Search
Content type: Examples
UK: O2 shares aggregated location data with government to test compliance with distancing guidelines
Mobile network operator O2 is providing aggregated data to the UK government to analyse anonymous smartphone location data in order to show people are following the country's social distancing guidelines, particularly in London, which to date accounts for about 40% of the UK's confirmed cases and 30% of deaths. The project is not designed to monitor individuals. Lessons from the impact on London of travel restrictions could then be applied in the rest of the country. The government says it has…
Content type: Examples
BT, owner of UK mobile operator EE, is in talks with the government about using its phone location and usage data to monitor whether coronavirus limitation measures such as asking the public to stay at home are working. The information EE supplies would be delayed by 12 to 24 hours, and would provide the ability to create movement maps that show patterns. The data could also feed into health services' decisions, and make it possible to send health alerts to the public in specific locations.…
Content type: Examples
The coronavirus action plan announced on March 3, alongside many measures for managing the NHS in the crisis, will also allow the Investigatory Powers Commissioner to appoint judicial commissioners (JCs) on a temporary basis in the event that there are insufficient JCs available to operate the system under the Investigatory Powers Act 2016. The Home Secretary, at the request of the Investigatory Powers Commissioner, will also be allowed to vary the time allowed for urgent warrants to be…
Content type: Long Read
Commercial interests seem to often overshadow the EU’s stance as a global privacy leader. After looking at Europes's shady funds to border forces in the Sahel area, Niger's new biometric voting system, and attempts to dismantle smugglers networks powered by Europe's gifts of surveillance, freelance journalist Giacomo Zandonini looks at the battle for data protection and digital rights in the continent.
What do a teenage labourer on a marijuana farm in Lesotho, a…
Content type: Long Read
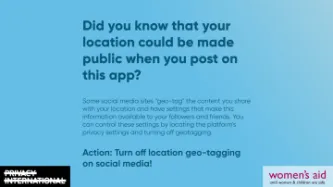
Valentine’s Day is traditionally a day to celebrate relationships, but many relationships that begin romantically can quickly become controlling, with partners reading emails, checking texts and locations of social media posts. This can be just the beginning.
Today, Friday 14th February, Privacy International and Women’s Aid are launching a series of digital social media cards giving women practical information on how to help stay safe digitally from control and abuse.
Did you know…
Content type: News & Analysis
In mid-2019, MI5 admitted, during a case brought by Liberty, that personal data was being held in “ungoverned spaces”. Much about these ‘ungoverned spaces’, and how they would effectively be “governed” in the future, remained unclear. At the moment, they are understood to be a ‘technical environment’ where personal data of unknown numbers of individuals was being ‘handled’. The use of ‘technical environment’ suggests something more than simply a compilation of a few datasets or databases.
The…
Content type: News & Analysis
Today Advocate General (AG) Campos Sánchez-Bordona of the Court of Justice of the European Union (CJEU), issued his opinions (C-623/17, C-511/18 and C-512/18 and C-520/18) on how he believes the Court should rule on vital questions relating to the conditions under which security and intelligence agencies in the UK, France and Belgium could have access to communications data retained by telecommunications providers.
The AG addressed two major questions:
(1) When states seek to impose…
Content type: Case Study
On 3 December 2015, four masked men in plainclothes arrested Isnina Musa Sheikh in broad daylight (at around 1 p.m.) as she served customers at her food kiosk in Mandera town, in the North East of Kenya, Human Rights Watch reported. The men didn’t identify themselves but they were carrying pistols and M16 assault rifles, commonly used by Kenyan defence forces and the cars that took her away had their insignia on the doors. Isnina’s body was discovered three days later in a shallow grave about…
Content type: Case Study
The prohibition against torture is absolute. There are no exceptional circumstances whatsoever which can be used to justify torture.
And yet, torture is still being carried out by state officials around the world, driven by states’ ability to surveil dissidents, and intercept their communications.
In 2007, French technology firm Amesys (a subsidiary of Bull) supplied sophisticated communications surveillance systems to the Libyan intelligence services. The systems allegedly permitted the…
Content type: Case Study
In the Xingjiang region of Western China, surveillance is being used to facilitate the government’s persecution of 8.6million Uighur Muslims.
Nurjamal Atawula, a Uighur woman, described how, in early 2016, police began regularly searching her home and calling her husband into the police station, as a result of his WeChat activity.
WeChat is a Chinese multi-purpose messaging, social media and mobile payment app. As of 2013, it was being used by around 1million Uighurs, but in 2014 WeChat was…
Content type: Case Study
The way digital technologies are deployed has radically influenced the distribution of power in our societies. Digital information can be created, transmitted, stored and distributed far more easily and cheaply than ever before, on a scale that was previously unimaginable. This information is power in the hands of those that know how to use it. Governments and companies alike have been racing to occupy as much space as possible, increasing their surveillance and their knowledge about each and…
Content type: News & Analysis
This creates a restraint on all people who merely seek to do as people everywhere do: to communicate freely.
This is a particularly worrying development as it builds an unreliable, pervasive, and unnecessary technology on top of an unnecessary and exclusionary SIM card registration policy. Forcing people to register to use communication technology eradicates the potential for anonymity of communications, enables pervasive tracking and communications surveillance.
Building facial recognition…
Content type: Advocacy
On November 1, 2019, we submitted evidence to an inquiry carried out by the Scottish Parliament into the use of Facial Recognition Technology (FRT) for policing purposes.
In our submissions, we noted that the rapid advances in the field of artificial intelligence and machine learning, and the deployment of new technologies that seek to analyse, identify, profile and predict, by police, have and will continue to have a seismic impact on the way society is policed.
The implications come not…
Content type: News & Analysis
Photo by Francesco Bellina
The wars on terror and migration have seen international funders sponsoring numerous border control missions across the Sahel region of Africa. Many of these rely on funds supposed to be reserved for development aid and lack vital transparency safeguards. In the first of a series, freelance journalist Giacomo Zandonini sets the scene from Niger.
Surrounded by a straw-yellow stretch of sand, the immense base of the border control mobile company of Maradi, in southern…
Content type: News & Analysis
Today, the High Court of South Africa in Pretoria in a historic decision declared that bulk interception by the South African National Communications Centre is unlawful and invalid.
The judgment is a powerful rejection of years of secret and unchecked surveillance by South African authorities against millions of people - irrespective of whether they reside in South Africa.
The case was brought by two applicants, the amaBhungane Centre for Investigative Journalism and journalist Stephen…
Content type: News & Analysis
Photo: The European Union
On 2 September 2019, Privacy International, together with 60 other organisations, signed an open letter to the European Parliament to express our deep concern about upcoming EU policy proposals which undermine the EU’s founding values of human rights, peace and disarmament.
Since 2017, the EU has diverted funds towards security research and security capacity-building in countries around the world. The proposal for the EU's next budget (2021-2027) will…
Content type: Report
“...a mobile device is now a huge repository of sensitive data, which could provide a wealth of information about its owner. This has in turn led to the evolution of mobile device forensics, a branch of digital forensics, which deals with retrieving data from a mobile device.”
The situation in Scotland regarding the use of mobile phone extraction has come a long way since the secret trials were exposed. The inquiry by the Justice Sub-Committee, commenced on 10 May 2018, has brought much…
Content type: Long Read
It is common ground that bulk collection of content would be a deprivation of the right to privacy. That is an inexcusable or unjustifiable step too far. Repeatedly the Government whether in litigation or legislating, has emphasised that they are not taking content in bulk. Content is the forbidden ground.
This has resulted in the Government seeking to explain, for example, what parts of an email would constitute content and meta data. Within the Investigatory Powers Act it has led to the…
Content type: Long Read
Six years after NSA contractor Edward Snowden leaked documents providing details about how states' mass surveillance programmes function, two states – the UK and South Africa – publicly admit using bulk interception capabilities.Both governments have been conducting bulk interception of internet traffic by tapping undersea fibre optic cables landing in the UK and South Africa respectively in secret for years.Both admissions came during and as a result of legal proceedings brought by Privacy…
Content type: Long Read
Imagine that every time you want to attend a march, religious event, political meeting, protest, or public rally, you must share deeply personal information with police and intelligence agencies, even when they have no reason to suspect you of wrongdoing.
First, you need to go to the police to register; have your photo taken for a biometric database; share the contacts of your family, friends, and colleagues; disclose your finances, health records, lifestyle choices, relationship status, and…
Content type: News & Analysis
According to the International Organization for Migration, an estimated 258 million people are international migrants – that is, someone who changes their country of usual residence, That’s one in every 30 people on earth.
These unprecedented movements levels show no sign of slowing down. It is predicted that by 2050, there will be 450 million migrants across the world.
Nowadays, it is politically acceptable to demonise migrants, and countless leaders have spewed divisive and xenophobic…
Content type: Long Read
Cellebrite, a surveillance firm marketing itself as the “global leader in digital intelligence”, is marketing its digital extraction devices at a new target: authorities interrogating people seeking asylum.
Israel-based Cellebrite, a subsidiary of Japan’s Sun Corporation, markets forensic tools which empower authorities to bypass passwords on digital devices, allowing them to download, analyse, and visualise data.
Its products are in wide use across the world: a 2019 marketing…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
In the era of smart cities, the gap between the internet and the so-called physical world is closing. Gone are the days, when the internet was limited to your activities behind a desktop screen, when nobody knew you were a dog.
Today, the…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
It is often communities who are already the most marginalised who are at risk because of the privacy invasions of data-intensive systems. Across the globe, we see the dangers of identity systems; the harms of online violence against women and the…
Content type: Impact Case Study
What HappenedOn 5 June 2013, The Guardian published the first in a series of documents disclosed by Edward Snowden, a whistleblower who had worked with the NSA. The documents revealed wide-ranging mass surveillance programs conducted by the USA’s National Security Agency (NSA) and the UK’s Government Communications Headquarters (GCHQ), which capture the communications and data of hundreds of millions of people around the world. In addition to revealing the mass surveillance programs of the NSA…
Content type: Advocacy
Este informe es presentado por Derechos Digitales, Ciudadano Inteligente, Fundación ProAcceso y Privacy International. Derechos Digitales es una organización no gubernamental de defensa, promoción y desarrollo de los derechos humanos en el entorno digital. Ciudadano Inteligente es una organización dedicada a fortalecer la democracia y reducir la desigualdad a través de la transparencia y la participación ciudadana. Fundación ProAcceso se dedica a la defensa del derecho de acceso a la…
Content type: Report
In December 2018, the National Coalition of Human Rights Defenders-Kenya published a report analysing the needs and concerns of human rights defenders (HRD) in relation to privacy, data protection and communications surveillance.
A summary of their findings is below. Access the full report on their website.
Content type: News & Analysis
This post was written by William Marks, a former volunteer at Privacy International.
The right to privacy is central to the protection of human dignity, and supports and reinforces other rights, such as the right to freedom of expression and association. Privacy International, supported by the International Human Rights Clinic at Harvard Law School, recently submitted a joint stakeholder report to the United Nations Human Rights Council regarding New Zealand’s protection of the right to…
Content type: Advocacy
This Universal Periodic Review stakeholder report is a submission by Privacy International presented to raise concerns regarding the situation of the violation of the right to privacy in New Zealand as part of the 32nd session of the Universal Periodic Review (UPR) Working Group.
Content type: News & Analysis
Our intervention comes on the back of mounting evidence that the South African state’s surveillance powers have been abused, and so-called “checks & balances” in RICA have failed to protect citizens’ constitutional right to privacy.
Among our core arguments are:
That people have a right to be notified when their communications have been intercepted so that they can take action when they believe their privacy has been unlawfully breached. Currently RICA prevents such notification, unlike…