New U.K. Law Fails European Court Standards on Mass Interception Disclosed by Snowden
This piece was originally published in Just Security.
Earlier this month, the European Court of Human Rights issued a major judgment in three consolidated cases challenging the U.K. government’s mass interception program, which was first revealed by Edward Snowden in 2013. That judgment finds notable deficiencies in the legal framework governing mass interception, rendering the program unlawful under Articles 8 and 10 of the European Convention on Human Rights (ECHR), which protect the rights to privacy and freedom of expression.
The response of the U.K. government has been to point to new surveillance legislation – the Investigatory Powers Act 2016 (IPA) – passed during the course of the proceedings, which it asserts fixes the flaws identified by the Court. David Omand, a former director of the Government Communications Headquarters (GCHQ), the U.K. signals intelligence agency, similarly dismissed the judgment on the grounds that “[i]t tells us very little new since parliament had already accepted the need to tighten up the regulation of bulk powers.”
But the particular failings identified by the Court persist in the U.K.’s new surveillance framework. Those failings relate to how GCHQ (1) selects the “bearers” within fiber optic cables for interception, (2) searches communications obtained from those cables, (3) examines communications-related metadata, and (4) searches and examines information subject to journalistic privilege.
The U.K.’s Mass Interception Program
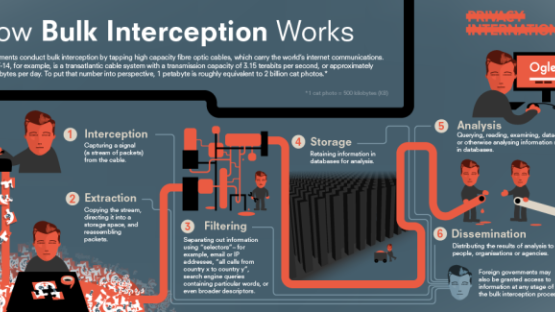
GCHQ conducts mass interception of internet traffic by tapping the undersea fiber optic cables landing in the U.K. Fiber optic cables contain fibers that carry internet traffic, and those fibers in turn carry “bearers.” GCHQ has described “bearers” as being “analogous to different television channels – there are various ways of feeding multiple bearers down a single optical fibre, with the commonest being to use light of different frequencies.”
GCHQ selects bearers to intercept, then directs a copy of intercepted internet traffic to buffers, which are temporary storage spaces that reportedly retain content for three days and metadata for 30 days. This information is then filtered and searched according to “selectors” and “search criteria.” The U.K. government has provided email addresses and telephone numbers as common examples of “selectors,” but the full scope of permissible selectors is not known. And we know even less about what can constitute “search criteria.”
Intercepted information is stored in databases, which analysts can query, data-mine, or use to call up information to examine further. In September 2015, a new disclosure of Snowden documents revealed three GCHQ programs, which shed light on the ways in which the U.K. government uses the mass interception of metadata. One program is Black Hole, a metadata repository storing “email and instant messenger records, details about search engine queries, information about social media activity, logs related to hacking operations, and data on people’s use of tools to browse the internet anonymously,” according to The Intercept. Another program, Mutant Broth, sifts through Black Hole data related to cookies – which are stored on devices to identify and track people browsing the internet – to monitor internet use and uncover online identities. The third program cited in the disclosed material is Karma Police, which the documents say “aims to correlate every user visible to passive SIGINT with every website they visit, hence providing either (a) a web browsing profile for every visible user on the internet or (b) a user profile for every visible website on the internet.”
The Court’s Findings on the Mass Interception Program
1. The Violation of the Right to Privacy under Article 8
The European Court of Human Rights held that the U.K. government’s mass interception program, authorized under section 8(4) of the Regulation of Investigatory Powers Act 2000 (RIPA), violated Article 8 of the ECHR in two key respects. First, the process for selecting “bearers” and filtering and searching communications lacked “safeguards…sufficiently robust to provide adequate guarantees against abuse” (§ 347). Second, the program lacked “any real safeguards” for selecting communications-related metadata for examination (§ 387).
a. “Bearers,” “Selectors,” and “Search Criteria”
With respect to “bearers,” while the Court concluded that “the safeguards governing the[ir] selection…for interception” were not “sufficiently robust,” it provided little guidance as to what those safeguards should entail (§ 347). Its only recommendation comes in its citation to a report by the Intelligence and Security Committee (ISC) of Parliament, produced in the aftermath of the Snowden revelations, which noted that neither Ministers nor Commissioners “have any significant visibility” of the selection of bearers. The ISC further recommended “retrospective review or audit” of this process. The Court agreed that, “[a]s the ISC observed, it would be desirable for the criteria for selecting the bearers to be subject to greater oversight by the Commissioner.” (§ 338)
The Court’s criticism of the process for filtering and searching communications using “selectors” and “search criteria” was significantly more pointed. In particular, it suggests that this process should be subject to some form of ex ante independent or judicial oversight.
For instance, the Court noted that the “certification by the Secretary of State,” which accompanies any warrant to authorize mass interception, sets out “categories…in very general terms (for example, ‘material providing intelligence on terrorism…’).” The Court observed that “it would be highly desirable for the certificate to be expressed in more specific terms” (but the ruling clarified that the specific “selectors” and “search criteria” themselves do not “necessarily need to be listed in the warrant”) (§§ 340, 342).
The Court also noted with dismay that “the only independent oversight of the process of filtering and selecting intercept data for examination is the post factum audit by the Interception of Communications Commissioner.” It concluded that, “[i]n a bulk interception regime, where the discretion to intercept is not significantly curtailed by the terms of the warrant, the safeguards applicable at the filtering and selecting for examination stage must necessarily be more robust.” (§ 346)
b. Communications-Related Metadata
The Court also found unacceptable that the U.K. government’s mass interception regime permits “related communications data of all intercepted communications – even internal communications [(i.e. communications of persons in the UK)] incidentally intercepted as a ‘by-catch’” to be “searched and selected for examination without restriction.” (§ 348) Notably, the Court rejected the government’s assertion that “the acquisition of related communications data is necessarily less intrusive than the acquisition of content.” (§ 349) The Court explained:
“For example, the content of an electronic communication might be encrypted and, even if it were decrypted, might not reveal anything of note about the sender or recipient. The related communications data, on the other hand, could reveal the identities and geographic location of the sender and recipient and the equipment through which the communication was transmitted. In bulk, the degree of intrusion is magnified, since the patterns that will emerge could be capable of painting an intimate picture of a person through the mapping of social networks, location tracking, Internet browsing tracking, mapping of communication patterns, and insight into who a person interacted with…” (§ 356).
The Court found specifically unlawful the U.K. government’s exemption of communications-related metadata from safeguards set out in section 16 RIPA. Those safeguards generally require that “intercepted material is read, looked at or listened to…[only] to the extent” that it is not “referable to an individual who is known to be for the time being in the British Islands.” In other words, they protect the communications of persons within the U.K. from the mass interception regime, “since persons of interest to the intelligence services who are known to be in the British Islands could be subject to a targeted warrant under section 8(1) of RIPA.” (§ 343)
The Court concluded that the exemption of metadata from this safeguard does not strike “a fair balance between the competing public and private interests” and should be limited only “to the extent necessary to determine whether an individual is, for the time being, in the British Islands.” (§ 357)
2. The Violation of the Right to Freedom of Expression under Article 10
The Court extended and amplified its criticisms about “the lack of transparency and oversight of the criteria for searching and selecting communications for examination” in the context of journalistic communications. It noted:
“[I]t is of particular concern that there are no [public] requirements…either circumscribing the intelligence services’ power to search for confidential journalistic or other material (for example, by using a journalist’s email as a selector), or requiring analysts, in selecting material for examination, to give any particular consideration to whether such material is or may be involved. Consequently, it would appear that analysts could search and examine without restriction both the content and the related communications data of these intercepted communications.” (§ 493)
The Court indicated that there should be “arrangements limiting the intelligence services’ ability to search and examine such material other than where ‘it is justified by an overriding requirement in the public interest.’” (§ 495) And it suggested that there should be “sufficient safeguards relating both to the circumstances in which they may be selected intentionally for examination, and to the protection of confidentiality where they have been selected, either intentionally or otherwise.” (§ 492) Unfortunately, however, the Court articulated no additional guidance in its decision, including what those safeguards might look like in practice.
The Investigatory Powers Act Fails to Fix the Problems
1. “Bearers,” “Selectors,” and “Search Criteria”
Before delving into the details of whether the IPA has anything to say about the authorization and oversight of “bearers,” “selectors,” and “search criteria” (spoiler alert, it doesn’t), it’s worth stepping back and considering how these processes are set out more generally within the U.K.’s new surveillance framework.
The U.K. government has coined the phrase “double lock” to describe its new authorization process for approving certain surveillance powers, including mass interception. But the supposed “double lock” is really just a single lock and that lock is not especially secure.
As with the prior mass interception regime under RIPA, the IPA preserves the power of the Secretary of State to issue warrants. From a human rights perspective, the Secretary of State’s involvement is not a lock because, as a member of the executive branch, the Secretary of State lacks the necessary independence.
And while the IPA permits Judicial Commissioners to “approve” this decision, there remain significant questions about the scope of scrutiny they may exercise in reviewing warrants. For example, section 140 of the IPA provides that Judicial Commissioners must “review the Secretary of State’s conclusions” on whether a warrant is necessary and proportionate and “apply the same principles as would be applied by a court on an application for judicial review.” Debate continues to swirl around what the “judicial review” standard will mean in practice, especially in the context of bulk warrants.
As for oversight, the IPA provides for an Investigatory Powers Commissioner, who has replaced the prior Interception of Communications Commissioner, the Chief Surveillance Commissioner, and the Intelligence Services Commissioner. The consolidation of oversight under a single Commissioner is a welcome improvement. But what that oversight will look like in practice remains subject to some speculation. The IPA speaks in broad, sweeping terms, providing that the new Commissioner “must keep under review” the various surveillance powers authorized by the IPA (section 229).
So at least with respect to the face of the IPA itself, it has absolutely nothing to say about whether there should be ex ante authorization or ex post oversight of “bearers,” “selectors,” and “search criteria.” And what the above digression reveals is that the very structure of the new authorization process raises serious questions as to how it would function as a vehicle for reviewing issues at the granularity of “selectors” and “search criteria.” Whether the selection of “bearers” becomes a subject of the oversight activities of the new Investigatory Powers Commissioner is a development we can only wait to observe.
2. Communications-Related Metadata
The IPA treats communications-related metadata similarly to RIPA, with one exception. Like RIPA, it generally adds another layer of safeguards for the communications content of persons known to be in the U.K. but does not extend those protections to the metadata attached to such communications. The perpetuation of this distinction is even more troubling considering that the IPA, unlike RIPA, provides that certain content, in and of itself, can be extricated from intercepted communications and treated as metadata (section 137(5) IPA).
The IPA does provide that the selection for examination of metadata – as with content – now must be for a stated operational purpose (section 152 IPA). But those purposes are exceedingly broad and simply those “specified in a list maintained by the heads of the intelligence services…as purposes which they consider are operational purposes for which intercepted content or secondary data…may be selected for examination” (section 142(4) IPA). In any event, this safeguard falls far short of what the Court indicates is necessary, which is to subject the communications content and metadata of persons in the U.K. to the same protections except for when examining metadata for the purpose of “determin[ing] whether an individual is, for the time being, in the British Islands.” (§ 357)
3. Confidential Journalistic Material
The IPA contains a single safeguard related to “confidential journalistic material” in the section devoted to mass interception – that where such a communication “is retained, following its examination, for purposes other than [its] destruction,” the agency “must inform the Investigatory Powers Commissioner” (section 154 IPA). The Interception of Communications Code of Practice provides some additional guidance. Where an analyst intends to select for examination confidential journalistic material (or content “in order to identify or confirm a source of journalistic information”), “he or she must notify a senior official” outside of the agency who “may only approve…if he or she considers that the Agency has arrangements in place for the handling, retention, use and destruction” of such communications (paras. 9.84, 9.86).
Neither of these safeguards satisfy the requirements set out in the Court’s ruling. First, the Court indicates that such communications should be selected for examination only where “justified by an overriding requirement in the public interest,” and no such assessment is built into the safeguards described above. Second, the Court provides that there should be safeguards both for “the circumstances in which [confidential journalistic material] may be selected intentionally for examination, and to the protection of confidentiality where they have been selected.” The safeguards described above do not address the latter; while the Code of Practice “handling” safeguard could potentially encompass this point, it does not appear sufficiently clear. Moreover, it remains questionable whether authorization by a “senior official” (who would appear to be someone designated by the Secretary of State for that purpose) is appropriate, as opposed to an independent authority.
Intelligence Sharing and the IPA
The Court’s judgment did not just address the U.K. government’s mass interception program but also its access to information collected by foreign intelligence agencies, including the U.S. National Security Agency. That part of the judgment explicitly articulated, for the first time, that where a government obtains information through such access, the interference with the right to privacy is equivalent to obtaining that information through direct surveillance.
The Court held that such a regime, like any direct surveillance regime, must therefore “be ‘in accordance with the law’…, proportionate to the legitimate aim pursued, and [provide] adequate and effective safeguards against abuse.” It added that “[i]n particular, the procedures for supervising the ordering and implementation of the measures in question must be such as to keep the ‘interference’ to what is ‘necessary in a democratic society.’” (§ 422)
Unfortunately, the Court’s judgment sanctions the U.K.’s intelligence-sharing regime, despite the fact that it falters under these very principles, both under RIPA and the IPA. RIPA had nothing to say about intelligence sharing. But the Court nevertheless found the “statutory framework” governing this activity sufficient because the U.K. government had disclosed a “note” during the domestic proceedings purporting to lay out the rules governing intelligence sharing. Never mind that the note consisted of 2 pages, with no heading, no author, and no indication of whether it represented an actual policy, part of a policy, a summary of a policy, or a summary of submissions made by the U.K. government during a closed hearing on the issue.
The Court also made much of the fact that the note was substantially reproduced in the Interception Communications Code of Practice. But the language of the note and Code of Practice remain woefully inadequate. Notably, both speak of the U.K. government making a “request” for “unanalyzed intercepted communications content (and secondary data).” The concept of “request” is an antiquated one that fails to address the manner in which intelligence agencies swap information in the digital age, for example, by offering direct and unfettered access to raw data intercepted in bulk or databases of material collected in bulk. No “request” is required in such circumstances.
The IPA suffers from the same deficiencies and more. Only one provision explicitly addresses the U.K. government’s access to foreign intelligence information. That provision (section 9 IPA) provides that the U.K. may not “request” foreign authorities to “carry out the interception of communications sent by, or intended for” a person in the U.K. unless an appropriate warrant has been issued. Thus, this provision again focuses on “requests” by the U.K. to foreign authorities. It is also limited to the interception of communications related to a person in the U.K.
Finally, the Court, perhaps because of its basic misunderstanding of the nature of modern intelligence sharing, essentially sanctions aspects of the U.K.’s mass interception framework as it applies to intelligence sharing, even as it found that very framework unlawful. It notes that “those requirements which relate to…storage, examination, use, onward dissemination, erasure and destruction” in the direct surveillance context must also “be present” in the intelligence sharing regime (§ 423). And yet, it found no need to extend its concerns about how the U.K. government filters and searches bulk intercept material to how it might similarly filter and search databases of bulk intercept material maintained under a foreign government’s mass surveillance program.
*****
In the coming months, the U.K. government is likely to continue to trot out the passage of the IPA as evidence that its mass interception program now rights the failings identified by the Court. As discussed above, that claim falters against a close reading of the IPA.
The U.K. is far from the only country to operate a mass interception program. The U.S. operates analogous programs, as do several Council of Europe members. The Court’s judgment provides a new and important guidepost for evaluating these programs as well.



