Filling the gaps on the understanding of cybersecurity and human rights across the world
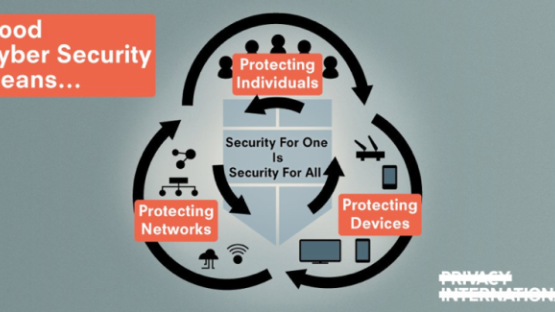
The pressing need to fix our cybersecurity (mis)understandings
Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being different concepts, the confusion between them and the broad application of criminal statutes is still leading to the criminalise legitimate behaviour.
All of this represents a sizable challenge for experts, human rights defenders and other stakeholders around the world. Some of these challenges have to do with the interaction between security and privacy, with decision makers willing to sacrifice our fundamental freedoms in the name of a vague idea of security. Closely related is the question of who or what are we protecting: Is it the state? The economy? The reputation of the powerful?
Filling the gaps around the world
In Privacy International, for a long time we have been documenting cases and advocating on these issues.
A particular concern from our side is what and who should be protected, and how to reduce our attack surface, especially for those at risk, such migrants or LGBTQ+ persons, who are being put at risk through the use of surveillance techniques and deficient privacy and security practices in apps targeting those audiences.
Strong principles and safeguards should always apply when governments intend to affect our right to privacy. As we have said before, cybersecurity means protecting individuals, networks and devices, where privacy and security should go together, not choosing one over the other.
This has also been an important challenge for our international partners. The Privacy International Network has been working to frame cybersecurity and human rights as a ‘perfect match’ in Latin America, countering dangerous government narratives on cybersecurity in Africa.
And this work is still ongoing. This year, our partners’ work has been focused on the relation between security and privacy, and on improving policy makers’ ability to work on privacy and cybersecurity issues.

In Peru, our partners from Hiperderecho published a series of articles called “Seguridad es Privacidad” (Security is privacy), analysing how Peruvian laws have been constantly undermining the right to privacy in favour of security, including a timeline of developments that started almost 25 years ago, in 1995.
Beyond its thorough revision of the Peruvian surveillance framework across multiple domains, Hiperderecho’s approach is clear and direct: We don’t need to ‘balance’ privacy and security, we need to understand that actually in most contexts Privacy is indeed the best public policy to achieve Security. Just as Miguel Morachimo, Hiperderecho’s executive director, said in his article: “Privacy for all is an excellent public policy to achieve security. Only with secure and tamper-proof technologies, clear rules and limits and strict necessity and proportionality criteria we can be truly secure.”

In Kenya, our partners from the Centre for Intellectual Property and Information Technology Law (CIPIT) of the Strathmore University decided to take a practical approach and aim directly at policy makers with a checklist for legislative drafting & interpretation in Kenya. The guide aims to address the ongoing trend of quick and reactionary legislative processes that are happening around the world, equipping decision makers with up-to-date knowledge on international standards on privacy and security in the digital world.
An interesting aspect of CIPIT’s guide is that it offers specific ways to address different interests and rights at stake, to reconcile and maximise them instead of adopting a zero-sum game where one issue (security, in this case) has to prevail over other rights. This usually happens almost by default, sometimes without identifying legitimate interests, alternative means to achieve the stated goals, or safeguards to prevent from misuse, among other necessary elements to develop regulations on this area.

In Indonesia, our partners from ELSAM developed a guide to map and identify issues related with cybersecurity and human rights, to help the development of cybersecurity regulations in the country, from both a legal and a technical perspective.
After analysing the current national framework on the issue, and comparative policies, legislations and best practices, ELSAM highlighted a number of necessary elements that the Government needs to keep in mind when designing a national cybersecurity framework, including: regulating and setting a vision for policy development, identifying and prioritising critical infrastructure, forming a team dedicated to incident response, and conducting a threat assessment and developing a recovery plan.
ELSAM’s report also confirms two things: first of all, that in some countries like Uganda, Thailand, Pakistan, Vietnam and Egypt, cybercrime laws have been misused by governments against activists, journalists and other human rights defenders. Secondly, it helps highlighting that presently there is not an internationally agreed concept of cybersecurity, confirming something we stated at the beginning of this article: that cybersecurity remains a disputed concept.
What next?
If we want to move the conversation forward, we need to seriously address the role of human rights in this process, not as an afterthought, but as an essential element in cybersecurity policy. Beyond generic claims for human rights protections, there is a pressing need to elaborate on how those protections should look like and how to embed them by default and by design in all the regulations and practices that they generate.
In relation with cybercrime, beyond avoiding its use to expand surveillance powers, there are important challenges to address: How to interpret them? What type of crimes should they cover? How to implement the Budapest Convention in a manner consistent with human rights?
In general, the global discussion is very far from over. There are diverse debates and forums around cybersecurity in different venues, including international organisations, high corporate levels, standards bodies, and national governments, among others. Different groups of experts, high-level commissions, forums and events are dealing with cybersecurity discussions, and the scenario is only getting more complex.
For example, the role of disinformation and the weaponization of data wasn’t present in the cybersecurity agenda 5 years ago, and now many cybersecurity policies and laws are increasingly covering related issues, in many cases with disastrous effects for our fundamental rights.
We need to understand and prevent real threats to cybersecurity instead of criminalising technical research or independent journalism. We need to develop law policies and technologies that enable people instead of repressing them. Instead of vague national security concerns, what we need to do is to put people and their rights at the centre of these debates.