Advanced Search
Content Type: Report
Financial services are changing, with technology being a key driver. It is affecting the nature of financial services, from credit and lending through to insurance, and even the future of money itself.
The field of fintech is where the attention and investment is flowing. Within it, new sources of data are being used by existing institutions and new entrants. They are using new forms of data analysis.
These changes are significant to this sector and the lives of people it serves. This…
Content Type: Press release
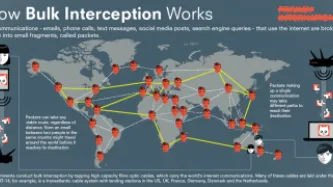
In today’s latest hearing in our ongoing legal challenge against the collection of massive troves of our personal data by the UK intelligence agencies, shocking new evidence has emerged about GCHQ’s attempts to yet again avoid proper independent scrutiny for its deeply intrusive surveillance activities.
In a truly breath-taking exchange of letters between the Investigatory Powers Commissioner’s Office (“IPCO”) and the Director of Legal Affairs at GCHQ, it has emerged that GCHQ have…
Content Type: Long Read
This piece was originally published in Just Security in November 2017.
The upcoming expiration of Section 702 of the Foreign Intelligence Surveillance Act (FISA) has launched a fresh wave of debate on how the statute’s “backdoor search loophole” allows the U.S. government to access Americans’ communications by searching information gathered on foreign intelligence grounds without a warrant. But while discussion about domestic information sharing is important, a critical…
Content Type: Landing Page
Privacy International is a registered charity in England & Wales (no. 1147471). We raise money to fund our work to promote and protect the human right of privacy throughout the world.
Our primary cost is our staff, whose legal, technological and campaigning expertise are PI’s main resource in achieving impact.
We also use our funds to protect privacy directly in dozens of countries across the world. We support national advocacy organisations who are driving change in their countries, and…
Content Type: Landing Page
Privacy International’s governing body is the Board of Trustees. The primary responsibility of the Board is to provide strategic leadership by formulating and reviewing Privacy International's strategic aims in consultation with staff, setting overall policy, regularly evaluating the charity's performance, and ensuring compliance with UK law. The board meets up to four times a year.New Trustees are recruited through an open application process. Appointments are made on the basis of…
Content Type: Landing Page
Working at PIAt Privacy International (PI) we believe that for people to be treated with dignity and to preserve autonomy, we must defend the right for all people everywhere to have access to privacy protection in laws and technologies. The empowerment of the individual is core to our work.Accordingly, PI aims to empower its staff and create a good work environment. PI celebrates diversity in its people, its approaches, and its strategy. People here are looking to change the world by…
Content Type: News & Analysis
This is the story of Privacy International's journey to building more secure services. Data collection and administering sensitive data on the open web is risky, and PI had to learn this the hard way.
Many companies say that the privacy of their audiences is their top priority. But do they mean it? Do they invest in it? Doing security on tight budgets is incredibly hard. But it is the natural state of the non-profit sector. We learned this through challenging experiences.…
Content Type: Landing Page
PI protects people’s privacy, dignity and freedoms from abuses by companies and governments. At PI we work to change the systems so that people have the protections they need. We create concrete change today so that freedom and privacy will be foundations of tomorrow’s societies.We want a world where people are in control of their data and technologies, free from exploitation, and in control of their lives.Through our strategic work we build a better future where:Companies and industries…
Content Type: Landing Page
In this section you will find a wide range of content that we hope you will find useful in learning more about how technology, privacy, autonomy and freedom are deeply interconnected. We also provide some guides on steps you can take to enhance your privacy - although, we need to be clear that few, if any, watertight measures exist, which is why we continue to press for better regulation, better safeguards and better technological solutions.
Content Type: Landing Page
PI supports people everywhere to protect privacy, dignity, and freedom.
We target companies and governments that don’t respect your right to be free from their prying technologies. We expose their practices to public scrutiny. We pursue them in court. With you, we fight in the public interest, demanding better rules and stronger technologies globally. We help other organisations around the world. We help you learn how to protect yourself, your loved ones, and everyone else around the world…
Content Type: Landing Page
We fight for the right to privacy of everyone everywhere. People must have access to privacy protection without regard to citizenship, race and ethnicity, economic status, gender, age, education.
We are building a global movement. We are supporting civil society partners in countries across the Global South, who constitute our international network of privacy advocates and researchers. Together we are building expertise on law and technology that investigates local developments and advocates…
Content Type: Landing Page
Litigation is a core component of PI's advocacy strategy. PI files cases, pursues regulatory complaints, and intervenes in worthwhile legal challenges around the world in order to defend and enhance our privacy rights and the rule of law. Below you will find links to our current and past legal work.
Content Type: Landing Page
Governments and corporations are using technology to exploit us. Their abuses of power threaten our freedoms and the very things that make us human.
That’s why PI is here: to protect democracy, defend people's dignity, and demand accountability from institutions who breach public trust.
Content Type: News & Analysis
Surveillance in digital spaces is the policing and monitoring of activity of those occupying these spaces. Surveillance affects free speech, privacy and behaviour of digital users. Feminism and a feminist approach to surveillance puts marginalised communities, those that are victims of class discrimination, racial and patriarchal structures, at the centre of discourse around privacy and surveillance.
Surveillance in Pakistan is often seen as an issue of national security. With the National…
Content Type: Advocacy
Thornsec is a piece of software developed by Privacy International’s Tech Team which is an automated way to deploy, test, and audit internal and external services for an organisation, saving a lot of time and creating a sustainable security model. We are using this software to run all of Privacy International’s services – website, calendar, project management tools, Tor hidden services, VPNs. The whole system runs on two servers and the whole cost is around US$1000 to set up.
Thornsec is…
Content Type: Advocacy
This briefing covers Part 3 (law enforcement processing) and Part 4 (intelligence services processing) of the Data Protection Bill.
Content Type: Advocacy
Privacy International has responded to the European Commission’s consultation on the interoperability of EU information systems for borders and security.
The Commission is currently looking at ways in which various border control and policing EU databases and IT systems can be connected to share and exchange more data.
The plans raise a number of concerns as highlighted by Privacy International in our response. These relate to significant potential harms associated with…
Content Type: News & Analysis
For further information on timeline and case history, read this briefing.
Arguments
The argument were based on the written submissions of the parties. The oral statements summarised key points in these submissions.
The submissions can be found on PI’s website under Legal Action. In terms of today’s proceedings (these are now available through webcast)
Counsel for the UK Government, James Eadie QC started off proceedings, his opening arguments were: 1) The issues are of…
Content Type: News & Analysis
This piece was co-written with Valeria Milanes of the Asociación por los Derechos Civiles (ADC). A Spanish version is available here.
In January 2015, the intelligence regime in Argentina was put in the limelight following the death of Prosecutor Alberto Nisman. It was alleged that the intelligence services were involved in his death. This scandal prompted reform of the country’s intelligence system.
In February of the same year, the Intelligence Act (N° 25…
Content Type: News & Analysis
This piece was written by PI Legal Office Millie Graham Wood.
“The UK is leading the way on modern data protection laws and we have worked closely with our EU partners to develop world leading data protection standards”[1] according to, Matt Hancock MP, Minister of State for Digital. However, the proposals in the UK Data Protection Bill continue and expand a highly secretive system which allows processing of personal data to be exempt from key safeguards and fundamental protections on…
Content Type: Press release
The European Court of Human Rights will hear a landmark case on surveillance tomorrow (7 November) as part of a challenge to the lawfulness of the UK’s surveillance laws and its intelligence agencies’ mass surveillance practices.
See the attached briefing for case background and historical information.
The case, described by campaigners as a “watershed moment for people’s privacy and freedom of expression across the world”, is being brought by Amnesty International, Liberty, Privacy…