Advanced Search
Content Type: News & Analysis
Yesterday the Investigatory Powers Tribunal announced next steps in Apple’s and PI’s challenges to the purported UK order undermining iCloud’s security.The Tribunal declared that it will aim to hear much of Apple’s case, as well as PI and our co-claimants’, in public based on assumed facts. The Tribunal will convene a seven day hearing to be scheduled in early 2026. Its aim will be to hear Apple’s case and PI’s case during those seven days.This ‘case management order’ follows submissions from…
Content Type: Press release
FOR IMMEDIATE RELEASELONDON - 7 April 2025The Investigatory Powers Tribunal (IPT) has confirmed it will hear Privacy International, Liberty and two individuals’ challenge to the legality of the Home Secretary’s decision to use her powers to secretly force Apple to allegedly give the UK Government access to users’ secured data stored on iCloud. The challenge will also cover the legality of the Government issuing these types of notices at all. Privacy International and Liberty,…
Content Type: News & Analysis
On 11 March 2025, The Atlantic journalist, Jeffrey Goldberg was added to a Signal chat where senior US Government officials were discussing the United States’ military strikes in Yemen.This happened to Goldberg as an accident. Yet, security services around the world have pushed for this to be part of their clandestine surveillance operations: the so-called “Ghost Protocol”.Governments have been trying to gain access to private online conversations since private online conversations have existed…
Content Type: Long Read
On 13 March 2025, we filed a complaint against the UK government challenging their use of dangerous, disproportionate and intrusive surveillance powers to undermine the privacy and security of people all over the world. Here, we answer some key questions about the case and the recent events that led to this development.Note: This post was last updated on 13 March 2025.What’s the fuss about?A month ago, it was reported that the UK government demanded Apple Inc – maker of the iPhone, iPads, Macs…
Content Type: Explainer
Imagine this: a power that secretly orders someone anywhere in the world to abide and the receiver can’t tell anyone, can’t even publicly say if they disagree, and can’t really question the power in open court because the secret order is, well, secret. Oh and that power affects billions of people’s security and their data. And despite being affected, we too can’t question the secret order.In this piece we will outline what’s ridiculous, the absurd, and the downright disturbing about what’s…
Content Type: News & Analysis
Edit: 13 March 2025 - You can find more about what happened next on our case pageOn February 21st, Apple disabled their ‘advanced data protection’ service for UK customers. That means no-one in Great Britain can now enable a powerful security safeguard that people who use Apple devices everywhere else on the planet can: user controlled end-to-end encryption of stored data.This is likely in response to a disturbing secret government power. Well, that’s what we think happened. We can’t know for…
Content Type: Press release
Privacy International (PI)FOR IMMEDIATE RELEASEUnited Kingdom goes after Apple's encrypted dataThe United Kingdom has used its investigatory powers to force disclosure of private data held by Apple Inc."The United Kingdom's unprecedented attack on individuals' private data around the globe is disproportionate and unnecessary.""This is a fight the UK should not have picked. The reported details suggest the UK is seeking the ability to access encrypted information Apple users store on iCloud, no…
Content Type: Advocacy
We responded to the Home Office consultation on codes of practices under the Investigatory Powers (Amendment) Act 2024 (IPAA). Our response focused on (1) the draft codes relating to bulk personal datasets with low or no reasonable expection of privacy, (2) third-party bulk personal datasets and (3) the notices regime. You can download our full response with its 23 recommendations for reform at the bottom of this page.'Low Privacy' Bulk Personal DatasetsThe IPAA introduces a new concept of…
Content Type: Video
Links - Read more about PI's work on encryption- Matt Blaze and crypto.com; you can now find Matt at mattblaze.org - More about ITAR and the export of cryptography- More about France's ban on encryption ending in this 1999 article from the Register- More about the Data Encryption Standard - Find out more about the Clipper Chip or take a look at this NY Times article from 1994 (paywalled)- Matt Blaze's flaw in the Clipper Chip- NSA Data Center and NSA holding data- An…
Content Type: Video
The case dealt with a Russian law obliging telecommunications service providers to indiscriminately retain content and communications data for certain time periods, as well as a 2017 disclosure order by the Russian Federal Security Service requiring Telegram Messenger company to disclose technical information which would facilitate “the decoding of communications”.Links:PI case pageECtHR judgment in the Podchasov casePI's work on encryptionPI's report on End-to-End Encryption (E2EE)More…
Content Type: Video
LinksFind out more about encryption:Computerphile on YouTube is a computer science professor with a range of useful and accessible videos on encryptionCloudflare have a helpful learning centre including this article on how encryption works and why cloudflare use Lava lamps to generate keysThis is a helpful article on Diffie-Hellman including a diagram of the colours demonstration, which Ed discusses during the podcastThis article is great for learning more about hashingAnd if you're interested…
Content Type: Advocacy
BackgroundThe Snowden revelations and subsequent litigation have repeatedly identified unlawful state surveillance by UK agencies. In response, the UK Parliament passed the highly controversial Investigatory Powers Act 2016 (IPA), which authorised massive, suspicionless surveillance on a scale never seen before, with insufficient safeguards or independent oversight.Privacy International led legal challenges to this mass surveillance regime both before and after the Act became law. The Act…
Content Type: Long Read
In June 2023, the UK government announced its proposal to expand its surveillance powers by, among others, forcing communications operators to undermine encryption or abstain from providing security software updates globally. Building on our response to the government’s plans, this piece explains why what they want to do puts every one of us at risk.
Why your trust (to technologies you use) matters
Surveillance and privacy are complex concepts to grasp – it’s part of the appeal to us at PI.…
Content Type: Advocacy
We are responding to the UK Government's consultation to expand its powers around Technical Capabilities Notices and National Security Notices.
Background
Following Edward Snowden's revelations about the illegal and expansive secret powers of the US and UK intelligence agencies, the UK Government took the opportunity to, rather than reflect on what powers are proportionate in the modern era, to expand its arsenal of surveillance powers.
One of the powers it added was the ability to issue…
Content Type: Long Read
On 18th January, it was announced that end-to-end encrypted iCloud services, Advanced Data Protection, would be offered to Apple users globally.The offer of such level of security globally, while overdue, is a key step to ensuring trust and confidence in today’s world. There are too many threats to our data and our rights. Twelve years ago, we called on Apple to encrypt iCloud storage for users all around the world.Why this is importantWhile privacy and security is often portrayed as opposite…
Content Type: Report
End-to-end encryption (E2EE) contributes significantly to security and privacy. For that reason, PI has long been in favour of the deployment of robust E2EE.Encryption is a way of securing digital communications using mathematical algorithms that protect the content of a communication while in transmission or storage. It has become essential to our modern digital communications, from personal emails to bank transactions. End-to-end encryption is a form of encryption that is even more private.…
Content Type: News & Analysis
Privacy International welcomes the judgment of the European Court of Human Rights in Catt v the United Kingdom.The Court found that the UK violated the right to privacy (Article 8 of the European Convention on Human Rights) of Mr John Catt, a peace movement activist, who despite having never being convicted of any offence, had his name and other personal data included in a police database known as the “Extremism Database”. The Court found problematic "the variety of definitions of…
Content Type: Long Read
This piece was written by Ashley Gorski, who is an attorney at the American Civil Liberties Union, and PI legal officer Scarlet Kim and originally appeared in The Guardian here.
In recent weeks, the Hollywood film about Edward Snowden and the movement to pardon the NSA whistleblower have renewed worldwide attention on the scope and substance of government surveillance programs. In the United States, however, the debate has often been a narrow one, focused on the…
Content Type: Long Read
This week, Privacy International, together with nine other international human rights NGOs, filed submissions with the European Court of Human Rights. Our case challenges the UK government’s bulk interception of internet traffic transiting fiber optic cables landing in the UK and its access to information similarly intercepted in bulk by the US government, which were revealed by the Snowden disclosures. To accompany our filing, we have produced two infographics to illustrate the…
Content Type: Long Read
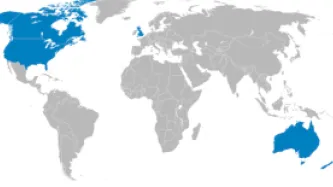
Few revelations have been been as troubling for the right to privacy as uncovering the scope of the Five Eyes alliance. The intelligence club made up of Australia, Canada, New Zealand, the United Kingdom and the United States has integrated its collection efforts, staff, bases, and analysis programs. Yet the legal rulebook governing how the agencies ensure the most comprehensive joint surveillance effort in the history of mankind remains secret.
The little that is known suggests a…
Content Type: Long Read
As Privacy International celebrates Friday's victory against Britain’s security services - the first such victory this century - we cannot help but feel the success is bittersweet.
After all, we may have convinced the Investigatory Powers Tribunal that GCHQ was acting unlawfully in accessing NSA databases filled with billions of emails and messages, but with a few technical adjustments the intelligence services have managed to insure themselves against any further challenge, at least in…
Content Type: Long Read
Many people imagine intelligence sharing to be a practice whereby men in trench coats silently slide manilla envelopes containing anonymous tip-offs or intelligence reports marked TOP SECRET across tables in smoke-filled rooms.
While such practices certainly exist, they represent only a tiny slice of intelligence sharing activities, and are vastly overshadowed by the massive exchange of bulk unanlysed (raw) intelligence data that takes place between the UK and its Five Eyes allies.…
Content Type: News & Analysis
Between 15th-19th of September, in the week leading up the first year aniversary of the 13 Necessary and Proportionate Principles, Privacy International and the coalition behind the 13 Principles will be conducting a Week of Action explaining some of the key guiding principles for surveillance law reform. Every day, we'll take on a different part of the principles, exploring what’s at stake and what we need to do to bring intelligence agencies and the police back under the rule of law. You can…
Content Type: Long Read
Bad analogies about surveillance technology pervade newspaper reports, politicians’ speeches, and legal arguments. While it’s natural to want simple explanations to understand complex technology, it does us a disservice when governments, the media, or the courts mislead us through analogies that are inadequate. It is even worse if these analogies are used as a basis for policy change.
Privacy International’s legal challenge against GCHQ’s mass surveillance rests…
Content Type: Long Read
The recent revelations, made possible by NSA-whistleblower Edward Snowden, of the reach and scope of global surveillance practices have prompted a fundamental re- examination of the role of intelligence services in conducting coordinated cross-border surveillance.
The Five Eyes alliance of States – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the…
Content Type: Press release
Privacy International today has filed a complaint with the Australian Inspector-General of Intelligence Security, calling for an immediate investigation into deeply troubling reports that the Australian intelligence services offered to violate the privacy rights of millions of citizens by handing over bulk metadata to its Five Eye partners.
According to the leaked Five Eyes memo published in the Guardian on 2 December, the Australian Signals Directorate, during a meeting…
Content Type: Report
The recent revelations, made possible by NSA-whistleblower Edward Snowden, of the reach and scope of global surveillance practices have prompted a fundamental re-examination of the role of intelligence services in conducting coordinated cross-border surveillance.
The Five Eyes alliance of States – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the…