Advanced Search
Content Type: Long Read
On the basis of a year of legal research by PI as well as documents obtained by other civil society organisations, and evidence provided by legal representatives fighting these automated systems on behalf of their clients, on the 18th August 2025, we issued a formal complaint to the UK Information Commissioner (ICO) regarding the UK Home Office’s use of two ‘automated recommendation-making tools’ (ARMTs), the Identify and Prioritise Immigration Cases tool (IPIC) and the Electronic Monitoring…
Content Type: News & Analysis
Yesterday the Investigatory Powers Tribunal announced next steps in Apple’s and PI’s challenges to the purported UK order undermining iCloud’s security.The Tribunal declared that it will aim to hear much of Apple’s case, as well as PI and our co-claimants’, in public based on assumed facts. The Tribunal will convene a seven day hearing to be scheduled in early 2026. Its aim will be to hear Apple’s case and PI’s case during those seven days.This ‘case management order’ follows submissions from…
Content Type: News & Analysis
We’ve been warning for a while now about the risks of AI Assistants. Are these assistants designed for us or to exploit us?The answer to that question hinges on whether the firms building these tools are considering security and privacy from the outset. The initial launches over the last couple of years were not promising.Now with OpenAI’s agent launch, users deserve to know whether these firms are considering these risks and designing their service for people in the real world. The OpenAI…
Content Type: Long Read
In June 2025, a team of researchers exposed how Meta and Yandex abused Android and browser-specific tools to track users outside of their application and collect associated data. The technique used to achieve this was truly innovative, and akin to malware behaviour. It exploited protocols to break the isolation between apps and browser, a fundamental security concept meant to protect users. This allowed these companies to tie the browsing history of individuals with their accounts on the…
Content Type: Long Read
Period tracking apps and the rollback of reproductive rightsThe aftermath of the overturning of Roe v. Wade in the United States (US) sparked widespread debate and concern that data from period tracking apps could be use to criminalise those seeking abortion care.While the surveillance and criminalisation of reproductive choices are neither new nor unique to the US, the scale and intensity of today’s crisis continue to grow. To put it into perspective, 22 million women and girls of reproductive…
Content Type: News & Analysis
Layla looks at her calendar on her phone. She’s in charge of planning her book club’s monthly meeting. After thinking for a second, she summons her AI assistant: “Hey Assistant, can you book me a table at that tapas restaurant I read about last week, and invite everyone from the book club? The restaurant should be in my browsing history. Let me know if the journey is more than 1-hour for anyone”. As the assistant compiles a response, she wonders if anyone else will hear this.Technology has made…
Content Type: Long Read
If you’ve ever used TikTok, Instagram, or X/Twitter, you will already be familiar with centralised social media.Centralised social media means big company owns the app, controls the software, and keeps all your data.For example, ByteDance makes TikTok. They own it, run the servers, decide what you see in your feed, and hold onto every video you like or comment on. They call the shots when it comes to your data.But what if social media didn’t work that way? What if no single company was in…
Content Type: Long Read
“Hey [enter AI assistant name here], can you book me a table at the nearest good tapas restaurant next week, and invite everyone from the book club?” Billions of dollars are invested in companies to deliver on this. While this is a dream that their marketing departments want to sell, this is a potential nightmare in the making.Major tech companies have all announced flavours of such assistants: Amazon’s Alexa+, Google’s Gemini inspired by Project Astra, Microsoft’s Copilot AI companion and…
Content Type: Press release
FOR IMMEDIATE RELEASELONDON - 7 April 2025The Investigatory Powers Tribunal (IPT) has confirmed it will hear Privacy International, Liberty and two individuals’ challenge to the legality of the Home Secretary’s decision to use her powers to secretly force Apple to allegedly give the UK Government access to users’ secured data stored on iCloud. The challenge will also cover the legality of the Government issuing these types of notices at all. Privacy International and Liberty,…
Content Type: News & Analysis
We’ve been asked a lot lately about whether it is safe to travel, particularly to the US. And it’s not surprising why: the US Government is increasing their cruelty at borders.Border management today is fueled by our data, but government officials want more. They want as much data as they can get to catch you out. They’ve reportedly detained or deported people based on their free speech activities, denying entry on tenuous grounds like having the wrong photos on phones (including in in the ‘…
Content Type: Long Read
On 13 March 2025, we filed a complaint against the UK government challenging their use of dangerous, disproportionate and intrusive surveillance powers to undermine the privacy and security of people all over the world. Here, we answer some key questions about the case and the recent events that led to this development.Note: This post was last updated on 13 March 2025.What’s the fuss about?A month ago, it was reported that the UK government demanded Apple Inc – maker of the iPhone, iPads, Macs…
Content Type: Advocacy
We believe the Government's position of refusing to confirm or deny the existence of the Technical Capability Notice or acknowledge Apple's appeal is untenable and violates principles of transparency and accountability.
Content Type: Explainer
Imagine this: a power that secretly orders someone anywhere in the world to abide and the receiver can’t tell anyone, can’t even publicly say if they disagree, and can’t really question the power in open court because the secret order is, well, secret. Oh and that power affects billions of people’s security and their data. And despite being affected, we too can’t question the secret order.In this piece we will outline what’s ridiculous, the absurd, and the downright disturbing about what’s…
Content Type: Advocacy
In May 2024, we made a submission for the forthcoming report of the UN Special Rapporteur on the right to education to the General Assembly in October 2024.
Amongst others we recommend the UN Special Rapporteur for this upcoming report to:
Underline the need for a human rights-based approach to all AI systems in the education sector and describe the necessary measures to achieve it.
Reassert that any interference with the right to privacy and the advancement of the right to education due to…
Content Type: Video
The case dealt with a Russian law obliging telecommunications service providers to indiscriminately retain content and communications data for certain time periods, as well as a 2017 disclosure order by the Russian Federal Security Service requiring Telegram Messenger company to disclose technical information which would facilitate “the decoding of communications”.Links:PI case pageECtHR judgment in the Podchasov casePI's work on encryptionPI's report on End-to-End Encryption (E2EE)More…
Content Type: Advocacy
BackgroundThe Snowden revelations and subsequent litigation have repeatedly identified unlawful state surveillance by UK agencies. In response, the UK Parliament passed the highly controversial Investigatory Powers Act 2016 (IPA), which authorised massive, suspicionless surveillance on a scale never seen before, with insufficient safeguards or independent oversight.Privacy International led legal challenges to this mass surveillance regime both before and after the Act became law. The Act…
Content Type: Advocacy
We are responding to the UK Government's consultation to expand its powers around Technical Capabilities Notices and National Security Notices.
Background
Following Edward Snowden's revelations about the illegal and expansive secret powers of the US and UK intelligence agencies, the UK Government took the opportunity to, rather than reflect on what powers are proportionate in the modern era, to expand its arsenal of surveillance powers.
One of the powers it added was the ability to issue…
Content Type: Advocacy
Privacy International welcomes the aim of the Cyber Resilience Act to bolster cybersecurity rules to ensure more secure hardware and software products. Nevertheless, we note that the proposal put forward by the European Commission contains certain shortcomings which could both hamper innovation and harm consumers who are increasingly relying on digital products and services.It is essential these shortcomings, detailed below, are effectively addressed by the EU co-legislators through the…
Content Type: Press release
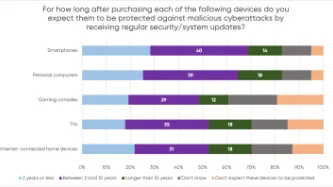
A YouGov survey commissioned by PI shows that consumers expect their smartphones, computers, smart TVs and gaming consoles to receive security updates for a much longer period than what several manufacturers actually provide, leaving consumers with expensive tech that is vulnerable to cyberattacks.
The majority of consumers in the survey assumed their devices would be protected beyond two years, but current industry practices fail to meet these expectations. PI investigated the software…
Content Type: Report
End-to-end encryption (E2EE) contributes significantly to security and privacy. For that reason, PI has long been in favour of the deployment of robust E2EE.Encryption is a way of securing digital communications using mathematical algorithms that protect the content of a communication while in transmission or storage. It has become essential to our modern digital communications, from personal emails to bank transactions. End-to-end encryption is a form of encryption that is even more private.…
Content Type: Long Read
Introduction
In response to the unprecedented social, economic, and public health threats posed by the Covid-19 pandemic, the World Bank financed at least 232 "Covid-19 Response" projects. The projects were implemented across countries the World Bank classifies as middle and low-income.
This article will focus on eight (8) Covid-19 Response projects which sought to deliver social assistance to individuals and families on a "non-contributory" basis (this means that the intended beneficiaries…
Content Type: Examples
Just as China uses technology system called "Integrated Joint Operations Platform" to control and surveil the persecuted population of Uighurs while restricting their movement and branding dissent as "terrorism", the Israeli military is using facial recognition and a massive database of personal information to control millions of Palestinians in the occupied West Bank. In November 2021, NSO Group's Pegasus spyware was found on the phones of six Palestinian human rights activists, three of whom…
Content Type: Examples
The Israeli minister of public security has joined police in denying claims in an article in Calcalist that the country's police force have used NSO Group's Pegasus software to spy on the phones of people who led protests against former premier Benjamin Netanyahu. Calcalist reported that the surveillance was carried out without court supervision or oversight of how the data was used. The daily Haaretz newspaper also reported that it had seen a 2013 invoice in which NSO billed police @@2.7…
Content Type: Long Read
This piece is a part of a collection of research that demonstrates how data-intensive systems that are built to deliver reproductive and maternal healthcare are not adequately prioritising equality and privacy.
What are they?
Short Message Services (SMS) are being used in mobile health (MHealth) initiatives which aim to deliver crucial information to expecting and new mothers. These initiatives are being implemented in developing countries experiencing a large percentage of maternal and…
Content Type: News & Analysis
After almost 20 years of presence of the Allied Forces in Afghanistan, the United States and the Taliban signed an agreement in February 2020 on the withdrawal of international forces from Afghanistan by May 2021. A few weeks before the final US troops were due to leave Afghanistan, the Taliban had already taken control of various main cities. They took over the capital, Kabul, on 15 August 2021, and on the same day the President of Afghanistan left the country.As seen before with regime…
Content Type: Press release
Amnesty International, Privacy International and The Centre for Research on Multinational Corporations (SOMO) have published a report uncovering NSO Group’s entire corporate structure, tracking the global money trail of both public and private investment into the lucrative spyware company.
Amnesty International and other rights groups have documented dozens of cases of NSO Group’s products being used by repressive governments across the world to put activists, journalists, and opposition…
Content Type: News & Analysis
Around the world, we see migration authorities use technology to analyse the devices of asylum seekers. The UK via the Policing Bill includes immigration officers amongst those who can exercise powers to extract information from electronic devices. There are two overarching reasons why this is problematic:
The sole provision in the Policing Bill to extract information rests on voluntary provision and agreement, which fails to account for the power imbalance between individual and state. This…
Content Type: News & Analysis
It is difficult to imagine a more intrusive invasion of privacy than the search of a personal or home computer ... when connected to the internet, computers serve as portals to an almost infinite amount of information that is shared between different users and is stored almost anywhere in the world.
R v Vu 2013 SCC 60, [2013] 3 SCR 657 at [40] and [41].
The controversial Police Crime Sentencing and Courts Bill includes provision for extracting data from electronic devices.
The Bill…
Content Type: Report
In this briefing, Amnesty International, PI and The Centre for Research on Multinational Corporations (SOMO) discuss the corporate structure of NSO group, one of the surveillance industry's well-known participants. The lack of transparency around NSO Group’s corporate structure and the lack of information about the relevant jurisdictions within which it operates are significant barriers in seeking prevention of, and accountability for, human rights violations reportedly linked to NSO Group’s…
Content Type: Explainer
What is hacking?
Hacking refers to finding vulnerabilities in electronic systems, either to report and repair them, or to exploit them.
Hacking can help to identify and fix security flaws in devices, networks and services that millions of people may use. But it can also be used to access our devices, collect information about us, and manipulate us and our devices in other ways.
Hacking comprises a range of ever-evolving techniques. It can be done remotely, but it can also include physical…