Search
Content type: Advocacy
In September 2018, the National Executive sent the proposed Data Protection Bill to the National Congress. The proposed law was directed to the Senate and it will be considered by two commissions: the Commission of Constitutional Affairs (Comision de Asuntos Constitucionales) and the Commission of Rights and Guarantees (Comision de Derechos y Garantías).
Privacy International welcomes the continued efforts by Argentina to provide protections for the right to privacy, already enshrined in the…
Content type: News & Analysis
Creative Commons Photo Credit: Source
In September 2018, a month after Argentina lawmakers voted against the legalisation of abortion, we spoke to Eduardo Ferreyra from the Buenos Aires-based Asociacion por los Derechos Civiles about the role of privacy in the abortion debate. Also joining us in this second episode of the Gender and Privacy Series is Ambika Tandon from the Centre for Internet and Society in India to discuss the intersection between privacy and bodily autonomy.…
Content type: News & Analysis
Image attribution: By Blue Diamond Gallery CC BY-SA 3.0.
In March 2017, when the UN Human Rights Council requested the High Commissioner for Human Rights to prepare a report on the right to privacy in the digital age, including the responsibility of business enterprises, Cambridge Analytica was an obscure company among others. A year later the data exploitation scandal erupted, leading to plenty of soul searching by politicians in US, UK, Europe and elsewhere, pledges of…
Content type: News & Analysis
This piece originally appeared here.
Creative Commons Photo Credit: Source
Tech competition is being used to push a dangerous corporate agenda.
High-tech industries have become the new battlefield as the United States and China clash over tariffs and trade deficits. It’s a new truism that the two countries are locked in a race for dominance in artificial intelligence and that data could drive the outcome.
In this purported race for technological high ground, the argument often goes, China…
Content type: Report
Countries with powerful security agencies are spending literally billions to equip, finance and train security and surveillance agencies around the world — including authoritarian regimes. This is resulting in entrenched authoritarianism, further facilitation of abuse against people, and diversion of resources from long-term development programmes.
Privacy International's report 'Teach 'em to Phish: State Sponsors of Surveillance' examines this problem closely, providng examples from US, China…
Content type: Long Read
Privacy International (PI) has today released a new report, 'Teach 'em to Phish: State Sponsors of Surveillance', showing how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies.
Spurred by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, rights, and the rule of law.
As well as providing a background to the issue, the report…
Content type: Press release
Privacy International has today released a report that looks at how powerful governments are financing, training and equipping countries — including authoritarian regimes — with surveillance capabilities. The report warns that rather than increasing security, this is entrenching authoritarianism.Countries with powerful security agencies are spending literally billions to equip, finance, and train security and surveillance agencies around the world — including authoritarian regimes. This is…
Content type: News & Analysis
Actualmente, las empresas tecnológicas se encuentran inmersas en constante cambio. Uno de ellos es la creciente importancia que ha cobrado la seguridad digital, convirtiéndose en una prioridad. Que un emprendimiento resguarde su seguridad digital significa que puede gestionar los riesgos asociados a mantener la confidencialidad, integridad y disponibilidad de su información.
En este contexto, resulta de gran relevancia que las personas responsables del emprendimiento digital y el…
Content type: News & Analysis
El objetivo es facilitar a la sociedad civil una guía para la navegación de este organismo, efectuar un diagnóstico que permita situar cualquier persona interesada sobre la actualidad de la temática a nivel regional y descubrir la agenda de seguridad digital que sostiene la OEA en el continente.
Finalmente, concluimos con una serie de breves recomendaciones dirigidas a los organismos de la OEA. Con ello, esperamos que este órgano reconozca el papel que puede jugar como catalizador en el…
Content type: Examples
In January 2018 the Cyberspace Administration of China summoned representatives of Ant Financial Services Group, a subsidiary of Alibaba, to rebuke them for automatically enrolling its 520 million users in its credit-scoring system. The main complaint was that people using Ant's Alipay service were not properly notified that enrolling in the credit-scoring system would also grant Ant the right to share their personal financial data, including information about their income, savings, and…
Content type: Examples
In February 2018, police in China began using connected sunglasses equipped with facial recognition to scan crowds looking for suspected criminals. In a test at a busy train station in the city of Zhengzhou, police were able to identify and apprehend seven suspects accused of crimes ranging from hit-and-run to human trafficking. Police also identified 26 people using fake IDs, according to the Communist Party's People's Daily Newspaper. The glasses allow police officers to take a…
Content type: Examples
The Chinese company Tencent has issued a statement denying that it stores or analyses communications sent over WeChat, the country's most popular messaging platform after Geely Automobile chairman Li Shufu claimed there was no data privacy in China at a business forum. Shufu also claimed that Tencent chairman Pony Ma was "definitely looking at our WeChat messages every day". Under the Chinese government's rules, all social media groups are required to store user records. Although relatively…
Content type: Examples
In the remote western city Xinjiang, the Chinese government is using new technology and humans to monitor every aspect of citizens' lives. China, which has gradually increased restrictions in the region over the last ten years in response to unrest and violent attacks, blames the need for these measures on the region's 9 million Uighurs. This Muslim ethnic minority make up nearly half of the region's population, and the government accuses them of forming separatist groups and fuelling…
Content type: Examples
In 2015, Ant Financial, a Chinese company affiliated with Alibaba, began deploying "Sesame Credit scores". Ant, which also runs the popular payment app Alipay, claims that it uses both online and offline purchasing and spending habits to calculate a credit worthiness score for each of its more than 350 million users. Users who meet various thresholds qualify for bonuses such as small loans or waivers on deposits. Almost as soon as the system went live, users of popular social media apps such as…
Content type: Examples
In 2016 researchers in China claimed an experimental algorithm could correctly identify criminals based on images of their faces 89% of the time. The research involved training an algorithm on 90% of a dataset of 1,856 photos of Chinese males between 18 and 55 with no facial hair or markings. Among them were 730 ID pictures of convicted criminals or suspects wanted by the Ministry of Public Security. However, criminology experts warned that the results may merely reflect bias in the criminal…
Content type: Examples
In a 2017 study of patterns of postings on Chinese social media, three Harvard researchers disagreed with the widespread claim that the government's strategy is to post "50c party" posts that argue for the government's side in policy and political debates. Instead, the researchers estimated that the Chinese government fabricates as many as 448 million social media comments a year but found that these avoid controversial issues and arguments with government skeptics. Instead, the researchers…
Content type: Examples
In 2016, the Big Data lab at the Chinese search engine company Baidu published a study of an algorithm it had developed that it claimed could predict crowd formation and suggested it could be used to warn authorities and individuals of public safety threats stemming from unusually large crowds. The study, which was inspired by a New Year's Eve 2014 stampede in Shanghai that killed more than 30 people, correlated aggregated data from Baidu Map route searches with the crowd density at the places…
Content type: Examples
According to the US security firm Statfor the Chinese government has been builsing a system to analyse the massive amounts of data it has been collecting over the past years. The company claims: "The new grid management system aims to help the Chinese government act early to contain social unrest. Under the new program, grid administrators each monitor a number of households (sometimes as many as 200). They then aggregate their reports into one enormous surveillance database, where it is…
Content type: Report
La seguridad digital es una discusión crítica y hay que reconocer que la sociedad civil y los grupos de interés público no han sido suficientemente considerados. Como respuesta, varias organizaciones de la sociedad civil de América Latina se unieron para presentar informes que recuerdan a las entidades estatales responsables de formulación de políticas públicas que la seguridad digital debe tener en cuenta la seguridad de las personas y los derechos humanos. Presentamos la serie, Derechos…
Content type: Press release
Below is a joint statement from Privacy International and Bytes for All.
This Friday, 27 September, marks the conclusion of the 24th session of the UN Human Rights Council, a session which has, for the first time, seen issues of internet surveillance in the spotlight. Privacy International and Bytes for All welcome the attention given at the Human Rights Council to this issue. However, we are concerned about developments which took place that threaten privacy rights and freedom of…
Content type: Long Read
To celebrate Data Privacy Week, we spent the week discussing privacy and issues related to control, data protection, surveillance, and identity. Join the conversation on Twitter using #dataprivacyweek.
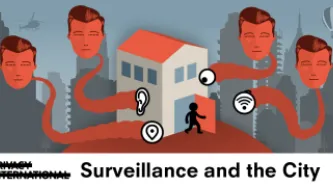
Do you live in a “smart city”? Chances are, you probably do (or at least your city claims to be). But do you know what exactly makes your city “smart”, beyond the marketing term? And what does this have to do with privacy?
Companies and governments will tell you that the more cameras, sensors…
Content type: Long Read
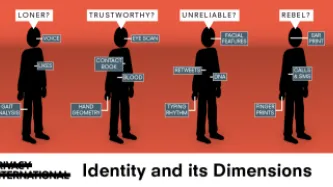
To celebrate International Data Privacy Day (28 January), PI and its International Network have shared a full week of stories and research, exploring how countries are addressing data governance in light of innovations in technology and policy, and implications for the security and privacy of individuals.
According to the World Bank, identity “provides a foundation for other rights and gives a voice to the voiceless”. The UN Deputy Secretary-General has called it a tool for “advancing…