Search
Content type: Landing Page
Working at PIAt Privacy International (PI) we believe that for people to be treated with dignity and to preserve autonomy, we must defend the right for all people everywhere to have access to privacy protection in laws and technologies. The empowerment of the individual is core to our work.Accordingly, PI aims to empower its staff and create a good work environment. PI celebrates diversity in its people, its approaches, and its strategy. People here are looking to change the world by…
Content type: News & Analysis
This is the story of Privacy International's journey to building more secure services. Data collection and administering sensitive data on the open web is risky, and PI had to learn this the hard way.
Many companies say that the privacy of their audiences is their top priority. But do they mean it? Do they invest in it? Doing security on tight budgets is incredibly hard. But it is the natural state of the non-profit sector. We learned this through challenging experiences.…
Content type: News & Analysis
Surveillance in digital spaces is the policing and monitoring of activity of those occupying these spaces. Surveillance affects free speech, privacy and behaviour of digital users. Feminism and a feminist approach to surveillance puts marginalised communities, those that are victims of class discrimination, racial and patriarchal structures, at the centre of discourse around privacy and surveillance.
Surveillance in Pakistan is often seen as an issue of national security. With the National…
Content type: News & Analysis
For further information on timeline and case history, read this briefing.
Arguments
The argument were based on the written submissions of the parties. The oral statements summarised key points in these submissions.
The submissions can be found on PI’s website under Legal Action. In terms of today’s proceedings (these are now available through webcast)
Counsel for the UK Government, James Eadie QC started off proceedings, his opening arguments were: 1) The issues are of…
Content type: News & Analysis
This piece was written by PI Legal Office Millie Graham Wood.
“The UK is leading the way on modern data protection laws and we have worked closely with our EU partners to develop world leading data protection standards”[1] according to, Matt Hancock MP, Minister of State for Digital. However, the proposals in the UK Data Protection Bill continue and expand a highly secretive system which allows processing of personal data to be exempt from key safeguards and fundamental protections on…
Content type: Press release
The European Court of Human Rights will hear a landmark case on surveillance tomorrow (7 November) as part of a challenge to the lawfulness of the UK’s surveillance laws and its intelligence agencies’ mass surveillance practices.
See the attached briefing for case background and historical information.
The case, described by campaigners as a “watershed moment for people’s privacy and freedom of expression across the world”, is being brought by Amnesty International, Liberty, Privacy…
Content type: Press release
Privacy International has filed a federal lawsuit seeking to compel disclosure of records relating to a 1946 surveillance agreement between the US, UK, Australia, Canada and New Zealand, known as the “Five Eyes alliance”.* We are represented by Yale Law School’s Media Freedom and Information Access Clinic (MFIA). The most recent publicly available version of the Five Eyes surveillance agreement dates from 1955. Our complaint was filed before the U.S. District Court for the District of Columbia…
Content type: News & Analysis
October 31st 2017 will mark the 3rd World Cities Day (we will forgive if you did not know that), with the general theme “Better City, Better Life.” On this date, PI will be launching its latest report “Smart Cities: Utopian Vision, Dystopian Reality”. This is an opportunity for us to ask: who exactly are our cities going to become better for?
Technology is often given as an answer when we are not sure what the question is. Cities are no exception to that. The current…
Content type: News & Analysis
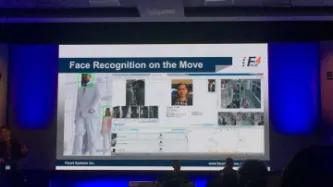
From unlocking a smartphone or getting through an airport, the use of an iris, fingerprint, or your face for identity verification is already widespread, and the market for it is set to rocket. While the technology is not new, its capability and uses are. As people, biometrics offers us much, but risks ultimately only serve data-hungry industries and government agencies: in the name of efficiency and security, it has the potential to bring chaos and vulnerability.
Obtaining reliable…
Content type: News & Analysis
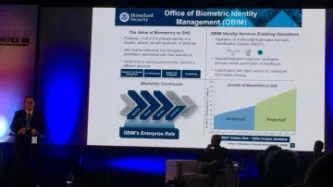
The United States Department of Homeland Security (DHS) has contracted one of the world’s largest arms companies to manage a huge expansion of its biometric surveillance programme.
According to a presentation seen by Privacy International, the new system, known as Homeland Advanced Recognition Technology (HART), will scoop up a whopping 180 million new biometric transactions per year by 2022.
It will replace the Automated Biometric Identification System (IDENT), which currently stores…
Content type: Advocacy
Privacy International wishes to raise serious concerns regarding the proposal to expand immigration records to include social media handles, associated identifiable information and search results. Specifically, in relation to the current request for comments Docket Number DHS 2017 0038, we object to the Department for Homeland Security proposal to update record source categories to include “publicly available information obtained from the internet”, “commercial data providers” and from “…
Content type: Explainer
What is SOCMINT?
Social media intelligence (SOCMINT) refers to the techniques and technologies that allow companies or governments to monitor social media networking sites (SNSs), such as Facebook or Twitter.
SOCMINT includes monitoring of content, such as messages or images posted, and other data, which is generated when someone uses a social media networking site. This information involves person-to-person, person-to-group, group-to-group, and includes interactions that are private and…
Content type: News & Analysis
Privacy International launches the Surveillance Industry Index & New Accompanying Report
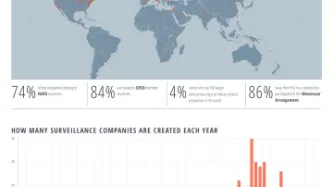
Privacy International is today proud to release the Surveillance Industry Index (SII), the world's largest publicly available educational resource of data and documents of its kind on the surveillance industry, and an accompanying report charting the growth of the industry and its current reach.
The SII, which is based on data collected by journalists, activists, and researchers across the world…
Content type: Report
This report sheds light on the current state of affairs in data retention regulation across the EU post the Tele-2/Watson judgment. Privacy International has consulted with digital rights NGOs and industry from across the European Union to survey 21 national jurisdictions (Austria, Belgium, Bulgaria, Croatia, Cyprus, Czech Republic, France, Germany, Hungary, Ireland, Italy, Luxembourg, the Netherlands, Poland, Portugal, Romania, Slovakia, Slovenia, Spain, Sweden, and the United Kingdom).…
Content type: Press release
Key points
Privacy International surveyed 21 EU member states' legislation on data retention and examined their compliance with fundamental human rights standards
0 out of the 21 States examined by PI are currently in compliance with these standards (as interpreted in two landmark judgements by the Court of Justice of the European Union: Tele-2/Watson and Digital Rights Ireland)
Privacy International is calling for:
EU member states to review their legislation on data retention…
Content type: Press release
Privacy International, in partnership with 30+ national human rights organisations, has today written to national intelligence oversight bodies in over 40 countries seeking information on the intelligence sharing activities of their governments.
Countries may use secret intelligence sharing arrangements to circumvent international and domestic rules on direct surveillance. These arrangements can also lead to the exchange of information that can facilitate human rights abuses,…
Content type: Advocacy
Privacy International has today submitted comments to a U.S. government consultation on whether the US Department of Homeland Security (DHS) should keep the social media details of individuals travelling to the US in so-called “Alien Files” documenting all immigrants.
We’ve urged that they don’t, and that they review and stop all similar social media surveillance by the DHS.
The systematic surveillance of social media is an increasingly dangerous trend …
Content type: Press release
While welcoming the objective of the Bill, Privacy International has sent a briefing to the House of Lords and a letter to Minister of State for Digital, Matt Hancock MP, outlining key concerns and recommendations. The Bill's stated aim is “to create a clear and coherent data protection regime”, and to update the UK data protection law, including by bringing the EU General Data Protection Regulation (GDPR) and the Data Protection Law Enforcement Directive (DPLED) - into the UK domestic system.…
Content type: News & Analysis
We found this image here.
On 11 October, the LIBE Committee of the European Parliament votes on the draft e-privacy regulation. As the landscape of generation, collection, and other processing of data in the digital sphere evolves, the proposal seeks to update the rules on confidentiality and security of electronic communications and online activities.
Unsurprisingly, companies whose business models rely on tracking individuals online have been busy lobbying against the new regulation. The…
Content type: Press release
On 5 October 2017, Privacy International will appear before the UK Court of Appeal to continue its challenge to the British government's large scale hacking powers. The case questions the decision by the Investigatory Powers Tribunal (IPT) to sanction the UK government's power to hack broad categories of people or property without any individualised suspicion.
TIMELINE AND KEY POINTS
- Privacy International began fighting bulk government hacking in 2014 at the…
Content type: Press release
While welcoming the objective of the Bill, Privacy International has sent a briefing to the House of Lords and a letter to Minister of State for Digital, Matt Hancock MP, outlining key concerns and recommendations. The Bill's stated aim is “to create a clear and coherent data protection regime”, and to update the UK data protection law, including by bringing the EU General Data Protection Regulation (GDPR) and the Data Protection Law Enforcement Directive (DPLED) - into the UK domestic system.…
Content type: People
Barry was a long-time trustee of Privacy International, up until his term ended in September 2017. In recognition of his substantial contribution to PI, the Board of Trustees designated him as Trustee Emeritus.
Barry was the Director of the American Civil Liberties Union's Program on Technology and Liberty. Prior to leading that programme, Barry served as Associate Director of the ACLU.
He has advocated tirelessly for privacy and information technology issues, speaking to audiences…
Content type: Advocacy
On 13 September 2017, Privacy International, in partnership with 30+ national human rights organisations, launched an international campaign for greater transparency around secretive intelligence sharing activities between governments. As part of this campaign, PI wrote to national intelligence oversight bodies in over 40 countries seeking information about the intelligence sharing activities of their governments. PI has created an interactive map which illustrates the countries…
Content type: Press release
Key points
Privacy International surveyed 21 EU member states' legislation on data retention and examined their compliance with fundamental human rights standards
0 out of the 21 States examined by PI are currently in compliance with these standards (as interpreted in two landmark judgements by the Court of Justice of the European Union: Tele-2/Watson and Digital Rights Ireland)
Privacy International is calling for:
EU member states to review their legislation on data retention…
Content type: Advocacy
This report sheds light on the current state of affairs in data retention regulation across the EU post the Tele-2/Watson judgment. Privacy International has consulted with digital rights NGOs and industry from across the European Union to survey 21 national jurisdictions (Austria, Belgium, Bulgaria, Croatia, Cyprus, Czech Republic, France, Germany, Hungary, Ireland, Italy, Luxembourg, the Netherlands, Poland, Portugal, Romania, Slovakia, Slovenia, Spain, Sweden, and the United…
Content type: Case Study
Cities around the world are deploying collecting increasing amounts of data and the public is not part of deciding if and how such systems are deployed.
Smart cities represent a market expected to reach almost $760 billion dollars by 2020. All over the world, deals are signed between local governments and private companies, often behind closed doors. The public has been left out of this debate while the current reality of smart cities redefines people’s right to privacy and creates new…
Content type: Case Study
Our connected devices carry and communicate vast amounts of personal information, both visible and invisible.
What three things would you grab if your house was on fire? It’s a sure bet your mobile is going to rank pretty high. It’s our identity, saying more about us than we perhaps realise. It contains our photos, calendar, internet browsing, locations of where we go, where we’ve been, our emails, social media. It holds our online banking, notes with half written poems, shopping lists, shows…
Content type: Case Study
Political campaigns around the world have turned into sophisticated data operations. In the US, Evangelical Christians candidates reach out to unregistered Christians and use a scoring system to predict how seriously millions these of voters take their faith. As early as 2008, the Obama campaign conducted a data operation which assigned every voter in the US a pair of scores that predicted how likely they would cast a ballot, and whether or not they supported him. The campaign was so confident…