Responsible security
Manufacturers and/or vendors must be responsible for the security and privacy design in the products they manufacture and sell, throughout a clearly identified period.
As computing becomes embedded everywhere, privacy, security and safety issues converge. In the future, our infrastructure will be insecure and unsafe due to insecure devices and components that are not patched.
What's the problem?
As more devices become ‘connected’ and services become ubiquitous, they may generate and collect massive amounts of data in excess of what is necessary for the provision of the specific service or function. For instance, the “always on” nature of connected or smart devices and the granularity of data collected potentially enables the provider and other parties access to vast types and volumes of data.
A mere software update or change in business practice can change the frequency of sharing and the parties to whom data can be transmitted can change at any point in time.
Securing these technologies becomes even more challenging as they are embedded in complex systems, difficult to alter or update for security purposes, and control by the individual is limited. Too often companies decide for business reasons they will no longer support the software or hardware, including for security updates when vulnerabilities are found, leaving consumers unprotected.
This creates an unsafe environment. Unpatched, insecure, and unmaintained systems and infrastructure leave us vulnerable.
Why this matters
In the future, our infrastructure will be insecure and unsafe due to insecure devices and components that are not patched. Manufacturers are not held responsible, vendors do not question the security of their products, and supply chain problems are left unaddressed.
There are too few incentives to implement and increase security. Even the companies who take security relatively seriously by doing bug bounties and updates often phase out the patching of security of software and devices after a period of time that has never been made clear to the public.
Too often marginalised communities have to use technologies that do not receive security updates in a timely manner, if at all or have to incur additional costs. Users should be able to accept updates without having to worry that it also adds functionalities that might be privacy-invasive or otherwise against the interest of the user.
What we would like to see
Security researchers will be able to and encouraged to test the products and services to break security and privacy. Open and transparent security research identifies defences necessary for cyber-physical security and safety and challenges information asymmetry.
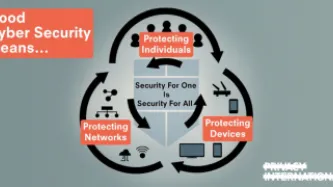
Cyber security will be considered a common good, which benefits everyone. Policies and initiatives must not advantage only some people over others. This means that a national government policy should not disadvantage people outside that country, or certain sectors of society.
What this will mean
Industry will have to commit to patches and updates for their systems, and create an environment where bugs are sought and reported, and fixed for users globally.
Industry will have to clearly articulate the length of time for which they will commit to security updates for a given service or product. It is essentially statement of expiration of the security viability of that connected service.
Listening and always on devices that are under the control of the service provider will be patched so long as it is processing for that provider.
Essential reform actions
Companies will have to notify individuals of the life-span of technologies and the period for which they will maintain security updates.
Consumer protection policy should reflect the security responsibilities of manufacturers and/or vendors.