Advanced Search
Content Type: Examples
DroneAcharya, which has recently merged with drone technology start-up AVPL International, has been awarded a contract worth 1.87m Indian Rupees ($21, 660) by the Indian Ministry of Defence. The agreement involves hardware and training for the piloting of drones. This will enhance the Indian military's surveillance capabilities to use drones for intelligence gathering, reconnaissance, and monitoring. Drone Acharya's share prices rose by 4% after news of the Public-Private Partnership went…
Content Type: Examples
On behalf of the Norwegian government, the Norwegian Intelligence Service has awarded Kongsberg Defence and Aerospace (“Kongsberg”) a four-year contract to supply satellite maritime surveillance data in order to cover Norwegian Areas of Interest. Kongsberg will produce three satellites and equip them with automatic identification system receivers and detector systems; the data will be used by the Norwegian Armed Forces and other Norwegian government bodies. Kongsberg will be the owner of the…
Content Type: Examples
Westminster Group PLC has ratified a ten-year, multi-million-pound contract to supply ground security operations and advanced detection, surveillance, and screening equipment, as well as maintenance, training, and support at one domestic and four international airports in the Democratic Republic of the Congo (DRC). Under the managed services model, which Westminster has deployed elsewhere in Africa, revenues will be driven by embarking passenger numbers and funded by a fee per passenger…
Content Type: Examples
As part of an agreement worth up to $20.8 million, Teledyne FLIR Defense will deliver ultra long-range multi-spectral imaging surveillance systems, or Star SAFIRE 380-HLD, to the Japan Maritime Defense Force, which will integrate them into the licenced Japan-based production version of the Sikorsky SH-60 helicopter. The system can operate continuously in all weather conditions and can transmit both thermal and visual imagery in high definition to those who are operating it. https://www.…
Content Type: Examples
The Swedish Defence Materiel Administration has awarded Saab a $245 million contract to provide the Swedish air force with a third GlobalEye surveillance aircraft and other services like those already in use in UAE. The contract runs until 2029. The air force is accelerating the schedule for introducing locally-designated assets after donating its current two Erieye radar-equipped Saab 340 early warning and control aircraft to Ukraine. https://www.flightglobal.com/defence/sweden-signs-…
Content Type: Examples
The US Air Force will give Capella Space Corp $15 million in funding to improve and scale its synthetic aperture radar to deliver enhanced resolution imagery. Capella also supplies technology to the National Geospatial Intelligence Agency, National Reconnaissance Office, US Navy, US Space Force, and NASA.https://www.capellaspace.com/press-releases/capella-space-awarded-a-15m-contract-with-the-u-s-air-forcePublication: Capella SpaceWriter: Capella Space
Content Type: Examples
It has been announced that the California Highway Patrol has signed a $1.6 million (for the first year) contract with Flock Safety to install 480 high-tech cameras on Oakland's streets and freeways to identify licence plates and catalogue passing vehicles by make, model, colour, and other features. An official asserted that footage obtained from the cameras would be deleted after 28 days and not shared with third parties or other states that might use the information to track people seeking or…
Content Type: Examples
The UK Home Office has renewed its 3 year long contract with Tekever to provide maritime surveillance as a service across the English Channel using its AR5 and AR3 model drones, also known as Unmanned Aerial Vehicles (UAVs). The AR5 system is a UAV that is intended to conduct surveillance missions and can fly for more than 20 hours and carry sensors such as maritime radar and day and night cameras. It will be used to detect, recognise, track, and identify potentially illegal vessels and…
Content Type: Examples
Under a new contract, Planet Labs PBC will provide the NATO Communications and Information Agency's Alliance Persistent Surveillance from Space programme (APSS) with satellite data to aid in detailed tracking and analysis of foreign military activities and fill intelligence gaps. APSS is a multi-year, multinational project to use space to collect data on any location at any time and enhance NATO's engagement with future technologies, for example Artificial Intelligence (AI) and cloud…
Content Type: Examples
The US Department of Defense has awarded a contract worth almost $250 million to Anduril Industries for more than 500 Roadrunner-Ms as well as Pulsar electronic warfare capabilities, with AI-enabled systems, to counter the threat of attacks using unmanned aerial systems in “priority regions”. Anduril has won nearly $350 million in contracts since these technologies were publicly launched.https://www.designdevelopmenttoday.com/industries/military/news/22922589/anduril-awarded-250-million-air-…
Content Type: Examples
Under a new contract effective from October 2024 to December 2025, PureTech Systems, which specialises in geospatial AI-boosted video analytics, will deploy its command-and-control software in 22,600 square kilometers of the US border. The software will integrate the sensors attached to existing surveillance towers while retaining the interface already familiar to border agents.https://www.prnewswire.com/news-releases/puretech-systems-inc-awarded-major-command-and-control-contract-by-us-…
Content Type: Long Read
1. What is the issue?Governments and international organisations are developing and accessing databases to pursue a range of vague and ever-expanding aims, from countering terrorism and investigating crimes to border management and migration control.These databases hold personal, including biometric, data of millions if not billions of people, and such data is processed by technologies, including Artificial Intelligence (AI), to surveil, profile, predict future behaviour, and ultimately make…
Content Type: Advocacy
In May 2024, we made a submission for the forthcoming report of the UN Special Rapporteur on the right to education to the General Assembly in October 2024.
Amongst others we recommend the UN Special Rapporteur for this upcoming report to:
Underline the need for a human rights-based approach to all AI systems in the education sector and describe the necessary measures to achieve it.
Reassert that any interference with the right to privacy and the advancement of the right to education due to…
Content Type: Examples
L3Harris is contracted by the U.S. Space Force to develop space surveillance information though a programme known as MOSSAIC (the Maintenance Of Space Situational Awareness Integrated Capabilities). The program is said to provide space surveillance information for military, civil and commercial users.https://www.satellitetoday.com/government-military/2024/04/19/us-space-force-awards-l3harris-contract-option-for-space-surveillance-program/Publication: ViaSatelliteWriter: Rachel Jewett
Content Type: Examples
Israel based company, High Lander, is providing demos of its system, called Orion, to U.S. police departments, suggesting the drones can help in law enforcement, including by performing video surveillance, searching for people or vehicles using AI and thermal sensors. https://theintercept.com/2024/05/17/israel-orione-drone-us-police-louisiana/Publication: The InterceptWriter: Delaney Nolan
Content Type: Examples
Microsoft pitched the use of OpenAI's DALL-E software to support battlefield operations of the US Department of Defense, in seeming contravention of OpenAI's ban against working in the military field. One of the potential use cases proposed by Microsoft is to use DALL-E, OpenAI's image generation model, to train battle management systems. The efficacy, reliability and ethics of such a use of private AI are questioned by various experts. https://theintercept.com/2024/04/10/microsoft-openai-…
Content Type: Examples
Fusion Technology will earn $159.8 million over 5 years to work with the US FBI's Criminal Justice Information Services (CJIS). It will support the FBI in developing the National Data Exchange ("an investigative tool for agencies to search, analyze, and share criminal justice information"), the Law Enforcement Online System (for information sharing between local, state, tribal, federal, and international criminal justice agencies) and "Crime Data apps".https://www.biometricupdate.com/202404/…
Content Type: Examples
US data analytics firm Palantir, known for its numerous contracts with intelligence agencies, military forces, or law enforcement and immigration authorities, has been awarded a £330m contract to run a new mass database for the UK's health service (NHS). The deal comes four years after Palantir was awarded a £1 contract during the Covid-19 pandemic to build an analytics platform for the NHS. People and organisations across the political spectrum have voiced significant privacy and data…
Content Type: Video
The case dealt with a Russian law obliging telecommunications service providers to indiscriminately retain content and communications data for certain time periods, as well as a 2017 disclosure order by the Russian Federal Security Service requiring Telegram Messenger company to disclose technical information which would facilitate “the decoding of communications”.Links:PI case pageECtHR judgment in the Podchasov casePI's work on encryptionPI's report on End-to-End Encryption (E2EE)More…
Content Type: Examples
Over 60 US cities and counties use Fusus, a "police technology platform that merges public and private cameras with predictive policing and other surveillance tools". Private surveillance camera owners are encouraged to enroll in a police-led program that enables the police to control these cameras. The result is an expanstion of policed spaces and integration of all private and public surveillance systems in one comprehensive dragnet. And Fusus' platform does not stop at integrating CCTV…
Content Type: Examples
Notorious military tech company Anduril is pushing its technology to the border surveillance market. Along the US-Mexico border, its surveillance towers "use an artificial intelligence system called Lattice to autonomously identify, detect and track “objects of interest”, such as humans or vehicles. The cameras pan 360 degrees and can detect a human from 2.8km away." But border surveillance technology has been shown to lead people to lengthier and more dangerous routes as they seek to avoid…
Content Type: Report
This policy paper seeks to determine the potential for the existing international private military and security companies (PMSCs) regulatory framework to support more effective regulation of surveillance services provided by the private sector.In order to achieve this, and given that this paper addresses an issue that is at the intersection of two domains, it seeks to establish a common language and terminology between security sector governance and surveillance practitioners.In…
Content Type: Examples
When the Los Angeles Police Department opted to monitor the messages posted in forums on Neighbors, a companion app to Amazon's Ring doorbell cameras, the system forwarded over 13,000 messages in just over two years. Research shows, however, that this type of surveillance does a poor job of deterring property crime. A study of Neighbors posts in LA also shows that posters typically live in whiter, more affluent districts, and about 30% of posts did not describe criminal activity, just behaviour…
Content Type: Advocacy
We are responding to the UK Government's consultation to expand its powers around Technical Capabilities Notices and National Security Notices.
Background
Following Edward Snowden's revelations about the illegal and expansive secret powers of the US and UK intelligence agencies, the UK Government took the opportunity to, rather than reflect on what powers are proportionate in the modern era, to expand its arsenal of surveillance powers.
One of the powers it added was the ability to issue…
Content Type: Long Read
The rise of racist and xenophobic narratives around the world has led to a ramping up of brutal migration control policies. Indefinite detention, pushbacks of boats at sea, or deportation for offshore processing of asylum claims all now form part of the arsenal deployed by some governments to “appear tough” on and provide "solutions" to immigration. A stark example is the UK’s “hostile environment” policy, announced 10 years ago by then Home Secretary Theresa May and designed to deter migrants…
Content Type: Advocacy
Privacy International welcomes the aim of the Cyber Resilience Act to bolster cybersecurity rules to ensure more secure hardware and software products. Nevertheless, we note that the proposal put forward by the European Commission contains certain shortcomings which could both hamper innovation and harm consumers who are increasingly relying on digital products and services.It is essential these shortcomings, detailed below, are effectively addressed by the EU co-legislators through the…
Content Type: Advocacy
We, the undersigned organisations, seek to draw your attention to aspects of the draft Corporate Sustainability Due Diligence Directive (the Directive), and its application to the use of technology and the technology sector, which require strengthening if the Directive is to realise its full potential in respect of this critical global sector that is today responsible for some of the most egregious human rights harms.
The technology and surveillance industries have ushered in an entirely new…
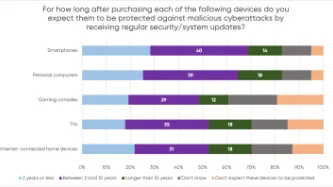
Content Type: Press release
A YouGov survey commissioned by PI shows that consumers expect their smartphones, computers, smart TVs and gaming consoles to receive security updates for a much longer period than what several manufacturers actually provide, leaving consumers with expensive tech that is vulnerable to cyberattacks.
The majority of consumers in the survey assumed their devices would be protected beyond two years, but current industry practices fail to meet these expectations. PI investigated the software…
Content Type: Report
End-to-end encryption (E2EE) contributes significantly to security and privacy. For that reason, PI has long been in favour of the deployment of robust E2EE.Encryption is a way of securing digital communications using mathematical algorithms that protect the content of a communication while in transmission or storage. It has become essential to our modern digital communications, from personal emails to bank transactions. End-to-end encryption is a form of encryption that is even more private.…
Content Type: Long Read
Introduction
In response to the unprecedented social, economic, and public health threats posed by the Covid-19 pandemic, the World Bank financed at least 232 "Covid-19 Response" projects. The projects were implemented across countries the World Bank classifies as middle and low-income.
This article will focus on eight (8) Covid-19 Response projects which sought to deliver social assistance to individuals and families on a "non-contributory" basis (this means that the intended beneficiaries…