ID systems analysed: e-Estonia
Our third research piece on some of the world’s most used foundational ID systems looks into e-Estonia. This analysis is part of PI's wider research into the tech behind ID systems around the world. Click here to learn more.

Overview
Estonia is widely considered one of the most digitally advanced countries in the world. Its e-ID is the gateway through which e-citizens are able to access most public services. Estonia's e-ID is both designed and operated by a collection of private companies, and overseen by the Police and Border Guard agency.
X-Road® (implemented in Estonia as X-tee) is the free and open-source data exchange layer which provides a standardised method for transferring information between the data systems of private and public sector organisations. X-Road has recently been made available on GitHub under the MIT License, one of the most permissive Free and Open Source Software (FOSS) licenses available.
The data held by the Estonian government is decentralised and duplicated through the use of data embassies. These are essentially data centres that, despite sitting outside Estonia's borders, remain fully under Estonia's control and have the same rights as physical embassies such as immunity.
The X-tee pilot project was initiated in 2000 from the budget of the Ministry of Transport and Communications, Ministry of the Interior and the Government Office and co-ordinated by the state information system department (RISO) of the Ministry of Economic Affairs.
A two-stage public procurement was organised in April and May 2001 and it was won by Estonian IT company AS Assert. Several Estonian companies were then sub-contracted to develop different components of the project:
- AS Cybernetica – architecture, protocols and security solutions;
- AS Andmevara – test queries to the population register, Estonian Registry of Buildings;
- Reaalsüsteemide AS – test queries to Commercial Register;
- AS Datel – test queries to electronic Land Register;
- Estonian commercial banks - authentication of users.
Gemalto (now part of Thales Group) was contracted to manufacture the physical ID cards used to authenticate against e-Estonia citizen services, and was later ordered to pay €2.2 million to the Police and Border Guard Board in compensation over security vulnerabilities in the manufactured cards. Since 2019, Oberthur Technologies has been in charge of manufacturing ID cards and maintaining their functionality.
Infrastructure makeup
In designing their identity system, Estonia harnessed widely-used technologies and applied them, in a novel way, to the state governance context. X-tee (Estonia's version of X-Road) was the outcome of this application of existing technologies. This is one of the major reasons behind X-Road's success; it is in fact a data-exchange layer modelled on tried and tested technologies, ambivalent to the authentication mechanism implemented.
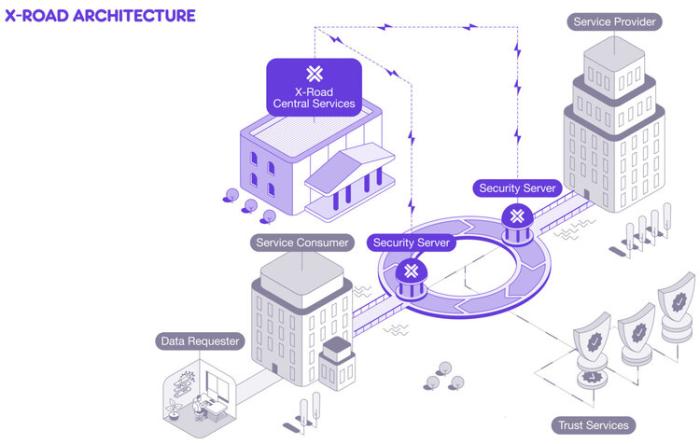
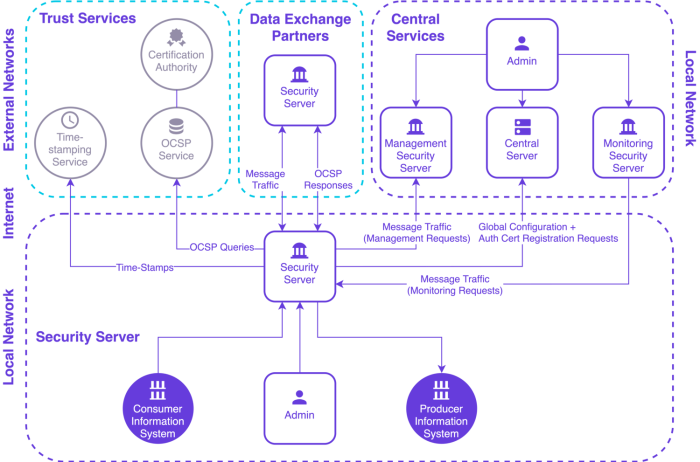
Technically the X-Road ecosystem consists of Central Services, Security Servers, Information Systems, Time-Stamping Authority(ies) (TSAs), and Certificate Authorities (CAs):
From X-Road's documentation we can see that Central Services consist of a Central Server and Configuration Proxy. This Central Server contains the registry of X-Road members and their Security Servers as well as the security policy of the X-Road instance. This security policy includes a list of trusted certification authorities, a list of trusted time-stamping authorities, and configuration parameters. Both the member registry and the security policy are made available to the Security Servers via HTTP protocol. This distributed set of data forms the global configuration that Security Servers use for mediating the messages sent via X-Road.
A Security Server is the entry point to X-Road, and it is required for both producing and consuming services via X-Road. The Security Server mediates service calls and service responses between Information Systems and handles the security aspects of the X-Road infrastructure such as:
- Managing keys for signing and authentication;
- Sending messages over a secure channel;
- Creating the proof value for messages with digital signatures;
- Time-stamping and logging.
The Information System produces or consumes services via X-Road and is owned by an X-Road member. X-Road supports both REST and SOAP as communication methods, however X-Road does not provide automatic conversions between different types of messages and services. The Information System is capable of discovering registered X-Road members and their available services by using the X-Road metadata protocol.
All messages sent via X-Road are time-stamped and logged by the Security Server. The purpose of the time-stamping is to certify the existence of data items at a certain point in time. The Time-Stamping Authority (TSA) provides a time-stamping service that the Security Server uses for time-stamping all the incoming/outgoing requests/responses. Only trusted TSAs that are defined in the Central Server can be used.
The certification authority (CA) issues certificates to Security Servers (authentication certificates) and X-Road member organizations (signing certificates). Authentication certificates are used for securing the connection between two Security Servers. Signing certificates are used for digitally signing messages sent by X-Road members. Only certificates issued by trusted certification authorities defined in the Central Server can be used.
Encryption used
From X-Road's publicly available documentation we can get a grasp of the encryption algorithms used within the different components of the platform. All the protocols mentioned in the documentation are widely used and well documented. In addition, X-Road has regular third-party security assessments, with a public bug bounty programme.
Estonia's e-ID system, however, had fundamental implementation failures when in 2011 the government distributed 120,000 faulty ID cards that were found to have programming errors allowing the card to be used by whoever was physically holding it without the need of knowing the respective PIN code.
More worrying, and not limited to 120,000 faulty cards affected, is a core design feature regarding the way private encryption keys were generated and handled. The ID card's private encryption key used to authenticate digital signatures should be generated inside the card chip to ensure only that card knows it - a good example of privacy by design. Instead, keys were generated in a server operated by the card manufacturer and copied to the card over the internet.
Another software bug was reported in which the same private key was copied to several different ID-cards, allowing cardholders that were assigned non-unique private keys to use one another's identity.
These above bugs' origins have been tracked down to Gemalto, the contractor tasked with manufacturing and maintaining functionality within Estonia's ID cards. This resulted in Gemalto being ordered to pay €2.2 million compensation to the Police and Border Guard Board. Since 2019 another company called Oberthur Technologies has been in charge of manufacturing ID cards and maintaining their functionality.
De-duplication
Very little is publicly available about the deduplication undertaken in e-Estonia, except that the processes of verification and deduplication during identification are overseen by the Police and Border Guard Board (PBGB), according to the Identity Documents Act. Where the applicant for the digital ID has not previously been issued any ID under the Act, it is the PBGB that conducts the process of verification/deduplication. The Identity Documents Act also allows the Authority, who collects the personal data, to transfer it to third parties for the “identification and verification of facts relevant to the issue” and for the “issue and revocation of an identity document.”
The use of biometrics when registering is optional, but there are talks of turning to fingerprints for authentication when using ID cards instead of PIN codes.
Principles of Engagement
Estonia's e-governance principles were published as follows:
Where
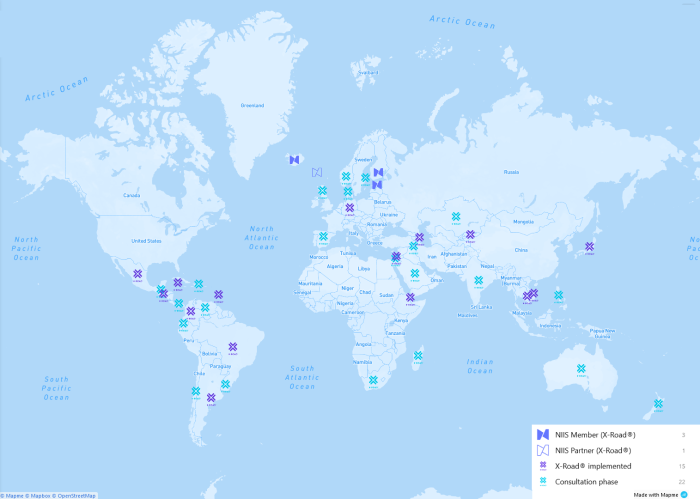
The story of the Nordic Institute for Interoperability Solutions (NIIS) is one of two European countries that throughout history joint forces to collaborate and face challenges together. In 2013, the challenge to overcome was data sharing in and between national governments. Estonia and Finland decided to find mutually beneficial solutions together. The framework for the collaboration was set up in 2017 and called the Nordic Institute for Interoperability Solutions, using X-Road as its underlying technology. Iceland joined NIIS on 1st June 2021 and became the third member government in the international consortium after initial founders Estonia and Finland.
NIIS partners are countries which implemented X-Road and have signed a partnership agreement with the NIIS aiming to deepen their cooperation, meaning they can one day may become members.
The remaining countries where X-Road is implemented have deployed the technology while not being tied to NIIS.
NIIS Member
NIIS Partner
X-Road Implemented
- The province of Neuquén, Argentina
- Azerbaijan
- Barbados
- The States of Mato Grosso and Amapá, Brazil (used for data exchange between the two states)
- Cambodia
- Cayman Islands
- Colombia
- El Salvador
- The State of Hessen, Germany (used for Medical video consultation and digital prescriptions)
- Japan
- Kyrgyzstan
- The State of Quintana Roo, Mexico
- Palestine
- Vietnam
Consultation Phase:
- Djibouti
- Chile
- Denmark
- Dominican Republic
- Ecuador
- Guatemala
- India
- Israel
- Kazakhstan
- Kurdistan Region
- Madagascar
- New Zealand
- Norway
- Panama
- Philippines
- Saudi Arabia
- Scotland
- South Africa
- Spain
- Sweden
- Uruguay
- Venezuela
Examples of Abuse
Transparency
Digital identity ecosystems are complex and have a great number of potential points of failure. In this sense, vulnerabilities should not be a surprise and it is essential that governments commit to transparency and make failures public as well as planned remediation. It took the Estonian government 9 months to communicate they handed out 120,000 ID-cards with no usable PIN authentication, which is arguably more worrying than the failure itself. Since then all those affected have had their cards replaced.
"This highlights an important risk – no one knows what the ID-card manufacturer is doing with private keys. There is no one to check that." - Arnis Paršovs (research fellow, cybersecurity expert) for ERR News
Public private partnerships, or the contracting of private companies to develop components of a technology stack adds an additional layer of opacity to the design and processes. For Estonia this layer was so thick that not even the government was able to observe or scrutinise decisions made by its contractor Gemalto (now part of Thales Group). Governments need to ensure that an external private agent is not trampling on important safeguards and is subject to scrutiny and held accountable.
Security
Besides the above mentioned issues related to ID card, there have also been reports of data breaches. Namely, the one where a hacker was able to obtain over 280,000 personal identity photos following an attack on a database of credentials held by the Estonian Information System Authority (RIA).
The data the hacker obtained, namely picture, personal ID code and the individual's name, were insufficient to access any of Estonia's e-state services but at the same time exposed vulnerabilities in the system.
Following Nordic Institute for Interoperability Solutions (NIIS)'s feedback on the original version of this piece, it was updated to ensure there are no misunderstandings and to include their response.