Search
Content type: News & Analysis
Photo by Mike MacKenzie (via www.vpnsrus.com)
Ever, a cloud storage app, is an example of how facial recognition technology can be developed in ways people do not expect and can risk amplifying discrimination.
Ever is a cloud storage app that brands itself as “helping you capture and rediscover your life’s memories,” including by uploading and storing personal photos; Ever does not advertise that it uses the millions of photos people upload to train its facial recognition software,…
Content type: News & Analysis
Privacy International welcomes WhatsApp's immediate reaction after the revelation that Israeli cyber intelligence company NSO group had exploited a vulnerability in their software. We encourage all WhatsApp users to update their app as soon as possible. However, we believe WhatsApp needs to be much more transparent with their users. We haven't seen a notification on the app itself that would inform users about both, the bug, and the fix. The current version merely states that you can now see…
Content type: Examples
Virginia Eubanks explains what we can draw from understanding the experience of surveillance of marginalised groups: it is a civil rights issue, technologies carry the bias of those who design them, people are resisting and why we need to move away from the privacy rights discourse.
https://prospect.org/article/want-predict-future-surveillance-ask-poor-communities
Author: Virginia Eubanks
Publication: The American Prospect
Content type: Long Read
Image Source: "Voting Key" by CreditDebitPro is licensed under CC BY 2.0
Democratic society is under threat from a range of players exploiting our data in ways which are often hidden and unaccountable. These actors are manifold: traditional political parties (from the whole political spectrum), organisations or individuals pushing particular political agendas, foreign actors aiming at interfering with national democratic processes, and the industries that provide products that …
Content type: Long Read
Imagine that every time you want to attend a march, religious event, political meeting, protest, or public rally, you must share deeply personal information with police and intelligence agencies, even when they have no reason to suspect you of wrongdoing.
First, you need to go to the police to register; have your photo taken for a biometric database; share the contacts of your family, friends, and colleagues; disclose your finances, health records, lifestyle choices, relationship status, and…
Content type: News & Analysis
The first half of 2018 saw two major privacy moments: in March, the Facebook/ Cambridge Analytica scandal broke, followed in May by the EU General Data Protection Regulation ("GDPR") taking effect. The Cambridge Analytica scandal, as it has become known, grabbed the attention and outrage of the media, the public, parliamentarians and regulators around the world - demonstrating that yes, people do care about violations of their privacy and abuse of power. This scandal has been one of…
Content type: Advocacy
Consultation Submission
In March 2019, Privacy International submitted a response to a consultation on Disinformation in Electoral Contexts, led by the Office of the Special Rapporteur for Freedom of Expression of the Inter-American Commission on Human Rights together with the Department of Electoral Cooperation and Observation (DECO) and the Department of International Law (DIL) of the Organisation of American States (OAS).
In our submission we highlighted the importance of minmising data…
Content type: News & Analysis
This piece was first published in GDPR today in March 2019.
Elections, referendums and political campaigns around the world are becoming ever more sophisticated data operations. This raises questions about the political use and abuse of personal data. With the European Union elections fast approaching and numerous national and local elections taking place across EU Member States, it is essential that the legal frameworks intended to protect our personal data do just that.
Member State…
Content type: Advocacy
This week a public debate on facial recognition will take place in Westminster Hall.
Following a public request for comment by Darren Jones MP (Science and Technology Committee), we sent our responses to the questions asked.
Below you can find the integral content of our letter.
1. Would you consent to the police scanning your face in a crowd to check you’re not a criminal?
Facial recognition technology uses cameras with software to match live footage of people in public with…
Content type: News & Analysis
Photo by DAVID ILIFF. License: CC-BY-SA 3.0
Between 23 and 26 May 2019 Europeans will be voting to elect members of the European Parliament.
Since the last elections in 2014, much has changed within and without the European Union: the rise of nationalism and Euroscepticism, the protracted armed conflict in Ukraine and the occupation of Crimea by Russia, the new political orientation of the United States, just to name a few.
Among the new challenges facing these elections is…
Content type: Long Read
This image was found here.
Spain is holding a national general election on April 28 (its third in four years). Four weeks later Spaniards will again go to the polls to vote in the European Parliament elections. At Privacy International we are working to investigate and challenge the exploitation of people’s data in the electoral cycle including in political campaigns. This includes looking at the legal frameworks governing the use of data by political parties and their…
Content type: Long Read
Last week, an investigation by Bloomberg revealed that thousands of Amazon employees around the world are listening in on Amazon Echo users.
As we have been explaining across media, we believe that by using default settings and vague privacy policies which allow Amazon employees to listen in on the recordings of users’ interactions with their devices, Amazon risks deliberately deceiving its customers.
Amazon has so far been dismissive, arguing that people had the options to opt out from the…
Content type: News & Analysis
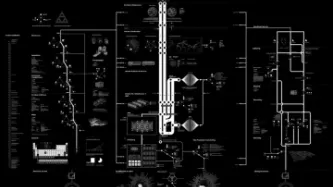
Image: Anatomy of an AI system: a map of the many processes — extracting material resources, data, and human labor — that make an Amazon Echo work. Credit: Kate Crawford and Vladan Joler
With over 6.3 million Amazon Echo devices worldwide, there is a good chance these constantly active devices will record criminal behavior.
Bloomberg, who recently reported on yet another creepy feature, that Amazon workers are listening to what you tell Alexa, were told by workers…
Content type: Examples
Facebook's latest tool for inspecting political ads showed that in the run-up to the US mid-term elections in November 2018, many of the same politicians who had been questioning Facebook about privacy and leaked user data were spending campaign funds on advertisements on the service. Between 2014 and 2018, the digital percentage of political spending rose from 1% to 22% (or about $1.9 billion); between May and November 2018 political spending on Facebook and its subsidiaries came to nearly $…
Content type: News & Analysis
According to the International Organization for Migration, an estimated 258 million people are international migrants – that is, someone who changes their country of usual residence, That’s one in every 30 people on earth.
These unprecedented movements levels show no sign of slowing down. It is predicted that by 2050, there will be 450 million migrants across the world.
Nowadays, it is politically acceptable to demonise migrants, and countless leaders have spewed divisive and xenophobic…
Content type: Long Read
The UK border authority is using money ring-fenced for aid to train, finance, and provide equipment to foreign border control agencies in a bid to “export the border” to countries around the world.
Under the UK Border Force’s “Project Hunter”, the agency works with foreign security authorities to bolster their “border intelligence and targeting” capabilities with UK know-how and equipment.
As well as the provision of equipment and training, the Border Force is also advising countries on…
Content type: Advocacy
Cases of female and gender diverse public figures being targeted with online harassment have become sadly common in the news. Female politicians are particularly affected – although journalists and in particular sports commentators are also frequently targeted as well. In some cases, the harassment goes as far death and rape threat for women and gender diverse people who dare speaking publicly. Beyond the freedom of speech implications – as we risk seeing women and gender diverse people being…
Content type: News & Analysis
The Committee on Foreign Investment in the United States (CFIUS) is trying to force the Chinese owner of the gay dating app Grindr to sell the app because of national security concerns. This is the first time the committee has considered the national security implications of a foreign social media app.
Early last year, the Chinese company Beijing Kunlun Tech purchased the Californian-based dating app. Kulun had already owned 60 per cent of Grindr since 2016. Yet, it is only now – with an…
Content type: News & Analysis
This past weekend, in an Op-Ed in the Washington Post, Mark Zuckerberg called for new regulations to address harmful content, electoral integrity, privacy and data portability.
Nine years since he proclaimed that privacy is no longer a social norm, four years since Facebook noticed broadscale harvesting and exploitation of their users' data by third party companies and chose not to tell us about it, two years since he denied there were any abuses of data in political campaigns, and…
Content type: News & Analysis
Planning and participating in peaceful protests against governments or non-state actors’ policies and practices requires the capacity of individuals to communicate confidentially without unlawful interference. From protests in support of LGBTI rights to protests against specific projects that undermine local communities’ wellbeing, these movements would not have been possible without the ability to exchange ideas and develop plans in private spaces.
Unlawful interference with…
Content type: State of Privacy
Introduction
Acknowledgment
The State of Surveillance in Tunisia is the result of an ongoing collaboration by Privacy International and partners.
On 14 February 2023, the United Nations High Commissioner for Human Rights voiced concern over the deepening crackdown in Tunisia targeting perceived political opponents of President Kais Saied as well as civil society.
We have updated this page to reflect important changes in the state of surveillance in Tunisia.
Key privacy facts
1.…
Content type: News & Analysis
At Privacy International, we talk about: “the world being on fire.”We say it to talk about the recurring threats to our democracies, the elections of authoritarian leaders, the current political climate… Or the actual climate. More often than not, we use it to talk about the (lack of) security in the design and implementation of computer systems.
But there is another kind of fire. The fourth wave of feminism – the one that contributed to the protests following the 2012 gang rape of…
Content type: Virtual Machine
The documentation below is a copy of the documentation found on Github: Interception environment on Github
Privacy International's data interception environment
Version: 2.1.2-20190730
Privacy International's data interception environment
Quick Start Guide
Step 0 - Prerequisites
Step 1 - Download
Step 2 - Importation
Step 3 - Initialising
Step 4 - Setup
Step 5 - Capture
Step 6 - Notes for Android Nougat or Later
Background
Theory
Implementation
Virtualbox (6.0.4)
Debian 10 (Buster)…
Content type: News & Analysis
At the beginning of November 2018, the first GDPR-related privacy and freedom of expression case arose in Romania in connection to the publication by the RISE Project of several articles about a corruption investigation. The articles reported a close relationship between a road construction company that is currently under investigation for fraud, European funds, and a high-profile politician.
Shortly after the first article was published, the Romanian data protection authority (“ANSPDCP”) sent…
Content type: News & Analysis
One of the UN's largest aid programmes just signed a deal with the CIA-backed data monolith Palantir
Last week, the UN's World Food Programme (WFP) announced a partnership with Palantir, the controversial US-based data analytics company with deep links to US intelligence agencies. This is a deal that has serious consequences for the privacy and security of the 90-million-plus recipients of WFP aid each year. The reaction to the news that WFP and Palantir have entered into this partnership, amongst many in the data and development community was immediate, and visceral. After all, Palantir has a…
Content type: Examples
In September 2018, the attorney general of the US state of New Mexico filed suit against Lithuania-based Tiny Lab Productions claiming that the maker of the children's app Fun Kid Racing had violated the Children's Online Privacy Protection Act (1998) by collecting location and other data about the children playing the game. The suit also included online ad businesses run by Google, Twitter, and three other companies, arguing that Google's inclusion of the app in the family section of its Play…
Content type: Long Read
Over the past year, the Privacy International Network has uncovered, campaigned, and advocated on how trends in surveillance and data exploitation are increasingly affecting our right to privacy.
To celebrate Data Privacy Day on 28 January, we shared a full week of stories and research, exploring how countries are addressing data governance, and the implications for our security and privacy.
Monday - Exposing Harms, Fighting Back
It is often communities who are already the most…
Content type: Long Read
During the last World Economic Forum in Davos, the CEO of Microsoft joined the chorus of voices calling for new global privacy rules, saying the following in regard to the new European General Data Protection Regulation (GDPR):
“My own point of view is that it's a fantastic start in treating privacy as a human right. I hope that in the United States we do something similar, and that the world converges on a common standard."
We have come a long way. From tech companies fighting and…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
Since 2014, the Privacy International Network has produced State of Privacy reports, a collaborative effort to record global privacy and related issues.
As we close Data Privacy Week this year, we’re pleased to share an update of the…
Content type: Explainer
This is the third part of Understanding Identity Systems. Read Part 1: Why ID?, and Part 2: Discrimination and Identity.
Biometrics
Biometrics are the physiological and behavioural characteristics of individuals. This could be fingerprints, voice, face, retina and iris patterns, hand geometry, gait or DNA profiles. However, the legal definition of ‘biometrics’ may differ – in some contexts, it may be defined by law, whereas in others it may not have, or only have…