Search
Content type: Report
Privacy International partnered with the International Human Rights Clinic at Harvard Law School to guide the reader through a simple presentation of the legal arguments explored by national courts around the world who have been tasked with national courts that discuss the negative implications of identity systems, particularly on human rights, and to present their judgement.
This argumentation guide seeks to fill that gap by providing a clear, centralised source of the arguments advanced in…
Content type: Report
Many countries in the world have existing ID cards - of varying types and prevalence - there has been a new wave in recent years of state “digital identity” initiatives.
The systems that states put in place to identify citizens and non-citizens bring with them a great deal of risks.
This is particularly the case when they involve biometrics - the physical characteristics of a person, like fingerprints, iris scans, and facial photographs.
Activists and civil society organisations around the…
Content type: Report
A common theme of all major pieces of national jurisprudence analyzing the rights implications of national identity system is an analysis of the systems’ impacts on the right to privacy.
The use of any data by the State including the implementation of an ID system must be done against this backdrop with respect for all fundamental human rights. The collection of data to be used in the system and the storage of data can each independently implicate privacy rights and involve overlapping and…
Content type: Report
Identity systems frequently rely on the collection and storage of biometric data during system registration, to be compared with biometric data collected at the point of a given transaction requiring identity system verification.
While courts have arguably overstated the effectiveness and necessity of biometric data for identity verification in the past, the frequency of biometric authentication failure is frequently overlooked. These failures have the potential to have profoundly…
Content type: Report
National identity systems naturally implicate data protection issues, given the high volume of data necessary for the systems’ functioning.
This wide range and high volume of data implicates raises the following issues:
consent as individuals should be aware and approve of their data’s collection, storage, and use if the system is to function lawfully. Despite this, identity systems often lack necessary safeguards requiring consent and the mandatory nature of systems ignores consent…
Content type: Report
While identity systems pose grave dangers to the right to privacy, based on the particularities of the design and implementation of the ID system, they can also impact upon other fundamental rights and freedoms upheld by other international human rights instruments including the International Covenant on Civil and Political Right and the International Covenant on Economic, Social and Cultural Rights such as the right to be free from unlawful discrimination, the right to liberty, the right to…
Content type: Report
Rather than providing a list of arguments, as is the case in the other sections of this guide, the fifth section provides a general overview describing the absence of consideration of these themes in existing jurisprudence and the reasons why these themes warrant future consideration including identity systems’ implications for the rule of law, the role of international human rights law, and considerations of gender identity.
Democracy, the Rule of Law and Access to Justice: This analysis of…
Content type: Key Resources
Content type: Video
You can listen and subscribe to the podcast where ever you normally find your podcasts:
Spotify
Apple podcasts
Google podcasts
Castbox
Overcast
Pocket Casts
Peertube
Youtube
Stitcher
And more...
Episode notes
Useful info
How to minimise targeted ads: privacyinternational.org/act/minimise-targeted-ads
Protect yourself from online tracking: privacyinternational.org/act/protect-yourself-online-tracking
Social media account settings: privacyinternational.org/act/protect-…
Content type: Explainer
The internet is filled with guides on how to file a Freedom of Information (FOI) request. Depending on the country you are in, it is likely that a local NGO – or your national freedom of information authority. – will have come up with one. The Global Investigative Journalism Network has an excellent list of FOI resources available in many countries across every continent. We really recommend you take a look at it; many of the FOI guides we love are in that repository.At PI we equally spend much…
Content type: Call to Action
You might have read our investigation into advertisers who upload your data on Facebook and found out some companies doing the same to you. Well, you can join us and hold them accountable by sending your own Data Subject Access Request (DSAR)!Before you get started we suggest you read our FAQ and take a look at our 7+1 tips to make the most out of your DSAR before and after.To do so you simply need to copy the message bellow and send it to the companies that uploaded your data despite…
Content type: Explainer
Hello friend,
You may have found your way here because you are thinking about, or have just submitted, a Data Subject Access Request, maybe to your Facebook advertisers like we did. Or maybe you are curious to see if Policing, Inc. has your personal data.
The right to access your personal data (or access right) is just one of a number of data rights that may be found in data protection law, including the European Union's General Data Protection Regulation, better known as "GDPR", which took…
Content type: Long Read
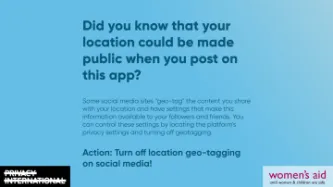
Valentine’s Day is traditionally a day to celebrate relationships, but many relationships that begin romantically can quickly become controlling, with partners reading emails, checking texts and locations of social media posts. This can be just the beginning.
Today, Friday 14th February, Privacy International and Women’s Aid are launching a series of digital social media cards giving women practical information on how to help stay safe digitally from control and abuse.
Did you know…