Advanced Search
Content Type: News & Analysis
Palantir and the UN’s World Food Programme (WFP) are partnering for a reported $45 million. Palantir, a US-based company that sells data software and has been the centre of numerous scandals.
The World Food Programme provides assistance in food and nutrition to around 92 million people each year. Systems that are produced in agreements such as the one between WFP and Palantir increase risks to the people the they are attempting to help. There are risks to both individuals and whole populations…
Content Type: Impact Case Study
What HappenedOn 5 June 2013, The Guardian published the first in a series of documents disclosed by Edward Snowden, a whistleblower who had worked with the NSA. The documents revealed wide-ranging mass surveillance programs conducted by the USA’s National Security Agency (NSA) and the UK’s Government Communications Headquarters (GCHQ), which capture the communications and data of hundreds of millions of people around the world. In addition to revealing the mass surveillance programs of the NSA…
Content Type: Press release
On the day that GDPR comes into force, PI has launched a campaign investigating a range of data companies that make up a largely hidden data ecosystem. This hidden data ecosystem is comprised of thousands of non-consumer facing data companies - such as Acxiom, Criteo, Quantcast - that amass and exploit large amounts of personal data. Using the rights and obligations provided for within the new data privacy law, PI's campaign involves investigating a selection of these companies whose business…
Content Type: Impact Case Study
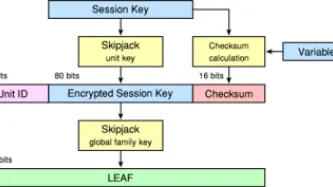
PI and our global partners have been at the forefront of challenging communications data retention for over a decade.
What is the problem
Communications data, also known as metadata, tells a story about your digital activity and answers the who, when, what, and how of a specific communication. While communications data doesn't include the contents of a message, all of the other information about the message can be very revealing about people, their habits, thoughts, health and personal…
Content Type: Impact Case Study
What happenedThe Clinton Administration kicked off the cypto-wars in 1993 with the Clipper Chip. The continued application of export controls restrained the deployment of strong cryptography in products at a key moment of internet history: as it began to be embedded in software and networking. What we didIn the early phases of the crypto-wars we placed pressure on global industry to implement encryption in their products. We ran campaigns and events across the world on the need for strong…
Content Type: Impact Case Study
What is the problem
Business models of lots of companies is based on data exploitation. Big Tech companies such Google, Amazon, Facebook; data brokers; online services; apps and many others collect, use and share huge amounts of data about us, frequently without our explicit consent of knowledge. Using implicit attributes of low-cost devices, their ‘free’ services or apps and other sources, they create unmatched tracking and targeting capabilities which are being used against us.
Why it is…
Content Type: Impact Case Study
What happenedIn the aftermath of 9/11, Governments across the world rushed to legislate to expand surveillance. GovernmentsMoved to limit debate and reduce consultations as they legislated with speed.Created new systems to collect data on all travellers, for the purpose of profiling and risk scoring.Expanded identity schemes, and began demanding biometrics, particularly at borders.Developed financial surveillance mechanisms on an unprecedented scale.What we didFew non-governmental…
Content Type: Impact Case Study
What happenedGovernments continuously seek to expand their communications surveillance powers. In the 1990s it was in the context of applying telephone surveillance laws to the internet. In the 2000s a spate of new laws arrived in response to 9/11. Expansions were then sought to monitor over-the-top services within the framing of Web 2.0. Then in the post-Snowden environment Governments rushed to legislate their previously secret powers.What we didWe supported…
Content Type: Impact Case Study
What is the problem
In the 1990s privacy was often maligned as a ‘rich Westerner’s right’. We were told often that non-Westerners didn’t need privacy and had different cultural attitudes and would greet surveillance policies and technologies — often exported from the West.
Global civil society was composed mostly of a few individuals with no resources but great passion. The larger and more established NGOs, such as consumer and human rights organisations were less interested in ‘digital’ and ‘…
Content Type: Impact Case Study
What happenedSince the late 1980s governments across the world have been trying to build identity registries. By the early 1990s, there were similar policies being pursued by a number of governments across the Pacific region, with similar technologies from the same companies. In the mid-90s ID cards became a ‘modern’ policy, implementing smart cards. By 9/11 biometric IDs became the preferred solution to undefinable problems. Then came vast databases of biometrics to identify people — with…
Content Type: Impact Case Study
[Photo By Ludovic Courtès - Own work, CC BY-SA 3.0] Last update: 14 December 2022What is the problem and why it is importantUntil the early '10s, the right to privacy had been sidelined and largely unaddressed within the UN human rights monitoring mechanisms, despite being upheld as a fundamental human right in the Universal Declaration of Human Rights and the International Covenant on Civil and Political Rights (ICCPR).Beyond the ICCPR General Comment No.16: Article 17 (…
Content Type: Impact Case Study
What happenedStrong and effective data protection law is a necessary safeguard against industry and governments' quest to exploit our data. A once-in-a-generation moment arose to reform the global standard on data protection law when the European Union decided to create a new legal regime. PI had to fight to ensure it wasn't a moment where governments and industry would collude to reduce protections.In January 2012, the European Commission published a proposal to comprehensively reform the…
Content Type: Long Read
TO TAKE PART IN OUR CAMPAIGN, RIGHT CLICK ON THE PICTURES BELOW, SAVE THEM, AND SHARE THEM ON SOCIAL MEDIA TAGGED #SPYPOLICE
Have you ever been to a peaceful protest, demo or march? Did you assume that the police would only be identifying 'troublemakers'? How would you feel if just by turning up at a peaceful protest, the police automatically identified you, without your consent or knowledge, and stored personal information about you (including photographs of your face) in a secret database?…
Content Type: Call to Action
Support our campaign against unregulated police surveillance technology by sharing our #spypolice posters on social media
Take part in our #spypolice campaign!
Content Type: News & Analysis
Ask people around you if they live in a smart city, and more likely than not they will answer that they don’t. I can tell you that because I have tried.
When giving talks about this very topic in cities like Berlin, The Hague and Stockholm, I always ask this question at the start. The rough ratio I tend to get is that: 15 per cent hesitantly raise their hand to say they do, 60 per cent don’t, 20 per cent just look confused and 5 per cent are not listening.
And yet most people who live in cities…
Content Type: News & Analysis
Following an extensive campaign by Privacy International and our network of groups in the United Kingdom, the UK Government has decided to abandon its current plans for data sharing legislation.
The government has announced that it will immediately abandon clause 152 of the Coroners and Justice Bill, following on from an open letter that Privacy International sent to the Justice Secretary earlier this week.
As the Sunday Telegraph observed, the eloquence of the letter together with the…