A guide to making use of disposable email addresses
Disposable email addresses protect you from unwanted spam and phishing attempts in your personal email inbox, online tracking, and other forms of data abuse, providing you with a stronger digital self-defense mechanism than if you are giving away your e-mail address to each online service you need to make use of.
The practice of buying and selling email addresses is a common one among digital data brokers. Say you register at an online shop to buy an item from a brand. The shop can then sell your email address to that same brand, so they can advertise to you directly in your email inbox. This is a form of targeted advertising, and we have written about its privacy implications to you as a digital citizen. Online marketing is not the sole reason you should consider concealing your personal email address when surfing the web.
For instance, suppose you create an account for a website using your personal email address, and that this website is later a victim of a data leak. Most likely, your email address and the password you used to register will be leaked too. This means, if an attacker gets a hold of this data, they can attempt to target different accounts of yours, provided you used the same personal email address across them. This is an even greater security risk if you [don't use a password manager][8] to avoid reusing passwords.
As such, from a privacy and security standpoint, it is preferable that you avoid handing out your email address to untrusted entities as much as possible. Instead, you can use disposable email addresses that mask your identity to protect your digital privacy.
Disposable email addresses are unique, preferably but not necessarily random email address to be use in untrusted online services. They help prevent data brokers from tracking you across the web, and your identity from being shared. When you no longer need a disposable address (e.g. for a one-time online purchase), you can destroy it without it affecting your personal email account.
This guide covers different solutions to creating and managing disposable email address depending on your operating system and email provider.
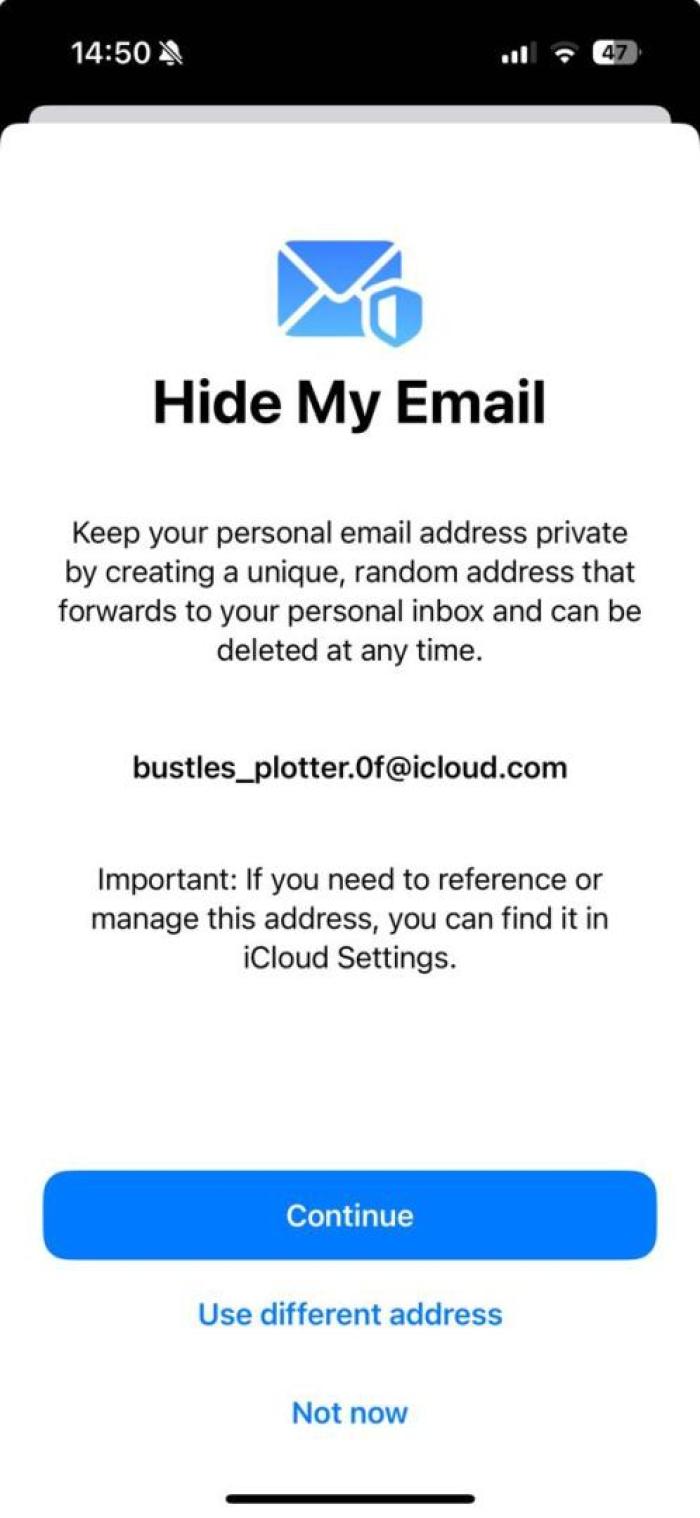
- If you are on iOS or macOS and have an iCloud+ subscription, you can use Apple's Hide My Email service. This will generate random, unique email addresses for you to use online or in apps. Messages sent to this address will be forwarded to your regular inbox without exposing your personal email. To learn how to setup Hide My Email, see here.
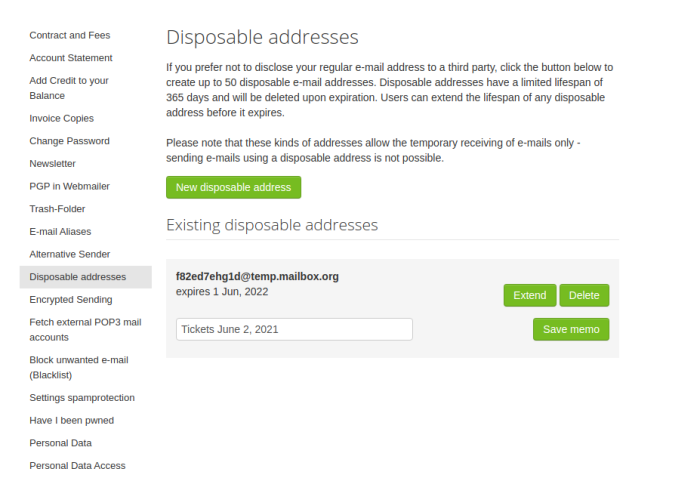
- Some email providers (e.g. Fastmail, Mailbox, Protonmail, Nordmail) provide this feature in their plans, allowing you to create unique, random disposable addresses or masks. Messages sent to this addresses are forwarded to your inbox, and you can dispose of them when you no longer need them. To learn how to set up disposable addresses, refer to your provider's manual.
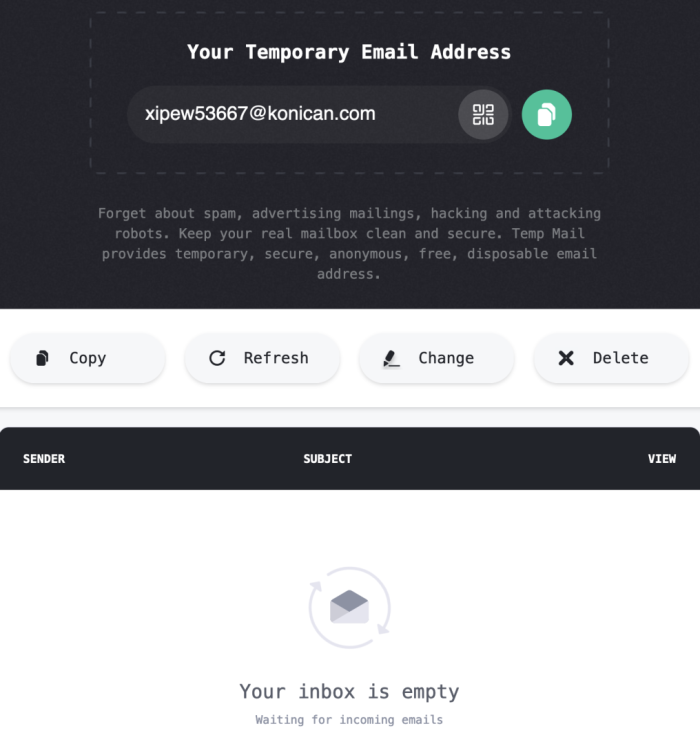
- You can use online email services to create disposable addresses. Services such as Temp Mail or 10 Minute Mail allow you to create unique, temporary email addresses to use online. Since these will expire after a period of time, they should only be considered for one-time account uses. For permanent uses, you can use services such as Firefox Relay or IronVest which provide you with secure email addresses and forward messages sent there to your inbox. Note that, as a general rule of thumb, websites providing this service for free should not be considered for secure communications, given their privacy policies. For such cases, consider using a secure email client that provides this feature.
The solutions presented above allow you to generate disposable email addresses with ease, in most cases delivering messages straight to your inbox, while preventing your personal email address from being shared. Whenever possible, we recommend you resort to this workflow to protect your digital privacy.
Note that this may have an interesting side effect and help you learn about how companies are sharing your data: if you generate a disposable address for an online service 'A', and suddenly start receiving emails from another source 'B' through that address, then you know that service 'A' has granted service 'B' with access to your address (and perhaps other data).
As a closing thought: do you want to check if your email has ever been (publicly) leaked? Visit this website.
Found a mistake? An outdated screenshot? Think this could be improved? Check out our Github repository and contribute to help keep these guides up-to-date and useful!