Search
Content type: Long Read
We are at a war footing as we enter an era where the tech world is increasingly defined by conflict. Innovation has never been driven solely by social needs, market forces or the common good. Military imperatives have periodically played central roles in steering the development of new generations of technologies. For instance, the origins of the internet can be traced back to defence research and initiatives like the ARPANET.Now we are witnessing a significant shift: states and corporations…
Content type: Long Read
What happened?On 19 July 2024, American cybersecurity company CrowdStrike released an update to its CrowdStrike Falcon software that ultimately caused 8.5 million computers running Microsoft Windows to crash. The damage done was both deep and wide: deep because the computers affected were unable to recover without direct user intervention. Wide because a whole range of companies - from airlines to healthcare to media - across a whole range of countries - from Sweden to India to New Zealand -…
Content type: Long Read
In 2019, the Waorani achieved a huge legal victory against the Ecuadorian government. They opposed the sale of millions of hectares of their rainforest to new oil companies, a forest that forms part of the home and territory of seven different Indigenous peoples in the southern Ecuadorian Amazon. Nemonte Nenquimo, as the first female leader of the Waorani of Pastaza and co-founder of the nonprofit Alianza Ceibo, and plaintiff in this case, has been a powerful advocate for her community’s…
Content type: Long Read
Education is a fundamental human right outlined in the Universal Declaration of Human Rights (Article 26), which states that everyone has the right to education. Schools play a core role in the education of children, but it’s also in schools that children are encouraged to learn to work with others, and to develop their own identities and emotional skills. The education process doesn’t stop there, it continues as children grow and make their way through different higher educational spaces such…
Content type: Long Read
Governments around the world are increasingly making registration in national digital ID systems mandatory for populations, justifying its need on a range of issues from facilitating access to services, to national security and fighting against corruption. This is an attempt to create a "foundational identity" for an individual, or "a single source of truth" about who someone is, according to a government agency. These identity systems are run by governments, sometimes by private companies, or…
Content type: Long Read
This piece was last updated in June 2021.
In many countries, access to social protection (such as welfare programmes or healthcare) is made conditional on producing a form of identification (“ID”). But obtaining a recognised and accurate ID is often a process riddled with discriminatory designs, bureaucracy and technical failures that prevent individuals from accessing the services they are entitled to. Even when people eventually get an ID, it might not accurately reflect who they are,…
Content type: Long Read
Now more than ever with a global pandemic happening, our lives are being shaped by our interaction with the digital world. Work meetings on Zoom followed by Skype with family before a quick run with your favourite running app and a Google search for your next meal: technologies and services offer us a lot and greatly improve our daily lives. But what's the real cost of these tools we rely on so much?
A lot of these companies, especially those offering free services, collect data about you. It…
Content type: Examples
Immunity passports would impose artificial restrictions on who can and cannot participate in social, civic, and economic activities, and create a perverse incentive for individuals, particularly those who can’t afford a period of exclusion, to seek out infection, posing a health risk to anyone they come into contact with. Both governments and individuals may be under pressure to return employees to the workforce, and immunity passports may lead governments to believe they have a quick fix that…
Content type: Explainer
Definition
An immunity passport (also known as a 'risk-free certificate' or 'immunity certificate') is a credential given to a person who is assumed to be immune from COVID-19 and so protected against re-infection. This 'passport' would give them rights and privileges that other members of the community do not have such as to work or travel.
For Covid-19 this requires a process through which people are reliably tested for immunity and there is a secure process of issuing a document or other…
Content type: Long Read
This research was commissioned as part of Privacy International’s global research into data exploitative technologies used to curtail women’s access to reproductive rights.
Read about Privacy International’s Reproductive Rights and Privacy Project here and our research findings here.
1. What are the barriers to access safe and legal abortion care?
Legal barriers
To identify the barriers experienced by women to access safe and legal abortion care, we have to understand the legal picture…
Content type: Case Study
In 2030 Amtis finds a future where property rights for data were adopted. Here’s how this future plays out:
My data, my turf. This was the first graffiti I saw as I was walking down the street and I said to myself, “Yeah, big corp, we’re going to get you good!”. I am fed up with companies making insane amounts of money from my data. If this is the game we’re playing, I want my fair share.
I was not the only one thinking like this. A few years back there was a strong push towards adopting…
Content type: Examples
Reports that Amazon is planning on launching a free ad-supported music service caused Spotify’s (the Swedish audio streaming platform) shares to fall 4% on Monday, April 15th. And, on April 18th, Amazon published a blog post where it announced that launch of Amazon’s free music-streaming service in the US. The ad-supported free service became available exclusively through Alexa, Amazon’s voice assistant programmed into Echo devices. It has been reported thatthe Alexa only launch…
Content type: Examples
In June 2018, a panel set up to examine the partnerships between Alphabet's DeepMind and the UK's NHS express concern that the revenue-less AI subsidiary would eventually have to prove its value to its parent. Panel chair Julian Huppert said DeepMind should commit to a business model, either non-profit or reasonable profit, and noted the risk that otherwise Alphabet would push the company to use its access to data to drive monopolistic profits. In that case, DeepMind would either have to…
Content type: Examples
Even after 2015, when Facebook said it had walled off user records from third parties, inside sources and court documents showed that the company went on maintaining a whitelist of companies that were allowed customised access to information about users' Friends, phone numbers, and a "friend link" metric that measured the degrees of separation. Whitelisted companies included Nissan and Royal Bank of Canada, and others that either advertised on the network or were valuable to Facebook for other…
Content type: Explainer
Introduction
Of all the data-intensive initiatives that a government can introduce, some of the largest are ID systems. They have implications across a broad range of human and civil rights. How do we begin to critique an ID system, to begin to understand its strengths and weaknesses? There are a series of issues that we believe should be addressed in the development of any ID system.
This could be of particular relevance to civil society organisations (CSOs): this is because civil…
Content type: Explainer
Photo credit: warrenski
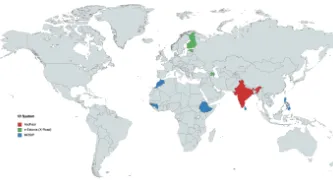
Mandatory SIM card registration eradicates the potential for anonymity of communications, enables location-tracking, and simplifies communications surveillance and interception. By facilitating the creation of an extensive database of user information, it places individuals at risk of being tracked or targeted, and having their private information misused. In the absence of comprehensive data protection legislation and judicial oversight, SIM users' information can be…
Content type: Examples
In May 2018, the ACLU of Northern California obtained documents under a FOIA request showing that Amazon was essentially giving away its two-year-old Rekognition facial recognition tools to law enforcement agencies in Oregon and Orlando, Florida. Amazon defended the move by saying the technology has many useful purposes, including finding abducted children and identify attendees at the 2018 wedding of Britain's Prince Harry and Meghan Markle. The company markets Rekognition as useful for…
Content type: Examples
In August 2018, two lawsuits, were filed against NSO Group, one brought in Israel by a Qatari citizen and the other in Cyprus by Mexican journalists and activists. All the plaintiffs had been targeted by the company's Pegasus spyware, which takes control of targets' phones when they click on links sent via carefully crafted phishing messages. The company claims that it sells the technology to governments on condition that they use it exclusively against criminals and it is not responsible for…
Content type: Examples
In August 2018, Facebook announced it would remove more than 5,000 ad targeting options in order to prevent discrimination. Options specifying the exclusion of people interested in "Passover", "Native American culture", or "Islam" could be used as proxies to allow advertisers to exclude ethnic and religious groups in contravention of the law. The announcement came shortly after the US Department of Housing and Urban Development filed a complaint alleging that the company had enabled…
Content type: Case Study
The exclusion caused by ID can have a devastating effect on people, limiting their opportunities and ability to survive.
Names have been changed.
Carolina is in a more privileged position than many other migrants, she admits that. She has a formal job, for one. She is – and has always been – in Chile legally: her previous visa has expired, and her new one is being processed. Under the law, she is permitted to stay and work in the country while this is happening. But she is finding the…
Content type: Case Study
Photo credit: Douglas Fernandes
The exclusion caused by ID can have a devastating effect on people, limiting their opportunities and ability to survive. In September 2018, Privacy International interviewed people in Santiago, Chile who had faced problems from the Chilean ID system, known as the RUT. Names have been changed.
It was never going to be easy for Liliana, entering Chile without a visa. But, in Chile, the ID system – known as the RUT – is ubiquitous; without one, as she would…
Content type: Explainer
In the digital economy there is a trend towards corporate concentration. This is true for social media platforms, search engines, smart phone operating systems, digital entertainment, or online retailers. Meanwhile, the way in which market dominance is measured traditionally does not always capture the extent of their control: firstly, their products and services are often “free” and secondly, it’s often not clear in which “markets” and “sectors” these companies operate, since there is so much…
Content type: Explainer
“Smart city” is a marketing term used to define the use of technology – and in particular data collection – to improve the functioning of cities. The idea behind smart cities is that the more local governments know about city inhabitants the better the services they deliver will be. However, the reality is that the term means different things to different actors from companies to governments.
The World Bank suggests two possible definitions of smart cities. The first one is “a technology-…
Content type: Case Study
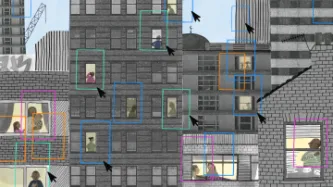
Cities around the world are deploying collecting increasing amounts of data and the public is not part of deciding if and how such systems are deployed.
Smart cities represent a market expected to reach almost $760 billion dollars by 2020. All over the world, deals are signed between local governments and private companies, often behind closed doors. The public has been left out of this debate while the current reality of smart cities redefines people’s right to privacy and creates new…
Content type: Case Study
Financial services are collecting and exploiting increasing amounts of data about our behaviour, interests, networks, and personalities to make financial judgements about us, like our creditworthiness.
Increasingly, financial services such as insurers, lenders, banks, and financial mobile app startups, are collecting and exploiting a broad breadth of data to make decisions about people. This is particularly affecting the poorest and most excluded in societies.
For example, the decisions…