Advanced Search
Content Type: News & Analysis
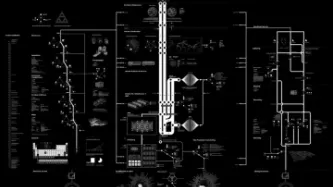
Image: Anatomy of an AI system: a map of the many processes — extracting material resources, data, and human labor — that make an Amazon Echo work. Credit: Kate Crawford and Vladan Joler
With over 6.3 million Amazon Echo devices worldwide, there is a good chance these constantly active devices will record criminal behavior.
Bloomberg, who recently reported on yet another creepy feature, that Amazon workers are listening to what you tell Alexa, were told by workers…
Content Type: Examples
In August 2018, domestic abuse victims, their lawyers, shelter workers, and emergency responders began finding that the Internet of Things was becoming an alarming new tool for harassment, monitoring, revenge, and control. Smartphone apps enable abusers to remotely control everyday objects inside their targets homes and use them to watch, listen, scare, or intimidate. Lack of knowledge about how the technology works and uncertainty about how much control the abusive partner has add a…
Content Type: Examples
In June 2018, security researchers found that Google's smart speaker and home assistant, Google Home, and its Chromecast streaming device could be made to leak highly accurate location information because they failed to require authentication from other machines on their local network. The attack worked by requesting a list of nearby wireless networks from the Google device and sending that list on to Google's geolocation lookup service, whose map of wireless network names around the world is…
Content Type: Examples
In 2018, documents filed in a court case showed that a few days before the 2017 inauguration of US president Donald Trump - timing that may have been a coincidence - two Romanian hackers took over 123 of the police department's 187 surveillance cameras in Washington, DC with the intention of using police computers to email ransomware to more than 179,000 accounts. The prosecution also said the alleged hackers had stolen banking credentials and passwords and could have used police computers to…
Content Type: Examples
In a talk at the 2018 Wall Street Journal CEO Council Conference, Darktrace CEO Nicole Eagan gave as an example of the new opportunities afforded by the Internet of Things a case in which attackers used a thermometer in a lobby aquarium to gain a foothold in a casino's network and exfiltrate the high-roller database. Regulation will be required to set minimum security standards.
https://www.businessinsider.de/hackers-stole-a-casinos-database-through-a-thermometer-in-the-lobby-fish-tank-2018-4…
Content Type: Examples
In 2018, a South Carolina woman realised her FREDI video baby monitor had been hacked when the camera began panning across the room to the spot where she breastfed her son. A 2015 study conducted by Rapid7 found that baby monitors have a number of vulnerabilities that are both easily exploited and long-ago solved for modern computers. Consumers eager to avoid these problems should either avoid buying monitors with internet connections or look for manufacturers that are known to fix security…
Content Type: Examples
In June 2018, after privacy activists found security flaws in toys such as My Friend Cayla and others and the US Consumer Product Safety Commission opened an investigation into the problems of connected gadgets, Amazon, Walmart, and Target announced they would stop selling CloudPets. Made by Spiral Toys, CloudPets uses voice recordings, an internet connection, and a Bluetooth-connected app. In 2017, a hackers were able to access and hold for ransom CloudPets' database, including email addresses…
Content Type: Examples
In May 2018, researchers in the US and China demonstrated that they could send commands that activate Apple's Siri, Amazon's Alexa, and Google Assistant but that are inaudible to the human ear. The researchers were able to make smartphones and smart speakers dial phone numbers and open websites; the potential is there to make them operate Internet of Things devices, wire money, or execute retail transactions by hiding commands in music or other audio.
https://www.nytimes.com/2018/05/10/…
Content Type: Examples
In October 2018, a transparency report from the smart home company Nest, which Google acquired for $3.2 billion in 2014, found that between 2015 and 2018 Nest had been told to hand over data on 300 separate occasions relating to up to 525 Nest account holders. Nest turned over data in fewer than 20% of the cases in the first half of 2018, down from the second half of 2015, when the company complied nearly 60% of the time. Nest is best known for its smart thermostats, but it also makes…
Content Type: Examples
Reporter Kashmir Hill tested life in a smart home by adding numerous connected devices. The self-heating bed gave her daily reports on whether she'd reached her "sleep goal". She liked the convenience of the voice-activated lights, coffee maker, and music, the ability to convey a message to a toddler through a toy, and the robot vacuum cleaner. Meanwhile, colleague Surya Mattu built a Raspberry Pi router to monitor these devices to find out what data they collected and where they wanted to send…
Content Type: Examples
Police investigating the 2016 rape and murder of a 19-year-old medical student were unable to search the iPhone of suspect Hussein Khavari, an Afghan refugee who declined to give them his password. The investigators gained access to the phone via a private company in Munich, and went through Apple's health app data to discern what kinds of activities Khavari participated in on the day of the murder. The app identified the bulk of his activity as "climbing stairs". An investigator of similar…
Content Type: Examples
The French data protection regulator, the Commission Nationale de l'Informatique et des Libertés (CNIL), has issued a formal notice to Genesis Industries Limited, the maker of the connected toys My Friend Cayla and I-QUE. Genesis has two months to bring the toys into compliance with data protection law. CNIL says that based on the security flaws found by a consumer association (presumably the Norwegian Consumer Council, which did this work in 2016) its chair decided to perform online…
Content Type: Examples
Recognising that many parents will be considering purchasing connected toys and other devices for their children, for Christmas 2017 the UK's Information Commissioner's Office issued a list of 12 guidelines for assessing products before purchasing. These include: research the product's security before buying; watch out for online shopping fraud; plan ahead to study the product's security and privacy options; change default user names and passwords; ensure your home router is security; use two-…
Content Type: Examples
Owners of the Hong Kong-based sex toy company Lovense's vibrators who installed the company's remote control app were surprised to discover that the app was recording user sessions without their knowledge. They had authorised the app to use the phone's built-in microphone and camera, but only for use within the app's built-in chat function and to send voice clips on command. Lovense says that no data was sent to its servers, and that the audio files users have found stored on their phones are…
Content Type: Examples
The UK consumer watchdog Which? has called on retailers to stop selling popular connected toys it says have proven security issues. These include Hasbro's Furby Connect, Vivid Imagination's I-Que robot, and Spiral Toys' Cloudpets and Toy-fi Teddy. In its report, Which? found that these toys do not require authentication to link to other devices via Bluetooth, meaning that any device within range could connect to the toys and take control of them or send messages. Spiral Toys did not comment.…
Content Type: Examples
Privacy and child advocacy groups in the US, Denmark, Belgium, the Netherlands, Sweden, Germany, and the UK are filing complaints with regulators after a study by the Norwegian Consumer Council found critical security flaws and missing privacy protection in children's smartwatches. The watches, which are functionally essentially wearable smartphones, are intended to help parents keep an eye on their children. However, the NCC's research found that they can be easily taken over by strangers and…
Content Type: Examples
In 2017, after protests from children's health and privacy advocates, Mattel cancelled its planned child-focused "Aristotle" smart hub. Aristotle was designed to adapt to and learn about the child as they grew while controlling devices from night lights to homework aids. However, Aristotle was only one of many tech devices being released onto the market to take over functions that have traditionally been part of the intimate relationship between children and their parents: a smart cradle that…
Content Type: Examples
A report from the University of Washington studies parents' and children's interactions with general-purpose connected devices and connected toys. There are numerous privacy issues: toy companies may collect masses of children's intimate data; the toys may enable parents to spy on their children, and criminals hacking these systems may be able to identify and locate the children. For example, the 2015 cyber attack on VTech, a children's tablet maker, exposed the personal data of 5 million…
Content Type: Examples
The "couples vibrator" We-Vibe 4 Plus is controlled via a smartphone app connected to the device via Bluetooth. In 2016, researchers revealed at Defcon that the devices uses its internet connectivity to send information back to its manufacturer including the device's temperature, measured every minute, and vibration level, whenever a user changes it. Based on that information, the manufacturer, Standard Innovations Corporation, can work out deeply intimate information about device users. The…
Content Type: Examples
Many people fail to recognise the sensitivity of the data collected by fitness tracking devices, focusing instead on the messages and photographs collected by mobile phone apps and social media. Increasingly, however, researchers are finding that the data collected by these trackers - seemingly benign information such as steps taken and heart rate - can be highly revealing of such intimate information as sexual dysfunction. In one Swedish study in 2015, researchers found a correlation between…
Content Type: Examples
In 2016, Verbraucherzentrale NRW, a consumer protection organisation in the German state of North Rhine-Westphalia accused Samsung of harvesting data and sending it back to the company over the internet without informing users as soon as its smart televisions are connected to the internet. The complaint specifies the model UE40H6270. The group wants Samsung to default to an anonymous setting rather than transmit information including the show being watched, the time of date, and the user's IP…
Content Type: Examples
In 2016, when security expert Matthew Garrett stayed in a London hotel where the light switches had been replaced by Android tablets, it took him only a few hours to gain access to all of the room's electronics. The steps he followed: plug his laptop into a link in place of one of the tablets; set up a transparent bridge; analyse the data traffic with WireShark to identify the protocol in use; then exploit that protocol. That protocol was Modbus, an old protocol with no authentication. Once…
Content Type: Examples
In 2015, ABI Research discovered that the power light on the front of Alphabet's Nest Cam was deceptive: even when users had used the associated app to power down the camera and the power light went off, the device continued to monitor its surroundings, noting sound, movement, and other activities. The proof lay in the fact that the device's power drain diminished by an amount consistent with only turning off the LED light. Alphabet explained the reason was that the camera had to be ready to be…
Content Type: Examples
In June 2016, National Security Agency deputy director Richard Ledgett told a conference on military technology conference that the agency was researching whether internet-connected biomedical devices such as pacemakers could be used to collect foreign intelligence. Ledgett identified the complexity of the Internet of Things as both a security nightmare and an opportunity for signals intelligence. However, the NSA prioritises its resources by focusing solely on technology used by its opponents…
Content Type: Examples
The news that connected TVs and set-top boxes were listening in on their owners' conversations led the state of California to pass legislation (AB1116) prohibiting companies from operating a voice recognition feature without prominently informing the user or installer during initial setup. In addition, the bill bars manufacturers and third parties from using recordings of spoken words "collected through the operation of a voice recognition feature" in order to improve their voice recognition or…
Content Type: Examples
A 2009 paper by the US National Academy of Sciences found that among forensic methods only DNA can reliably and consistency match evidence to specific individuals or sources. While it's commonly understood that techniques such as analysis of blood spatter patterns are up for debate, other types of visual evidence have been more readily accepted. In 2015 the FBI announced that virtually all of its hair analysis testing was scientifically indefensible, and in 2016 the Texas Forensic Science…
Content Type: Examples
A US House of Representatives oversight committee was told in March 2017 that photographs of about half of the adult US population are stored in facial recognition databases that can be accessed by the FBI without their knowledge or consent. In addition, about 80% of the photos in the FBI's network are of non-criminals and come from sources such as passports. Eighteen states supply driver's licences under arrangement with the FBI. In response, privacy advocates and politicians called for…
Content Type: Examples
Connecticut police have used the data collected by a murder victim's Fitbit to question her husband's alibi. Richard Dabate, accused of killing his wife in 2015, claimed a masked assailant came into the couple's home and used pressure points to subdue him before shooting his wife, Connie. However, her Fitbit's data acts as a "digital footprint", showing she continued to move around for more than an hour after the shooting took place. A 2015 report from the National Institute of…
Content Type: Examples
Even after they move out, domestic abusers may retain control over their former residence via Internet of Things devices and the mobile phone apps that control them. Using those tools, abusers can confuse, intimidate, and spy upon their former spouses and partners. Lack of knowledge about how these technologies work means that those who complain are often not taken seriously. Even the victims themselves may believe it's all in their minds; lawyers are struggling to develop language to add to…
Content Type: Examples
A 2017 lawsuit filed by Chicagoan Kyle Zak against Bose Corp alleges that the company uses the Bose Connect app associated with its high-end Q35 wireless headphones to spy on its customers, tracking the music, podcasts, and other audio they listen to and then violates their privacy rights by selling the information without permission. The case reflects many of the concerns associated with Internet of Things devices, which frequently arrive with shoddy security or dubious data…