Advanced Search
Content Type: Long Read
On the basis of a year of legal research by PI as well as documents obtained by other civil society organisations, and evidence provided by legal representatives fighting these automated systems on behalf of their clients, on the 18th August 2025, we issued a formal complaint to the UK Information Commissioner (ICO) regarding the UK Home Office’s use of two ‘automated recommendation-making tools’ (ARMTs), the Identify and Prioritise Immigration Cases tool (IPIC) and the Electronic Monitoring…
Content Type: Long Read
In June 2025, a team of researchers exposed how Meta and Yandex abused Android and browser-specific tools to track users outside of their application and collect associated data. The technique used to achieve this was truly innovative, and akin to malware behaviour. It exploited protocols to break the isolation between apps and browser, a fundamental security concept meant to protect users. This allowed these companies to tie the browsing history of individuals with their accounts on the…
Content Type: News & Analysis
Layla looks at her calendar on her phone. She’s in charge of planning her book club’s monthly meeting. After thinking for a second, she summons her AI assistant: “Hey Assistant, can you book me a table at that tapas restaurant I read about last week, and invite everyone from the book club? The restaurant should be in my browsing history. Let me know if the journey is more than 1-hour for anyone”. As the assistant compiles a response, she wonders if anyone else will hear this.Technology has made…
Content Type: Long Read
“Hey [enter AI assistant name here], can you book me a table at the nearest good tapas restaurant next week, and invite everyone from the book club?” Billions of dollars are invested in companies to deliver on this. While this is a dream that their marketing departments want to sell, this is a potential nightmare in the making.Major tech companies have all announced flavours of such assistants: Amazon’s Alexa+, Google’s Gemini inspired by Project Astra, Microsoft’s Copilot AI companion and…
Content Type: News & Analysis
Is the AI hype fading? Consumer products with AI assistant are disappointing across the board, Tech CEOs are struggling to give examples of use cases to justify spending billions into Graphics Processing Units (GPUs) and models training. Meanwhile, data protection concerns are still a far cry from having been addressed.
Yet, the believers remain. OpenAI's presentation of ChatGPT was reminiscent of the movie Her (with Scarlett Johannsen's voice even being replicated a la the movie), Google…
Content Type: Advocacy
BackgroundThe Snowden revelations and subsequent litigation have repeatedly identified unlawful state surveillance by UK agencies. In response, the UK Parliament passed the highly controversial Investigatory Powers Act 2016 (IPA), which authorised massive, suspicionless surveillance on a scale never seen before, with insufficient safeguards or independent oversight.Privacy International led legal challenges to this mass surveillance regime both before and after the Act became law. The Act…
Content Type: Examples
Just as China uses technology system called "Integrated Joint Operations Platform" to control and surveil the persecuted population of Uighurs while restricting their movement and branding dissent as "terrorism", the Israeli military is using facial recognition and a massive database of personal information to control millions of Palestinians in the occupied West Bank. In November 2021, NSO Group's Pegasus spyware was found on the phones of six Palestinian human rights activists, three of whom…
Content Type: Examples
The Israeli minister of public security has joined police in denying claims in an article in Calcalist that the country's police force have used NSO Group's Pegasus software to spy on the phones of people who led protests against former premier Benjamin Netanyahu. Calcalist reported that the surveillance was carried out without court supervision or oversight of how the data was used. The daily Haaretz newspaper also reported that it had seen a 2013 invoice in which NSO billed police @@2.7…
Content Type: Video
<br />
Links
Read more about the ICO's provisional decision
Support our work
You can find out more about Clearview by listening to our podcast: The end of privacy? The spread of facial recognition
Content Type: Press release
Amnesty International, Privacy International and The Centre for Research on Multinational Corporations (SOMO) have published a report uncovering NSO Group’s entire corporate structure, tracking the global money trail of both public and private investment into the lucrative spyware company.
Amnesty International and other rights groups have documented dozens of cases of NSO Group’s products being used by repressive governments across the world to put activists, journalists, and opposition…
Content Type: Report
In this briefing, Amnesty International, PI and The Centre for Research on Multinational Corporations (SOMO) discuss the corporate structure of NSO group, one of the surveillance industry's well-known participants. The lack of transparency around NSO Group’s corporate structure and the lack of information about the relevant jurisdictions within which it operates are significant barriers in seeking prevention of, and accountability for, human rights violations reportedly linked to NSO Group’s…
Content Type: Explainer
What is hacking?
Hacking refers to finding vulnerabilities in electronic systems, either to report and repair them, or to exploit them.
Hacking can help to identify and fix security flaws in devices, networks and services that millions of people may use. But it can also be used to access our devices, collect information about us, and manipulate us and our devices in other ways.
Hacking comprises a range of ever-evolving techniques. It can be done remotely, but it can also include physical…
Content Type: News & Analysis
Unwanted Witness’ research into Safeboda highlighted the company’s failure to comply with some of the law's core data protection principles, with a number of implications for the exercise of data subject rights. The enforcement action against Safeboda by National Information Technology Authority, Uganda (NITA-U) requires the company to make fundamental changes to how they handle people's personal data in order to comply with the Data Protection and Privacy Act, 2019.
This first landmark…
Content Type: Long Read
On 8 January 2021, the UK High Court issued a judgment in the case of Privacy International v. Investigatory Powers Tribunal. The Secretary of State for Foreign and Commonwealth Affairs and Government Communication Headquarters (GCHQ) appeared as interested parties to the case.
After our initial reaction, below we answer some of the main questions relating to the case.
NOTE: This post reflects our initial reaction to the judgment and may be updated.
What’s the ruling all about?
In…
Content Type: Frequently Asked Questions
On 8 January 2021, the UK High Court issued a judgment in the case of Privacy International v. Investigatory Powers Tribunal. The Secretary of State for Foreign and Commonwealth Affairs and Government Communication Headquarters (GCHQ) appeared as interested parties to the case.
After our initial reaction, below we answer some of the main questions relating to the case.
NOTE: This post reflects our initial reaction to the judgment and may be updated.
Content Type: Long Read
In 2019, we exposed the practices of five menstruation apps that were sharing your most intimate data with Facebook and other third parties. We were pleased to see that upon the publication of our research some of them decided to change their practices. But we always knew the road to effective openness, transparency, informed consent and data minimisation would be a long one when it comes to apps, which for the most part make profit from our menstrual cycle and even sometimes one’s desire to…
Content Type: Frequently Asked Questions
On 27 October 2020, the UK Information Commissioner's Office (ICO) issued a report into three credit reference agencies (CRAs) - Experian, Equifax and TransUnion - which also operate as data brokers for direct marketing purposes.
After our initial reaction, below we answer some of the main questions regarding this report.
Content Type: Explainer
At first glance, infrared temperature checks would appear to provide much-needed reassurance for people concerned about their own health, as well as that of loved ones and colleagues, as the lockdown is lifted. More people are beginning to travel, and are re-entering offices, airports, and other contained public and private spaces. Thermal imaging cameras are presented as an effective way to detect if someone has one of the symptoms of the coronavirus - a temperature.
However, there is little…
Content Type: News & Analysis
New technologies continue to present great risks and opportunities for any users but for some communities the implications and harms can have severe consequences and one of the sectors facing increasing challenges to keep innovating whilst protecting themselves and the people they serve is the humanitarian sector.
Over the course of engagement with the humanitarian sector, one of our key observations has been how risk assessments undertaken in the sector omitted to integrate a hollistic…
Content Type: News & Analysis
In September 2019, PI published the report Your Mental Health for Sale. Our investigation looked into popular mental health websites and their data sharing practices.
Our findings suggest that, at the time of the research, most websites we looked at were using third party tracking for advertising purposes, sometimes relying on programmatic advertising technologies such as Real Time Bidding (RTB), sharing personal data with potentially thousands of actors. Some websites were also found sharing…
Content Type: Call to Action
You might have read our investigation into advertisers who upload your data on Facebook and found out some companies doing the same to you. Well, you can join us and hold them accountable by sending your own Data Subject Access Request (DSAR)!Before you get started we suggest you read our FAQ and take a look at our 7+1 tips to make the most out of your DSAR before and after.To do so you simply need to copy the message bellow and send it to the companies that uploaded your data despite…
Content Type: Report
Back in October 2019, PI started investigating advertisers who uploaded personal data to Facebook for targeted advertising purposes. We decided to take a look at "Advertisers Who Uploaded a Contact List With Your Information", a set of information that Facebook provides to users about advertisers who upload files containing their personal data (including unique identifier such as phone numbers, emails etc...). Looking at the limited and often inaccurate information provided by Facebook through…
Content Type: Explainer
In a scramble to track, and thereby stem the flow of, new cases of COVID-19, governments around the world are rushing to track the locations of their populace.
In this third installment of our Covid-19 tracking technology primers, we look at Satellite Navigation technology. In Part 1 of our mini-series on we discussed apps that use Bluetooth for proximity tracking. Telecommunications operators ('telcos'), which we discussed in Part 2, are also handing over customer data, showing the cell towers…
Content Type: Long Read
This week saw the release of a coronavirus tracking app within the United Kingdom, initially to be trialled in the Isle of Wight. Privacy International has been following this closely, along with other ‘track and trace’ apps like those seen in over 30 other countries.
The UK’s app is no different. It is a small part of a public health response to this pandemic. As with all the other apps, it is vital that it be integrated with a comprehensive healthcare response, prioritise people, and…
Content Type: Video
You’re a witness or a victim or a suspect of a crime; or even just travelling going on holiday. Officials demand your phone, then disappear with it. What happened to your phone? What happened to your data? What will happen to you?
We all generate vast amounts of data using our mobile phones - more than most of us are aware of - and that data has become increasingly attractive to law enforcement agencies around the world, enabled by ‘extraction technologies’ supplied by companies like…
Content Type: Long Read
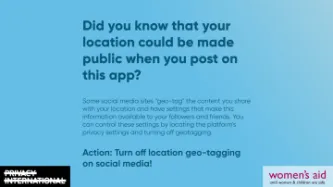
Valentine’s Day is traditionally a day to celebrate relationships, but many relationships that begin romantically can quickly become controlling, with partners reading emails, checking texts and locations of social media posts. This can be just the beginning.
Today, Friday 14th February, Privacy International and Women’s Aid are launching a series of digital social media cards giving women practical information on how to help stay safe digitally from control and abuse.
Did you know…
Content Type: Case Study
In early May 2019, it was revealed that a spyware, exploiting a vulnerability in Facebook’s WhatsApp messaging app, had been installed onto Android and iOS phones. The spyware could be used to turn on the camera and mic of the targeted phones and collect emails, messages, and location data. Citizen Lab, the organization that discovered the vulnerability, said that the spyware was being used to target journalists and human rights advocates in different countries around the world. The spyware…
Content Type: News & Analysis
On 24 October 2019, the Swedish government submitted a new draft proposal to give its law enforcement broad hacking powers. On 18 November 2019, the Legal Council (“Lagråd”), an advisory body assessing the constitutionality of laws, approved the draft proposal.
Privacy International believes that even where governments conduct hacking in connection with legitimate activities, such as gathering evidence in a criminal investigation, they may struggle to demonstrate that hacking as…
Content Type: News & Analysis
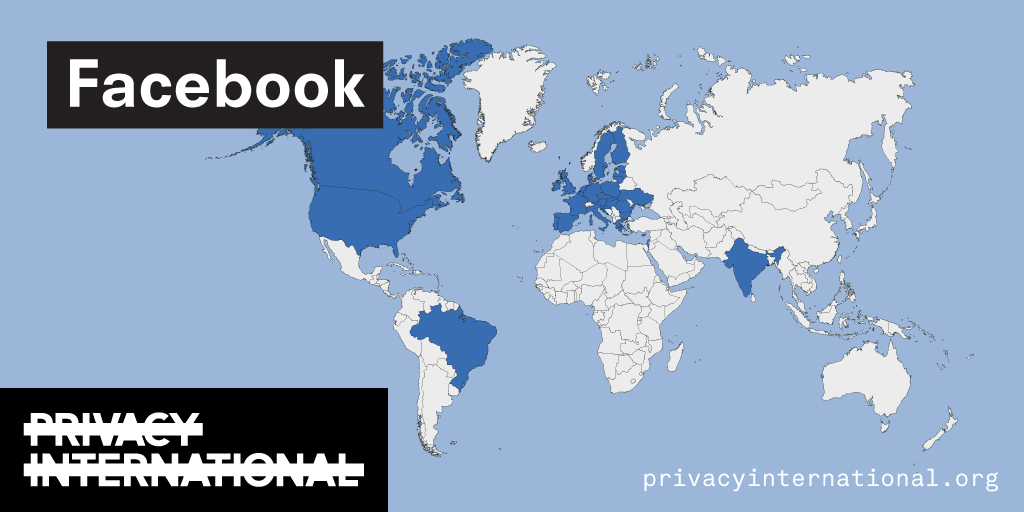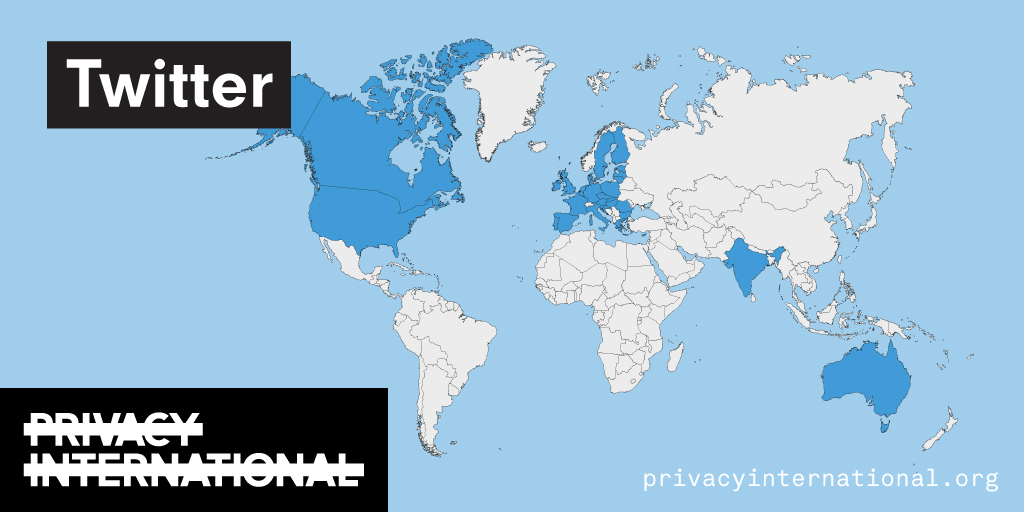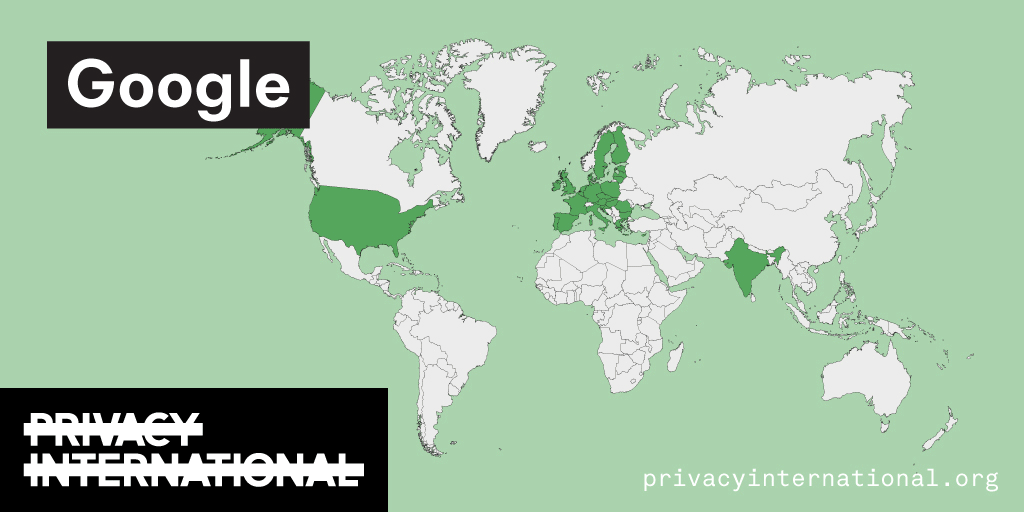
Yesterday, we found out that Google has been reported to collect health data records as part of a project it has named “Project Nightingale”. In a partnership with Ascension, Google has purportedly been amassing data for about a year on patients in 21 US states in the form of lab results, doctor diagnoses and hospitalization records, among other categories, which amount to a complete health history, including patient names and dates of birth.
This comes just days after the news of Google'…