Long Reads

PI is launching a new brand in 2020, with a clearer focus on reimagining the future, where privacy gives us all the freedom to be human.
Over the coming months, PI is going to start to look a bit different. We will have a new logo and a whole new visual identity. And in turn, our new visual identity will only be one step in a wider process of PI reconnecting with our core mission and communicating it more effectively to you

Exclusive - Privacy International obtains contract between the UK Department of Health and Amazon.
Following a series of FOI requests from Privacy International and other organisations, the Department of Health and Social Care has now released its contract with Amazon, regarding the use of NHS content by Alexa, Amazon’s virtual assistant. The content of the contract is to a big extent redacted

The role of social media and search platforms in political campaigning and elections has come under scrutiny.
Recently the role of social media and search platforms in political campaigning and elections has come under scrutiny. Concerns range from the spread of disinformation, to profiling of users without their knowledge, to micro-targeting of users with tailored messages, to interference by foreign
Miguel Morachimo, Executive Director of Hiperderecho. Hiperderecho is a non-profit Peruvian organisation dedicated to facilitating public understanding and promoting respect for rights and freedoms in digital environments. The original version of this article was published in Spanish on Hiperderecho
*Photo by Kristina Flour on Unsplash The British government needs to provide assurances that MI5’s secret policy does not authorise people to commit serious human rights violations or cover up of such crimes Privacy International, along Reprieve, the Committee on the Administration of Justice, and

Niger has recently joined other countries in creating a biometric database that will be used in the upcoming elections.
Sitting on the ground inside an unadorned courtyard in Koira Tegui, one of Niamey’s most popular districts, Halimatou Hamadou shows a copy of what, she’s been told, is a certificate of birth. The 33 year old woman, who’s unable to read and write, received it days earlier during a crowded public
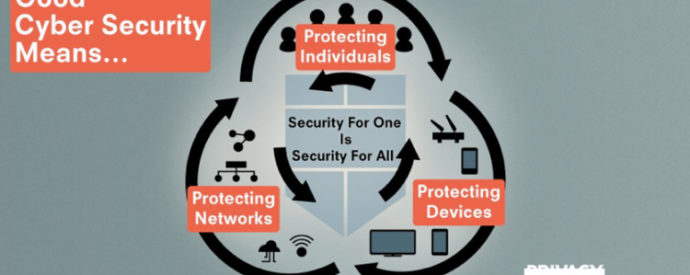
The pressing need to fix our cybersecurity (mis)understandings Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being

Governments across the world are building technologically integrated programmes to allow citizens to access welfare payments, and these could have adverse effects on those they should be supporting.
This research is the result of a collaboration between Grace Tillyard, a doctoral researcher in the Media, Communications and Cultural Studies department at Goldsmiths College, London, and Privacy International. Social Protection Systems in the Digital Age In the digital age, governments across the
[Photo credit: Images Money] The global counter-terrorism agenda is driven by a group of powerful governments and industry with a vested political and economic interest in pushing for security solutions that increasingly rely on surveillance technologies at the expenses of human rights. To
Police officers who operate mobile phone extraction technologies often have little or no forensic training and are increasingly reliant on devices whose capabilities they do not understand, particularly as budgets are cut and the volume of data they have to cope with increases.