The hidden threat: Privacy and security risks in chips
- Integrated circuits, also referred to as chips (or microchips), are a key part of our devices and infrastructure. Their security is paramount for our privacy.
- However, chips can be subject to vulnerabilities that allow for unauthorised access to our data and our devices. Chips’ vulnerabilities can arise through supply chain interference or through government intervention.
- With growing tensions across the world, complex global supply chains that intersect many interests and jurisdictions can put privacy and security further in jeopardy.
- Governments and regulators must adopt policies that protect our privacy and security. Find out more below!

The security of our devices, applications and infrastructure is paramount to the safe functioning of our digital lives. Good security enables trust in our systems, it is fundamental to protecting the critical information we store and exchange through networks and devices. Similar to how we physically secure our homes, offices and schools, securing devices and software allows us to operate in safe and trusted environments where our security is guaranteed and protected.
Security for information technology is particularly important as digital identities can, without adequate protection, be duplicated and abused with ease. Imagine what someone with access to your personal email address and favourite messaging app could do. Those are only two parts of your digital identity and yet the amount of information they would have access to, and the damage they could create, is immense. Worse, damage could be done without you realising it, as service providers expect people to be accessing email and messaging apps from multiple devices.
Most of our previous work on cyber security has focused on vulnerabilities in the software (ie the code that runs on a device and gives it instructions to perform as intended). But security vulnerabilities can also arise at the hardware level which includes the actual physical electronic components and the firmware (ie a different type of software programmed into certain components to help them operate effectively). Just like a security guard at a hotel is ineffective if all the windows and back doors are wide open, software security is only effective if the hardware it runs on is secure. That includes the devices in our hands as well as huge parts of our infrastructure that can be invisible to us: undersea cables, internet exchange points, even the routers in our house. Hardware plays a role as important as software in enabling our security.
To better understand why hardware security matters, its position in our modern infrastructure, and how it impacts us, we will zoom in on one of its most important components, the integrated circuit.
Integrated Circuits
You are probably familiar with the idea that a component called a ‘chip’ or a ‘microchip’ can be found at the heart of so many of our devices, present both in the simplest electronic gadget and in cutting edge technologies. These chips are ‘integrated circuits’: they are a small piece of technology that has revolutionised our societies.
These small chips of silicon, hidden inside our devices, perform mathematical operations that power our technology and drive innovation. Integrated circuits are the engine that make so much of our lives possible. They form a critical part of our infrastructure.
This piece will explore the origins of integrated circuits and their pivotal role in geopolitics, tech and innovation. It will examine questions that surround the development, manufacturing, commmercialisation and use of microchips, looking particularly at the security tensions of their design and production and the potential impact on our lives when their security fails.
The cornerstone of the tech revolution
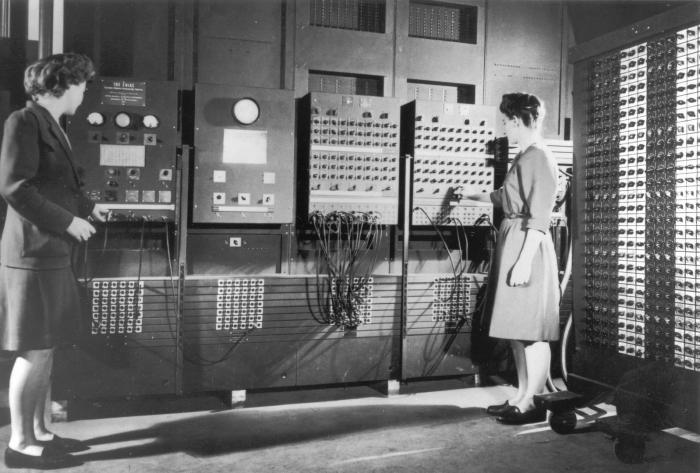
Invented in the late 50s and commercialised in the early 60s, integrated circuits revolutionised how electronic components (such as transistors) could be etched onto a piece of semi-conductor material (ie a material that sits between a electrical conductor and an isolator) to perform mathematical operation. Compared to the previous way of doing it (think gigantic machines relying on flimsy vacuum tubes such as the ENIAC, microchips brought fundamental advantages in terms of performance, cost and size.
The density of microchips compared to the mechanical methods that proceeded them allowed for the development of more complex mathematical processing, at a fraction of the size and cost. Microchips could also be specialised to do specific tasks, be it maths, information storage or logic and then be chained together to do ever more sophisticated tasks. Microchips today are a key component in everything from radio-frequency modulation and transmission (like you would find in a wifi device) to graphics rendering. Their mathematical computations underpin almost every aspects of our lives.
Advantages of the integrated circuits in chips over circuits that use discrete components include:
- They are much smaller. For example, modern Central Processing Units (CPUs) are integrated circuits that have billions of transistors in a package smaller than 4x4cm (Apple’s M2 has 134 billions for example), something that would be impossible using discrete components.
- Performance is also increased on integrated circuits as they can incorporate many different components close together and consume less power.
- They can be mass-manufactured using photolitography (ie the process enabling the etching of electronic components).
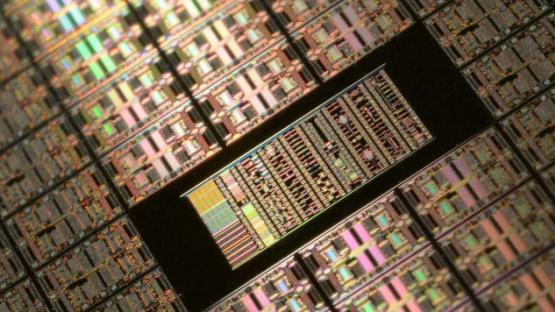
The following images help visualise the differences between a circuit made of a limited number of discrete components and an integrated circuit with hundreds or thousands of transistors.
Despite their many advantages, developing and producing integrated circuits required and still requires significant initial investment. Its cost advantage exists only when it is produced at scale and the first integrated circuits were costly and far from the optimised version we have now. But with the cold war raging in the late 50s and the success of the USSR space programme sending Sputnik and Yuri Gagarin to space, the United States invested into the nascent technology, first through NASA and then through the military, allowing it to further develop.
For a deep dive into the history of microchips, have a look at “Chip War” by Chris Miller
Following this initial spurt of funding and trust in the 60s, other countries and sectors started adopting, researching and developing microchips, eventually making them a core component of many industries, from Texas Instruments’ first laser guided bomb to IBM’s first personal computer.
The success of integrated circuits is in part because the possibilities they offer allow for infinite potential applications. Chips indeed offer the ability to store information and perform binary operations very quickly and at a large scale which can be leveraged to make them handle complex tasks. With integrated circuits, one can calculate weather forecasts in real time or display and animate three-dimensional objects on a screen, process data from a sensor interpret it, things that require processing a lot of information really fast. Application specific integrated circuits (ASICs) have been developed that are optimised for particular tasks, but other chips can be used for many different computational tasks and roles.
Consequently, by the 90s, integrated circuits could be found in many everyday objects. The growth of the internet greatly increased demands for these powerful chips that act as the brain of personal computers and servers. Thanks to this development and other similarly important demands in markets at different times, microchips have roughly followed Moore’s law and doubled their number of transistors every two years, making increasingly powerful chips available and promising even more power with each generation.
“Moore’s law” is based on a prediction from Gordon Moore concerning the ability of the industry and research to double the transistor count of microchips every two years. It is an economic rule of thumb that has proved reliable in part because of competition and partially through becoming a self-fulfilling prophecy.
In 2025, chips are virtually everywhere: it’s almost impossible to buy a household appliance without a microchip in it, and they are incredibly diverse, with many being ASICs, be it in your washing machine or your Television. Up to 3000 chips can be found in a car, they are in batteries for power management, in cameras, medical devices, audio effect pedals… Some are small, simple, cheap and easily available, designed for very basic purpose such as to amplify a signal. Others are incredibly complex and expensive and fill the rack of data centers to run highly resource consuming processes like the highly in demand Nvidia H100 used by many generative AI tech companies.
With this picture in mind, we can see how important and ubiquitous chips have become. But what integrated circuits are used for is only the first part of the story. How they are developed, produced, licensed and traded is where the real challenges and concerns for our privacy and security come in.
The global microchip supply chain
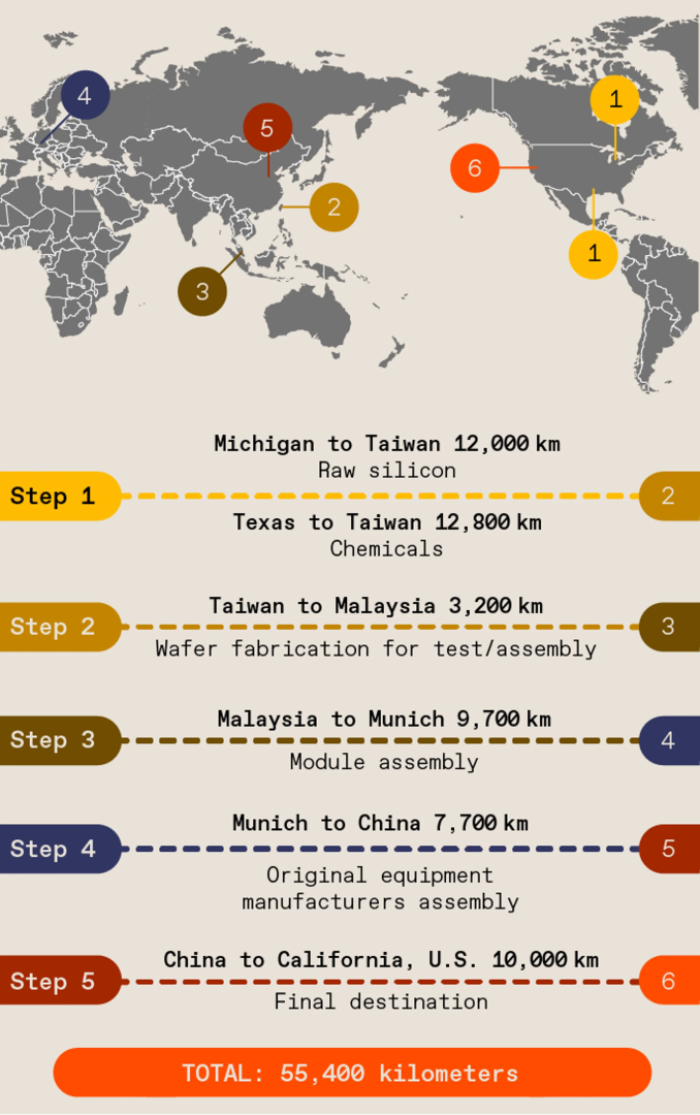
There are a number of particularities of the modern supply chain behind integrated circuits that give rise to challenges for privacy and security.
First is their globalised nature. As with many modern industries, the complex process to produce a microchip is broken down into different steps, such as the extraction of silicon, the production of silicon wafers (on which modern chip are built), the design of microchips, the design of machinery used to produce microchips, the licensing of instruction sets architecture and so on and so forth. Different regions and countries have specialised in these different steps, meaning that the supply chain is truly global.
Directly related to this globalised supply chain is the high concentration of expertise. For example, China is by far the main producer of silicon. ASML, a Dutch company, is the only company able to produce the USD380M photolitography machines used to produce cutting edge chips (etching transistors that are smaller than 10nm!). The Taiwan Semiconductor Manufacturing Company (TSMC) is the undisputed leader in manufacturing these cutting edge chips using ASML machines (among other things), and does so for all the biggest chip companies. Meanwhile the design of the chips themselves is not something TSMC has expertise on: that is up to its clients, including Nvidia, Apple, Intel, and AMD.
This concentration means there is a very high barrier to entry, particularly with regard to the production of complex cutting edge chips. Costs depend on the need for R&D and the scale of production (you need to produce a massive quantity of powerful and high quality chips to repay the costs of research and development, acquisition of machines, raw materials, labour etc.).
Some chips that rely on open standards can be mass produced using old manufacturing techniques (eg the 555 timer chip). These can be extremely cheap to produce and so adopted by a larger number of players, but they don’t provide nearly the same complex computing power as higher end chips.
The complexity of the microchip supply chain creates a wide attack surface for potential threats. Security vulnerabilities can emerge at different steps, from a mistake in the design of a chip, to a targeted attack by an adversary in a manufacturing plant, to interception and interference in the shipping process. There are many links in the chain where opportunities for interference or exploitation arise, and understanding each of those links requires a high degree of specialism.
Such a complex supply chain is also part of the reason we saw a shortage of microchips during the covid-19 pandemic. Increase in demand for consumer electronics and medical devices coupled with the impact of restrictions on sourcing of raw material, manufacturing and the trade restrictions between US and China translated into a massive shortage impacting every industry.
Security and privacy challenges
Integrated circuits are a prime target for attack because they are at the heart of how our devices process information and at the physical core of so much of our crucial infrastructure. Whether the goal is to be able to control the device remotely, to access or modify the information it processes, to inject false information, or to make the device inoperable, the success of an attack will depend on how secure the chip and its firmware (the software that controls it) are.
Meltdown and Spectre are two famous examples of vulnerabilities in modern processors that are tied to modern chip design and that affected almost all existing CPUs at their time of discovery. These two vulnerabilities, disclosed simultaneously in 2018, revealed a problem with a specific feature in the CPU design (“speculative execution”, where the processor runs ahead of the code to precompute what calculations are likely to be done next). This had the side effect of enabling unauthorised processes to infer and access information stored on the CPU’s cache. Concretely, this meant that all CPUs with this feature (mostly, but not limited to, Intel CPUs) were vulnerable to attacks accessing its memory, which could include sensitive data such as passwords, emails, photos and more.
The vulnerability has now been patched through OS updates, but at the cost of significant performance loss (of 2 to 14 percent). The loss in performance happens when precomputation is disabled, resulting in a wait while computation takes place, and because of additional checks to make sure that memory hasn’t been accessed without authorisation.
There is now a whole class of vulnerablities that seek to exploit speculative execution (and/or branch prediction, as well as other privileged entry points to chips such as the baseband, which manages communication functions and hyperthreading (a method of improving performance devised by Intel, which has now been dropped from their latest consumer processors). Vulnerabilities like these have long forced CPU designers to implement both hardware and software changes to the design of their CPU to mitigate against them.
Cases like Meltdown and Spectre illustrate how the security of chips against vulnerabilities is of the utmost importance to consumers and governments alike. For governments, it can be a matter of national security that ends up guiding wider policy (for example, in export control, with the US preventing China from acquiring cutting edge chips). The high complexity of some modern chip designs and the associated software is driving concern around foreign state interference. We can see how high this tension is with the bans on manufacturers such as Huawei because of concerns about chips designed and manufactured in China and the disputed Bloomburg story on SuperMicro servers.
A Huawei 5G antenna such that was banned by Japan, Sweden, Austria, Poland and more countries due to security concerns - image from Huawei
Integrated circuits are also used extensively by states in military contexts where they can enable technical superiority (as was the case for the US during the Gulf War with laser guided bombs like the Paveway). Military integrated circuits can be either a critical asset (including through the ability to hack an adversary) or a dangerous liability (by being the target of a hack).
But there can be a tension between the interest of national security and the security of individuals. Governments might have an incentive to discover or build vulnerabilities in the design of their chips for military advantage and surveillance (or lean heavily on companies that do for other state actors). But this exposes their own infrastructure and population to the risk of attack. Indeed, once a backdoor exists, it might be found and exploited by others, and the embedded nature of microchips make it hard to rectify or fix.
Not dissimilar to the “breaking” encryption debate
The growing demand for IoT and smaller, less advanced chips that can be mass manufactured at a low cost also represent a great security risk. Those chips might be perceived as less critical that a cutting edge CPU or GPU but can be leveraged by an attacker to access sensitive information, as was demonstrated with the MediaTek chip vulnerability, which gave access to a device’s microphone and camera. Yet, due to their lower costs and seemingly less important role, the security of those chips is often subject to less scrutiny, opening the door to vulnerabilities that affect millions.
At the other end of the spectrum, with more complex chips comes a certain obscurity as to what part of the chip does what. For example, in 2013, GCHQ demanded that journalists at the Guardian destroy their laptops on which were stored files leaked by Edward Snowden. While you might think that destroying the hard drives and memory should be enough as those are the components designed to store information, GCHQ requested that all chips be destroyed, as even the controllers for the keyboard or trackpad could store information to some extent.
Why we need security and privacy by design
Understanding the components that form our devices and infrastructure, as well as how they function and how they are produced, is critical to be able to effectively promote and defend security. Privacy and security go hand in hand: secure devices and infrastructure limits the surveillance capabilities of states and malicious actors.
- Refrain from exploiting vulnerabilities that undermine security and privacy of everyone.
- Uphold safeguards against unlawful surveillance, including safeguards against government hacking
- Require companies to disclose security vulnerabilities quickly, transparently and responsibly.
- Enact and enforce laws requiring companies to provide software and security updates for the full lifecycle of devices.
- Support the development of security standards in multistakeholder environments to promote security and privacy by design.
Being able to trust the security of our devices is a cornerstone of our digital and physical lives and paramount to being able to protect ourselves against harmful actors. The complex and multifaceted potential attack surface for integrated circuits means this is something that governments, institutions, and companies across the world must take seriously.