Search
Content type: Long Read
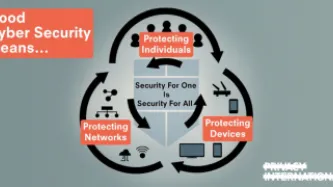
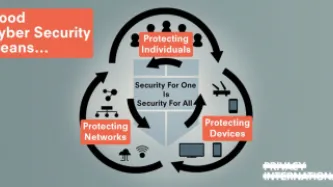
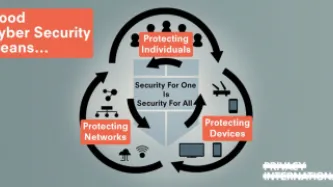
The security of our devices, applications and infrastructure is paramount to the safe functioning of our digital lives. Good security enables trust in our systems, it is fundamental to protecting the critical information we store and exchange through networks and devices. Similar to how we physically secure our homes, offices and schools, securing devices and software allows us to operate in safe and trusted environments where our security is guaranteed and protected.Security for information…
Content type: Long Read
In June 2023, the UK government announced its proposal to expand its surveillance powers by, among others, forcing communications operators to undermine encryption or abstain from providing security software updates globally. Building on our response to the government’s plans, this piece explains why what they want to do puts every one of us at risk.
Why your trust (to technologies you use) matters
Surveillance and privacy are complex concepts to grasp – it’s part of the appeal to us at PI.…
Content type: Long Read
The same day that the United Nations General Assembly convened an emergency special session to respond to Russia’s full-scale invasion of Ukraine in early March, a very different set of negotiations was underway in another U.N. conference room. More than two years after its establishment, the Ad Hoc Committee to Elaborate a Comprehensive International Convention on Countering the Use of Information and Communication Technologies for Criminal Purposes (hereinafter the Ad Hoc Committee) held its…
Content type: Long Read
Miguel Morachimo, Executive Director of Hiperderecho. Hiperderecho is a non-profit Peruvian organisation dedicated to facilitating public understanding and promoting respect for rights and freedoms in digital environments.The original version of this article was published in Spanish on Hiperderecho's website.Where does our feeling of insecurity come from? As we walk around our cities, we are being observed by security cameras most of the time. Our daily movement, call logs, and internet…
Content type: Long Read
The pressing need to fix our cybersecurity (mis)understandings
Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being different concepts, the confusion between them and the broad application of criminal statutes is still leading to the criminalise legitimate behaviour.
All of this represents a sizable challenge…
Content type: Long Read
image from portal gda (cc)
Many people are still confused by what is 5G and what it means for them. With cities like London, New York or San Francisco now plastered with ads, talks about national security, and the deployment of 5G protocols being treated like an arms race, what happens to our privacy and security?
5G is the next generation of mobile networks, which is meant to be an evolution of the current 4G protocols that mobile providers have deployed over the last decade, and there are…
Content type: News & Analysis
Privacy International has joined a global coalition of privacy campaigners, tech companies, and technology experts to respond to proposals by British intelligence chiefs aimed at allowing them access to encrypted messaging apps such as WhatsApp or Signal.
If implemented, the proposals would allow government authorities to force messaging platforms to silently add a law enforcement participant to a group chat or call.
Such a capability poses serious threats to…
Content type: Long Read
Image Source: "Voting Key" by CreditDebitPro is licensed under CC BY 2.0
Democratic society is under threat from a range of players exploiting our data in ways which are often hidden and unaccountable. These actors are manifold: traditional political parties (from the whole political spectrum), organisations or individuals pushing particular political agendas, foreign actors aiming at interfering with national democratic processes, and the industries that provide products that …
Content type: News & Analysis
A mobile device is a huge repository of sensitive data, which could provide a wealth of information about its owner and many others with whom the user interacts.
Companies like Cellebrite, MSAB and Oxygen Forensics sell software and hardware to law enforcement. Once your phone is connected to one of these mobile phone extraction tools, the device extracts, analyses and presents the data contained on the phone.
What data these tools can extract and what method is used will…
Content type: News & Analysis
Earlier this month, Brunei attracted international condemnation for a new law that will make gay sex punishable by death. While this is clearly abhorrent, Brunei is not the only country with explicit anti-gay laws.
Homosexuality is criminalised in over 70 countries around the world. And even in countries where gay sex is legal, such as the US, the LGBTIQ+ community still faces discriminatory surveillance and profiling by law enforcement agencies.
Through using the Internet and mobile apps,…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
Innovations in surveillance and data exploitation present challenges in the fight to protect personal data across the world. Since 1990 we have been working to build a global movement through working with others - from leading civil society…
Content type: Long Read
Since 2004, October has been designated National Cyber Security Awareness Month in the United States. Many other countries have followed suit, as part of the effort to raise awareness about the importance of cybersecurity, and how we can all work together to improve it.
However, cyber security (or sometimes, just ‘cyber’) has not only become a term with multiple and sometimes contradictory meanings - that go from digital security or digital diplomacy to criminal activities with a digital…
Content type: News & Analysis
As the international cyber security debate searches for new direction, little attention is paid to what is going on in Africa. Stepping over the remains of the UN Group of Governmental Experts, and passing by the boardrooms of Microsoft struggling to deliver their Digital Geneva Convention, African nations are following their own individual paths.
Unfortunately, these paths increasingly prioritise intrusive state surveillance and criminalisation of legitimate expression online as…
Content type: News & Analysis
Actualmente, las empresas tecnológicas se encuentran inmersas en constante cambio. Uno de ellos es la creciente importancia que ha cobrado la seguridad digital, convirtiéndose en una prioridad. Que un emprendimiento resguarde su seguridad digital significa que puede gestionar los riesgos asociados a mantener la confidencialidad, integridad y disponibilidad de su información.
En este contexto, resulta de gran relevancia que las personas responsables del emprendimiento digital y el…
Content type: News & Analysis
El objetivo es facilitar a la sociedad civil una guía para la navegación de este organismo, efectuar un diagnóstico que permita situar cualquier persona interesada sobre la actualidad de la temática a nivel regional y descubrir la agenda de seguridad digital que sostiene la OEA en el continente.
Finalmente, concluimos con una serie de breves recomendaciones dirigidas a los organismos de la OEA. Con ello, esperamos que este órgano reconozca el papel que puede jugar como catalizador en el…
Content type: News & Analysis
Nota de prensa
Peruanos rutinariamiente otorgan y son sometidos a verificación de sus datos personales y biométricos (huella digital, retina) en entidades públicas y privadas sin ser informados claramente de la finalidad y tratamiento posterior de la información.
RENIEC ocupa un rol predominante dentro del ecosistema nacional para dotar de coherencia al sistema de identificación que emplea tecnología biométrica. Sin embargo, pese a contar con diferentes estándares y medidas de seguridad en el…
Content type: News & Analysis
We found the above image here.
Background
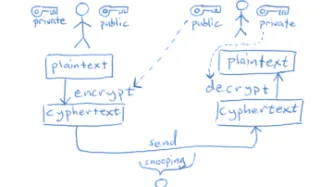
Email is hard to secure. For years we've been trying to build security on top of email, such as through technologies like Pretty Good Privacy (PGP) and the open source implementation: GnuPG (GPG).
What happened
In the past 48 hours, there have been very scary looking reports recommending people switch off PGP in their email clients.
The TL;DR version of this post is:
PGP is not broken by this attack
You absolutely should not stop…
Content type: News & Analysis
This post was written by PI Technologist Ed Geraghty.
At the very heart of ThornSec’s design is that we assume our security will fail. There is nothing perfect on this earth (except kittens). The entire point is to fail well. For charities and NGOs that are fragile, poorly resourced, and often at risk, this is relatively novel thinking. We prepare for that with a strict adherence to good security practice.
It is exactly this element of novelty that makes us more open than your…
Content type: News & Analysis
Overview
CIPIT is currently investigating how the privacy of Kenyan citizens was affected by the use of biometric data during the just concluded 2017 general and repeat elections. The IEBC is mandated by law to register voters, verify their registration details and conduct elections. Accordingly, the IEBC is the custodian of the public voter register. There have been reports that individuals received SMS texts from candidates vying for various political seats during the campaign period of the…
Content type: News & Analysis
There are three good reasons why security is so hard for NGOs. First, we are afraid to speak about meaningful security. Second, we focus on the wrong areas of security and in turn spend money and prioritise the wrong things. Third, we struggle to separate the world we want from the worlds we build within our own organisations. At PI we have failed and struggled with each of these for over 20 years. Out of exhaustion, we decided to do something about it: we are building an open framework, a…
Content type: News & Analysis
This is the story of Privacy International's journey to building more secure services. Data collection and administering sensitive data on the open web is risky, and PI had to learn this the hard way.
Many companies say that the privacy of their audiences is their top priority. But do they mean it? Do they invest in it? Doing security on tight budgets is incredibly hard. But it is the natural state of the non-profit sector. We learned this through challenging experiences.…
Content type: News & Analysis
Photo Credit: MoD UK
‘Security’ in the policy world has practically no currency without a specific prefix. For example, we could discuss 'national' security as distinct from 'consumer' security or 'energy' security. ‘Cyber’ security is the new prefix on the policy block, and it is gradually forcing a rethink on what it means to be secure in a modern society. In the course of Privacy International’s work globally, we have observed that many governments frame cyber security as national security…
Content type: News & Analysis
The past few years have seen a huge rise in the number of attacks both active and passive, against organisations big and small. Attacks against organisations happen for a multitude of reasons: extortion via "ransomware", exfiltration of commercial secrets, or just "the lulz". While this can be crippling to a commercial business, it can potentially be devastating to an NGO, especially those which work to hold powerful institutions to account. The types of information held by such NGOs could…
Content type: News & Analysis
Dear Politicians,
With elections coming up and quite a few cringe-worthy comments that have come from many of you and from all sides of the political spectrum, we figured it was time to have a chat about encryption.
First, let’s say what you shouldn’t do:
call for boycotts of companies because they protect their users’ data even from the companies themselves.
say something like “we’ll develop a Manhattan-level project on this” (which, as we’ll remind you, ended up with the creation of a…
Content type: News & Analysis
On a hot day in Nairobi, our researcher is speaking to an officer of Kenya’s National Intelligence Service (NIS). The afternoon is wearing on and the conversation has turned to the presidential elections, taking place in August this year. He has just finished describing the NIS’ highly secret surveillance powers and the disturbing ways in which these powers are deployed.
“It is what you might call ‘acceptable deaths,’” he states about the misuse of communications surveillance powers. “People…
Content type: News & Analysis
This guest piece was written by Elonnai Hickok and Vipul Kharbanda of the Centre for Internet and Society. It does not necessarily reflect the views or position of Privacy International.
In light of the complex challenges and threats posed to, and by, the field of information telecommunications in cyberspace, in 1998 the draft resolution in the First Committee of the UN General Assembly was introduced and adopted without a vote (A/RES/53/70)…
Content type: News & Analysis
The connectivity afforded by the internet has changed the world forever. While the increasing ‘corporatization’ of what many still feel is an open, non-hierarchical, largely uncensored and unfiltered ecosystem, this is increasingly not the case. The emergence of the ‘Internet of Things’ will soon throw into sharp relief who owns the internet and who owns the data we all generate when using the internet. Companies today have a vested interest in portraying their products as safe and…
Content type: News & Analysis
Privacy can be seen as a reflex of innovation. One of the seminal pieces on the right to privacy as the 'right to be let alone emerged in response to the camera and its use by the tabloid media. Seminal jurisprudence is in response to new surveillance innovations... though often with significant delays.
While one approach would be to say that privacy is a norm and that with modern technologies the norm must be reconsidered and if necessary, abandoned; I think there’s an interesting idea around…
Content type: News & Analysis
Everyone wants to know what you need to do to be i) happy, ii) fit, iii) secure. And the easier and more listy it is, the better.
The Guardian recently published an article that left PI’s techies sceptical, to say the least. “Extreme online security measures to protect your digital privacy – a guide” offered nine pieces of advice to stay secure online, including covering your house with a few layers of aluminium (!!!).
While there is no one-solution-fits-all when it comes to security and…
Content type: News & Analysis
The much maligned Prevention of Electronic Crimes Bill (PECB) was dealt a critical blow by senior Senate members on Tuesday in Pakistan. Digital Rights Foundation, in conjunction with Bolo Bhi, held a consultation for members of the Pakistan Senate, other lawmakers, members of civil society, and the media.
The aim of the consultation was to discuss the Bill, the problematic provisions and amendments that have been suggested in its most recent version, and the steps…