Search
Content type: Case Study
In this next leap to year 2030, Amtis lives the life of a data labourer, being paid wages for data inputs. Here’s how Amtis begins the story:
I am in my green pyjamas, but I can’t say for sure if it’s morning or evening. My eyes are red from staring at screens. I am discouraged and very tired. Of course, all these emotions and reactions are registered by my Playbour – my pocket-sized smart console that has basically become my entire life. It’s my connection to family, friends and the world; my…
Content type: Case Study
In 2030 Amtis finds a future where property rights for data were adopted. Here’s how this future plays out:
My data, my turf. This was the first graffiti I saw as I was walking down the street and I said to myself, “Yeah, big corp, we’re going to get you good!”. I am fed up with companies making insane amounts of money from my data. If this is the game we’re playing, I want my fair share.
I was not the only one thinking like this. A few years back there was a strong push towards adopting…
Content type: Advocacy
Privacy International has today sent letters to leading social media platforms to ask what they're doing to protect their users' from dangerous surveillance by government immigration authorities.
The letter comes following the implementation of plans by US authorities to require nearly all visa applicants to hand over identifiers of all social media accounts they have used in the previous five years, or face “serious immigration consequences”.
The move not only represents…
Content type: News & Analysis
Privacy International has joined a global coalition of privacy campaigners, tech companies, and technology experts to respond to proposals by British intelligence chiefs aimed at allowing them access to encrypted messaging apps such as WhatsApp or Signal.
If implemented, the proposals would allow government authorities to force messaging platforms to silently add a law enforcement participant to a group chat or call.
Such a capability poses serious threats to…
Content type: Examples
GDPR complaints about Real-Time Bidding (RTB) in the online advertising industry were filed today with Data Protection Authorities in Spain, the Netherlands, Belgium, and Luxembourg. The complaints detail the vast scale of personal data leakage by Google and other major companies in the “Ad Tech” industry. This week marks one year since the introduction of the GDPR.
The new complaints have been filed by Gemma Galdon Clavell (Eticas Foundation) and Diego Fanjul (Finch), David Korteweg (…
Content type: Examples
In an effort to improve political advertising transparency, Canada drafted a Bill that requires companies to develop ad libraries, to which ads are added immediately in order for researchers, journalists, and other people to be able to search and understand how political actors are targeting ads. In response, Google announced that it would blanket-ban all political ads in Canada, saying the company was unable to comply with the new law. Google’s decision shows both that the current state of…
Content type: Examples
The two leading Presidential candidates in Ukraine's 2019 elections have expressed frustration at major social media platform's seemingly lack of assistance combatting disinformation and bots. Bots flood social media networks and can promote content or flood platforms with pull requests to have a piece of content taken down. Campaigns are unable to directly contact Google, YouTube, and Facebook for assistance directly and waste resources constantly fighting against bot armies.
https://www.…
Content type: Examples
Simultaneous complaints have been filed with European data protection authorities against Google and other ad tech firms. The complainants are being made by Dr Johnny Ryan of Brave, the private web browser, Jim Killock, Executive Director of the Open Rights Group, and Michael Veale of University College London. The complaint notifies European regulators of a massive and ongoing data breach that affects virtually every user on the web.
Content type: Examples
Panoptykon Foundation, the Warsaw based digital rights organization, has joined in the complaints filed in the UK and Ireland in September by Jim Killock of the Open Rights Group, Michael Veale of University College London, and Dr Johnny Ryan of Brave, by filing a new complaint in Poland. Together, the complainants in Ireland, Poland, and the UK, have also filed new evidence today with the national data protection authorities of Ireland, Poland, and the United Kingdom, that reveals how ad…
Content type: Examples
Dr Johnny Ryan filed a formal complaint with the Irish Data Protection Commission against IAB Europe, the tracking industry’s primary lobbying organization. The complaint was filed against IAB Europe’s use of an unlawful “cookie wall” on its website. Visitors to IAB Europe’s website, www.iabeurope.eu, are forced to accept tracking by Google, Facebook, and others, which may then monitor them.
Content type: Examples
In August 2018, Apple forced Facebook to remove its Onava VPN from the App Store because the Facebook had been using it to harvest data across multiple apps and track user activity. In January 2019, a TechCrunch investigation revealed that in a separate part of the same programme Facebook had been paying users aged 13 to 35 to download a "Facebook Research" VPN and give it root access to their devices to enable it to collect data on their usage habits. The programmed, known as "Project Atlas",…
Content type: Examples
In February 2019 Google engineers announced that they had created faster, more efficient encryption system that could function on less-expensive Android phones that were too low-powered to implement existing full-device encryption. The scheme, known as Adiantum, uses established and well-vetted encryption tools and principles. Android has required smartphones to support encryption since 2015's version 6, but low-end devices were exempt because of the performance hit. It will now be up to device…
Content type: Examples
In October 2018, Google developers announced Manifest V3, a new standard for developing extensions for its Chrome web browser. One of the modifications included replacing the API used by extensions that need to intercept and work with network requests. The new API, DeclarativeNetRequest, limits the number of network requests an extension can access; the result was to muzzle third-party adblockers but not the new one Google was building in. Google claimed that implementing a maximum value was…
Content type: Examples
In November 2018 Bidooh announced it was developing an intelligent and automated digital billboard advertising platform that it said would leverage facial recognition and blockchain technology to track engagement. Billboard advertising is valued globally at almost $34.8 billion a year. Bidooh has said it considers itself the "Google Adwords" for digital billboard advertising; it intends the new system to be able to target passers-by based on criteria such as age, gender, facial hair, and…
Content type: Long Read
CEOs of the big tech companies have all recently discovered the value of privacy. On Tuesday, 30 April 2019, Mark Zuckerberg, announced his future plans to make Facebook a "privacy-focused social platform". This was followed by Google's Sundar Pichai demand that “privacy must be equally available to everyone in the world.” Meanwhile, Twitter's Jack Dorsey, has described the General Data Protection Regulation (GDPR) as "net-positive", while Apple had already positioned itself as the champion of…
Content type: Examples
In February 2019, the cybersecurity company Trend Micro found that at least 29 beauty and photo editing apps that had been downloaded more than 4 million times from Google's Play Store included code that pushed full-screen ads for fraudulent or pornography content or that directed users to phishing sites by making them believe they had won a contest. A second group of camera apps that claimed to improve photos actually uploaded them to a remote server controlled by the app developer and then…
Content type: Long Read
Image Source: "Voting Key" by CreditDebitPro is licensed under CC BY 2.0
Democratic society is under threat from a range of players exploiting our data in ways which are often hidden and unaccountable. These actors are manifold: traditional political parties (from the whole political spectrum), organisations or individuals pushing particular political agendas, foreign actors aiming at interfering with national democratic processes, and the industries that provide products that …
Content type: News & Analysis
The first half of 2018 saw two major privacy moments: in March, the Facebook/ Cambridge Analytica scandal broke, followed in May by the EU General Data Protection Regulation ("GDPR") taking effect. The Cambridge Analytica scandal, as it has become known, grabbed the attention and outrage of the media, the public, parliamentarians and regulators around the world - demonstrating that yes, people do care about violations of their privacy and abuse of power. This scandal has been one of…
Content type: Examples
According to research conducted by Ronan Chardonneau, a French associate professor of digital marketing at Angers University, none of the websites of the eleven candidates' in the 2017 French presidential elections, that he looked into respected CNIL's directives regarding information that should be available on the website and consent requirements for data collection. According to this research, nine of the candidates used Google Analytics, without activating the option to anonymize data…
Content type: Advocacy
This week a public debate on facial recognition will take place in Westminster Hall.
Following a public request for comment by Darren Jones MP (Science and Technology Committee), we sent our responses to the questions asked.
Below you can find the integral content of our letter.
1. Would you consent to the police scanning your face in a crowd to check you’re not a criminal?
Facial recognition technology uses cameras with software to match live footage of people in public with…
Content type: Explainer
It’s tough to minimise targeted ads on phones because ads can be delivered based on data from the device level (such as what operating system your phone is using or based on unique numbers that identify your phone), browser level (what you search for within a browser), and within the apps you use. An app could target ads at you based on your location (tied to your unique device id number(s)) for example. Apps, including Instagram, direct you to opt-out of targeted ads at the device level.…
Content type: News & Analysis
Photo by DAVID ILIFF. License: CC-BY-SA 3.0
Between 23 and 26 May 2019 Europeans will be voting to elect members of the European Parliament.
Since the last elections in 2014, much has changed within and without the European Union: the rise of nationalism and Euroscepticism, the protracted armed conflict in Ukraine and the occupation of Crimea by Russia, the new political orientation of the United States, just to name a few.
Among the new challenges facing these elections is…
Content type: Long Read
“Truth exists, but you have to find it”, Oleksandra Matviychuk of Ukraine’s Center for Civil Liberties told me as I interviewed her in central Kyiv one week before the 2019 Ukrainian run-off election, “and in order to do so you have to make some effort”. We’re talking about her experience working on the ground in Ukraine, a country with a long history of battling against disinformation.
Activists in Ukraine have long experience navigating the noisy and chaotic environment that disinformation…
Content type: Long Read
This image was found here.
Spain is holding a national general election on April 28 (its third in four years). Four weeks later Spaniards will again go to the polls to vote in the European Parliament elections. At Privacy International we are working to investigate and challenge the exploitation of people’s data in the electoral cycle including in political campaigns. This includes looking at the legal frameworks governing the use of data by political parties and their…
Content type: News & Analysis
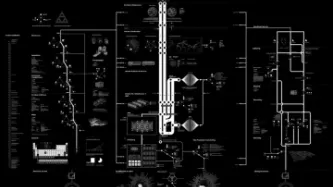
Image: Anatomy of an AI system: a map of the many processes — extracting material resources, data, and human labor — that make an Amazon Echo work. Credit: Kate Crawford and Vladan Joler
With over 6.3 million Amazon Echo devices worldwide, there is a good chance these constantly active devices will record criminal behavior.
Bloomberg, who recently reported on yet another creepy feature, that Amazon workers are listening to what you tell Alexa, were told by workers…
Content type: Examples
A startling amount of the internet is fake in one way or another, studies found in 2018. Less than 60% of web traffic is human; a 2013 study found that at least half of YouTube traffic was bots masquerading as people; in November 2018 the US Justice Department revealed that eight people were accused of stealing $36 million in digital advertising fraud that involved sending fake traffic to spoofed websites which were made to look to advertisers like premium publishers. Also fake in at least some…
Content type: Examples
A December 2018 report prepared by the Oxford Internet Institute's Computational propaganda Research Project and the network analysis firm Graphika for the US Senate Intelligence Committee found that the campaign conducted by Russia's Internet Research Agency during the 2016 US presidential election used every major social media platform to deliver messages in words, images, and videos to help elect Donald Trump - and stepped up efforts to support him once he assumed office. The report relied…
Content type: Examples
In the run-up to the May 2019 European Parliament elections, Google announced it would launch a new set of transparency tools to combat voter manipulation. Before being allowed to buy advertising on Google platforms, campaigns will be required to verify their identity, and approved ads will be required to display the identity of their purchaser. Google will build a real-time searchable database of all political ads and show their purchasers, costs, and demographics. Facebook announced similar…
Content type: News & Analysis
PI has today written to Google, Instagram, Snapchat, TicTok, Twitter, YouTube, and WhatsApp to ask for more information about their steps to tell people why they are seeing ads. Facebook recently announced expanding the company's ad transparency measures to include more information about why an ad or content appears in a user's newsfeed. While Facebook has a lot more to do, it is important that all technology companies provide advertising transparency.
Recently, we have seen how platforms…