Advanced Search
Content Type: Long Read
If you’ve ever used TikTok, Instagram, or X/Twitter, you will already be familiar with centralised social media.Centralised social media means big company owns the app, controls the software, and keeps all your data.For example, ByteDance makes TikTok. They own it, run the servers, decide what you see in your feed, and hold onto every video you like or comment on. They call the shots when it comes to your data.But what if social media didn’t work that way? What if no single company was in…
Content Type: News & Analysis
We’ve been asked a lot lately about whether it is safe to travel, particularly to the US. And it’s not surprising why: the US Government is increasing their cruelty at borders.Border management today is fueled by our data, but government officials want more. They want as much data as they can get to catch you out. They’ve reportedly detained or deported people based on their free speech activities, denying entry on tenuous grounds like having the wrong photos on phones (including in in the ‘…
Content Type: Long Read
Social media is now undeniably a significant part of many of our lives, in the UK and around the world. We use it to connect with others and share information in public and private ways. Governments and companies have, of course, taken note and built fortunes or extended their power by exploiting the digital information we generate. But should the power to use the information we share online be unlimited, especially for governments who increasingly use that information to make material…
Content Type: Long Read
The Chief Surveillance Commissioner, The Rt Hon Sir Christopher Rose’s Annual Report 2011 - 12 did not refer to social networks but to overt investigations using the internet as a surveillance tool, stating that:
“5.17 A frequent response to my Inspectors’ enquiries regarding a reduction in directed surveillance is that ‘overt’ investigations using the Internet suffice. My Commissioners have expressed concern that some research using the Internet may meet the criteria of directed…
Content Type: Long Read
Online covert activity
3.10 The growth of the internet, and the extent of the information that is now available online, presents new opportunities for public authorities to view or gather information which may assist them in preventing or detecting crime or carrying out other statutory functions, as well as in understanding and engaging with the public they serve. It is important that public authorities are able to make full and lawful use of this information for their statutory purposes. Much…
Content Type: Explainer
Social media platforms are a vast trove of information about individuals, including their personal preferences, political and religious views, physical and mental health and the identity of their friends and families.
Social media monitoring, or social media intelligence (also defined as SOCMINT), refers to the techniques and technologies that allow the monitoring and gathering of information on social media platforms such as Facebook and Twitter which provides valuable intelligence to others…
Content Type: Long Read
It is common for families with no recourse to public funds who attempt to access support from local authorities to have their social media monitored as part of a ‘Child in Need’ assessment.
This practice appears to be part of a proactive strategy on the part of local authorities to discredit vulnerable families in order to refuse support. In our experience, information on social media accounts is often wildly misinterpreted by local authorities who make serious and unfounded allegations…
Content Type: News & Analysis
Lockdowns and quarantines are an extraordinary measure that help in slowing down the global COVID-19 pandemic, and protecting the population.
However, they come at an even higher cost to some individuals, such as victims of domestic violence, persons in a vulnerable situation, and human rights defenders, who face specific threats that are exacerbated by measures taken by governments to address the global pandemic.
In that context, states should adopt special measures to keep those people…
Content Type: Long Read
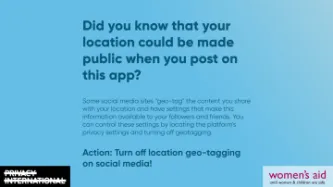
Valentine’s Day is traditionally a day to celebrate relationships, but many relationships that begin romantically can quickly become controlling, with partners reading emails, checking texts and locations of social media posts. This can be just the beginning.
Today, Friday 14th February, Privacy International and Women’s Aid are launching a series of digital social media cards giving women practical information on how to help stay safe digitally from control and abuse.
Did you know…
Content Type: News & Analysis
Photo by VanveenJF on Unsplash
Last week, Amnesty International published a report revealing the Moroccan government appears to have been using spyware from Israeli company NSO Group against two human rights defenders, historian and columnist Maati Monjib and lawyer Abdessadak El Bouchattaoui.
In order for the government to gain control over their phones, Monjib and El Bouchattaoui had to click on a malicious link which would install NSO Group’s Pegasus spyware. NSO therefore has to craft…
Content Type: Advocacy
In this submission, Privacy International aims to provide the Office of the UN High Commissioner for Human Rights with information on how surveillance technologies are affecting the right to peaceful protests in new and often unregulated ways.
Based on Privacy International’s research, we provide observations, regarding the following:
the relationship between peaceful protests and the right to privacy;
the impact of new surveillance technologies in the context of peaceful protests…
Content Type: News & Analysis
The latest news of Twitter “inadvertently” sharing email addresses or phone numbers provided for safety or security purposes (for example, two-factor authentication) for advertising purposes is extremely concerning for several reasons.
First of all, it is not the first time for Twitter's used people's data in ways they wouldn't expect or that ignores their choices: in August, the company disclosed that it may have shared data on users with advertising partners, even if they had opted out from…
Content Type: News & Analysis
Photo by Daniel Jensen on Unsplash
Everyone is talking about Facebook's end-to-end encryption plans and the US, UK and Australian government's response. Feeling lost? Here is what you need to know.
What's Facebook trying to do?
First let's be clear: Facebook has many faults when it comes to privacy. It's also suffered a number of security failures recently. See here for instance.
In response to their successive failures to protect your privacy, Facebook announced in their 'pivot to privacy…
Content Type: Examples
A 17-year-old Palestinian resident of Lebanon, Ismail B. Ajjawi, was deported shortly after he arrived at Boston Airport, where he was due to start attending Harvard University the following week.
Immigration officers subjected him to hours of questioning — at one point leaving to search his phone and computer — according to a written statement by Ajjawi. According to the student, his visa was revoked because of content posted by some social media contacts.
The student alleges that…
Content Type: Examples
In November 2018, worried American parents wishing to check out prospective babysitters and dissatisfied with criminal background checks began paying $24.99 for a scan from the online service Predictim, which claimed to use "advanced artificial intelligence" to offer an automated risk rating. Predictim based its scores in part on Facebook, Twitter, and Instagram posts - applicants were required to share broad access to their accounts - and offered no explanation of how it reached its risk…
Content Type: Examples
In November 2018, researchers at Sweden's University of Lund, the US's Worcester Polytechnic Institute, and the UK's Oxford University announced that in August the US State Department had begun using a software program they had designed that uses AI to find the best match for a refugee's needs, including access to jobs, medical facilities, schools, and nearby migrants who speak the same language. Known as "Annie MOORE", refugees matched by the program were finding jobs within 90 days about a…
Content Type: News & Analysis
While people may think that providing their photos and data is a small price to pay for the entertainment FaceApp offers, the app raises concerns about privacy, manipulation, and data exploitation—although these concerns are not necessarily unique to FaceApp.According to FaceApp's terms of use and privacy policy, people are giving FaceApp "a perpetual, irrevocable, nonexclusive, royalty-free, worldwide, fully-paid, transferable sub-licensable license" to use or publish the…
Content Type: Examples
In 2017, US Immigration & Customs Enforcement (ICE) announced that it would seek to use artificial intelligence to automatically evaluate the probability of a prospective immigrant “becoming a positively contributing member of society.” In a letter to acting Department of Homeland Security Secretary Elaine Duke, a group of 54 concerned computer scientists, engineers, mathematicians, and researchers objected to ICE’s proposal and demanded that ICE abandon this approach because it would be…
Content Type: Examples
US Immigrations & Customs Enforcement (ICE) used social media monitoring to track groups and people in New York City associated with public events opposing the Trump administration’s policies, including ones related to immigration and gun control. The investigative branch of ICE created and circulated a spreadsheet, entitled ‘Anti-Trump Protest Spreadsheet 07/31/2018,” that provided details of events planned between July 31, 2018, and August 17, 2018. The spreadsheet pulled data from…
Content Type: Examples
The US government created a database of more than 50 journalists and immigrant rights advocates, many of whom were American citizens, associated with the journey of migrants travelling from Central America to the Mexico-US border in late 2018. Officials from Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), the US Border Patrol, Homeland Security Investigations, and the Federal Bureau of Investigation (FBI) had access to this database. This list allowed the…
Content Type: Examples
A private intelligence company, LookingGlass Cyber Solutions, used social media to monitor more than 600 “Family Separation Day Protests” held across the United States on June 30, 2018, to oppose the Trump administration’s policy family separation policy. The policy was part of a “zero tolerance” approach to deter asylum seekers from coming to the United States by separating children from their parents. After collecting information about these protests through Facebook, including the precise…
Content Type: Examples
Absher, an online platform and mobile phone app created by the Saudi Arabian government, can allow men to restrict women’s ability to travel, live in Saudi Arabia, or access government services. This app, which is available in the Google and Apple app stores, supports and enables the discriminatory male guardianship system in Saudi Arabia and violations of womens’ rights, including the right to leave and return to one’s own country. Because women in Saudi Arabia are required to have a male…
Content Type: Examples
Bahrain has warned its citizens and residents could face legal action simply for following social media accounts it deems anti-government, which raises concerns about the ability of Bahraini citizens and residents to exercise their fundamental rights and freedoms. In May 2019, a state terrorism law was expanded to criminalise anyone “promoting, glorifying, justifying, approving or supporting acts which constitute terrorist activities,” whether within or outside Bahrain. The government’s…
Content Type: Long Read
Whilst innovation in technology and data processing have provided individuals and communities with new opportunities to exercise their fundamental rights and freedoms, this has not come without risks, and these opportunities have not been enjoyed by all equally and freely.
Our relationships and interactions with governments and industry have become increasingly dependent on us providing more and more data and information about ourselves. And, it’s not only the information we provide knowingly…
Content Type: News & Analysis
Today, the British Health Secretary Matt Hancock announced a partnership between the NHS and Amazon to use the NHS’s website content as the source for the answer given to medical question, such as “Alexa, how do I treat a migraine?”
While we welcome Amazon’s use of a trusted source of information for medical queries, we are however extremely concerned about the nature and the implications of this partnership. Amazon is a company with a worrying track record when it comes to the way they…
Content Type: Report
Like many others, PI were alarmed at recent reports that Facebook have been making mobile phone numbers (which users believed to be) provided for the express purpose of "two-factor authentication" (2FA) both searchable, and a target for advertising by default.
One of the myriad ways Facebook displays targeted adverts to users is through so-called "Custom Audiences". These "custom audiences" are lists of contact details, including phone numbers and email addresses, uploaded by advertisers.…
Content Type: Long Read
When you go abroad, you expect to show your passport right? But what if immigration authorities wanted access to your Facebook, Instagram and Twitter accounts before they let you enter a country? What if they wanted to vet you based on your updates, photos, likes, retweets and even your DMs?We think social media companies, who make literally billions of dollars out of you, and wield massive power and influence, should challenge governments on YOUR behalf. They should be protecting their users…
Content Type: Advocacy
Privacy International has today sent letters to leading social media platforms to ask what they're doing to protect their users' from dangerous surveillance by government immigration authorities.
The letter comes following the implementation of plans by US authorities to require nearly all visa applicants to hand over identifiers of all social media accounts they have used in the previous five years, or face “serious immigration consequences”.
The move not only represents…
Content Type: News & Analysis
Privacy International has joined a global coalition of privacy campaigners, tech companies, and technology experts to respond to proposals by British intelligence chiefs aimed at allowing them access to encrypted messaging apps such as WhatsApp or Signal.
If implemented, the proposals would allow government authorities to force messaging platforms to silently add a law enforcement participant to a group chat or call.
Such a capability poses serious threats to…
Content Type: Explainer
Could an app you have never even heard of put you at risk? This is what happened to Chloe (real name has been changed), an investigative journalist exposed by an app that her source was using.
Her source was using TrueCaller, an app that aims to identify phone numbers so users can filter out calls, even if it is from a number they have never encountered before. TrueCaller relies on users tagging numbers who are calling them. And when your number is tagged there is no way for you to know that…