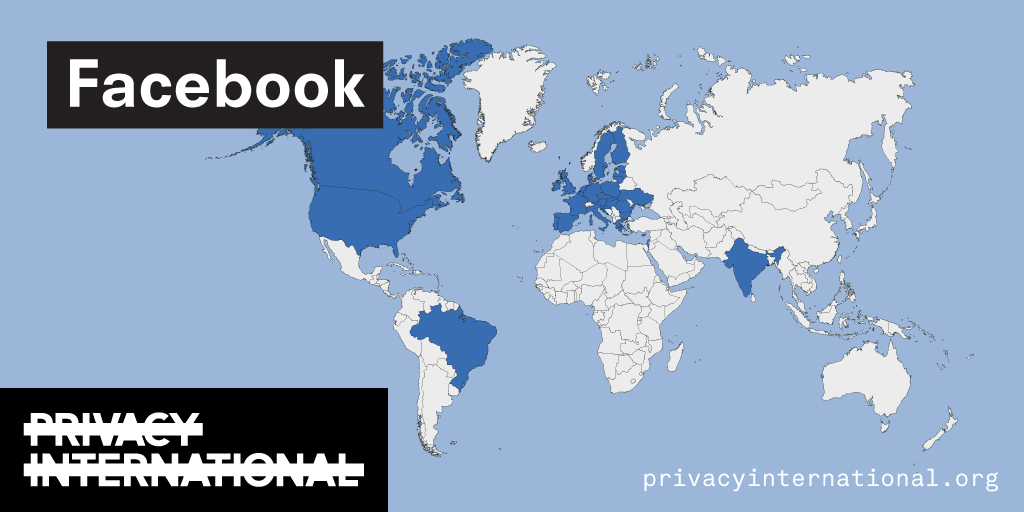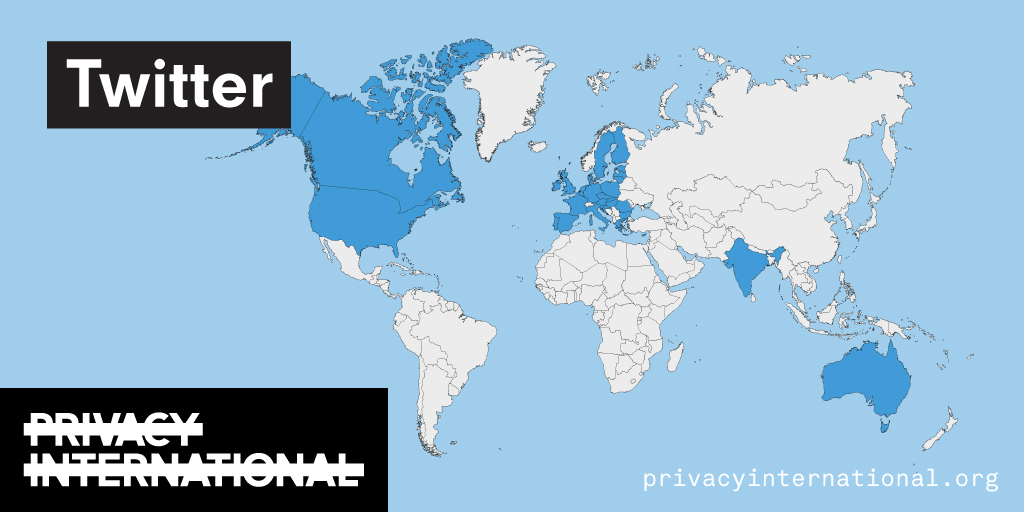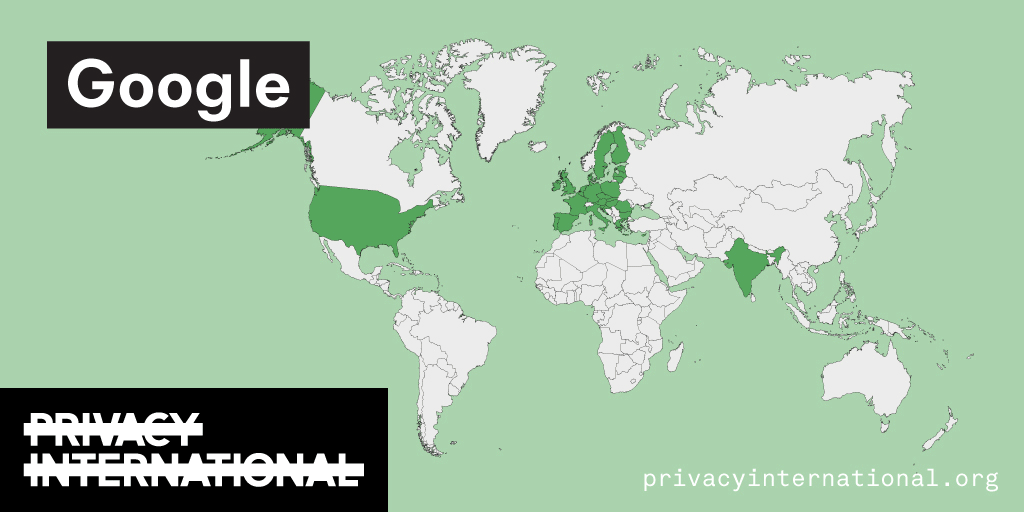
Advanced Search
Content Type: Examples
The pregnancy apps many women were using in December 2018 proved to be incapable of handling miscarriages, even though up to 20% of all known pregnancies end this way. There are only two choices: allow the apps to continue sending alerts celebrating the pregnancy's progress or delete the pregnancy entirely, losing all the records they'd saved - information that doctors routinely request. Many menstruation apps, similarly, lack the ability to adapt to long breaks and disrupted cycles, and many…
Content Type: Examples
In February 2019, the World Food Programme, a United Nations aid agency, announced a five-year, $45 million partnership with the data analytics company Palantir. WFP, the world's largest humanitarian organisation focusing on hunger and food security, hoped that Palantir, better known for partnering with police and surveillance agencies, could help analyse large amounts of data to create new insights from the data WFP collects from the 90 million people in 80 countries to whom it distributes 3…
Content Type: Explainer
Recently the role of social media and search platforms in political campaigning and elections has come under scrutiny. Concerns range from the spread of disinformation, to profiling of users without their knowledge, to micro-targeting of users with tailored messages, to interference by foreign entities, and more. Significant attention has been paid to the transparency of political ads - what are companies doing to provide their users globally with meaningful transparency into how they…
Content Type: Examples
The Lumi by Pampers nappies will track a child's urine (not bowel movements) and comes with an app that helps you "Track just about everything". The activity sensor that is placed on the nappy also tracks a baby's sleep.
Concerns over security and privacy have been raised, given baby monitors can be susceptible to hackers and any app that holds personal information could potentially expose that information.
Experts say the concept could be helpful to some parents but that there…
Content Type: Examples
Le Monde exposed anti-IVG (anti-abortion) advertising on Facebook as part of a borader campaign led by anti-abortion website IVG.net. The advertisement relied on stock photos and fake testimonies posted in public Facebook groups and promoted to young women. Most of the posts attempt to promote the idea that abortion leads to mental health issues, a fact that has been proved to be falacious.
https://www.lemonde.fr/les-decodeurs/article/2018/07/11/les-anti-ivg-ciblent-les-jeunes-femmes-grace-aux…
Content Type: Examples
French website IVG.net, first Google result when typing IVG (Interuption Volontaire de Grossesse or abortion in french), has been exposed as being anti-abortion website spreading misinformation. Offering an official looking "Numero vert" (free to call phone number number), IVG.net attempts to convince pregnant women calling the service that abortion is a high risk operation which will have terrible impact on their health and personal life, pressuring women to not undertake such operation. The…
Content Type: Examples
In 2009, Amazon Kindle readers were surprised to find that their copies of George Orwell’s 1984 was missing from their devices. Amazon had remotely deleted these copies after it found out from the publisher that the third-party vendor selling them did not own the rights to the books. Amazon refunded the cost of the books but told its readers who were affected that they could no longer read the books and that the titles were “no longer available for purchase.” This was not the first time that…
Content Type: Examples
From 2014 to early 2017, Amazon used an artificial intelligence (AI) hiring tool to review prospective employees’ resumes and select qualified candidates, based on Amazon’s previous hiring decisions from a ten-year period; however, the tool was much more effective at simply selecting male candidates, rather than the most qualified candidates, because Amazon had hired predominantly male candidates in the past. The hiring tool learned to discriminate against resumes that included the word “women’…
Content Type: Examples
The American Civil Liberties Union (ACLU) used Rekognition, Amazon’s facial recognition software, to compare images of US lawmakers to a publicly available database of 25,000 mugshot photos. The ACLU’s study validated research that has shown that facial recognition technology is more likely to produce false matches for women and people with darker skin. Amazon’s software misidentified 28 lawmakers as being the people in mugshots, and these false matches were disproportionately of members of…
Content Type: Examples
More than 450 Amazon employees delivered a letter to Jeff Bezos and other Amazon executives, demanding that the company immediately stop selling facial recognition software to law enforcement, sever connections to companies like Palantir that help immigration authorities track and deport immigrants, and provide greater employee oversight when making ethical decisions. The employees protested against Amazon allowing its technologies to be used for mass surveillance and abused by those in power,…
Content Type: Examples
Amazon shareholders rejected two non-binding proposals governing its facial recognition software, Rekognition: one would have limited sales of Rekognition to governments, unless a board determined that such sales would not violate peoples’ rights, and the other was to study the extent to which Rekognition infringed peoples’ privacy and other rights. These two proposals were presented to shareholders despite Amazon’s effort to stop the votes, which were thwarted by the US Securities and Exchange…
Content Type: Examples
Millions of people own smart home devices like the Amazon Echo and Echo Dot—equipped with the Alex cloud-based artificial intelligence service—which have concerning implications for privacy rights. While, Amazon’s own policies promise that only the user and Amazon will listen to what those devices record, it was recently reported that Amazon failed to follow its own policy when it erroneously shared one user’s information with a total stranger.
In August 2018, a German customer exercised his…
Content Type: Examples
A 19-year-old medical student was raped and drowned in the River Dresiam in October 2016. The police identified the accused by a hair found at the scene of the crime. The data recorded by the health app on his phone helped identify his location and recorded his activities throughout the day. A portion of his activity was recorded as “climbing stairs”, which authorities were able to correlate with the time he would have dragged his victim down the river embankment, and then climbed…
Content Type: Examples
The body of a 57-year-old was found in the laundry room of her home in Valley View, Adelaide, in September 2016. Her daughter-in-law who was in the house at the time of the murder claimed that she was tied up by a group of men who entered the house and managed to escape when they left. However, the data from the victim's smartwatch did not corroborate her story.The prosecution alleged that the watch had recorded data consistent with a person going into shock and losing consciousness. "The…
Content Type: Examples
The 90-year old suspect when to his stepdaughter's house at San Jose, California for a brief visit. Five days later, his stepdaugter's body, Karen was discovered by a co-worker in her house with fatal lacerations on her head and neck. The police used the data recorded by the victim's Fitbit fitness tracker to determine the time of the murder. It was been reported that the Fitbit data showed that her heart rate had spiked significantly around 3:20 p.m. on September 8, when her stepfather was…
Content Type: Examples
In 2017, US Immigration & Customs Enforcement (ICE) announced that it would seek to use artificial intelligence to automatically evaluate the probability of a prospective immigrant “becoming a positively contributing member of society.” In a letter to acting Department of Homeland Security Secretary Elaine Duke, a group of 54 concerned computer scientists, engineers, mathematicians, and researchers objected to ICE’s proposal and demanded that ICE abandon this approach because it would be…
Content Type: Examples
US Immigrations & Customs Enforcement (ICE) used social media monitoring to track groups and people in New York City associated with public events opposing the Trump administration’s policies, including ones related to immigration and gun control. The investigative branch of ICE created and circulated a spreadsheet, entitled ‘Anti-Trump Protest Spreadsheet 07/31/2018,” that provided details of events planned between July 31, 2018, and August 17, 2018. The spreadsheet pulled data from…
Content Type: Examples
The US government created a database of more than 50 journalists and immigrant rights advocates, many of whom were American citizens, associated with the journey of migrants travelling from Central America to the Mexico-US border in late 2018. Officials from Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), the US Border Patrol, Homeland Security Investigations, and the Federal Bureau of Investigation (FBI) had access to this database. This list allowed the…
Content Type: Examples
On 14 May 2018, the husband of the victim, a pharmacist living in Linthorpe in Middlesbrough, subdued his wife with insulin injection before straggling her. He then ransacked the house to make it appear as a burglary. The data recorded by the health app on the murder’s phone, showed him racing around the house as he staged the burglary, running up and down the stairs. The victim’s app showed that she remained still after her death apart from a movement of 14 paces when her husband moved her…
Content Type: Examples
A private intelligence company, LookingGlass Cyber Solutions, used social media to monitor more than 600 “Family Separation Day Protests” held across the United States on June 30, 2018, to oppose the Trump administration’s policy family separation policy. The policy was part of a “zero tolerance” approach to deter asylum seekers from coming to the United States by separating children from their parents. After collecting information about these protests through Facebook, including the precise…
Content Type: Examples
Absher, an online platform and mobile phone app created by the Saudi Arabian government, can allow men to restrict women’s ability to travel, live in Saudi Arabia, or access government services. This app, which is available in the Google and Apple app stores, supports and enables the discriminatory male guardianship system in Saudi Arabia and violations of womens’ rights, including the right to leave and return to one’s own country. Because women in Saudi Arabia are required to have a male…
Content Type: Examples
A man from Middletown, Ohio, was indicted in January 2017 for aggravated arson and insurance fraud for allegedly setting fire to his home in September 2016. Ohio authorities decided and succeeded to obtain a search warrant for the data recorded on the pacemaker after identifying inconsistencies in the suspect’s account of facts. Ohio authorities alleged that the data showed that the accused was awake when he claimed to be sleeping. It has been reported that a cardiologist, examining data from…
Content Type: Examples
Bahrain has warned its citizens and residents could face legal action simply for following social media accounts it deems anti-government, which raises concerns about the ability of Bahraini citizens and residents to exercise their fundamental rights and freedoms. In May 2019, a state terrorism law was expanded to criminalise anyone “promoting, glorifying, justifying, approving or supporting acts which constitute terrorist activities,” whether within or outside Bahrain. The government’s…
Content Type: Explainer
We look at the recently published report on forensic science in the UK, highlight concerns about police not understanding new tech used to extract data from mobile phones; the risk of making incorrect inferences and the general lack of understanding about the capabilities of these tools.
The delivery of justice depends on the integrity and accuracy of evidence and trust that society has in it. So starts the damning report of the House of Lords Science and Technology Select…
Content Type: Case Study
In this next leap to year 2030, Amtis lives the life of a data labourer, being paid wages for data inputs. Here’s how Amtis begins the story:
I am in my green pyjamas, but I can’t say for sure if it’s morning or evening. My eyes are red from staring at screens. I am discouraged and very tired. Of course, all these emotions and reactions are registered by my Playbour – my pocket-sized smart console that has basically become my entire life. It’s my connection to family, friends and the world; my…
Content Type: Case Study
In 2030 Amtis finds a future where property rights for data were adopted. Here’s how this future plays out:
My data, my turf. This was the first graffiti I saw as I was walking down the street and I said to myself, “Yeah, big corp, we’re going to get you good!”. I am fed up with companies making insane amounts of money from my data. If this is the game we’re playing, I want my fair share.
I was not the only one thinking like this. A few years back there was a strong push towards adopting…
Content Type: Explainer
Could an app you have never even heard of put you at risk? This is what happened to Chloe (real name has been changed), an investigative journalist exposed by an app that her source was using.
Her source was using TrueCaller, an app that aims to identify phone numbers so users can filter out calls, even if it is from a number they have never encountered before. TrueCaller relies on users tagging numbers who are calling them. And when your number is tagged there is no way for you to know that…
Content Type: Case Study
Photo by Roger H. Goun
Chloe is an investigative journalist working for an international broadcast service; we will call the TV show she works for The Inquirer. She travels around the world to work with local journalists on uncovering stories that make the headlines: from human trafficking to drug cartels and government corruption. While her documentaries are watched by many and inspire change in the countries she works in, you would not know who Chloe is if we were to tell you her real name.…
Content Type: Video
Watch our video primer (1m54s) on how political advertisers use highly detailed data about you to target political adverts at you.
Read about some simple steps you can take to minimise the amount of political ads you see online and questions you can be asking of those that profit from your data.
Content Type: Examples
GDPR complaints about Real-Time Bidding (RTB) in the online advertising industry were filed today with Data Protection Authorities in Spain, the Netherlands, Belgium, and Luxembourg. The complaints detail the vast scale of personal data leakage by Google and other major companies in the “Ad Tech” industry. This week marks one year since the introduction of the GDPR.
The new complaints have been filed by Gemma Galdon Clavell (Eticas Foundation) and Diego Fanjul (Finch), David Korteweg (…