Search
Content type: Examples
The 20 years since the 9/11 attacks have fundamentally changed the way the New York Police Department operates, leading it to use facial recognition software, licence plate readers, and mobile X-ray vans, among other surveillance tools for both detecting and blocking potential terrorist attacks and solving minor crimes. Surveillance drones monitor mass protests, antiterrorism officers interrogate protesters, and the NYPD’s Intelligence Division uses antiterror tactics against gang violence and…
Content type: Examples
The whistleblower said they were unable to find any legitimate reason for the high volume of the requests for location information. “There is no other explanation, no other technical reason to do this. Saudi Arabia is weaponising mobile technologies,” the whistleblower claimed.
The data leaked by the whistleblower was also seen by telecommunications and security experts, who confirmed they too believed it was indicative of a surveillance campaign by Saudi Arabia.
The data shows requests for…
Content type: News & Analysis
The elections in our midst here, there, and everywhere are increasingly resulting in governments who introduce policies that result in leaps backwards for dignity, equality, civil liberties, and the rule of law. Whether it is Poland or the Philippines, governments are overriding essential safeguards.
This week Britain’s proposed surveillance legislation took another step toward normalising mass surveillance. The United States of America has long promoted mass surveillance and maintains its…
Content type: News & Analysis
This piece was written by PI Research Officer Edin Omanovic and originally appeared here.
Whatever happens over the next few years, if there is to be a storm, then it is best to prepare. It is essential that western liberal democratic societies are resilient enough to uphold their fundamental values.
One of the UK’s biggest security assets is one of its biggest security threats. The UK’s spies have access to and are allowed to exercise some of the most sophisticated electronic…
Content type: Long Read
This piece was written by Ashley Gorski, who is an attorney at the American Civil Liberties Union, and PI legal officer Scarlet Kim and originally appeared in The Guardian here.
In recent weeks, the Hollywood film about Edward Snowden and the movement to pardon the NSA whistleblower have renewed worldwide attention on the scope and substance of government surveillance programs. In the United States, however, the debate has often been a narrow one, focused on the…
Content type: Long Read
This week, Privacy International, together with nine other international human rights NGOs, filed submissions with the European Court of Human Rights. Our case challenges the UK government’s bulk interception of internet traffic transiting fiber optic cables landing in the UK and its access to information similarly intercepted in bulk by the US government, which were revealed by the Snowden disclosures. To accompany our filing, we have produced two infographics to illustrate the…
Content type: News & Analysis
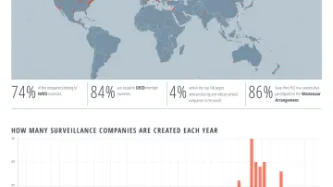
Privacy International is today proud to release the Surveillance Industry Index (SII), the world's largest publicly available educational resource of data and documents of its kind on the surveillance industry, and an accompanying report charting the growth of the industry and its current reach.
The SII, which is based on data collected by journalists, activists, and researchers across the world is the product of months of collaboration between Transparency Toolkit and Privacy…
Content type: Long Read
The recent back and forth between Apple and the FBI over security measures in place to prevent unauthorised access to data has highlighted the gulf in understanding of security between technologists and law enforcement. Modern debates around security do not just involve the state and the individual, the private sector plays a very real role too. There are worrying implications for the safety and security of our devices. Today, a new company stepped in to this discussion -- though it had been…
Content type: News & Analysis
According to Snowden documents analysed by Privacy International, the Australian Signals Directorate had access to and used PRISM, a secret US National Security Agency program which provides access to user data held by Google, Facebook and Microsoft.
This is the third spy agency of the 'Five Eyes' alliance confirmed to have had secret access to Silicon Valley company data - an alliance whose rules and policies remain classified. Earlier this year, a British court ruled that GCHQ access to…
Content type: News & Analysis
Privacy is a human right, and needs very clear legal protections. 'Safe Harbor' was clear as mud and placed privacy rights globally at risk.
Today's European Court of Justice decision should be no surprise for industry or governments. For over fifteen years the U.S. Government has resisted implementing basic and effective privacy law and created absurd stopgap measures because U.S. Congress is incapable of acting upon what consumers and citizens have long asked for. The fact over 100 countries…
Content type: News & Analysis
While two of the Vice journalists who were recently arrested in Turkey and charged with terror offenses have now been released, this remain a deeply concerning incident.* It is the latest episode in what is a pincer movement against our right to protect our data.
Two British journalists and their Turkey-based Iraqi translator working for VICE News were arrested last Thursday and charged with "engaging in terrorist activity". According to Turkish authorities, one member of the group had an…
Content type: News & Analysis
Here are eight things we have learned from this week's hack of some 400GB of internal company material and correspondence from Italian surveillance company Hacking Team.
The Citizen Lab was right
The Citizen Lab, who in 2014 identified some 21 countries that are potential customers of Hacking Team, were right about all of them. A 2015 report stated that there was likely to be more. In fact, at least 45 countries are purchasers of Hacking Team's…
Content type: Press release
British intelligence services acted unlawfully in accessing millions of people’s personal communications collected by the NSA, the Investigatory Powers Tribunal ruled today. The decision marks the first time that the Tribunal, the only UK court empowered to oversee GHCQ, MI5 and MI6, has ever ruled against the intelligence and security services in its 15 year history.
The Tribunal declared that intelligence sharing between the United States and the…
Content type: News & Analysis
The following is an excerpt from an Op-Ed written in the New Zealand Herald by Privacy International's Legal Officer Anna Crowe:
Since the release of documents by Edward Snowden nearly a year ago, New Zealand has often been seen as a passive participant in the Five Eyes intelligence-sharing alliance, not unlike a good kid hanging out with the wrong crowd.
However, Snowden documents released last month and the news that New Zealand appears to be sharing intelligence…
Content type: News & Analysis
May Day serves as a timely reminder that across their history, intelligence services have targeted trade unions and other organisations working for progressive social change.
Intelligence agencies have sought to justify expanded surveillance capabilities on the basis of pressing national security threats, particularly terrorism; however, as the Snowden revelations have highlighted, intelligence agencies actually often use these capabilities to monitor organisations that promote human…
Content type: News & Analysis
A strong, unified voice from the tech industry is absolutely essential to reforming the mass and intrusive surveillance programs being run by the Five Eyes, so we welcome today's statement from AOL, Apple, Google, Facebook, LinkedIn, Microsoft, Twitter, and Yahoo.
Companies have obligations to respect human rights and not be complicit in mass surveillance. Given what has been publicly revealed over the past six months, we must know for certain that the companies we entrust with our information…
Content type: Long Read
The recent revelations, made possible by NSA-whistleblower Edward Snowden, of the reach and scope of global surveillance practices have prompted a fundamental re- examination of the role of intelligence services in conducting coordinated cross-border surveillance.
The Five Eyes alliance of States – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the…
Content type: News & Analysis
With the launch of the "Eyes Wide Open" project, Privacy International has put together a fact sheet about the secretive Five Eyes alliance. Consider this a guide to the secret surveillance alliance that has infiltrated every aspect of the modern global communications system.
Beginning in 1946, an alliance of five English-speaking countries (the US, the UK, Australia, Canada and New Zealand) developed a series of bilateral agreements over more than a decade that became known as the UKUSA…
Content type: Press release
The United Nations General Assembly should approve a new resolution and make clear that indiscriminate surveillance is never consistent with the right to privacy, five human rights organizations said in a November 21, 2013 letter to members of the United Nations General Assembly.
After heated negotiations, the draft resolution on digital privacy initiated by Brazil and Germany emerged on November 21 relatively undamaged, despite efforts by the …
Content type: Press release
General Assembly Should Pass Strong Resolution on the Right to Privacy in the Digital Age
(New York, November 21, 2013) – The United Nations General Assembly should approve a new resolution and make clear that indiscriminate surveillance is never consistent with the right to privacy, five human rights organizations said in a November 21, 2013 letter to members of the United Nations General Assembly.
After heated negotiations, the draft resolution on digital…
Content type: News & Analysis
http://www.spiegel.de/international/world/how-the-nsa-spies-on-international-bank-transactions-a-922430.html*Update: The European Parliament has voted to recommend suspension of its Terrorist Finance Tracking Program (TFTP) agreement with the US. The vote in favour of suspension only highlights how the NSA’s reported activities have undermined the agreement. Negotiations should immediately commence to strengthen the privacy and redress provisions, to ensure that governments…
Content type: Press release
Civil society organisations today called upon the members of the Human Rights Council to assess whether national surveillance laws and activities are in line with their international human rights obligations.
The Snowden revelations have confirmed that governments worldwide continue to expand their spying capabilities, at home and abroad. Widespread surveillance is being conducted in violation of individuals’ rights to privacy and free expression, and is seldom regulated by strong legal…
Content type: News & Analysis
Below is an excerpt of an article that recently appeared in Melbourne, Australia's The Age, written by Carly Nyst, Head of International Advocacy at Privacy International:
"Mass surveillance of a country's citizens by its government can no longer be said to be the preserve of authoritarian and dictatorial states.
The publication last week by The Guardian of classified National Security Agency documents has exposed the extent of surveillance by the US government, throwing into question…
Content type: News & Analysis
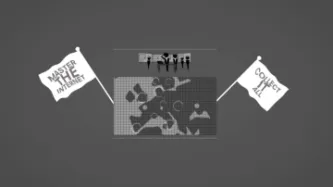
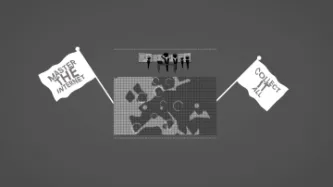
Privacy International is proud to announce our new project, Eyes Wide Open, which aims to pry open the Five Eyes arrangement and bring it under the rule of law. Read our Special Report "Eyes Wide Open" and learn more about the project below.
For almost 70 years, a secret post-war alliance of five English-speaking countries has been building a global surveillance infrastructure to “master the internet” and spy on the worlds communications. This arrangement binds together the US, UK, Canada,…
Content type: News & Analysis
The APEC Data Privacy Subgroup (DPS) commenced a new five year work programme at a meeting in Moscow in February 2012. This follows the commitment by APEC Leaders in late 2011 to the Cross Border Privacy Rules (CBPR) system as one way implementing the APEC Data Privacy Framework.
The Joint Oversight Panel was formed at the DPS meeting in Moscow and comprises members from the US (chair), Chinese Taipei and Mexico, with the chair of the DPS (from Canada) as alternate – who will…
Content type: Report
The US does not have a general overarching privacy law like European Data Directive or the sweeping privacy protections contained in the European declarations of rights. The EU-US accord cites several laws, which it claims, give privacy rights to non-US persons. None of the cited laws offer any real substantive or procedural protections for Europeans. As explained below, the one law – the Privacy Act 5 U.S.C 552a – that could offer some modest protections is tellingly not even mentioned.
But…
Content type: News & Analysis
The second 2011 meeting of the APEC Privacy Subgroup took place in San Francisco in mid September, and finalised the package of documents that comprise the Cross Border Privacy Rules (CBPR) system. Endorsed by the parent Electronic Commerce Steering Group (ECSG), these will now go forward for ratification by Ministers in Hawaii in November, and subsequent implementation. The Subgroup’s 2012 Work Plan envisages establishment of the Joint Oversight Panel (JoP), commencement of…
Content type: News & Analysis
For the past couple of months we have been discussing with Google their transparency plans regarding governments accessing data held by Google. Last week Google released initial data on how many requests for data were coming from which governments.
We congratulate Google on this first step, and we believe that by seeking answers to some additional questions, greater clarity may yet emerge. Of course we have many more questions. We hope that this is the first step in an ongoing dialogue with…