Search
Content type: News & Analysis
A mobile device is a huge repository of sensitive data, which could provide a wealth of information about its owner and many others with whom the user interacts.
Companies like Cellebrite, MSAB and Oxygen Forensics sell software and hardware to law enforcement. Once your phone is connected to one of these mobile phone extraction tools, the device extracts, analyses and presents the data contained on the phone.
What data these tools can extract and what method is used will…
Content type: Advocacy
This week a public debate on facial recognition will take place in Westminster Hall.
Following a public request for comment by Darren Jones MP (Science and Technology Committee), we sent our responses to the questions asked.
Below you can find the integral content of our letter.
1. Would you consent to the police scanning your face in a crowd to check you’re not a criminal?
Facial recognition technology uses cameras with software to match live footage of people in public with…
Content type: Long Read
Last week, an investigation by Bloomberg revealed that thousands of Amazon employees around the world are listening in on Amazon Echo users.
As we have been explaining across media, we believe that by using default settings and vague privacy policies which allow Amazon employees to listen in on the recordings of users’ interactions with their devices, Amazon risks deliberately deceiving its customers.
Amazon has so far been dismissive, arguing that people had the options to opt out from the…
Content type: News & Analysis
Protest movements throughout history have helped to shape the world we know today. From the suffragettes to the civil rights movement, and to contemporary movements such as those focusing on LGBTIQ+ rights, protests have become a vital way for many, who feel powerless otherwise, to have their voices heard.
But now, making the decision to attend a protest comes with consequences that you may very well be unaware of. This is because policing and security services, always hungry in their quest to…
Content type: News & Analysis
Earlier this month, Brunei attracted international condemnation for a new law that will make gay sex punishable by death. While this is clearly abhorrent, Brunei is not the only country with explicit anti-gay laws.
Homosexuality is criminalised in over 70 countries around the world. And even in countries where gay sex is legal, such as the US, the LGBTIQ+ community still faces discriminatory surveillance and profiling by law enforcement agencies.
Through using the Internet and mobile apps,…
Content type: Examples
In February 2019, with a general election expected in May, the Australian government revealed that Australia's main political parties had been hacked by a "sophisticated state actor". The Australian Cyber Security Centre uncovered the hack while investigating a just-revealed hack of the Australian parliament's computer networks. A spokeswoman for China's ministry of foreign affairs denied the suggestion that China was responsible.
https://www.ft.com/content/9de75c4a-331f-11e9-bd3a-8b2a211d90d5…
Content type: Examples
In 2015, officials within the US Treasury Department Office of Terrorist Financing and Financial Crimes unit used a network of private Gmail and Hotmail accounts set up by the Russians with the stated goal of jointly defeating ISIS. Soon, however, instead the Russian financial crimes agency was using the back channel to seek sensitive information on enemies in the US and elsewhere - individuals such as the newspaper publisher Alexander Lebedev, a company tied to the Panama Papers, and nearly…
Content type: Examples
In November 2018, the Spanish senate approved 220-21 an online data protection law intended to ensure compliance with the General Data Protection Regulation with an added amendment that allowed political parties to use personal data obtained from web pages and other publicly accessible sources for political purposes during campaign periods. Spain's Platform for the Defence of Freedom of Information criticised the law's potential to allow parties to create ideological profiles and emulate the…
Content type: Examples
During the campaign leading up to the 2018 US midterm elections, the email accounts of four senior aides at the National Republican Congressional Committee were surveilled for several months. The intrusion was detected in April 2018 by an NRCC vendor, who alerted the committee and its cybersecurity contractor; the NRCC then began an internal investigation and alerted the FBI. House Republicans did not learn of the incident until Politico called the NRCC with questions about the attack in…
Content type: News & Analysis
According to the International Organization for Migration, an estimated 258 million people are international migrants – that is, someone who changes their country of usual residence, That’s one in every 30 people on earth.
These unprecedented movements levels show no sign of slowing down. It is predicted that by 2050, there will be 450 million migrants across the world.
Nowadays, it is politically acceptable to demonise migrants, and countless leaders have spewed divisive and xenophobic…
Content type: Long Read
The UK border authority is using money ring-fenced for aid to train, finance, and provide equipment to foreign border control agencies in a bid to “export the border” to countries around the world.
Under the UK Border Force’s “Project Hunter”, the agency works with foreign security authorities to bolster their “border intelligence and targeting” capabilities with UK know-how and equipment.
As well as the provision of equipment and training, the Border Force is also advising countries on…
Content type: Long Read
Cellebrite, a surveillance firm marketing itself as the “global leader in digital intelligence”, is marketing its digital extraction devices at a new target: authorities interrogating people seeking asylum.
Israel-based Cellebrite, a subsidiary of Japan’s Sun Corporation, markets forensic tools which empower authorities to bypass passwords on digital devices, allowing them to download, analyse, and visualise data.
Its products are in wide use across the world: a 2019 marketing…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: News & Analysis
Planning and participating in peaceful protests against governments or non-state actors’ policies and practices requires the capacity of individuals to communicate confidentially without unlawful interference. From protests in support of LGBTI rights to protests against specific projects that undermine local communities’ wellbeing, these movements would not have been possible without the ability to exchange ideas and develop plans in private spaces.
Unlawful interference with…
Content type: Advocacy
Privacy International's submission to the Human Rights Committee on a future General Comment on Article 21 of the International Covenant on Civil and Political Rights (ICCPR).
In this submission, Privacy International aims to provide the Committee with information on how surveillance technologies are affecting the right to peaceful assembly in new and often unregulated ways.
Based on Privacy International’s research, we provide the following observations:
the relationship between right…
Content type: State of Privacy
Introduction
Acknowledgment
The State of Surveillance in Tunisia is the result of an ongoing collaboration by Privacy International and partners.
On 14 February 2023, the United Nations High Commissioner for Human Rights voiced concern over the deepening crackdown in Tunisia targeting perceived political opponents of President Kais Saied as well as civil society.
We have updated this page to reflect important changes in the state of surveillance in Tunisia.
Key privacy facts
1.…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
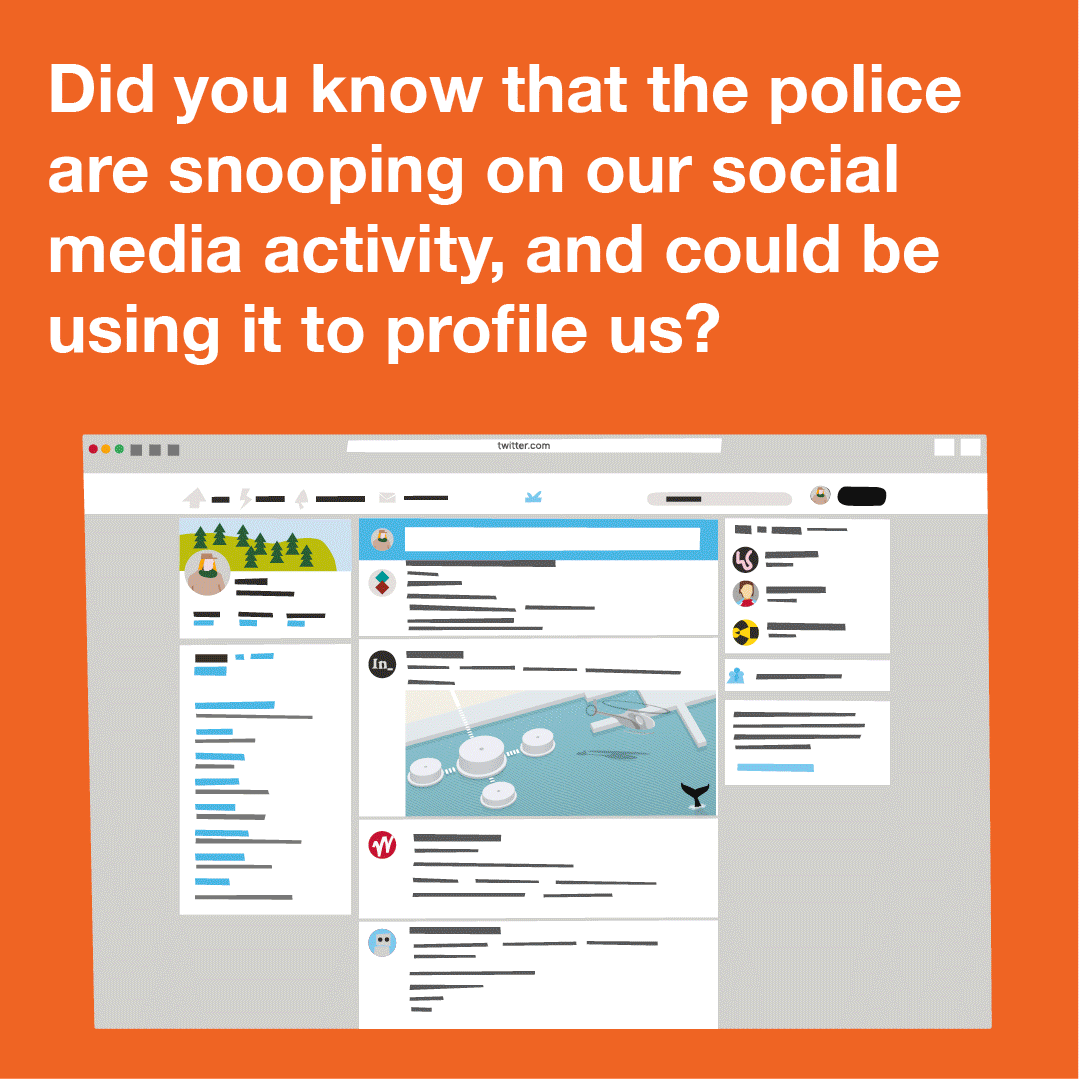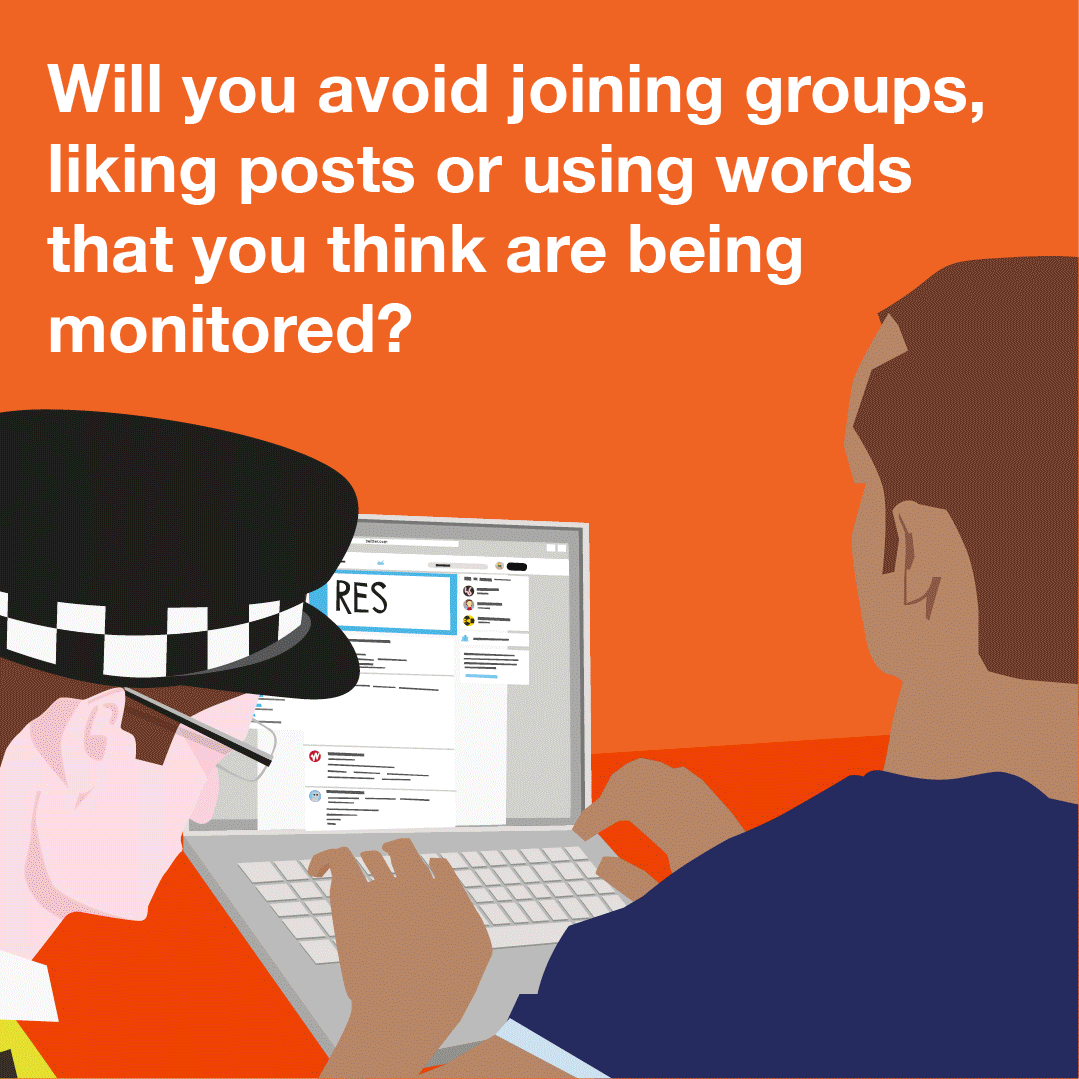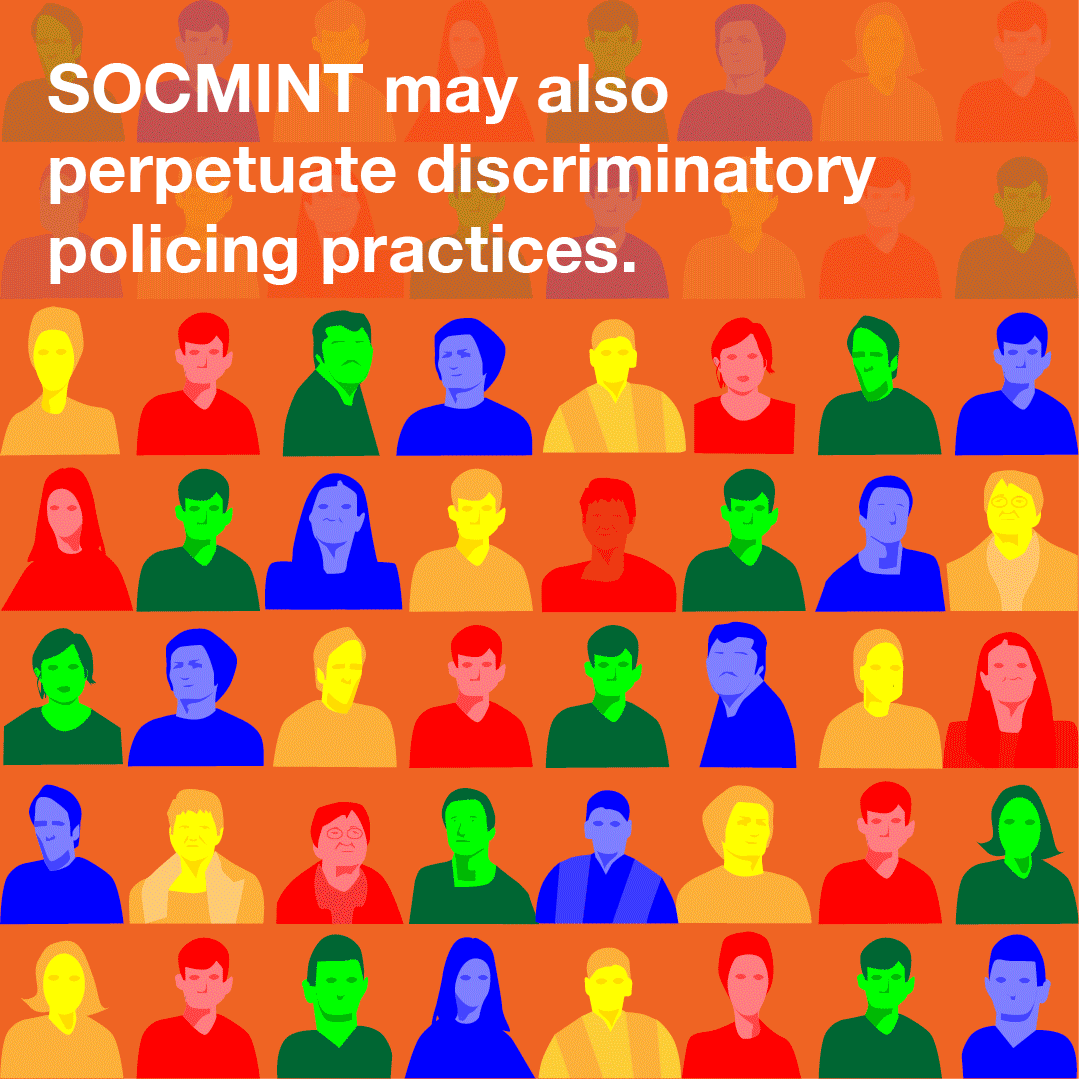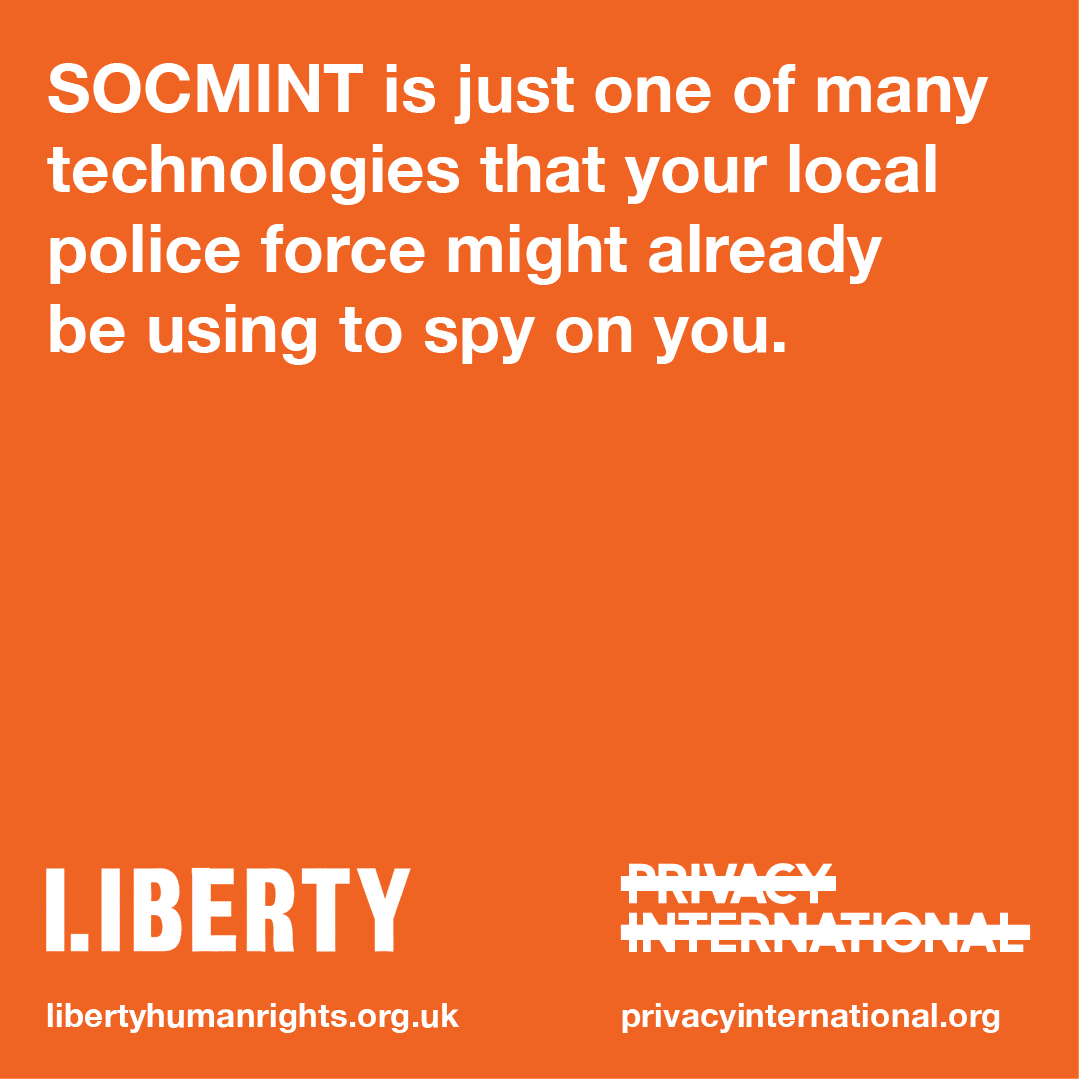
Content type: Explainer graphic
You can also read a more detailed explainer about social media intelligence (SOCMINT) here.
Content type: News & Analysis
At Privacy International, we talk about: “the world being on fire.”We say it to talk about the recurring threats to our democracies, the elections of authoritarian leaders, the current political climate… Or the actual climate. More often than not, we use it to talk about the (lack of) security in the design and implementation of computer systems.
But there is another kind of fire. The fourth wave of feminism – the one that contributed to the protests following the 2012 gang rape of…
Content type: News & Analysis
Image source: Oxfam
This piece was co-authored with Ruhiya Seward, Senior Program Officer at IDRC and originally appeared here.
What if in trying to make development more equitable we’re creating risks that disproportionately impact people based on their gender?
Development programming aims to be both sustainable and equitable in part by recognizing the implications of inequality in its many forms, whether by gender, ethnicity, socioeconomic status, or geolocation. The adoption of the…
Content type: Report
Whose privacy are we fighting for when we say we defend the right to privacy? In this report we take a hard look at the right to privacy and its reality for women, trans and gender diverse people. We highlight how historically privacy has been appropriated by patriarchal rule and systems of oppression to keep women, trans and gender diverse people in the private sphere.
For us, this report is also an opportunity to show how surveillance and data exploitation are also uniquely affecting…
Content type: Report
6 March 2019
Privacy International (PI) has written Facebook to express our concern and request urgent answers regarding its policy on the sharing of mobile phone numbers of its users.
Alarmingly, recent reports say that some of the phone numbers provided by users for the express purpose of two-factor authentication (2FA) as a way of securing their accounts are now made searchable across the platform by default.
PI is concerned that allowing such numbers to be searchable…
Content type: Advocacy
In October 2018, Privacy International submitted to the public consultation on the “Consolidated Guidance to Intelligence Officers and Service Personnel on the Detention and Interviewing of Detainees Overseas, and on the Passing and Receipt of Intelligence Relating to Detainees” (“Consolidated Guidance”) held by the Investigatory Powers Commissioner’s Office (“IPCO”).Privacy International’s submission addresses the portions of the Consolidated Guidance on “the Passing and Receipt…
Content type: Examples
In 2017, Alphabet's Sidewalk Labs began a collaboration with Waterfront Toronto intended to turn a 12-acre lakeside area into a "smart city" equipped with sensors and responsive infrastructure. Frustration that Torontonians' data privacy concerns were not being addressed led Saadia Muzaffar, founder of TechGirls Canada, to resign from Waterfront Toronto's Digital Strategy Advisory Panel in October 2018. In a lengthy resignation letter, she called attention to the risk that embedding poorly…
Content type: Examples
In July 2018, Facebook announced it was investigating whether the Boston-based company Crimson Hexagon had violated the company's policies on surveillance. Crimson Hexagon markets itself as offering "consumer insights". Its customers include a Russian non-profit with ties to the Kremlin, and multiple US government agencies. After pressure from civil liberties groups, Facebook put a policy in place in March 2017 barring the use of members' data for the purposes of government surveillance.…
Content type: News & Analysis
Palantir and the UN’s World Food Programme (WFP) are partnering for a reported $45 million. Palantir, a US-based company that sells data software and has been the centre of numerous scandals.
The World Food Programme provides assistance in food and nutrition to around 92 million people each year. Systems that are produced in agreements such as the one between WFP and Palantir increase risks to the people the they are attempting to help. There are risks to both individuals and whole populations…
Content type: Long Read
Over the past year, the Privacy International Network has uncovered, campaigned, and advocated on how trends in surveillance and data exploitation are increasingly affecting our right to privacy.
To celebrate Data Privacy Day on 28 January, we shared a full week of stories and research, exploring how countries are addressing data governance, and the implications for our security and privacy.
Monday - Exposing Harms, Fighting Back
It is often communities who are already the most…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
Since 2014, the Privacy International Network has produced State of Privacy reports, a collaborative effort to record global privacy and related issues.
As we close Data Privacy Week this year, we’re pleased to share an update of the…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
Innovations in surveillance and data exploitation present challenges in the fight to protect personal data across the world. Since 1990 we have been working to build a global movement through working with others - from leading civil society…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
In the era of smart cities, the gap between the internet and the so-called physical world is closing. Gone are the days, when the internet was limited to your activities behind a desktop screen, when nobody knew you were a dog.
Today, the…