Search
Content type: News & Analysis
In the last few months strong concerns have been raised in the UK about how police use of mobile phone extraction dissuades rape survivors from handing over their devices: according to a Cabinet Office report leaked to the Guardian, almost half of rape victims are dropping out of investigations even when a suspect has been identified. The length of time it takes to conduct extractions (with victims paying bills whilst the phone is with the police) and the volume of data obtained by the…
Content type: Examples
A woman was killed by a spear to the chest at her home in Hallandale Beache, Florida, north of Miami, in July. Witness "Alexa" has been called yet another time to give evidence and solve the mystery. The police is hoping that the smart assistance Amazon Echo, known as Alexa, was accidentally activated and recorded key moments of the murder. “It is believed that evidence of crimes, audio recordings capturing the attack on victim Silvia Crespo that occurred in the main bedroom … may be found on…
Content type: Long Read
In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone…
Content type: Report
“...a mobile device is now a huge repository of sensitive data, which could provide a wealth of information about its owner. This has in turn led to the evolution of mobile device forensics, a branch of digital forensics, which deals with retrieving data from a mobile device.”
The situation in Scotland regarding the use of mobile phone extraction has come a long way since the secret trials were exposed. The inquiry by the Justice Sub-Committee, commenced on 10 May 2018, has brought much…
Content type: Examples
In 2018, Brian Hofer, the chair of Oakland's Privacy Advisory Commission, filed suit after police wrongfully stopped him at gunpoint because their automated license plate recognition system, supplied by Vigilant Solutions, indicated that the rental car he was driving had been stolen. The car had in fact been stolen some months earlier, but been recovered. Despite such errors, police claim that the technology has helped reduce crime, identify stolen vehicles, and identify and arrest suspects.…
Content type: Examples
In February 2019 Gemalto announced it would supply the Uganda Police Force with its Cogent Automated Biometric Identification System and LiveScan technology in order to improve crime-solving. LiveScan enables police to capture biometric data alongside mugshots and biographical data. CABIS speeds up the biometric matching process by mapping distinctive characteristics in fingerprints, palm prints, and facial images. The Ugandan police will also pilot Gemalto's Mobile Biometric Identification…
Content type: Examples
VeriPol, a system developed at the UK's Cardiff University, analyses the wording of victim statements in order to help police identify fake reports. By January 2019, VeriPol was in use by Spanish police, who said it helped them identify 64 false reports in one week and was successful in more than 80% of cases. The basic claim is that AI can find patterns that are common to false statements; among the giveaways experts say that false statements are likely to be shorter than genuine ones, focus…
Content type: Examples
In November 2016 the UK Information Commissioner's Office issued an enforcement notice against London's Metropolitan Police, finding that there had been multiple and serious breaches of data protection law in the organisation's use of the Gangs Violence Matrix, which it had operated since 2012. The ICO documented failures of oversight and coherent guidance, and an absence of basic data protection practices such as encryption and agreements covering data sharing. Individuals whose details are…
Content type: Examples
A 19-year-old medical student was raped and drowned in the River Dresiam in October 2016. The police identified the accused by a hair found at the scene of the crime. The data recorded by the health app on his phone helped identify his location and recorded his activities throughout the day. A portion of his activity was recorded as “climbing stairs”, which authorities were able to correlate with the time he would have dragged his victim down the river embankment, and then climbed…
Content type: Examples
The body of a 57-year-old was found in the laundry room of her home in Valley View, Adelaide, in September 2016. Her daughter-in-law who was in the house at the time of the murder claimed that she was tied up by a group of men who entered the house and managed to escape when they left. However, the data from the victim's smartwatch did not corroborate her story.The prosecution alleged that the watch had recorded data consistent with a person going into shock and losing consciousness. "The…
Content type: Examples
The 90-year old suspect when to his stepdaughter's house at San Jose, California for a brief visit. Five days later, his stepdaugter's body, Karen was discovered by a co-worker in her house with fatal lacerations on her head and neck. The police used the data recorded by the victim's Fitbit fitness tracker to determine the time of the murder. It was been reported that the Fitbit data showed that her heart rate had spiked significantly around 3:20 p.m. on September 8, when her stepfather was…
Content type: Examples
On 14 May 2018, the husband of the victim, a pharmacist living in Linthorpe in Middlesbrough, subdued his wife with insulin injection before straggling her. He then ransacked the house to make it appear as a burglary. The data recorded by the health app on the murder’s phone, showed him racing around the house as he staged the burglary, running up and down the stairs. The victim’s app showed that she remained still after her death apart from a movement of 14 paces when her husband moved her…
Content type: Examples
A man from Middletown, Ohio, was indicted in January 2017 for aggravated arson and insurance fraud for allegedly setting fire to his home in September 2016. Ohio authorities decided and succeeded to obtain a search warrant for the data recorded on the pacemaker after identifying inconsistencies in the suspect’s account of facts. Ohio authorities alleged that the data showed that the accused was awake when he claimed to be sleeping. It has been reported that a cardiologist, examining data from…
Content type: Explainer
We look at the recently published report on forensic science in the UK, highlight concerns about police not understanding new tech used to extract data from mobile phones; the risk of making incorrect inferences and the general lack of understanding about the capabilities of these tools.
The delivery of justice depends on the integrity and accuracy of evidence and trust that society has in it. So starts the damning report of the House of Lords Science and Technology Select…
Content type: Examples
In yet another murder case, a New Hampshire judge ordered Amazon to turn over two days of Amazon Echo recordings in a double murder case in November 2018.
Prosecutors believe that recordings from an Amazon Echo in the Farmington home where two women were murdered in January 2017 may yield further clues as to who their killer might be. Though the Echo was seized when police secured the crime scene, the recordings are stored on Amazon servers.
Timothy Verrill, of Dover, New Hampshire, was…
Content type: Examples
In 2015, James Bates (of Arkansas, United States) was charged with first-degree murder in the death of Victor Collins. Collins was found floating face down in Bates’ hot tub in November 2015, police said. Amazon Echo entered the murder case because someone present on the night of Collins’ death recalled hearing music streaming through the device. It was widely reported that Amazon fought the prosecution’s request to hand over data recorded by the device that night. Eventually, the argument…
Content type: Long Read
Imagine that every time you want to attend a march, religious event, political meeting, protest, or public rally, you must share deeply personal information with police and intelligence agencies, even when they have no reason to suspect you of wrongdoing.
First, you need to go to the police to register; have your photo taken for a biometric database; share the contacts of your family, friends, and colleagues; disclose your finances, health records, lifestyle choices, relationship status, and…
Content type: News & Analysis
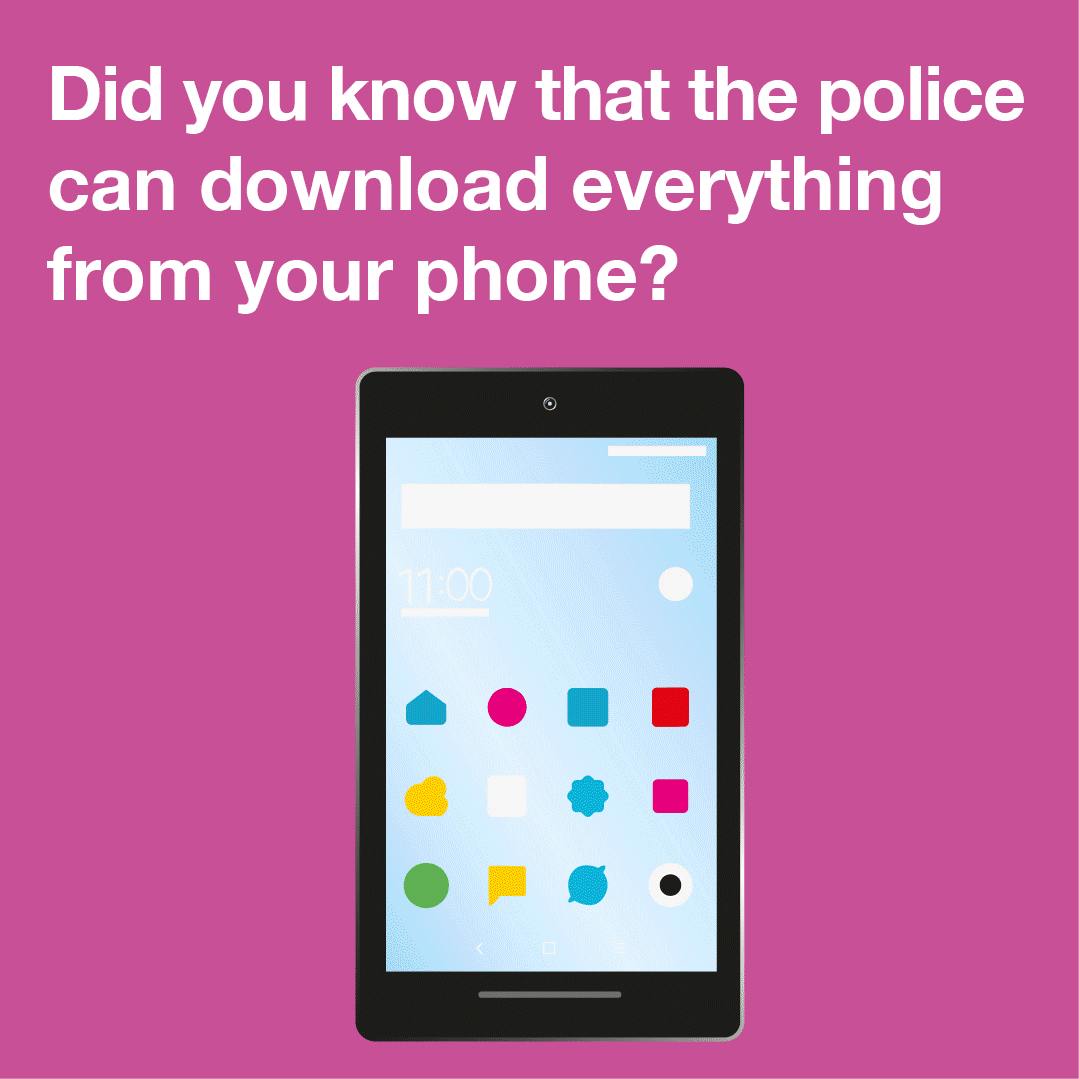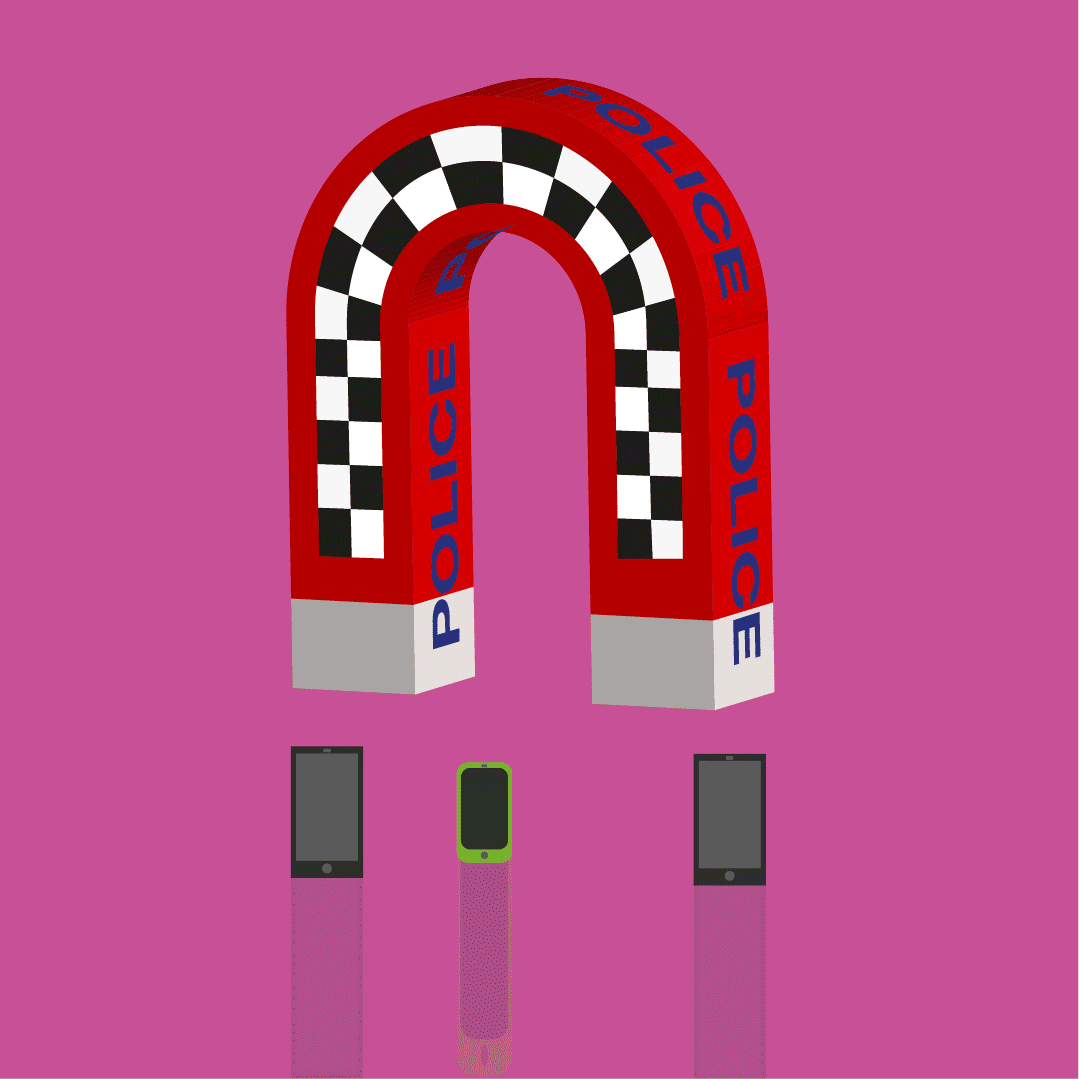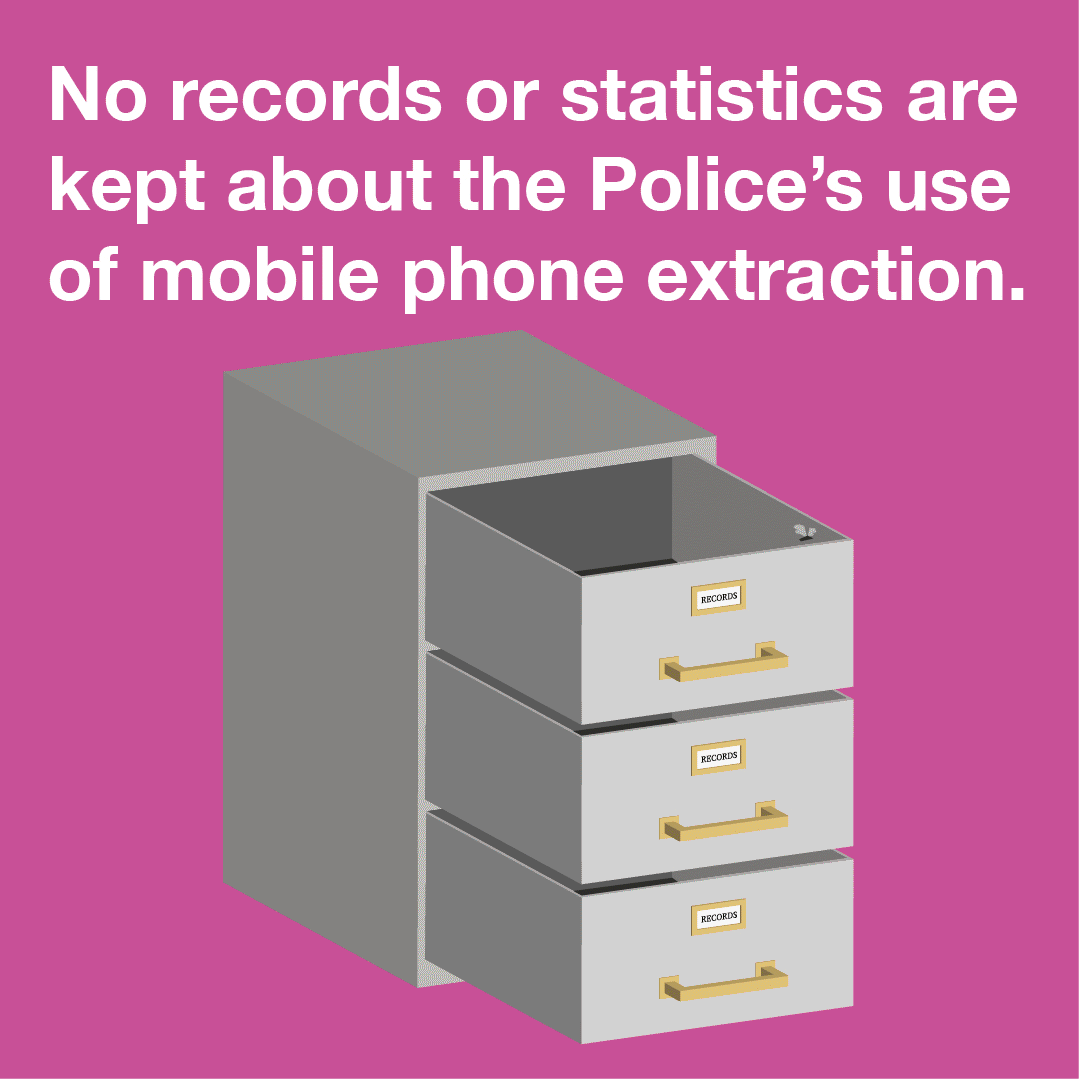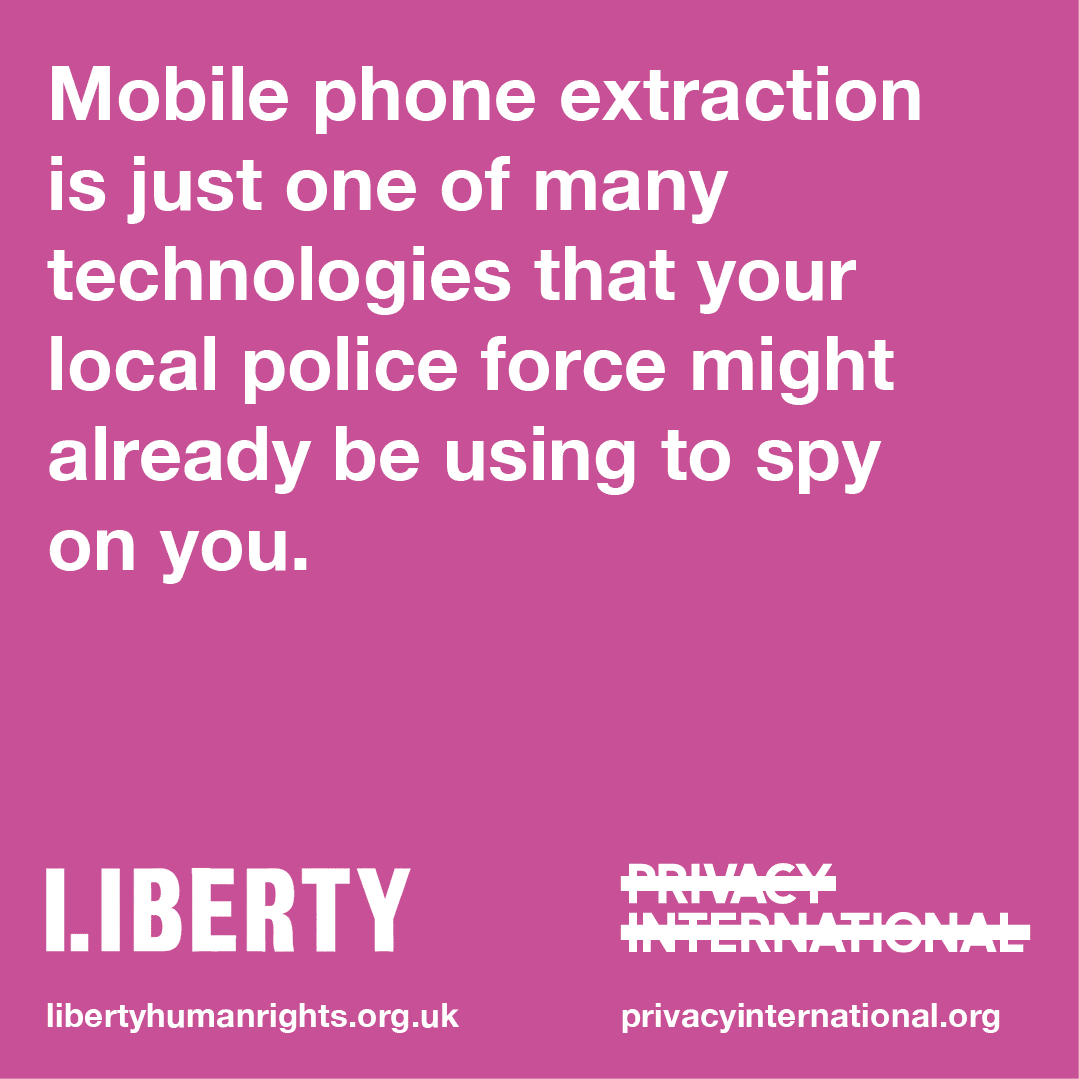
A mobile device is a huge repository of sensitive data, which could provide a wealth of information about its owner and many others with whom the user interacts.
Companies like Cellebrite, MSAB and Oxygen Forensics sell software and hardware to law enforcement. Once your phone is connected to one of these mobile phone extraction tools, the device extracts, analyses and presents the data contained on the phone.
What data these tools can extract and what method is used will…
Content type: News & Analysis
Protest movements throughout history have helped to shape the world we know today. From the suffragettes to the civil rights movement, and to contemporary movements such as those focusing on LGBTIQ+ rights, protests have become a vital way for many, who feel powerless otherwise, to have their voices heard.
But now, making the decision to attend a protest comes with consequences that you may very well be unaware of. This is because policing and security services, always hungry in their quest to…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: News & Analysis
Planning and participating in peaceful protests against governments or non-state actors’ policies and practices requires the capacity of individuals to communicate confidentially without unlawful interference. From protests in support of LGBTI rights to protests against specific projects that undermine local communities’ wellbeing, these movements would not have been possible without the ability to exchange ideas and develop plans in private spaces.
Unlawful interference with…
Content type: Advocacy
Privacy International's submission to the Human Rights Committee on a future General Comment on Article 21 of the International Covenant on Civil and Political Rights (ICCPR).
In this submission, Privacy International aims to provide the Committee with information on how surveillance technologies are affecting the right to peaceful assembly in new and often unregulated ways.
Based on Privacy International’s research, we provide the following observations:
the relationship between right…
Content type: Explainer graphic
You can also read a more detailed explainer about mobile phone extraction here.
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
In the era of smart cities, the gap between the internet and the so-called physical world is closing. Gone are the days, when the internet was limited to your activities behind a desktop screen, when nobody knew you were a dog.
Today, the…