Search
Content type: Video
Links Read more about your optionsLearn more about PI's position on the Cyber Resilience Act
Content type: Long Read
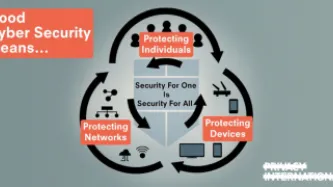
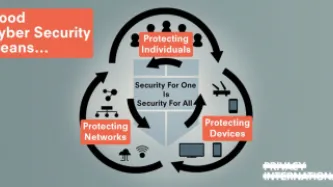
The security of our devices, applications and infrastructure is paramount to the safe functioning of our digital lives. Good security enables trust in our systems, it is fundamental to protecting the critical information we store and exchange through networks and devices. Similar to how we physically secure our homes, offices and schools, securing devices and software allows us to operate in safe and trusted environments where our security is guaranteed and protected.Security for information…
Content type: Long Read
What happened?On 19 July 2024, American cybersecurity company CrowdStrike released an update to its CrowdStrike Falcon software that ultimately caused 8.5 million computers running Microsoft Windows to crash. The damage done was both deep and wide: deep because the computers affected were unable to recover without direct user intervention. Wide because a whole range of companies - from airlines to healthcare to media - across a whole range of countries - from Sweden to India to New Zealand -…
Content type: Advocacy
While PI recognises the threats posed by cybercrime, PI reiterates the need both for a narrow scope for the proposed Convention, focusing solely on core cyber-dependent crimes, as well as for effective safeguards throughout the entire treaty to ensure human rights are respected and protected, especially in the areas of privacy and freedom of expression. Throughout the negotiations most of proposals by Member States and other stakeholders aimed at restricting the scope of the treaty and…
Content type: Report
Introduction
Several policy initiatives are in progress at the EU level. They seek to address the sustainability of connected devices such as smartphones, tablets and smart speakers. While initiatives to extend the useful life of hardware are important, software must not be ignored. Almost any digital device with which we interact today relies on software to function, which acts as a set of instructions that tells the hardware what to do. From smart thermostats to smart speakers, to our…
Content type: Press release
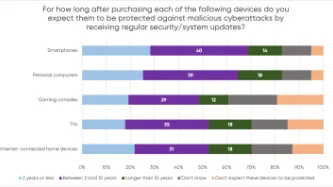
A YouGov survey commissioned by PI shows that consumers expect their smartphones, computers, smart TVs and gaming consoles to receive security updates for a much longer period than what several manufacturers actually provide, leaving consumers with expensive tech that is vulnerable to cyberattacks.
The majority of consumers in the survey assumed their devices would be protected beyond two years, but current industry practices fail to meet these expectations. PI investigated the software…
Content type: Long Read
The same day that the United Nations General Assembly convened an emergency special session to respond to Russia’s full-scale invasion of Ukraine in early March, a very different set of negotiations was underway in another U.N. conference room. More than two years after its establishment, the Ad Hoc Committee to Elaborate a Comprehensive International Convention on Countering the Use of Information and Communication Technologies for Criminal Purposes (hereinafter the Ad Hoc Committee) held its…
Content type: Advocacy
Our environment is increasingly populated by devices connected to the Internet, from computers and mobile phones to sound systems and TVs to fridges, kettles, toys, or domestic alarms. There has been research into the negative safety and privacy impacts of inadequate security provided by the software in such devices (such as the creation of large scale botnets). This is also the case with outdated security, a risk enabled by software support periods that are shorter than a product’s usable life…
Content type: Examples
An engineering and computer science professor and his team from The Ohio State University discovered a design flaw in low-powered Bluetooth devices that leaves them susceptible to hacking.
Zhiqiang Lin, associate professor of computer science and engineering at the university, found the commonly used Bluetooth Low Energy devices, such as fitness trackers and smart speakers, are vulnerable when they communicate with their associated apps on the owner’s mobile phone.
"There is a fundamental…
Content type: Long Read
Miguel Morachimo, Executive Director of Hiperderecho. Hiperderecho is a non-profit Peruvian organisation dedicated to facilitating public understanding and promoting respect for rights and freedoms in digital environments.The original version of this article was published in Spanish on Hiperderecho's website.Where does our feeling of insecurity come from? As we walk around our cities, we are being observed by security cameras most of the time. Our daily movement, call logs, and internet…
Content type: Long Read
The pressing need to fix our cybersecurity (mis)understandings
Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being different concepts, the confusion between them and the broad application of criminal statutes is still leading to the criminalise legitimate behaviour.
All of this represents a sizable challenge…
Content type: Long Read
image from portal gda (cc)
Many people are still confused by what is 5G and what it means for them. With cities like London, New York or San Francisco now plastered with ads, talks about national security, and the deployment of 5G protocols being treated like an arms race, what happens to our privacy and security?
5G is the next generation of mobile networks, which is meant to be an evolution of the current 4G protocols that mobile providers have deployed over the last decade, and there are…
Content type: Report
Like many others, PI were alarmed at recent reports that Facebook have been making mobile phone numbers (which users believed to be) provided for the express purpose of "two-factor authentication" (2FA) both searchable, and a target for advertising by default.
One of the myriad ways Facebook displays targeted adverts to users is through so-called "Custom Audiences". These "custom audiences" are lists of contact details, including phone numbers and email addresses, uploaded by advertisers.…
Content type: Explainer
We look at the recently published report on forensic science in the UK, highlight concerns about police not understanding new tech used to extract data from mobile phones; the risk of making incorrect inferences and the general lack of understanding about the capabilities of these tools.
The delivery of justice depends on the integrity and accuracy of evidence and trust that society has in it. So starts the damning report of the House of Lords Science and Technology Select…
Content type: News & Analysis
Privacy International has joined a global coalition of privacy campaigners, tech companies, and technology experts to respond to proposals by British intelligence chiefs aimed at allowing them access to encrypted messaging apps such as WhatsApp or Signal.
If implemented, the proposals would allow government authorities to force messaging platforms to silently add a law enforcement participant to a group chat or call.
Such a capability poses serious threats to…
Content type: Case Study
Photo by Roger H. Goun
Chloe is an investigative journalist working for an international broadcast service; we will call the TV show she works for The Inquirer. She travels around the world to work with local journalists on uncovering stories that make the headlines: from human trafficking to drug cartels and government corruption. While her documentaries are watched by many and inspire change in the countries she works in, you would not know who Chloe is if we were to tell you her real name.…
Content type: Long Read
Image Source: "Voting Key" by CreditDebitPro is licensed under CC BY 2.0
Democratic society is under threat from a range of players exploiting our data in ways which are often hidden and unaccountable. These actors are manifold: traditional political parties (from the whole political spectrum), organisations or individuals pushing particular political agendas, foreign actors aiming at interfering with national democratic processes, and the industries that provide products that …
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
Innovations in surveillance and data exploitation present challenges in the fight to protect personal data across the world. Since 1990 we have been working to build a global movement through working with others - from leading civil society…
Content type: Long Read
Since 2004, October has been designated National Cyber Security Awareness Month in the United States. Many other countries have followed suit, as part of the effort to raise awareness about the importance of cybersecurity, and how we can all work together to improve it.
However, cyber security (or sometimes, just ‘cyber’) has not only become a term with multiple and sometimes contradictory meanings - that go from digital security or digital diplomacy to criminal activities with a digital…
Content type: News & Analysis
As the international cyber security debate searches for new direction, little attention is paid to what is going on in Africa. Stepping over the remains of the UN Group of Governmental Experts, and passing by the boardrooms of Microsoft struggling to deliver their Digital Geneva Convention, African nations are following their own individual paths.
Unfortunately, these paths increasingly prioritise intrusive state surveillance and criminalisation of legitimate expression online as…
Content type: Key Resources
Introduction
Why We Are So Concerned about Government Hacking for Surveillance
Scope of Our Safeguards
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4. Judicial Authorisation
5. Integrity of information
6. Notification
7. Destruction and Return of Data
8. Oversight and Transparency
9. Extraterritoriality
10. Effective Remedy
Commentary on each
1. Legality
2. Security and Integrity of Systems
3. Necessity and Proportionality
4.…
Content type: News & Analysis
This is the story of Privacy International's journey to building more secure services. Data collection and administering sensitive data on the open web is risky, and PI had to learn this the hard way.
Many companies say that the privacy of their audiences is their top priority. But do they mean it? Do they invest in it? Doing security on tight budgets is incredibly hard. But it is the natural state of the non-profit sector. We learned this through challenging experiences.…
Content type: News & Analysis
Photo Credit: MoD UK
‘Security’ in the policy world has practically no currency without a specific prefix. For example, we could discuss 'national' security as distinct from 'consumer' security or 'energy' security. ‘Cyber’ security is the new prefix on the policy block, and it is gradually forcing a rethink on what it means to be secure in a modern society. In the course of Privacy International’s work globally, we have observed that many governments frame cyber security as national security…
Content type: News & Analysis
The past few years have seen a huge rise in the number of attacks both active and passive, against organisations big and small. Attacks against organisations happen for a multitude of reasons: extortion via "ransomware", exfiltration of commercial secrets, or just "the lulz". While this can be crippling to a commercial business, it can potentially be devastating to an NGO, especially those which work to hold powerful institutions to account. The types of information held by such NGOs could…
Content type: News & Analysis
On a hot day in Nairobi, our researcher is speaking to an officer of Kenya’s National Intelligence Service (NIS). The afternoon is wearing on and the conversation has turned to the presidential elections, taking place in August this year. He has just finished describing the NIS’ highly secret surveillance powers and the disturbing ways in which these powers are deployed.
“It is what you might call ‘acceptable deaths,’” he states about the misuse of communications surveillance powers. “People…
Content type: News & Analysis
This guest piece was written by Elonnai Hickok and Vipul Kharbanda of the Centre for Internet and Society. It does not necessarily reflect the views or position of Privacy International.
In light of the complex challenges and threats posed to, and by, the field of information telecommunications in cyberspace, in 1998 the draft resolution in the First Committee of the UN General Assembly was introduced and adopted without a vote (A/RES/53/70)…
Content type: News & Analysis
The connectivity afforded by the internet has changed the world forever. While the increasing ‘corporatization’ of what many still feel is an open, non-hierarchical, largely uncensored and unfiltered ecosystem, this is increasingly not the case. The emergence of the ‘Internet of Things’ will soon throw into sharp relief who owns the internet and who owns the data we all generate when using the internet. Companies today have a vested interest in portraying their products as safe and…
Content type: News & Analysis
Privacy can be seen as a reflex of innovation. One of the seminal pieces on the right to privacy as the 'right to be let alone emerged in response to the camera and its use by the tabloid media. Seminal jurisprudence is in response to new surveillance innovations... though often with significant delays.
While one approach would be to say that privacy is a norm and that with modern technologies the norm must be reconsidered and if necessary, abandoned; I think there’s an interesting idea around…