Search
Content type: Examples
In December 2012, the US Federal Trade Commission opened an investigation into data brokers' privacy practices, requesting information from nine companies: Acxiom, Corelogic, Datalogix, eBureau, ID Analytics, Intelius, Peekyou, Rapleaf, and Recorded Future. The FTC sought information about: the nature and sources of the consumer information the data brokers collect; how they use, maintain, and disseminate the information; and the extent to which the data brokers allow consumers to access and…
Content type: Examples
In 2003, the Electronic Privacy Information Center, Privacy Rights Clearinghouse, and PrivacyActivism filed complaints with the US Federal Trade Commission alleging that JetBlue Airways and Acxiom engaged in deceptive trade practices by supplying personal information about consumers to the Alabama-based information mining company Torch Concepts without the knowledge or consent of those consumers. EPIC argued that the FTC should investigate and enjoin these activities, which it believed were in…
Content type: Examples
In 2013, 44 years after Acxiom went into business selling consumer data, the company opened a website, aboutthedata.com, to allow Americans to see the data the company holds about them and make it easier to opt out of tracking. However, using the site requires visitors to input a substantial amount of personal information for authentication; the results of these searchers omit many of the data elements Acxoim sells its customers; the privacy policy allows the company considerable latitude in…
Content type: Examples
In 2003, the for-profit privacy company Private Citizen, which helps paying consumers unsubscribe from telemarketers' lists and direct mailing offers, found that Acxiom had begun rejecting the batches of opt-out notices the service sent on behalf of its subscribers. Acxiom insisted that each person was required to contact the company individually, apparently on the basis that each should hear the company's pitch for staying in its database. Aciom's membership of the Direct Marketing Association…
Content type: Examples
In 2012, Acxiom's database was reported to be the largest commercial database on consumers in the world, containing approximately 1,500 data points, or "elements", for each of the 500 million active consumers worldwide and processing more than 50 trillion data transactions per year. Each of the individuals in its database is slotted into one of 70 specific socioeconomic clusters as an attempt to predict what they will buy and what types of persuasion they will respond to. In its latest fiscal…
Content type: Examples
In April 2018, Facebook announced that in six months it would end a programme it called "Partner Categories", in which the social network acted as a bridge between data brokers like Acxiom, Epsilon, and TransUnion and the consumers their customers want to reach. In this deal, Facebook did not actually sell the data it collects; instead, it targeted ads to the lists of people the data brokers uploaded. Facebook users can see the results for themselves by going to their privacy settings and…
Content type: Examples
In 2016, Acxiom announced a deal with the media delivery company Valassis, a subsidiary of Harland Clarke Holdings Corp, intended to provide marketers with better post-campaign analytics. The linkage of the two companies was intended to "provide an integrated view of a consumer's purchase behaviour" by integrating Acxiom's people-based recognition tools with Valassis' services to advertisers, such as targeting its customers' most influential and valuable shoppers.
http://www.valassis.com/about…
Content type: Examples
In 2004, the US Department of Justice investigated the theft of 8.2GB of personal data from File Transfer Protocol (FTP) servers belonging to Acxiom between 2002 and 2003. The case was thought to represent the largest case of data theft at the time. Scott Levine, the owner of the email spamming company Snipermail, was indicated on 144 offences in connection with the attack, and was eventually found guilty of 120 of them and sentenced to jail for eight years. In all, Levine and Snipermail were…
Content type: Examples
In 2014, Acxiom's chief product and engineering officer, Phil Mui, described the system the company had been building to link individuals' activities across the many channels, devices, and applications they use. A single individual may accumulate four different personas via 24 cookies across six different devices; Acxiom's goal was to unify these. The company holds some 5,000 pieces of customer data for each of the 700 million individual consumers in its database.
https://www.mediapost.com/…
Content type: Examples
In 2003, Acxiom announced that law enforcement officials had notified the company that it had been hacked, and that the attacker had intercepted information in transit between the company and some of its clients via a File Transfer Protocol (FTP) server located outside the company's firewall. The hacker, later identified as Daniel Baas and prosecuted, had access to passwords and data files belonging to Acxiom customers for two years, from January 2001 to January 2003.
https://www.…
Content type: Long Read
Photo Credit: Max Pixel
The fintech sector, with its data-intensive approach to financial services, faces a looming problem. Scandals such as Cambridge Analytica have brought public awareness about abuses involving the use of personal data from Facebook and other sources. Many of these are the same data sets that the fintech sector uses. With the growth of the fintech industry, and its increase in power and influence, it becomes essential to interrogate this use of data by the…
Content type: Advocacy
Privacy International welcomes the effort by the Government of India to reaffirm its commitment to upholding and respecting the right to privacy, and for noting the need to regulate the processing of personal data as essential for the protection of privacy through the adoption of a data protection law.
The urgent need for this legislation has been validated in the Supreme Court decision regarding the Aadhaar Act, which stipulates the need for a robust data protection regime. …
Content type: News & Analysis
Image Source
On 10 October 2018, the US Senate Committee on Commerce, Science, and Transportation, will convene a hearing titled “Consumer Data Privacy: Examining Lessons From the European Union’s General Data Protection Regulation and the California Consumer Privacy Act".
The Senate will hear from:
Dr. Andrea Jelinek, Chair, European Data Protection Board
Mr. Alastair Mactaggart, Board Chair, Californians for Consumer Privacy
Ms. Laura Moy, Executive Director and Adjunct…
Content type: Examples
Google announced on October 8 having discovered a vulnerability in the Google+ API which has been open since 2015. This vulnerability allowed third-party developers to access data for more than 500,000 users, including their usernames, email addresses, occupation, date of birth, profile photos, and gender-related information. While Google only retains 2 weeks of activity logs and cannot assert the exact reach of the breach, it believes that up to 438 applications had access to these data.…
Content type: Long Read
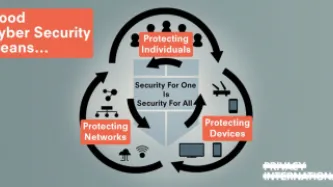
Since 2004, October has been designated National Cyber Security Awareness Month in the United States. Many other countries have followed suit, as part of the effort to raise awareness about the importance of cybersecurity, and how we can all work together to improve it.
However, cyber security (or sometimes, just ‘cyber’) has not only become a term with multiple and sometimes contradictory meanings - that go from digital security or digital diplomacy to criminal activities with a digital…
Content type: News & Analysis
Image attribution: By Blue Diamond Gallery CC BY-SA 3.0.
In March 2017, when the UN Human Rights Council requested the High Commissioner for Human Rights to prepare a report on the right to privacy in the digital age, including the responsibility of business enterprises, Cambridge Analytica was an obscure company among others. A year later the data exploitation scandal erupted, leading to plenty of soul searching by politicians in US, UK, Europe and elsewhere, pledges of…
Content type: Advocacy
In parallel to the legislative process initiated by the Kenya Senate in July 2018, a Task Force constituted by the Ministry of Information, Communication and Telecommunication developed a draft Data Protection Bill which it published for consultation in May of this year.
Privacy International and its Kenya Partners, the National Coalition of Human Rights Defenders – Kenya (NCHRD-K), the Centre for Intellectual Property and Information Technology (CIPIT) are pleased to have had the…
Content type: Advocacy
Privacy International encourages the European Commission to consider ways to reform or at least re-interpret competition regulation to address the data protection implications and the broader societal challenges posed by the exploitation of data by big corporations. This includes, for example, systematic consideration of data protection issues (including though consultation with relevant data protection authorities and organisations protecting privacy and consumer rights) when assessing mergers…
Content type: Examples
Facebook-owned Onavo VPN (adertised as a way to block harmful websites, and keep a user's data safe) is pulled from the Apple App Store due to tracking, collecting, and analysing customers' usage data, including from other unrelated apps.
https://arstechnica.com/tech-policy/2018/08/facebook-violates-apples-data-gathering-rules-pulls-vpn-from-app-store/
Author: Valentina Palladino
Ars Technica
Content type: Examples
30 million users had their accounts breached, with a total of 90 million accounts reset after Facebook's "view as" feature leaked unique user account access tokens, allowing attackers to not only trivially impersonate any other user on the platform, but also to potentially automate the attack on a massive scale using their API.
This is of particular concern where these access tokens were used as a "Single Sign On" for third-party services who authenticate against Facebook. The…
Content type: Advocacy
Both “cyber security” and “cyber crime” are terms widely used but often poorly understood. This briefing provides an overview of terminology, concepts and trends in addressing cyber security and cyber crime. It describes the differences between them and associated challenges for the protection of peoples’ security and their human rights. It also highlights key elements and examples from cyber security frameworks and cyber crime legislation globally. The aim is to provide a basis for…