formal complaint to the UK Information Commissioner (ICO) regarding the UK Home Office’s use of two ‘automated recommendation-making tools’ (ARMTs), the Identify and Prioritise Immigration Cases tool (IPIC) and the Electronic Monitoring…
Content Type: Long Read
On 13 March 2025, we filed a complaint against the UK government challenging their use of dangerous, disproportionate and intrusive surveillance powers to undermine the privacy and security of people all over the world. Here, we answer some key questions about the case and the recent events that led to this development.Note: This post was last updated on 13 March 2025.What’s the fuss about?A month ago, it was reported that the UK government demanded Apple Inc – maker of the iPhone, iPads, Macs…
Content Type: Advocacy
In May 2024, we made a submission for the forthcoming report of the UN Special Rapporteur on the right to education to the General Assembly in October 2024.
Amongst others we recommend the UN Special Rapporteur for this upcoming report to:
Underline the need for a human rights-based approach to all AI systems in the education sector and describe the necessary measures to achieve it.
Reassert that any interference with the right to privacy and the advancement of the right to education due to…
Content Type: Video
The case dealt with a Russian law obliging telecommunications service providers to indiscriminately retain content and communications data for certain time periods, as well as a 2017 disclosure order by the Russian Federal Security Service requiring Telegram Messenger company to disclose technical information which would facilitate “the decoding of communications”.Links:PI case pageECtHR judgment in the Podchasov casePI's work on encryptionPI's report on End-to-End Encryption (E2EE)More…
Content Type: Advocacy
We are responding to the UK Government's consultation to expand its powers around Technical Capabilities Notices and National Security Notices.
Background
Following Edward Snowden's revelations about the illegal and expansive secret powers of the US and UK intelligence agencies, the UK Government took the opportunity to, rather than reflect on what powers are proportionate in the modern era, to expand its arsenal of surveillance powers.
One of the powers it added was the ability to issue…
Content Type: Advocacy
Privacy International welcomes the aim of the Cyber Resilience Act to bolster cybersecurity rules to ensure more secure hardware and software products. Nevertheless, we note that the proposal put forward by the European Commission contains certain shortcomings which could both hamper innovation and harm consumers who are increasingly relying on digital products and services.It is essential these shortcomings, detailed below, are effectively addressed by the EU co-legislators through the…
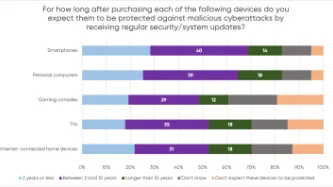
Content Type: Press release
A YouGov survey commissioned by PI shows that consumers expect their smartphones, computers, smart TVs and gaming consoles to receive security updates for a much longer period than what several manufacturers actually provide, leaving consumers with expensive tech that is vulnerable to cyberattacks.
The majority of consumers in the survey assumed their devices would be protected beyond two years, but current industry practices fail to meet these expectations. PI investigated the software…
Content Type: News & Analysis
It is difficult to imagine a more intrusive invasion of privacy than the search of a personal or home computer ... when connected to the internet, computers serve as portals to an almost infinite amount of information that is shared between different users and is stored almost anywhere in the world.
R v Vu 2013 SCC 60, [2013] 3 SCR 657 at [40] and [41].
The controversial Police Crime Sentencing and Courts Bill includes provision for extracting data from electronic devices.
The Bill…
Content Type: News & Analysis
Unwanted Witness’ research into Safeboda highlighted the company’s failure to comply with some of the law's core data protection principles, with a number of implications for the exercise of data subject rights. The enforcement action against Safeboda by National Information Technology Authority, Uganda (NITA-U) requires the company to make fundamental changes to how they handle people's personal data in order to comply with the Data Protection and Privacy Act, 2019.
This first landmark…
Content Type: News & Analysis
An excerpt of this piece was first published in June 2020 in Adbusters, an international not-for-profit magazine produced by a global collective of artists and activists who want to 'shake up complacent consumer culture'.
Big oil. Big tobacco. Big pharma. How did we let ‘big tech’ happen? You would have thought humanity would learn its lesson. That nothing good comes of the mass accumulation and concentration of power into the hands of so few.
The internet was meant to be different. No…
Content Type: Frequently Asked Questions
On 27 October 2020, the UK Information Commissioner's Office (ICO) issued a report into three credit reference agencies (CRAs) - Experian, Equifax and TransUnion - which also operate as data brokers for direct marketing purposes.
After our initial reaction, below we answer some of the main questions regarding this report.
Content Type: News & Analysis
Privacy International (PI) welcomes today's report from the UK Information Commissioner's Office (ICO) into three credit reference agencies (CRAs) which also operate as data brokers for direct marketing purposes. As a result, the ICO has ordered the credit reference agency Experian to make fundamental changes to how it handles people's personal data within its offline direct marketing services.
It is a long overdue enforcement action against Experian.…
Content Type: News & Analysis
New technologies continue to present great risks and opportunities for any users but for some communities the implications and harms can have severe consequences and one of the sectors facing increasing challenges to keep innovating whilst protecting themselves and the people they serve is the humanitarian sector.
Over the course of engagement with the humanitarian sector, one of our key observations has been how risk assessments undertaken in the sector omitted to integrate a hollistic…
Content Type: News & Analysis
In September 2019, PI published the report Your Mental Health for Sale. Our investigation looked into popular mental health websites and their data sharing practices.
Our findings suggest that, at the time of the research, most websites we looked at were using third party tracking for advertising purposes, sometimes relying on programmatic advertising technologies such as Real Time Bidding (RTB), sharing personal data with potentially thousands of actors. Some websites were also found sharing…
Content Type: News & Analysis
Name: Google/Fitbit mergerAge: GestatingAppearance: A bit dodgy. One of the world’s biggest tech giants, trying to purchase a company that makes fitness tracking devices, and therefore has huge amounts of our health data.I don’t get it. Basically Google is trying to buy Fitbit. As if Google doesn’t already have enough data about us, it now wants huge amounts of health data too.Oh, Fitbit, that’s that weird little watch-type-thing that people get for Christmas, wear for about a month while they…
Content Type: Call to Action
Google wants to know everything about you.It already holds a massive trove of data about you, but by announcing its plans to acquire the health and fitness tracker company Fitbit, it now clearly wants to get its hands on your health too. We don’t think any company should be allowed to accumulate this much intimate information about you. This is why we’re trying to stop its merger with Fitbit.Google and Fitbit need the European Commission’s approval before they can merge. The merger would have…
Content Type: Report
Back in October 2019, PI started investigating advertisers who uploaded personal data to Facebook for targeted advertising purposes. We decided to take a look at "Advertisers Who Uploaded a Contact List With Your Information", a set of information that Facebook provides to users about advertisers who upload files containing their personal data (including unique identifier such as phone numbers, emails etc...). Looking at the limited and often inaccurate information provided by Facebook through…
Content Type: Explainer
In a scramble to track, and thereby stem the flow of, new cases of Covid-19, Governments around the world are rushing to track the locations of their populace. One way to do this is to write a smartphone app which uses Bluetooth technology, and encourage (or mandate) that individuals download and use the app. We have seen such examples in Singapore and emerging plans in the UK.
Apps that use Bluetooth are just one way to track location. There are several different technologies in a smartphone…
Content Type: Long Read
We are excited to spotlight our Reproductive Rights and Privacy Project!
The Project is focused on researching and exposing organisations that collect and exploit the information of those seeking to exercise their reproductive rights. Working together with PI partners, other international grassroots organisations and NGOs, PI is researching and advocating against this data exploitation.
So, what are reproductive rights?
Sexual and reproductive rights, which are contained within Economic,…
Content Type: Long Read
In December 2018, Privacy international exposed the dubious practices of some of the most popular apps in the world.Out of the 36 apps we tested, we found that 61% automatically transfer data to Facebook the moment a user opens the app. This happens whether the user has a Facebook account or not, and whether they are logged into Facebook or not. We also found that some of those apps routinely send Facebook incredibly detailed and sometimes sensitive personal data. Again, it didn’t matter if…
Content Type: Video
Watch our video primer (1m54s) on how political advertisers use highly detailed data about you to target political adverts at you.
Read about some simple steps you can take to minimise the amount of political ads you see online and questions you can be asking of those that profit from your data.
Content Type: Impact Case Study
What HappenedOn 5 June 2013, The Guardian published the first in a series of documents disclosed by Edward Snowden, a whistleblower who had worked with the NSA. The documents revealed wide-ranging mass surveillance programs conducted by the USA’s National Security Agency (NSA) and the UK’s Government Communications Headquarters (GCHQ), which capture the communications and data of hundreds of millions of people around the world. In addition to revealing the mass surveillance programs of the NSA…
Content Type: Impact Case Study
What is the problem
Business models of lots of companies is based on data exploitation. Big Tech companies such Google, Amazon, Facebook; data brokers; online services; apps and many others collect, use and share huge amounts of data about us, frequently without our explicit consent of knowledge. Using implicit attributes of low-cost devices, their ‘free’ services or apps and other sources, they create unmatched tracking and targeting capabilities which are being used against us.
Why it is…
Content Type: Impact Case Study
What happenedStrong and effective data protection law is a necessary safeguard against industry and governments' quest to exploit our data. A once-in-a-generation moment arose to reform the global standard on data protection law when the European Union decided to create a new legal regime. PI had to fight to ensure it wasn't a moment where governments and industry would collude to reduce protections.In January 2012, the European Commission published a proposal to comprehensively reform the…