Search
Content type: Long Read
This piece was last updated in June 2021.
In many countries, access to social protection (such as welfare programmes or healthcare) is made conditional on producing a form of identification (“ID”). But obtaining a recognised and accurate ID is often a process riddled with discriminatory designs, bureaucracy and technical failures that prevent individuals from accessing the services they are entitled to. Even when people eventually get an ID, it might not accurately reflect who they are,…
Content type: News & Analysis
Uganda's Presidential election in January 2021 resulted in the incumbent President Museveni winning his sixth term in office, having held power for 35 years. The election took place amidst a global pandemic and the run up to election day was fraught. Violence left dozens dead and hundreds more arrested, including the opposition candidate Bobi Wine. Mass rallies and in person campaign meetings were banned due to Covid restrictions and political parties in Uganda were encouraged to conduct “…
Content type: News & Analysis
Unwanted Witness’ research into Safeboda highlighted the company’s failure to comply with some of the law's core data protection principles, with a number of implications for the exercise of data subject rights. The enforcement action against Safeboda by National Information Technology Authority, Uganda (NITA-U) requires the company to make fundamental changes to how they handle people's personal data in order to comply with the Data Protection and Privacy Act, 2019.
This first landmark…
Content type: Examples
On 2 March 2021, the Ministry of Health of Uganda unveiled its plan to immunize millions against COVID-19 starting on 10 March 2021.
The statement made by the Ministry of Health noted that "All persons eligible for vaccination will be required to provide a National Identification Card in the case of Ugandan citizens or a passport in the case of non-Ugandans".
Source: https://www.youtube.com/watch?v=asc5mQe0-3I
Publication: NTV News
Content type: Case Study
The Ugandan government has a running contract with the Chinese tech giant, Huawei, to supply and install CCTV cameras along major highways within the capital, Kampala, and other cities.
While details of the contract remain concealed from the public, the Uganda Police Force (UPF) released a statement, simply confirming its existing business partnership for telecommunication and surveillance hardware, and software between the security force and Huawei. However, it is not clear whether the…
Content type: Examples
Our partners from Unwanted Witness in Uganda wrote a formal letter to the Ministry of Information Communications Technology and National Guidance demanding for strict observance of human rights for any intended use of surveillance technologies to fight COVID-19.
In a letter addressed to the Permanent Secretary Ministry of ICT, Hon. Vincent Bagiire and copied to Minister Judith Nabakooba, calls on government to respect its human rights obligation and restrain from exercising excessive…
Content type: Examples
Ten Ugandan police officers were charged with torture after allegedly caning 38 women and forcing them to swim in mud in Elegu, a town in the northern part of the country. Police have also arrested 23 people during a raid on a shelter for homeless lesbian, gay, bisexual and transgender youth, accused them of disobeying orders by remaining in the shelter, and charging them with a negligent act likely to spread infection or disease.
Source: https://www.bbc.co.uk/news/world-africa-52214740…
Content type: Examples
The Uganda Communications Commission announced on March 22 that it would crack down on people spreading fake videos and misinformation about the novel coronavirus through social media, noting that this behaviour is illegal under the Computer Misuse Act, the Data Protection and Privacy Act, and other penal laws. UCC went on to warn in a public notice that it would arrest and prosecute violators.
Sources:
http://www.china.org.cn/world/Off_the_Wire/2020-03/23/content_75847935.htm
https://twitter…
Content type: News & Analysis
This piece was originally published by Unwanted Witness here.
Today marks exactly one year since Uganda passed its data protection law, becoming the first East African country to recognize privacy as a fundamental human right, as enshrined in Art 27 of the 1995 Uganda Constitution as well as in regional and International laws.
The Data Protection and Privacy Act, 2019 aims to protect individuals and their personal data by regulating processing of personal information by state and non-state…
Content type: Examples
In February 2019 Gemalto announced it would supply the Uganda Police Force with its Cogent Automated Biometric Identification System and LiveScan technology in order to improve crime-solving. LiveScan enables police to capture biometric data alongside mugshots and biographical data. CABIS speeds up the biometric matching process by mapping distinctive characteristics in fingerprints, palm prints, and facial images. The Ugandan police will also pilot Gemalto's Mobile Biometric Identification…
Content type: News & Analysis
According to the International Organization for Migration, an estimated 258 million people are international migrants – that is, someone who changes their country of usual residence, That’s one in every 30 people on earth.
These unprecedented movements levels show no sign of slowing down. It is predicted that by 2050, there will be 450 million migrants across the world.
Nowadays, it is politically acceptable to demonise migrants, and countless leaders have spewed divisive and xenophobic…
Content type: State of Privacy
Table of contents
Introduction
Right to Privacy
Communication Surveillance
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgement
The State of Privacy in Uganda is the result of an ongoing collaboration by Privacy International and Unwanted Witness.
Key privacy facts
1. Constitutional privacy protection: The constitution contains an explicit protection of the right to privacy (Art. 27).
2. Data protection law: There is no…
Content type: News & Analysis
This piece was originally published on Just Security.
Ten years ago, an FBI official impersonated an Associated Press reporter to lure and track a teenager suspected of sending in prank bomb threats to his school. To find him, the FBI agent, posing as a reporter, sent the teenager links to a supposed story he was working on, but the links were infested with malware that once clicked on quickly exposed the teen’s location. More recently, the FBI has seized and modified websites so…
Content type: News & Analysis
Around the world, from North America to Europe and Asia, governments are starting to roll out smart meters. While the technology promises increased energy efficiency through greater consumer control over energy consumption, smart meters also raise serious privacy concerns. Smart meters collect energy usage data at high frequencies - typically every five, fifteen or 30 minutes. That level of granularity reveals how much electricity is being used in a home and when, which in turn can paint an…
Content type: Advocacy
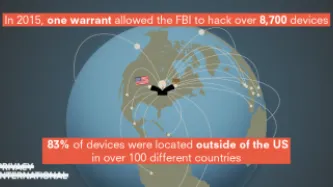
Privacy and security are both essential to protecting individuals, including their autonomy and dignity. Undermining privacy undermines the security of individuals, their devices and the broader infrastructure. People need privacy to freely secure themselves, their information, and fully enjoy other rights.
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. When governments hack for surveillance purposes, they seek to…
Content type: Long Read
The European Union's new data privacy law (General Data Protection Regulation, better known as GDPR) takes effect today May 25th, 2018, after a two-year transition period. Despite some companies appearing to believe otherwise, and many articles misrepresenting its contents, the GDPR will have a significative impact beyond the European Union, and it will extend many of its data privacy safeguards to users’ data globally.
There are a number of reasons that explain this impact:
Obligations…
Content type: Long Read
As we said before, Facebook and Cambridge Analytica scandals are a wake-up call for policy makers. And also a global issue. People around the world are concerned by the exploitation of their data. The current lack of transparency into how companies are using people’s data is unacceptable and needs to be addressed.
There is an entire hidden ecosystem of companies harvesting and sharing personal data. From credit scoring and insurance quotations to targeted political communication, this…
Content type: Advocacy
At the core of data protection debates, there is a power play between empowering individuals to control their data and empowering those who use (or want to) use their data. By regulating data processing, it provides avenues for individuals to exercise their rights if there is any unlawful interference in this power play.
It is crucial for any regulatory framework to be centred around the protection of human rights, autonomy and dignity, and therefore essential to ensure that…
Content type: Press release
Below is a joint statement from Privacy International and Bytes for All.
This Friday, 27 September, marks the conclusion of the 24th session of the UN Human Rights Council, a session which has, for the first time, seen issues of internet surveillance in the spotlight. Privacy International and Bytes for All welcome the attention given at the Human Rights Council to this issue. However, we are concerned about developments which took place that threaten privacy rights and freedom of…
Content type: News & Analysis
7 July 2016
It has been said is that we pay for free services with our personal data. Now, the Privacy Shield exponentially expands this truth and we are paying for the cost of U.S. political dysfunction combined with EU complacency with our privacy. More than four months after the first EU-US Privacy Shield was published on 29 February 2016, a new version has been leaked. Remarkably, it is expected to be adopted.
Four months, two opinions by group of EU data protection…
Content type: News & Analysis
The elections in our midst here, there, and everywhere are increasingly resulting in governments who introduce policies that result in leaps backwards for dignity, equality, civil liberties, and the rule of law. Whether it is Poland or the Philippines, governments are overriding essential safeguards.
This week Britain’s proposed surveillance legislation took another step toward normalising mass surveillance. The United States of America has long promoted mass surveillance and maintains its…
Content type: News & Analysis
For further information on timeline and case history, read this briefing.
Arguments
The argument were based on the written submissions of the parties. The oral statements summarised key points in these submissions.
The submissions can be found on PI’s website under Legal Action. In terms of today’s proceedings (these are now available through webcast)
Counsel for the UK Government, James Eadie QC started off proceedings, his opening arguments were: 1) The issues are of…
Content type: News & Analysis
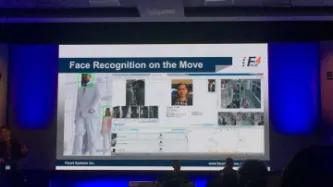
From unlocking a smartphone or getting through an airport, the use of an iris, fingerprint, or your face for identity verification is already widespread, and the market for it is set to rocket. While the technology is not new, its capability and uses are. As people, biometrics offers us much, but risks ultimately only serve data-hungry industries and government agencies: in the name of efficiency and security, it has the potential to bring chaos and vulnerability.
Obtaining reliable…
Content type: News & Analysis
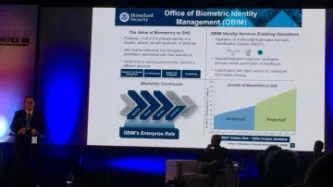
The United States Department of Homeland Security (DHS) has contracted one of the world’s largest arms companies to manage a huge expansion of its biometric surveillance programme.
According to a presentation seen by Privacy International, the new system, known as Homeland Advanced Recognition Technology (HART), will scoop up a whopping 180 million new biometric transactions per year by 2022.
It will replace the Automated Biometric Identification System (IDENT), which currently stores…
Content type: Advocacy
Privacy International wishes to raise serious concerns regarding the proposal to expand immigration records to include social media handles, associated identifiable information and search results. Specifically, in relation to the current request for comments Docket Number DHS 2017 0038, we object to the Department for Homeland Security proposal to update record source categories to include “publicly available information obtained from the internet”, “commercial data providers” and from “…
Content type: Advocacy
Privacy International has today submitted comments to a U.S. government consultation on whether the US Department of Homeland Security (DHS) should keep the social media details of individuals travelling to the US in so-called “Alien Files” documenting all immigrants.
We’ve urged that they don’t, and that they review and stop all similar social media surveillance by the DHS.
The systematic surveillance of social media is an increasingly dangerous trend …
Content type: News & Analysis
On 23 May 2016, the Inter-American Commission on Human Rights (IACHR) reported that severe financial problems have forced it to cancel its July and October sessions in 2016, and all trips planned for this year and, if new funding cannot be secured by 15 June 2016, will lead to the non-renewal of the contracts of 40 per cent of its staff.
Privacy International has joined PEN International, writers and other international members of the International Freedom of Expression Exchange…
Content type: Advocacy
This stakeholder report is a submission by Privacy International (PI), Unwanted Witness Uganda, the Collaboration on International ICT Policy for East and Southern Africa (CIPESA) and the East and Horn of Africa Human Rights Defenders Project (EHAHRDP).
Content type: News & Analysis
Should the European Union agree to legitimise trade with a country that refuses to adhere to European legal standards? This is the fundamental question that will be addressed at tomorrow’s meeting among European privacy regulators when they publish their opinion on the data-sharing agreement known as the ‘Privacy Shield’, the replacement to the failed ‘Safe Harbour’ agreement.
Background
Many of the world’s largest companies, such as Google and Facebook, store their customers’ data in…
Content type: Advocacy
Introduction
On 29 February 2016, the European Commission and the US government released the details of the proposed EU-U.S. “Privacy Shield”. The “Privacy Shield” replaces the now defunct so-called “Safe Harbor”.
The Privacy Shield is in fact a significant number of documents from various parts of the U.S. administration, which merely outline the existing, weak U.S. safeguards applicable to personal data of EU citizens. These documents are meant to serve as the basis for an “adequacy”…