Advanced Search
Content Type: Advocacy
On 3 July 2025, the General Conference of the International Labour Organization (ILO) adopted a resolution committing the ILO to adopt a Convention supplemented by a Recommendation concerning decent work in the platform economy following a second discussion on this issue in 2026. PI welcomes the ILO's decision as a step in the right direction to protect platform workers who have been at the forefront of new forms of data exploitation in the workplace as we have been documenting for many…
Content Type: News & Analysis
Yesterday the Investigatory Powers Tribunal announced next steps in Apple’s and PI’s challenges to the purported UK order undermining iCloud’s security.The Tribunal declared that it will aim to hear much of Apple’s case, as well as PI and our co-claimants’, in public based on assumed facts. The Tribunal will convene a seven day hearing to be scheduled in early 2026. Its aim will be to hear Apple’s case and PI’s case during those seven days.This ‘case management order’ follows submissions from…
Content Type: Long Read
Period tracking apps and the rollback of reproductive rightsThe aftermath of the overturning of Roe v. Wade in the United States (US) sparked widespread debate and concern that data from period tracking apps could be use to criminalise those seeking abortion care.While the surveillance and criminalisation of reproductive choices are neither new nor unique to the US, the scale and intensity of today’s crisis continue to grow. To put it into perspective, 22 million women and girls of reproductive…
Content Type: Long Read
If you’ve ever used TikTok, Instagram, or X/Twitter, you will already be familiar with centralised social media.Centralised social media means big company owns the app, controls the software, and keeps all your data.For example, ByteDance makes TikTok. They own it, run the servers, decide what you see in your feed, and hold onto every video you like or comment on. They call the shots when it comes to your data.But what if social media didn’t work that way? What if no single company was in…
Content Type: Long Read
The security of our devices, applications and infrastructure is paramount to the safe functioning of our digital lives. Good security enables trust in our systems, it is fundamental to protecting the critical information we store and exchange through networks and devices. Similar to how we physically secure our homes, offices and schools, securing devices and software allows us to operate in safe and trusted environments where our security is guaranteed and protected.Security for information…
Content Type: Press release
FOR IMMEDIATE RELEASELONDON - 7 April 2025The Investigatory Powers Tribunal (IPT) has confirmed it will hear Privacy International, Liberty and two individuals’ challenge to the legality of the Home Secretary’s decision to use her powers to secretly force Apple to allegedly give the UK Government access to users’ secured data stored on iCloud. The challenge will also cover the legality of the Government issuing these types of notices at all. Privacy International and Liberty,…
Content Type: Long Read
On 13 March 2025, we filed a complaint against the UK government challenging their use of dangerous, disproportionate and intrusive surveillance powers to undermine the privacy and security of people all over the world. Here, we answer some key questions about the case and the recent events that led to this development.Note: This post was last updated on 13 March 2025.What’s the fuss about?A month ago, it was reported that the UK government demanded Apple Inc – maker of the iPhone, iPads, Macs…
Content Type: Advocacy
We believe the Government's position of refusing to confirm or deny the existence of the Technical Capability Notice or acknowledge Apple's appeal is untenable and violates principles of transparency and accountability.
Content Type: Explainer
Imagine this: a power that secretly orders someone anywhere in the world to abide and the receiver can’t tell anyone, can’t even publicly say if they disagree, and can’t really question the power in open court because the secret order is, well, secret. Oh and that power affects billions of people’s security and their data. And despite being affected, we too can’t question the secret order.In this piece we will outline what’s ridiculous, the absurd, and the downright disturbing about what’s…
Content Type: Advocacy
Our submission made the following recommendations to the Committee regarding the Kenya:Review and amend the proposed digital identity system, the Maisha Numba, to ensure it aligns with Kenya’s national and international human rights obligations in its design and implementation, and adopts legal, policy and technical safeguards to prevent exclusion and marginalisation.Ensure that measures taken to develop digital public infrastructures abide by Kenya’s national and international human rights…
Content Type: Advocacy
When it comes to elections around the world, we find ourselves in a terrain that is more and more populated by digital technologies, which have an increasingly critical impact upon the realisation of democracy. Digital technologies used in the context of elections offer new opportunities to support voter participation, whilst simultaneously posing increasing challenges for voters and those who manage and oversee elections. The introduction of technologies into electoral systems in countries…
Content Type: Long Read
Social media is now undeniably a significant part of many of our lives, in the UK and around the world. We use it to connect with others and share information in public and private ways. Governments and companies have, of course, taken note and built fortunes or extended their power by exploiting the digital information we generate. But should the power to use the information we share online be unlimited, especially for governments who increasingly use that information to make material…
Content Type: Video
The case dealt with a Russian law obliging telecommunications service providers to indiscriminately retain content and communications data for certain time periods, as well as a 2017 disclosure order by the Russian Federal Security Service requiring Telegram Messenger company to disclose technical information which would facilitate “the decoding of communications”.Links:PI case pageECtHR judgment in the Podchasov casePI's work on encryptionPI's report on End-to-End Encryption (E2EE)More…
Content Type: Long Read
In June 2023, the UK government announced its proposal to expand its surveillance powers by, among others, forcing communications operators to undermine encryption or abstain from providing security software updates globally. Building on our response to the government’s plans, this piece explains why what they want to do puts every one of us at risk.
Why your trust (to technologies you use) matters
Surveillance and privacy are complex concepts to grasp – it’s part of the appeal to us at PI.…
Content Type: Advocacy
We are responding to the UK Government's consultation to expand its powers around Technical Capabilities Notices and National Security Notices.
Background
Following Edward Snowden's revelations about the illegal and expansive secret powers of the US and UK intelligence agencies, the UK Government took the opportunity to, rather than reflect on what powers are proportionate in the modern era, to expand its arsenal of surveillance powers.
One of the powers it added was the ability to issue…
Content Type: Advocacy
Privacy International welcomes the aim of the Cyber Resilience Act to bolster cybersecurity rules to ensure more secure hardware and software products. Nevertheless, we note that the proposal put forward by the European Commission contains certain shortcomings which could both hamper innovation and harm consumers who are increasingly relying on digital products and services.It is essential these shortcomings, detailed below, are effectively addressed by the EU co-legislators through the…
Content Type: Report
End-to-end encryption (E2EE) contributes significantly to security and privacy. For that reason, PI has long been in favour of the deployment of robust E2EE.Encryption is a way of securing digital communications using mathematical algorithms that protect the content of a communication while in transmission or storage. It has become essential to our modern digital communications, from personal emails to bank transactions. End-to-end encryption is a form of encryption that is even more private.…
Content Type: Video
In Kenya, if you don’t have an ID, life can be extremely difficult. But for thousands of people across the country, getting an ID can be nigh on impossible. Some Kenyan citizens can’t obtain a national ID because they are registered in the Kenyan refugee database. Often referred to as victims of double registration, their predicaments reveal a deeper problem with ID itself.Now Haki na Sheria - a Kenyan organisation advocating for and supporting the victims of double registration - and three…
Content Type: Long Read
What if your boss was an algorithm? What would you do if your employer suddenly fired you or reduced your pay without telling you why? And without being willing to give you a reason when you ask for one?
This is not science fiction or some far-fetched reality. Millions of people worldwide are working in the gig economy sector for companies like Uber, Deliveroo, Bolt, Just Eat… And this could be the future of work for people working outside the gig economy, as surveillance technologies are…
Content Type: Video
Update: Pa has since won a settlement from UberPlease note the views expressed in the video are interviewee's own and do not necessarily reflect the views of PI.Pa used to work for Uber. After some time, Uber started asking him to submit a picture of himself to the platform to confirm it was indeed him who had completed the job. However, with time, the frequency of the requests increased. In the beginning, the requests for a picture only happened once a week, but as time went by Pa told us that…
Content Type: News & Analysis
What if we told you that every photo of you, your family, and your friends posted on your social media or even your blog could be copied and saved indefinitely in a database with billions of images of other people, by a company you've never heard of? And what if we told you that this mass surveillance database was pitched to law enforcement and private companies across the world?
This is more or less the business model and aspiration of Clearview AI, a company that only received worldwide…
Content Type: Press release
Today, following an in-depth investigation, the UK Competition and Market Authority (CMA) assessed that the competition concerns can only be addressed by Facebook selling Giphy in its entirety. This is a very significant decision. Facebook, the largest provider of social media sites and display advertising in the UK, acquired Giphy, the largest provider of GIFs. The merger would further increase Facebook’s dominance and Facebook would have benefitted from Giphy’s data collection practices and…
Content Type: Advocacy
Our environment is increasingly populated by devices connected to the Internet, from computers and mobile phones to sound systems and TVs to fridges, kettles, toys, or domestic alarms. There has been research into the negative safety and privacy impacts of inadequate security provided by the software in such devices (such as the creation of large scale botnets). This is also the case with outdated security, a risk enabled by software support periods that are shorter than a product’s usable life…
Content Type: Long Read
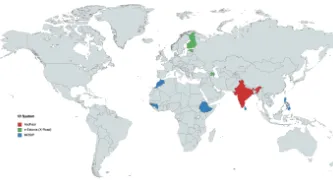
Governments around the world are increasingly making registration in national digital ID systems mandatory for populations, justifying its need on a range of issues from facilitating access to services, to national security and fighting against corruption. This is an attempt to create a "foundational identity" for an individual, or "a single source of truth" about who someone is, according to a government agency. These identity systems are run by governments, sometimes by private companies, or…
Content Type: Advocacy
Some of the most vulnerable groups in Mexico are amongst the groups at risk from a draft General Population Law that creates a biometric “Unique Digital Identity Card” (CUID), argue civil society organisations. The proposed law has now reached the senate, and has raised serious concerns from civil society organisations. Led by our global partner in Mexico Red en Defensa de los Derechos Digitales (R3D), PI along with 25 organisations have signed a joint letter to the members of the senate,…
Content Type: News & Analysis
After almost 20 years of presence of the Allied Forces in Afghanistan, the United States and the Taliban signed an agreement in February 2020 on the withdrawal of international forces from Afghanistan by May 2021. A few weeks before the final US troops were due to leave Afghanistan, the Taliban had already taken control of various main cities. They took over the capital, Kabul, on 15 August 2021, and on the same day the President of Afghanistan left the country.As seen before with regime…
Content Type: Press release
Dear TECNO,
We, the undersigned, don’t believe that privacy should be a luxury. And yet, when TECNO manufacture and sell phones with an outdated operating system, that’s the world TECNO are helping to create.
Our recent investigation into the TECNO Y2 showed that at least one TECNO phone is currently on sale with an operating system that hasn’t received updates since 2013. We are concerned because this is leaving users vulnerable to hundreds of well-known and serious exploits.
The Y2 was…
Content Type: Advocacy
Dear TECNO,
We, the undersigned, don’t believe that privacy should be a luxury. And yet, when TECNO manufacture and sell phones with an outdated operating system, that’s the world TECNO are helping to create.
Our recent investigation into the TECNO Y2 showed that at least one TECNO phone is currently on sale with an operating system that hasn’t received updates since 2013. We are concerned because this is leaving users vulnerable to hundreds of well-known and serious exploits.
The Y2 was…
Content Type: Long Read
When you buy a brand-new low-cost phone, it’s likely to come pre-installed with insecure apps and an outdated operating system. What this means is that you or your loved ones could be left vulnerable to security risks or to having their data exploited. Privacy shouldn’t be a luxury. That’s why we advocate for companies to provide the latest security features and privacy protections for both low- and high-cost phones.
Content Type: Advocacy
On 6 August 2021, the World Health Organisation (WHO) published its technical specifications and implementation guidance for “Digital Documentation of COVID-19 Certificates: Vaccination Status” (DDCC:VS) following months of consultations. As governments around the world are deploying their own Covid-19 certificates, guidance from the global health agency was expected to set a global approach, and one that prioritises public health. As such, we would expect the WHO to identify what these…