Advanced Search
Content Type: Long Read
Monday, 16 June 2025
It’s 7:33 am. Lila’s GoogBit watch vibrates. “You got 6 hours and 57 minutes of sleep last night, including 2 hours and 12 minutes of deep sleep”, the watch reads. “In total, you tossed and turned for 15 minutes only”. Taking into account Lila’s online browsing activity, her sleep pattern, the recent disruptions in some of her other biorhythms, as well as her daily schedule, GoogBit watch has calculated the very best minute to wake her up.
Content Type: Explainer
Hello friend,
You may have found your way here because you are thinking about, or have just submitted, a Data Subject Access Request, maybe to your Facebook advertisers like we did. Or maybe you are curious to see if Policing, Inc. has your personal data.
The right to access your personal data (or access right) is just one of a number of data rights that may be found in data protection law, including the European Union's General Data Protection Regulation, better known as "GDPR", which took…
Content Type: Long Read
Introduction
In August 2019, when Facebook announced a few new features for advertisers such as ads in search, PI decided to take an in-depth look at what features the company offers its users when it comes to understanding its advertising practices. One of these features, which caught our attention is Facebook Ads Preference, a tool that among other things, lists businesses/advertisers that have uploaded your personal data to target you with (or exclude you from) ads on the platform.
Content Type: Long Read
Covid Apps are on their way to a phone near you. Is it another case of tech-solutionism or a key tool in our healthcare response to the pandemic? It’s fair to say that nobody quite knows just yet.
We’ve been tracking these apps since the early days. We’ve been monitoring Apple and Google closely, have been involved in the UK’s app process, our partners in Chile and Peru have been tracking their governments’ apps, and more.
Of course privacy concerns arise. But only a simplistic analysis would…
Content Type: News & Analysis
As parts of the world are preparing to go back to factories, offices, and other workplaces, or in the case of Amazon, trying to make continually unsafe workplaces less hazardous, we must be on the watch yet again for profiteering, data-grabs, and surveillance as a solution to an undefined problem.
Many of the measures are predicated on the idea of catching employees who are sick. But, why do employers think that employees are or will lie about their health? Is it because they love their jobs…
Content Type: Explainer
In a scramble to track, and thereby stem the flow of, new cases of COVID-19, governments around the world are rushing to track the locations of their populace.
In this third installment of our Covid-19 tracking technology primers, we look at Satellite Navigation technology. In Part 1 of our mini-series on we discussed apps that use Bluetooth for proximity tracking. Telecommunications operators ('telcos'), which we discussed in Part 2, are also handing over customer data, showing the cell towers…
Content Type: Long Read
Photo by Cade Roberts on Unsplash
For those of you who don't spend the most productive part of your day scanning the news for developments about data and competition, here's what has been going on in the UK since summer 2019.
Basically, the UK competition authority started an investigation into online platforms and digital advertising last summer, and issued their preliminary findings in December 2019, concluding that Facebook and Google are very powerful in the search engine and social media…
Content Type: News & Analysis
Political campaigns around the world have turned into sophisticated data operations. They rely on data- your data- to facilitate a number of decisions: where to hold rallies, which States or constituencies to focus resources on, which campaign messages to focus on in which area, and how to target supporters, undecided voters, and non-supporters.
While data driven political campaigns are not new, the granularity of data available and the potential power to sway or suppress voters through that…
Content Type: News & Analysis
A few weeks ago, its name would probably have been unknown to you. Amidst the covid-19 crisis and the lockdown it caused, Zoom has suddenly become the go-to tool for video chat and conference calling, whether it’s a business meeting, a drink with friends, or a much needed moment with your family. This intense rise in use has been financially good to the company, but it also came with a hefty toll on its image and serious scrutiny on its privacy and security practices.
While Zoom already had a…
Content Type: Long Read
‘Let’s build an app for that’ has become the response to so many things. It’s no surprise it’s happening now.
Apps are notorious for their lack of security and privacy safeguards, exploiting people’s data and devices. Now we’re being asked to trust governments with their proposed apps -- of which there are many. These are the very same governments who have been keen to exploit data in the past. For instance, PI currently has four outstanding legal cases arising from the last times governments…
Content Type: News & Analysis
These are difficult and challenging times around the world.
In this global crisis, businesses are stepping in to support efforts by Governments and public health authorities to seek to control the impact of the virus.
This is important, as help of all kinds is sorely needed. However, we must also be wary that industry initatives and public-private partnerships are not used as an opportunity to profit from this crisis or to exploit data without legal safeguards.
Companies all over the world…
Content Type: Examples
An engineering and computer science professor and his team from The Ohio State University discovered a design flaw in low-powered Bluetooth devices that leaves them susceptible to hacking.
Zhiqiang Lin, associate professor of computer science and engineering at the university, found the commonly used Bluetooth Low Energy devices, such as fitness trackers and smart speakers, are vulnerable when they communicate with their associated apps on the owner’s mobile phone.
"There is a fundamental…
Content Type: Examples
On November 3rd, 2019, [...] a critical vulnerability affecting the Android Bluetooth subsystem [was reported]. This vulnerability has been assigned CVE-2020-0022 and was now patched in the latest security patch from February 2020. The security impact is as follows:
On Android 8.0 to 9.0, a remote attacker within proximity can silently execute arbitrary code with the privileges of the Bluetooth daemon as long as Bluetooth is enabled. No user interaction is required and only the Bluetooth MAC…
Content Type: Examples
Researchers at the Center for IT-Security, Privacy and Accountability (CISPA) have identified a security vulnerability related to encryption on Bluetooth BR/EDR connections. The researchers identified that it is possible for an attacking device to interfere with the procedure used to set up encryption on a BR/EDR connection between two devices in such a way as to reduce the length of the encryption key used. In addition, since not all Bluetooth specifications mandate a minimum…
Content Type: Case Study
In Peru, you get asked for your fingerprint and your ID constantly - when you’re getting a new phone line installed or depositing money in your bank account – and every Peruvian person has an ID card, and is included in the National Registry of Identity – a huge database designed to prove that everyone is who they say they are. After all, you can change your name, but not your fingerprint.
However, in 2019 the National Police of Peru uncovered a criminal operation that was doing just that:…
Content Type: News & Analysis
Almost a year and a half ago we complained about seven companies to three data protection authorities in Europe. These companies, ranging from AdTech to data brokers and credit rating agencies, thrive on the collection, exploitation and processing of personal data. They profile and categorise people - without our knowledge and infringing multiple legal requirements.
Now, the French Data Protection Authority CNIL has informed us that they are following the same route and …
Content Type: Case Study
In 2015, James Bates was charged with first-degree murder in the death of Victor Collins. Collins was found floating face down in Bates’ hot tub in November 2015. Bentonville police served two search warrants ordering Amazon to turn over the “electronic data in the form of audio recordings, transcribed records, text records and other data contained on the Amazon Echo device” in Bates’ home.
The reason for the warrants? According to the police, just because the device was in the house that…
Content Type: Long Read
In 2018, following the Cambridge Analytica scandal, Facebook announced the “Download Your Information” feature allowing users to download all the information that the company have on them since the creation of the account. All of it? It doesn’t seem so. Concerns were quickly raised when Facebook released the feature, that the information was inaccurate and incomplete.
Privacy International recently tested the feature to download all ‘Ads and Business’ related information (You can accessed it…
Content Type: Report
The changes discussed in this article are based on a second analysis performed in late November, 3 months after the original study Your Mental Health is for Sale and following the exact same methodology. All data collected can be found at the bottom of this page.
Change is possible
Back in September 2019 we published the report Your Mental Health is for Sale exposing how a majority of the top websites related to mental health in France, Germany and the UK share data for advertising purposes.…
Content Type: Long Read
Sitting on the ground inside an unadorned courtyard in Koira Tegui, one of Niamey’s most popular districts, Halimatou Hamadou shows a copy of what, she’s been told, is a certificate of birth.
The 33 year old woman, who’s unable to read and write, received it days earlier during a crowded public ceremony at a nearby primary school.
“It’s my first document ever,'' she says, with surprise.
Thanks to the paper, she’ll be able to take part in a crucial passage for the future of Niger: the…
Content Type: Long Read
In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone…
Content Type: Long Read
Photo by Nadine Shaabana on Unsplash
Digital identity providers
Around the world, we are seeing the growth of digital IDs, and companies looking to offer ways for people to prove their identity online and off. The UK is no exception; indeed, the trade body for the UK tech industry is calling for the development of a “digital identity ecosystem”, with private companies providing a key role. Having a role for private companies in this sector is not necessarily a problem: after all, …
Content Type: News & Analysis
Photo by Daniel Jensen on Unsplash
Everyone is talking about Facebook's end-to-end encryption plans and the US, UK and Australian government's response. Feeling lost? Here is what you need to know.
What's Facebook trying to do?
First let's be clear: Facebook has many faults when it comes to privacy. It's also suffered a number of security failures recently. See here for instance.
In response to their successive failures to protect your privacy, Facebook announced in their 'pivot to privacy…
Content Type: Long Read
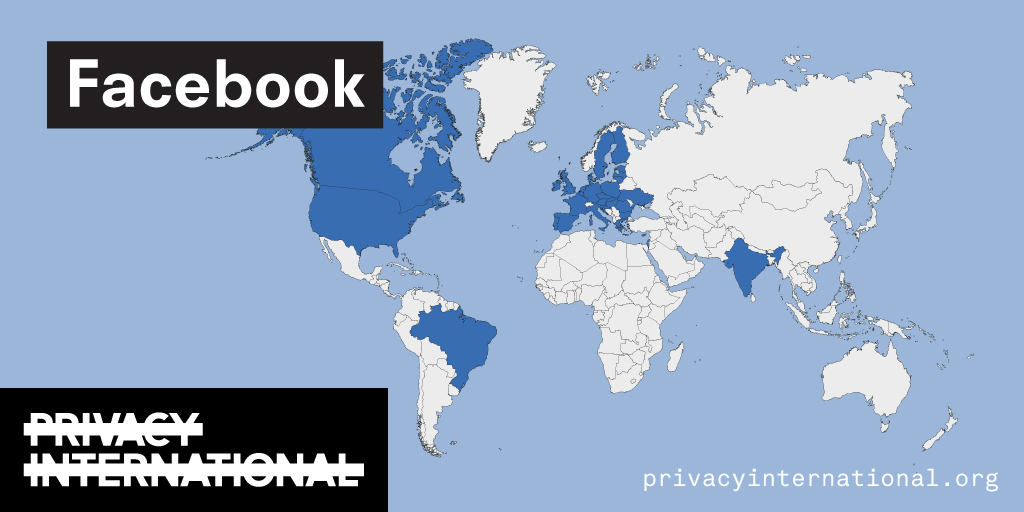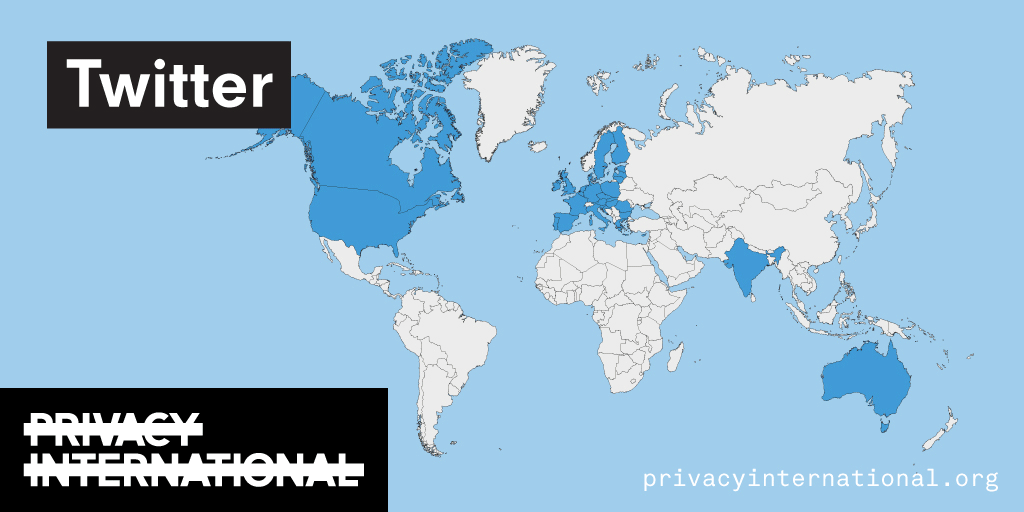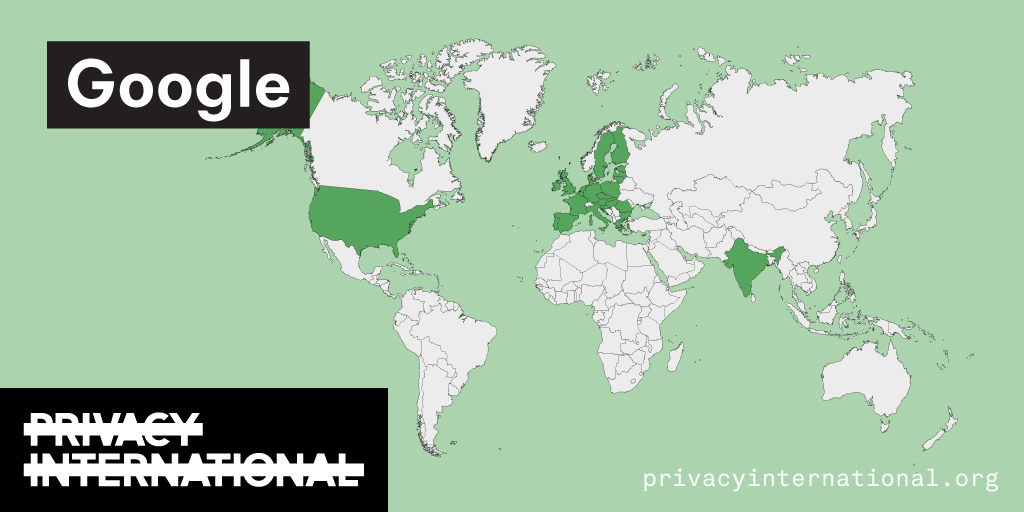
An analysis of what Facebook, Google, and Twitter have done to provide users with political ad transparency as of September 2019. Our full analysis is linked below.
Recently the role of social media and search platforms in political campaigning and elections has come under scrutiny. Concerns range from the spread of disinformation, to profiling of users without their knowledge, to micro-targeting of users with tailored messages, to interference by foreign entities, and more. Significant…
Content Type: Long Read
In December 2018, Privacy international exposed the dubious practices of some of the most popular apps in the world.Out of the 36 apps we tested, we found that 61% automatically transfer data to Facebook the moment a user opens the app. This happens whether the user has a Facebook account or not, and whether they are logged into Facebook or not. We also found that some of those apps routinely send Facebook incredibly detailed and sometimes sensitive personal data. Again, it didn’t matter if…
Content Type: Case Study
This time, Amtis travels to year 2030 to get a sense of how the data rights framework played out:
I just moved into a new apartment and everything was a mess. My stuff was all over the place and I couldn't find anything. I received a notification on my dashboard that a delivery drone had arrived with my package.
Data rights dashboard
The dashboard showed me a summary report with information about how my data was handled: which company processed my order, the type of data that was collected…
Content Type: News & Analysis
In December 2018, we revealed how some of the most widely used apps in the Google Play Store automatically send personal data to Facebook the moment they are launched. That happens even if you don't have a Facebook account or are logged out of the Facebook platform (watch our talk at the Chaos Communication Congress (CCC) in Leipzig or read our full legal analysis here).Today, we have some good news for you: we retested all the apps from our report and it seems as if we…
Content Type: News & Analysis
Palantir and the UN’s World Food Programme (WFP) are partnering for a reported $45 million. Palantir, a US-based company that sells data software and has been the centre of numerous scandals.
The World Food Programme provides assistance in food and nutrition to around 92 million people each year. Systems that are produced in agreements such as the one between WFP and Palantir increase risks to the people the they are attempting to help. There are risks to both individuals and whole populations…
Content Type: Impact Case Study
What HappenedOn 5 June 2013, The Guardian published the first in a series of documents disclosed by Edward Snowden, a whistleblower who had worked with the NSA. The documents revealed wide-ranging mass surveillance programs conducted by the USA’s National Security Agency (NSA) and the UK’s Government Communications Headquarters (GCHQ), which capture the communications and data of hundreds of millions of people around the world. In addition to revealing the mass surveillance programs of the NSA…
Content Type: Examples
In April 2018, the Austrian cabinet agreed on legislation that required asylum seekers would be forced to hand over their mobile devices to allow authorities to check their identities and origins. If they have been found to have entered another EU country first, under the Dublin regulation, they can be sent back there. The number of asylum seekers has dropped substantially since 2016, when measures were taken to close the Balkan route. The bill, which must pass Parliament, also allows the…