Search
Content type: Long Read
Privacy and security are both essential to protecting individuals, including their autonomy and dignity. Undermining privacy undermines the security of individuals, their devices and the broader infrastructure. People need privacy to freely secure themselves, their information, and fully enjoy other rights. However, a growing number of governments around the world are embracing hacking to facilitate their surveillance activities.
As a form of government surveillance, hacking presents…
Content type: News & Analysis
Privacy International (PI) welcomes today's report from the UK Information Commissioner's Office (ICO) into three credit reference agencies (CRAs) which also operate as data brokers for direct marketing purposes. As a result, the ICO has ordered the credit reference agency Experian to make fundamental changes to how it handles people's personal data within its offline direct marketing services.
It is a long overdue enforcement action against Experian.…
Content type: Long Read
Content type: Case Study
amaBhungane is an independent, non-profit newsroom based in South Africa. amaBhungane plays a key role in exposing corruption, promoting transparency and accountability at all levels of government. In recent years, amaBhungane has been at the forefront of privacy litigation in amaBhungane Centre and Sole Stephen v. Minister of Justice and Correctional Services and others, a challenge to South Africa’s expansive surveillance laws.
Qn: Please briefly describe your work and the issues/…
Content type: Case Study
Ananda Badudu is an activist, musician and former journalist. In September 2019, he started a crowdfunding campaign page to support student protesters taking part in demonstrations against the Indonesian House of Representatives.
Qn: Please briefly describe your work and the issues/topics you work on.
I’ve been full-time musician for 2 years. Before that I was a journalist from 2010 to 2016, first at Tempo, then at Vice. In late September 2019, I took part in a crowd-funding campaign…
Content type: Case Study
Centro Prodh is a non-profit civil association which promotes human rights, and has been involved in some of the most emblematic cases in Mexico. The impact of their work is only matched by the severity of surveillance threats they face. In his end-of-mission statement after a visit to Mexico, the former Special Rapporteur on the situation of human rights defenders expressed specific concern about Centro Prodh in light of its being targeted for its work on enforced disappearances,…
Content type: News & Analysis
Privacy International (PI) has today warned UK regulatory and law enforcement bodies about the potential deployment of an extensive and potentially nationwide police facial recognition surveillance system. We are urging them to investigate and take steps to ensure that no ‘backdoor’ for unlawful facial recognition surveillance will be developed under the umbrella of a crime reporting system.
According to pricing and data-sharing templates, UK surveillance company Facewatch is offering to…
Content type: Long Read
As more and more of us feel compelled to cover our faces with masks, companies that work on facial recognition are confronted with a new challenge: how to make their products relevant in an era where masks have gone from being seen as the attribute of those trying to hide to the accessory of good Samaritans trying to protect others.
Facewatch is one of those companies. In May 2020, they announced they had developed a new form of facial recognition technology that allows for the…
Content type: Long Read
Q&A: EU's top court rules that UK, French and Belgian mass surveillance regimes must respect privacy
Content type: Press release
By treating everyone as a suspect, the bulk data collection or retention regimes engage European fundamental rights to privacy, data protection, freedom of expression, as guaranteed respectively by Articles 7, 8, and 11 of the EU Charter of Fundamental Rights.
Caroline Wilson Palow, Legal Director of Privacy International, said:
"Today’s judgment reinforces the rule of law in the EU. In these turbulent times, it serves as a reminder that no government should be above the law. Democratic…
Content type: News & Analysis
On September 16, Google announced their intention to enforce a new "stalkerware" policy after a 15 day grace period ending on 1 October 2020.The policy change states that the Google Play Store will only host stalkerware apps that give "a persistent notification is displayed while the data is being transmitted."
In its announcement, Google defines stalkerware as "Code that transmits personal information off the device without adequate notice or consent and doesn't display a persistent…
Content type: News & Analysis
Back in June, we published our investigation into Facebook brands, highlighting how Facebook failed to provide its users with a fair and meaningful understanding of how targeted advertising operated on its platform, and a number of issues preventing users from exercising their rights to the fullest possible extent. In face of the serious gaps encountered, we published an open letter to Facebook drawing attention to four main issues as well as our recommended actions to tackle them. This letter…
Content type: Press release
A joint press release from Privacy International, Reprieve, CAJ, and the Pat Finucane Centre.
Agents of MI5 and other Government bodies could be legally authorised to commit crimes under new legislation introduced today. There appear to be no express limits in the legislation on the types of crime which could be authorised.
The Covert Human Intelligence Sources (Criminal Conduct) Bill appears not to explicitly prohibit the authorisation of murder, torture, or sexual violence. Reprieve,…
Content type: Examples
As part of efforts to make returning to campus safer, US universities are considering or implementing mandates requiring students to install exposure notification apps, quarantine enforcement programs, and other unproven new technologies, risking exacerbating existing inequalities in access to both technology and education. In some cases, such as Indiana University, UMass Amherst, and the University of New Hampshire, universities are requiring students to make a blanket commitment to install…
Content type: Examples
US epidemiologists are complaining that secrecy is interfering with public health efforts to curb the coronavirus. Beginning in April, California state and county health authorities have refused requests from scientists from Stanford University and several University of California campuses for detailed COVID-19 and contact tracing data for research they hope will find more effective approaches to slowing the epidemic. The agencies have cited reasons such as workload constraints and privacy…
Content type: Long Read
An edited version of this article was originally published on the EDRi website in September 2020.
Introduction
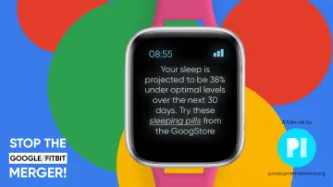
Monopolies, mergers and acquisitions, anti-trust laws. These may seem like tangential or irrelevant issues for privacy and digital rights organisations. But having run our first public petition opposing a big tech merger, we wanted to set out why we think this is an important frontier for people's rights across Europe and indeed across the world.
In June, Google notified the…
Content type: Case Study
The Peruvian government has a history of collaboration with the private sector in developing technology with the alleged purpose of providing greater security to citizens. The most recent example, the smartphone application "Peru En Tus Manos" launched in the context of the Covid-19 crisis, has been developed in a similar fashion and currently collects geolocation data on more than a million users. Although Peru has a proper legal framework for public private partnerships, developments are…
Content type: Case Study
Como is one of the most advanced cities in Italy in the use of facial recognition technology (FRT). An investigation for the Italian Wired magazine published in June 2020 exposed how the system had been bought, installed and tested for months with little transparency and despite the lack of a clear legal framework.
The investigation was entirely based on tools available to everyone, such as Freedom of Information requests (FOI requests. Similar to PI’s campaign 'Unmasking policing, inc', it…
Content type: Report
Many countries in the world have existing ID cards - of varying types and prevalence - there has been a new wave in recent years of state “digital identity” initiatives.
The systems that states put in place to identify citizens and non-citizens bring with them a great deal of risks.
This is particularly the case when they involve biometrics - the physical characteristics of a person, like fingerprints, iris scans, and facial photographs.
Activists and civil society organisations around the…
Content type: Report
A common theme of all major pieces of national jurisprudence analyzing the rights implications of national identity system is an analysis of the systems’ impacts on the right to privacy.
The use of any data by the State including the implementation of an ID system must be done against this backdrop with respect for all fundamental human rights. The collection of data to be used in the system and the storage of data can each independently implicate privacy rights and involve overlapping and…
Content type: Report
National identity systems naturally implicate data protection issues, given the high volume of data necessary for the systems’ functioning.
This wide range and high volume of data implicates raises the following issues:
consent as individuals should be aware and approve of their data’s collection, storage, and use if the system is to function lawfully. Despite this, identity systems often lack necessary safeguards requiring consent and the mandatory nature of systems ignores consent…
Content type: Report
Madhewoo (Appellant) v The State of Mauritius and another (Respondents) (Mauritius)
The first case in the recent line of national identity systems cases is Madhewoo v. The State of Mauritius and Anor. This case, decided by the Mauritian Supreme Court in 2015, upheld the collection of fingerprint data as part of a national identity card scheme, but rejected a centralised database for the storage of this data in the system. The Mauritian court found that privacy rights guaranteed by the…
Content type: News & Analysis
A new report by the UN Working Group on mercenaries analyses the impact of the use of private military and security services in immigration and border management on the rights of migrants, and highlights the responsibilities of private actors in human rights abuses as well as lack of oversight and, ultimately, of accountability of the system.
Governments worldwide have prioritised an approach to immigration that criminalises the act of migration and focuses on security.
Today, borders are not…
Content type: Examples
Brazil’s Federal Supreme Court has struck down a government order forcing telecommunications companies to provide access to the user information relating to the country’s 200 million citizens to enable the government to conduct phone interviews to determine the economic response to the COVID-19 pandemic. In the process, the ruling established that data protection is a fundamental right. However, privacy advocates warned that the lack of established data protection law in the country opened the…
Content type: News & Analysis
Back in January, Privacy International and over 50 other organisations wrote to Google asking the company to take action over pre-installed apps that cannot be deleted (often known as “bloatware”), which can leave users vulnerable to their data being collected, shared and exposed without their knowledge or consent. Thousands of people from over 50 countries signed our petition supporting this ask. We welcome the constructive conversations we had with Google following this campaign and for the…
Content type: Long Read
The Law Enforcement Data Service (LEDS) is a unified, common interface to a new mega-database currently being developed by the Home Office National Law Enforcement Data Programme (NLEDP).
It might not sound like the most exciting thing in the world (and it isn't!) - but it will have a profound impact on policing and surveillance in the UK for generations.
We believe that the development of the programme poses a threat to privacy and other rights and must be subjected to strong oversight,…
Content type: Case Study
Privacy matters. It matters when you’re walking the streets of your home town and when you’re fleeing your home in search of safety. It matters if you’re at a protest or if you’re in bed.
Our wellbeing in each of these instances depends on the protection of our privacy. No situation can be fully understood in isolation.
Unjustifiable intrusions on our privacy become a weapon to eradicate communities and prey upon refugees and asylum seekers, push people away from protests in fear of…
Content type: Explainer
In the name of reinforcing migration control and increasing security, the EU is introducing a host of new surveillance measures aimed at short-term visitors to the Schengen area. New tools and technologies being introduced as part of the visa application process and the incoming “travel authorisation” requirement include automated profiling systems, a ‘pre-crime’ watchlist, and the automated cross-checking of numerous national, European and international databases. There are significant risks…
Content type: News & Analysis
Banning TikTok? It's time to fix the out-of-control data exploitation industry - not a symptom of it
Chinese apps and tech companies have been at the forefront of the news recently. Following India's ban of 59 chinese apps in July, President Trump announced his desire to ban TikTok, shortly followed by his backing of Microsoft's intention to buy the US branch of its parent company ByteDance. Other than others lip syncing his public declaration, what does President Trump fear from this app, run by a firm, based in China?
It's all about that data
One clear answer emerges: the exploitation of…
Content type: Explainer
At first glance, infrared temperature checks would appear to provide much-needed reassurance for people concerned about their own health, as well as that of loved ones and colleagues, as the lockdown is lifted. More people are beginning to travel, and are re-entering offices, airports, and other contained public and private spaces. Thermal imaging cameras are presented as an effective way to detect if someone has one of the symptoms of the coronavirus - a temperature.
However, there is little…