Advanced Search
Content Type: Long Read
Privacy and security are both essential to protecting individuals, including their autonomy and dignity. Undermining privacy undermines the security of individuals, their devices and the broader infrastructure. People need privacy to freely secure themselves, their information, and fully enjoy other rights. However, a growing number of governments around the world are embracing hacking to facilitate their surveillance activities.
As a form of government surveillance, hacking presents…
Content Type: News & Analysis
The Watson/Tele2 decision of the CJEU concerned section 1 and 2 of DRIPA and the Data Retention Regulations 2014. This contained the legislative scheme concerning the power of the Secretary of State to require communications service providers to retain communications data. Part 3 of the Counter-Terrorism and Security Act 2015 amended DRIPA so that an additional category of data - that necessary to resolve Internet Protocol addresses - could be included in a requirement to retain…
Content Type: Advocacy
RESPONSE OF PRIVACY INTERNATIONAL TO THE CONSULTATION ON THE GOVERNMENT’S PROPOSED RESPONSE TO THE RULING OF THE COURT OF JUSTICE OF THE EUROPEAN UNION ON 21 DECEMBER 2016 REGARDING THE RETENTION OF COMMUNICATIONS DATA
[Full response below]
Introduction
The consultation is in response to the judgment in Tele2 Sverige AB v Post-och telestyrelsen (Case-203/15) and R (Watson) v Secretary of State for the Home Department (Case C-698/15) [“Watson judgment”].
The case concerned…
Content Type: Explainer
In 2000, the Government told Parliament that the Regulation of Investigatory Powers Act 2000 (RIPA) was the total extent of surveillance powers that were needed. However, within weeks of RIPA receiving Royal Assent, a report from UK law enforcement was leaked, stating that the power the Government truly wanted was companies to retain communications data on all their users.
Immediately after 9/11 as governments around the world over-reached with new pieces of…
Content Type: News & Analysis
Federal law enforcement is deploying powerful computer hacking tools to conduct domestic criminal and immigration investigations.
By Alex Betschen, Student Attorney, Civil Liberties & Transparency Clinic, University at Buffalo School of Law
Hacking by the government raises grave privacy concerns, creating surveillance possibilities that were previously the stuff of science fiction. It also poses a security risk, because hacking takes advantage of unpatched vulnerabilities in our…
Content Type: Press release
FOR IMMEDIATE RELEASE
December 21, 2018
CONTACTS:
Alex Betschen, Civil Liberties & Transparency Clinic, [email protected], 716–531–6649
Colton Kells, Civil Liberties & Transparency Clinic, [email protected], 585–766–5119
Abdullah Hasan, ACLU, [email protected], 646–905–8879
NEW YORK — Privacy International, the American Civil Liberties Union, and the Civil Liberties & Transparency Clinic of the University at Buffalo School of Law filed a lawsuit today…
Content Type: News & Analysis
This piece was originally published on Just Security.
Ten years ago, an FBI official impersonated an Associated Press reporter to lure and track a teenager suspected of sending in prank bomb threats to his school. To find him, the FBI agent, posing as a reporter, sent the teenager links to a supposed story he was working on, but the links were infested with malware that once clicked on quickly exposed the teen’s location. More recently, the FBI has seized and modified websites so…
Content Type: Advocacy
This report sheds light on the current state of affairs in data retention regulation across the EU post the Tele-2/Watson judgment. Privacy International has consulted with digital rights NGOs and industry from across the European Union to survey 21 national jurisdictions (Austria, Belgium, Bulgaria, Croatia, Cyprus, Czech Republic, France, Germany, Hungary, Ireland, Italy, Luxembourg, the Netherlands, Poland, Portugal, Romania, Slovakia, Slovenia, Spain, Sweden, and the United…
Content Type: Long Read
This piece was orignally published in Slate in February 2017
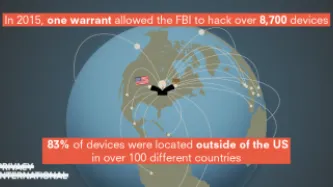
In 2015, the FBI obtained a warrant to hack the devices of every visitor to a child pornography website. On the basis of this single warrant, the FBI ultimately hacked more than 8,700 computers, resulting in a wave of federal prosecutions. The vast majority of these devices—over 83 percent—were located outside the United States, in more than 100 different countries. Now, we are in the midst of the first cases…
Content Type: Long Read
This piece was written by Ashley Gorski, who is an attorney at the American Civil Liberties Union, and PI legal officer Scarlet Kim and originally appeared in The Guardian here.
In recent weeks, the Hollywood film about Edward Snowden and the movement to pardon the NSA whistleblower have renewed worldwide attention on the scope and substance of government surveillance programs. In the United States, however, the debate has often been a narrow one, focused on the…
Content Type: Long Read
This week, Privacy International, together with nine other international human rights NGOs, filed submissions with the European Court of Human Rights. Our case challenges the UK government’s bulk interception of internet traffic transiting fiber optic cables landing in the UK and its access to information similarly intercepted in bulk by the US government, which were revealed by the Snowden disclosures. To accompany our filing, we have produced two infographics to illustrate the…
Content Type: Press release
Privacy International General Counsel Caroline Wilson Palow said
"Today's opinion issued by the Advocate General of the European Court of Justice (ECJ) is a serious blow to the UK's Investigatory Powers Bill (IPBill). It, hopefully, presages a strong judgment from the Court itself.
The bulk powers - what we would call mass surveillance powers - embedded throughout the IPBill go far beyond tackling serious crime. They would give a range of public bodies, not just the Police and…
Content Type: Long Read
This piece originally appeared here.
On both sides of the Atlantic, we are witnessing the dramatic expansion of government hacking powers. In the United States, a proposed amendment to Rule 41 of the Federal Rules of Criminal Procedure would permit the government to obtain a warrant, in certain circumstances, to hack unspecified numbers of electronic devices anywhere in the world. Meanwhile, across the pond, the British Parliament is currently debating the Investigatory…
Content Type: Press release
Tomorrow, Privacy International and Open Rights Group will argue that wholesale and indiscriminate retention of our personal data is not permissible. The case, brought by MPs Tom Watson and David Davis against the Data Retention and Investigatory Powers Act 2014 (DRIPA), and in which PI intervened, will be heard in the European Court of Justice (CJEU) on 12 April. It has the potential to send shockwaves through the Investigatory Powers Bill, the controversial…
Content Type: Long Read
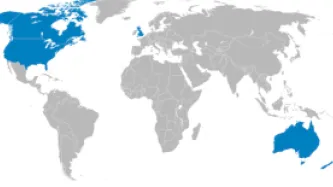
Few revelations have been been as troubling for the right to privacy as uncovering the scope of the Five Eyes alliance. The intelligence club made up of Australia, Canada, New Zealand, the United Kingdom and the United States has integrated its collection efforts, staff, bases, and analysis programs. Yet the legal rulebook governing how the agencies ensure the most comprehensive joint surveillance effort in the history of mankind remains secret.
The little that is known suggests a…
Content Type: Long Read
Many people imagine intelligence sharing to be a practice whereby men in trench coats silently slide manilla envelopes containing anonymous tip-offs or intelligence reports marked TOP SECRET across tables in smoke-filled rooms.
While such practices certainly exist, they represent only a tiny slice of intelligence sharing activities, and are vastly overshadowed by the massive exchange of bulk unanlysed (raw) intelligence data that takes place between the UK and its Five Eyes allies.…