Search
Content type: Explainer
Following sustained reporting by researchers, journalists and activists around the world, including recent disclosures exposed by the PegasusProject, the surveillance industry is facing scrutiny like never before.
In the latest move, eighteen U.S. lawmakers have today demanded that the U.S. government imposes sanctions on four non-US surveillance companies for, as they mention in their letter, facilitating “disappearance, torture and murder of human rights activists and journalists”.
The move…
Content type: Press release
Amnesty International, Privacy International and The Centre for Research on Multinational Corporations (SOMO) have published a report uncovering NSO Group’s entire corporate structure, tracking the global money trail of both public and private investment into the lucrative spyware company.
Amnesty International and other rights groups have documented dozens of cases of NSO Group’s products being used by repressive governments across the world to put activists, journalists, and opposition…
Content type: Report
In this briefing, Amnesty International, PI and The Centre for Research on Multinational Corporations (SOMO) discuss the corporate structure of NSO group, one of the surveillance industry's well-known participants. The lack of transparency around NSO Group’s corporate structure and the lack of information about the relevant jurisdictions within which it operates are significant barriers in seeking prevention of, and accountability for, human rights violations reportedly linked to NSO Group’s…
Content type: Explainer
What is hacking?
Hacking refers to finding vulnerabilities in electronic systems, either to report and repair them, or to exploit them.
Hacking can help to identify and fix security flaws in devices, networks and services that millions of people may use. But it can also be used to access our devices, collect information about us, and manipulate us and our devices in other ways.
Hacking comprises a range of ever-evolving techniques. It can be done remotely, but it can also include physical…
Content type: Explainer
What is an IMSI catcher?
‘IMSI’ stands for ‘international mobile subscriber identity’, a number unique to your SIM card. IMSI catchers are also known as ‘Stingrays’.
An ‘IMSI catcher’ is a device that locates and then tracks all mobile phones that are connected to a phone network in its vicinity, by ‘catching’ the unique IMSI number.
It does this by pretending to be a mobile phone tower, tricking mobile phones nearby to connect to it, enabling it to then intercept the data from that phone…
Content type: Video
Links
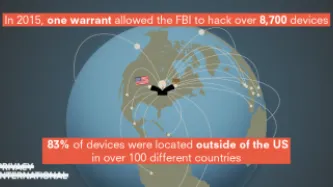
Find out more about general warrants and out case
Listen to our last podcast with Caroline - about a ruling in the European Union's top court that UK, French and Belgian mass surveillance regimes must respect privacy: Judgement Day
And make sure we can keep taking these fights to court: support.privacyinternational.org
You can listen and subscribe to the podcast where ever you normally find your podcasts:
Spotify
Apple podcasts
Google podcasts
Castbox
Overcast
Pocket Casts…
Content type: Report
Privacy International has released a report summarising the result of its research into the databases and surveillance tools used by authorities across the UK’s borders, immigration, and citizenship system.
The report uses procurement, contractual, and other open-source data and aims to inform the work of civil society organisations and increase understanding of a vast yet highly opaque system upon which millions of people rely.
It also describes and maps…
Content type: Long Read
On 8 January 2021, the UK High Court issued a judgment in the case of Privacy International v. Investigatory Powers Tribunal. The Secretary of State for Foreign and Commonwealth Affairs and Government Communication Headquarters (GCHQ) appeared as interested parties to the case.
After our initial reaction, below we answer some of the main questions relating to the case.
NOTE: This post reflects our initial reaction to the judgment and may be updated.
What’s the ruling all about?
In…
Content type: Frequently Asked Questions
On 8 January 2021, the UK High Court issued a judgment in the case of Privacy International v. Investigatory Powers Tribunal. The Secretary of State for Foreign and Commonwealth Affairs and Government Communication Headquarters (GCHQ) appeared as interested parties to the case.
After our initial reaction, below we answer some of the main questions relating to the case.
NOTE: This post reflects our initial reaction to the judgment and may be updated.
Content type: News & Analysis
Today, the UK High Court has quashed a decision by the Investigatory Powers Tribunal (IPT) and held that section 5 of the Intelligence Services Act (ISA) 1994 does not permit the issue of general warrants to authorise property interference and certain forms of computer hacking.
The Court referred to cases dating back to the 18th century, which demonstrate the common law’s insistence that the Government cannot search private premises without lawful authority even in the national security…
Content type: Press release
Today, the UK High Court has quashed a decision by the Investigatory Powers Tribunal (IPT), and ruled that section 5 of the Intelligence Services Act (ISA) 1994 does not permit the issuing of general warrants to authorise property interference and certain forms of computer hacking.
The Court referred to cases dating back to the 18th century, which demonstrate the common law’s insistence that the Government cannot search private premises without lawful authority even in the context of national…
Content type: Impact Case Study
What HappenedOn 5 June 2013, The Guardian published the first in a series of documents disclosed by Edward Snowden, a whistleblower who had worked with the NSA. The documents revealed wide-ranging mass surveillance programs conducted by the USA’s National Security Agency (NSA) and the UK’s Government Communications Headquarters (GCHQ), which capture the communications and data of hundreds of millions of people around the world. In addition to revealing the mass surveillance programs of the NSA…
Content type: Long Read
As our four year battle against the UK government’s extraordinarily broad and intrusive hacking powers goes to the Supreme Court, we are launching a new fundraising appeal in partnership with CrowdJustice.
We are seeking to raise £5k towards our costs and need your help. If we lose, the court may order us to pay for the government’s very expensive army of lawyers. Any donation you make, large or small, will help us both pursue this important case and protect the future ability of…
Content type: News & Analysis
Privacy International notes a recent ruling issued by Italy’s Supreme Court (Corte di Cassazione) that addresses the need to limit government hacking powers for surveillance purposes and articulates required safeguards when hacking is conducted as part of a criminal investigation.
The ruling addresses the appeals of several individuals involved in a case of corruption; the appeals challenge irregularities in the collection of data as part of the criminal investigation, which resulted in the…
Content type: News & Analysis
This piece was originally published on Just Security.
Ten years ago, an FBI official impersonated an Associated Press reporter to lure and track a teenager suspected of sending in prank bomb threats to his school. To find him, the FBI agent, posing as a reporter, sent the teenager links to a supposed story he was working on, but the links were infested with malware that once clicked on quickly exposed the teen’s location. More recently, the FBI has seized and modified websites so…
Content type: Advocacy
Privacy and security are both essential to protecting individuals, including their autonomy and dignity. Undermining privacy undermines the security of individuals, their devices and the broader infrastructure. People need privacy to freely secure themselves, their information, and fully enjoy other rights.
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. When governments hack for surveillance purposes, they seek to…
Content type: Advocacy
Introduction
Why We Are So Concerned about Government Hacking for Surveillance
Scope of Our Safeguards
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4. Judicial Authorisation
5. Integrity of information
6. Notification
7. Destruction and Return of Data
8. Oversight and Transparency
9. Extraterritoriality
10. Effective Remedy
Commentary on each
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4.…
Content type: Press release
In a remarkable development in Privacy International's four year legal battle against the UK Government's powers to hack phones and computers on a massive scale, the UK Supreme Court has agreed to hear the London-based charity's case in December 2018.
Privacy International's case stems from a decision by the Investigatory Powers Tribunal (a specialised court set up to hear complaints against government surveillance, including surveillance carried out by the UK intelligence agencies) finding…
Content type: Long Read
If you operate an internet company in Russia, you aren’t necessarily surprised to one day open the door to someone, grasping in one hand a bundle of wires and in the other a letter from a government agency demanding access to your servers, with a black box wedged under one arm.
Internet companies in Russia are required by law to store the content of users’ communications for six months and the metadata of users’ communications for three years, essentially meaning that what a person does…
Content type: Examples
In June 2016, National Security Agency deputy director Richard Ledgett told a conference on military technology conference that the agency was researching whether internet-connected biomedical devices such as pacemakers could be used to collect foreign intelligence. Ledgett identified the complexity of the Internet of Things as both a security nightmare and an opportunity for signals intelligence. However, the NSA prioritises its resources by focusing solely on technology used by its opponents…
Content type: Examples
In 2015, the Canadian Department of National Defence issued a procurement request for a contractor who could find "vulnerabilities and security measures" in a 2015 pick-up truck whose model and make were not specified and "develop and demonstrate exploits" for the military. The contractor was to find as many exploits as possible by analysing every part of the truck, demonstrate that the hacks could actually hurt someone or enable an attacker to gather information, and deliver explicit source…
Content type: Impact Case Study
What is the problem
For over two decades we have been documenting an alarming use and spread of surveillance. It is no longer just the wars on terror or drugs or migration that is driving this trend. The management of health crises and distribution of welfare regularly are among others being used to justify this turn to increasingly invasive forms of surveillance. From country to country we see the same ideas and the same profiteers expanding their reach.
When we first released our report on…
Content type: Advocacy
On 6 March 2018, Privacy International participated in an interactive dialogue with the UN Special Rapporteur on the right to privacy at the 37th Ordinary Session of the Human Rights Council in Geneva. We highlighted the growing trend of governments embracing hacking to facilitate their surveillance activities, and recommended the development of a human rights analysis of government hacking for surveillance purposes, with the view to forming specific…
Content type: Explainer
What is the Global Surveillance Industry?
Today, a global industry consisting of hundreds of companies develops and sells surveillance technology to government agencies around the world. Together, these companies sell a wide range of systems used to identify, track, and monitor individuals and their communications for spying and policing purposes. The advanced powers available to the best equipped spy agencies in the world are being traded around the world. It is a…
Content type: Press release
Privacy International and Open Rights Group have submitted a response to the Consultation on establishing a UK Privacy and Civil Liberties Board.
Content type: Press release
On 15 March 2017, the Italian Senate voted on a Bill, put forward by Justice Minister Andrea Orlando, that will reform the criminal justice system, including amending the Code of Criminal Procedure. Among the many provisions contained in DDL Orlando, currently pending approval by the Italian House of Representatives, the Government is mandated to regulate, via a legislative decree, the utilisation of malware (commonly referred to as ‘Trojans’ in Italian discourse) to engage hacking for criminal…
Content type: Key Resources
Introduction
Why We Are So Concerned about Government Hacking for Surveillance
Scope of Our Safeguards
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4. Judicial Authorisation
5. Integrity of information
6. Notification
7. Destruction and Return of Data
8. Oversight and Transparency
9. Extraterritoriality
10. Effective Remedy
Commentary on each
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4.…