Search
Content type: Long Read
The Law Enforcement Data Service (LEDS) is a unified, common interface to a new mega-database currently being developed by the Home Office National Law Enforcement Data Programme (NLEDP).
It might not sound like the most exciting thing in the world (and it isn't!) - but it will have a profound impact on policing and surveillance in the UK for generations.
We believe that the development of the programme poses a threat to privacy and other rights and must be subjected to strong oversight,…
Content type: Press release
Today, the ICO has issued a long-awaited and critical report on Police practices regarding extraction of data from people's phones, including phones belonging to the victims of crime.
The report highlights numerous risks and failures by the police in terms of data protection and privacy rights. The report comes as a result of PI’s complaint, dating back to 2018, where we outlined our concerns about this intrusive practice, which involves extraction of data from devices of victims, witnesses…
Content type: Long Read
In December 2019, the Information Rights Tribunal issued two disappointing decisions refusing appeals brought by Privacy International (PI) against the UK Information Commissioner.
The appeals related to decisions by the Information Commissioner (IC), who is responsible for the UK’s Freedom of Information regime, concerning responses by the Police and Crime Commissioner for Warwickshire and the Commissioner of Police for the Metropolis (The Metropolitan Police) to PI’s freedom of information…
Content type: News & Analysis
Yesterday, Amazon announced that they will be putting a one-year suspension on sales of its facial recognition software Rekognition to law enforcement. While Amazon’s move should be welcomed as a step towards sanctioning company opportunism at the expense of our fundamental freedoms, there is still a lot to be done.
The announcement speaks of just a one-year ban. What is Amazon exactly expecting to change within that one year? Is one year enough to make the technology to not discriminate…
Content type: Examples
After police in Bellevue, WA were inundated with calls from local residents reporting suspected violations of the state's week-old stay-at-home order, they asked the public to use the MyBellevue app instead, to keep 911 lines open for emergencies. The police added that they have no plans to charge or arrest violators, but will visit reported hot spots in order to educate the public about the rules. Residents are required to remain at home but there are exceptions for essential industries, trips…
Content type: Examples
Spanish police are using drones to warn people to stay indoors apart from necessary trips after seeing a spike in COVID-19 cases. Human officers control the drones and relay via radio warnings to people to leave public parks and return home.
Source: https://www.businessinsider.com/spanish-police-using-drones-to-ask-people-stay-at-home-2020-3
Writer: Charlie Wood
Publication: BusinessInsider
Content type: Examples
On March 9, SK Telecom began providing South Korea's Gyeongbuk Provincial Police Agency with its Geovision population analysis service and GIRAF platform. The company claims that the combination can analyse mobile geolocation data across the country in real time, create visualisations, and show how many people are in 10x10 metre lattices, enabling police to send officers where they're needed to enforce distancing measures. The company is in talks with the Korean National Police Agency to expand…
Content type: Report
On 12 December 2018 a member of Lancashire Police Department UK told viewers of a Cellebrite webinar that they were using Cellebrite's Cloud Analyser to obtain cloud based 'evidence'. In response to a Freedom of Information request Hampshire Constabulary told Privacy International they were using Cellebrite Cloud Analyser.
They are not alone. In Cellebrite's 2019 Annual Trend Survey, Cellebrite found that law enforcement is increasingly using 'cloud extraction.' But the…
Content type: Examples
Together with Norwegian company Simula the Norwegian Institute of Public Health is developping a voluntary app to track users geolocation and slow the spread of Covid-19. Running in the background, the app will collect GPS and Bluetooth location data and store them on a server for 30 days. If a user is diagnosed with the virus, its location data can be user to trace all the phones that have been in close contact with the person. Authorities will use this data to send an SMS only to those phones…
Content type: Examples
The new Singaporean app, TraceTogether, developed by the Government Technology Agency in collaboration with the Ministry of Health was launched on March 20 after eight weeks of development. The app, which can be downloaded by anyone with a Singapore mobile number and a Bluetooth-enabled smartphone, asks users to turn on Bluetooth and location services, and enable push notifications. The app works by exchanging short-distance Bluetooth signals between phones to detect other users within two…
Content type: Examples
Technology such as Hong Kong's electronic monitoring bracelets, used to ensure that people do not break their mandated quarantine, may appear reasonable during a pandemic, but could be problematic if deployed widely and used to identify those who have joined anti-government protests. The same applies to emergency legislation such as that passed by the UK government granting the government extraordinary new powers to shut down airports and ban gatherings. History provides examples:…
Content type: Examples
Hong Kong is issuing electronic tracker wristbands to people under compulsory home quarantine to ensure they do not go out. The wristbands are accompanied by a mandatory smartphone app that shares their location with the government via messaging platforms such as WeChat and WhatsApp. Upon arriving at the place where they are quarantined, users walk around the corners so the technology can track the space in which they are confined.
Source: https://www.cnbc.com/2020/03/18/hong-kong-uses-…
Content type: Video
You’re a witness or a victim or a suspect of a crime; or even just travelling going on holiday. Officials demand your phone, then disappear with it. What happened to your phone? What happened to your data? What will happen to you?
We all generate vast amounts of data using our mobile phones - more than most of us are aware of - and that data has become increasingly attractive to law enforcement agencies around the world, enabled by ‘extraction technologies’ supplied by companies like…
Content type: Advocacy
In December 2019 Privacy International made submissions to Police Scotland in relation to documents designed to explain to the public how cyber kiosks will work and what information will be given to victims when Police Scotland extract data from their phone.
Police Scotland rely on 'consent' to seize a phone from a victim. We believe the lack of information provided to the individual regarding extraction, examination, retention, deletion, sharing and search parameters undermines that any…
Content type: News & Analysis
In the last few months strong concerns have been raised in the UK about how police use of mobile phone extraction dissuades rape survivors from handing over their devices: according to a Cabinet Office report leaked to the Guardian, almost half of rape victims are dropping out of investigations even when a suspect has been identified. The length of time it takes to conduct extractions (with victims paying bills whilst the phone is with the police) and the volume of data obtained by the…
Content type: Long Read
In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone…
Content type: Report
“...a mobile device is now a huge repository of sensitive data, which could provide a wealth of information about its owner. This has in turn led to the evolution of mobile device forensics, a branch of digital forensics, which deals with retrieving data from a mobile device.”
The situation in Scotland regarding the use of mobile phone extraction has come a long way since the secret trials were exposed. The inquiry by the Justice Sub-Committee, commenced on 10 May 2018, has brought much…
Content type: Examples
In 2018, Brian Hofer, the chair of Oakland's Privacy Advisory Commission, filed suit after police wrongfully stopped him at gunpoint because their automated license plate recognition system, supplied by Vigilant Solutions, indicated that the rental car he was driving had been stolen. The car had in fact been stolen some months earlier, but been recovered. Despite such errors, police claim that the technology has helped reduce crime, identify stolen vehicles, and identify and arrest suspects.…
Content type: Examples
In February 2019 Gemalto announced it would supply the Uganda Police Force with its Cogent Automated Biometric Identification System and LiveScan technology in order to improve crime-solving. LiveScan enables police to capture biometric data alongside mugshots and biographical data. CABIS speeds up the biometric matching process by mapping distinctive characteristics in fingerprints, palm prints, and facial images. The Ugandan police will also pilot Gemalto's Mobile Biometric Identification…
Content type: Examples
VeriPol, a system developed at the UK's Cardiff University, analyses the wording of victim statements in order to help police identify fake reports. By January 2019, VeriPol was in use by Spanish police, who said it helped them identify 64 false reports in one week and was successful in more than 80% of cases. The basic claim is that AI can find patterns that are common to false statements; among the giveaways experts say that false statements are likely to be shorter than genuine ones, focus…
Content type: Examples
In November 2016 the UK Information Commissioner's Office issued an enforcement notice against London's Metropolitan Police, finding that there had been multiple and serious breaches of data protection law in the organisation's use of the Gangs Violence Matrix, which it had operated since 2012. The ICO documented failures of oversight and coherent guidance, and an absence of basic data protection practices such as encryption and agreements covering data sharing. Individuals whose details are…
Content type: Explainer
We look at the recently published report on forensic science in the UK, highlight concerns about police not understanding new tech used to extract data from mobile phones; the risk of making incorrect inferences and the general lack of understanding about the capabilities of these tools.
The delivery of justice depends on the integrity and accuracy of evidence and trust that society has in it. So starts the damning report of the House of Lords Science and Technology Select…
Content type: Long Read
Imagine that every time you want to attend a march, religious event, political meeting, protest, or public rally, you must share deeply personal information with police and intelligence agencies, even when they have no reason to suspect you of wrongdoing.
First, you need to go to the police to register; have your photo taken for a biometric database; share the contacts of your family, friends, and colleagues; disclose your finances, health records, lifestyle choices, relationship status, and…
Content type: News & Analysis
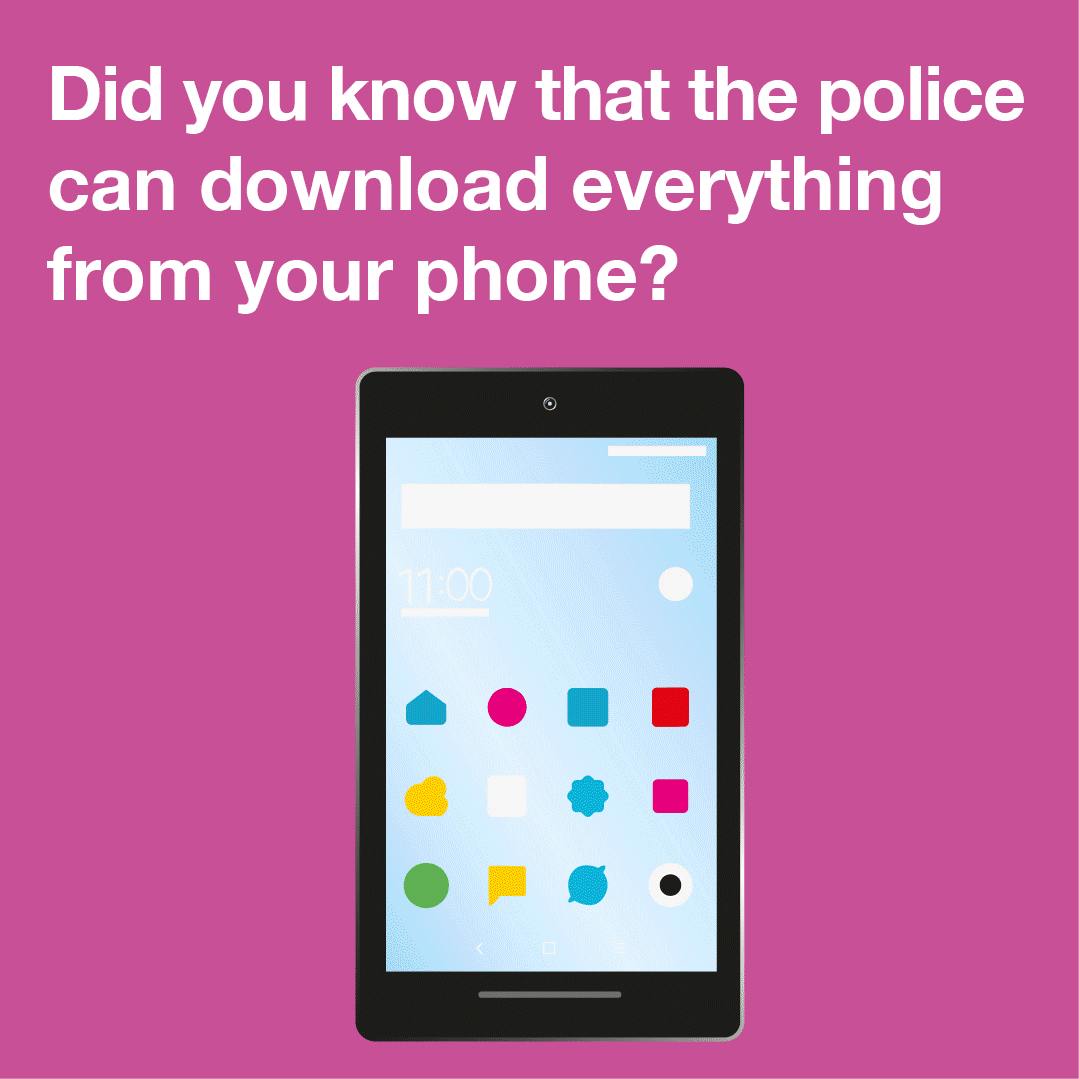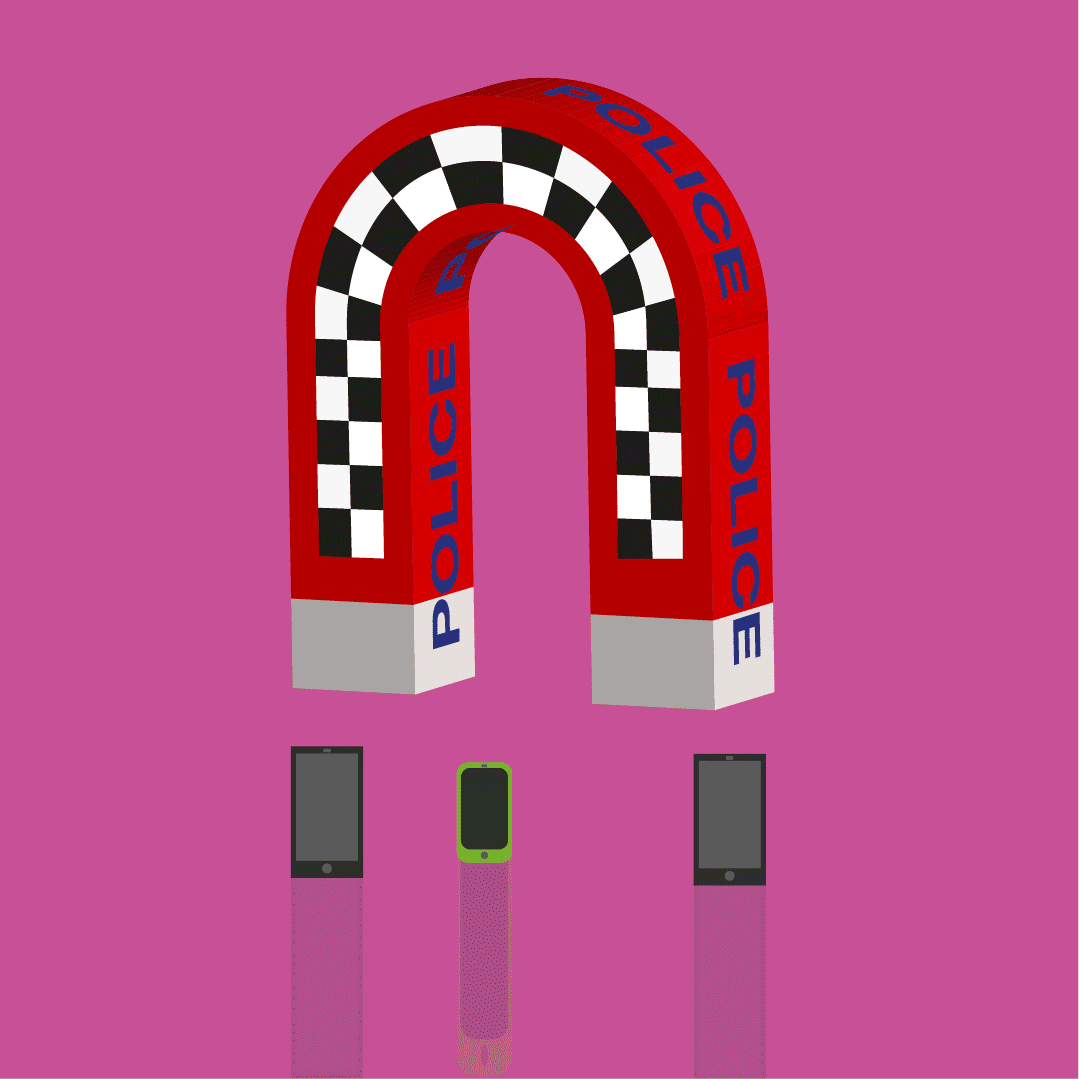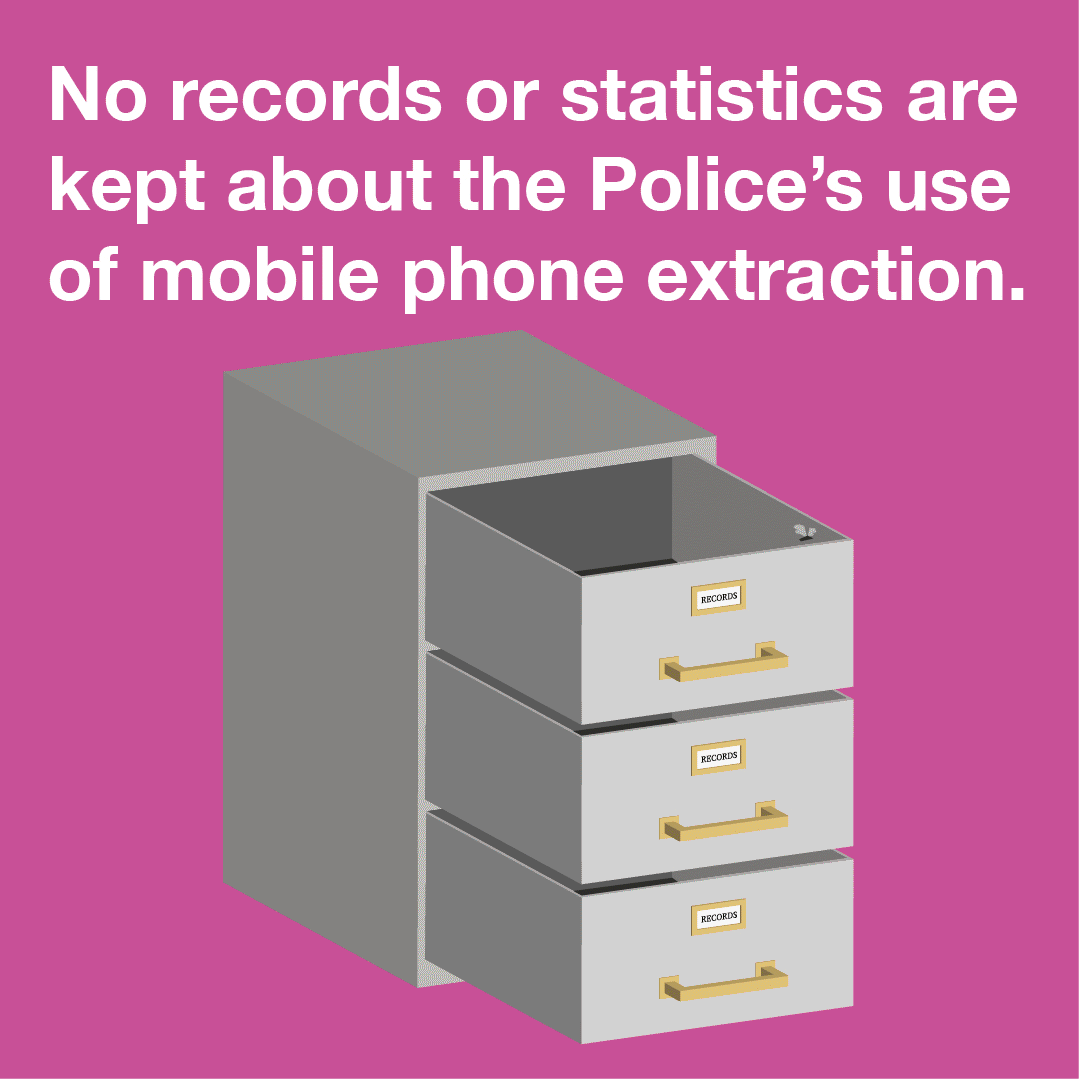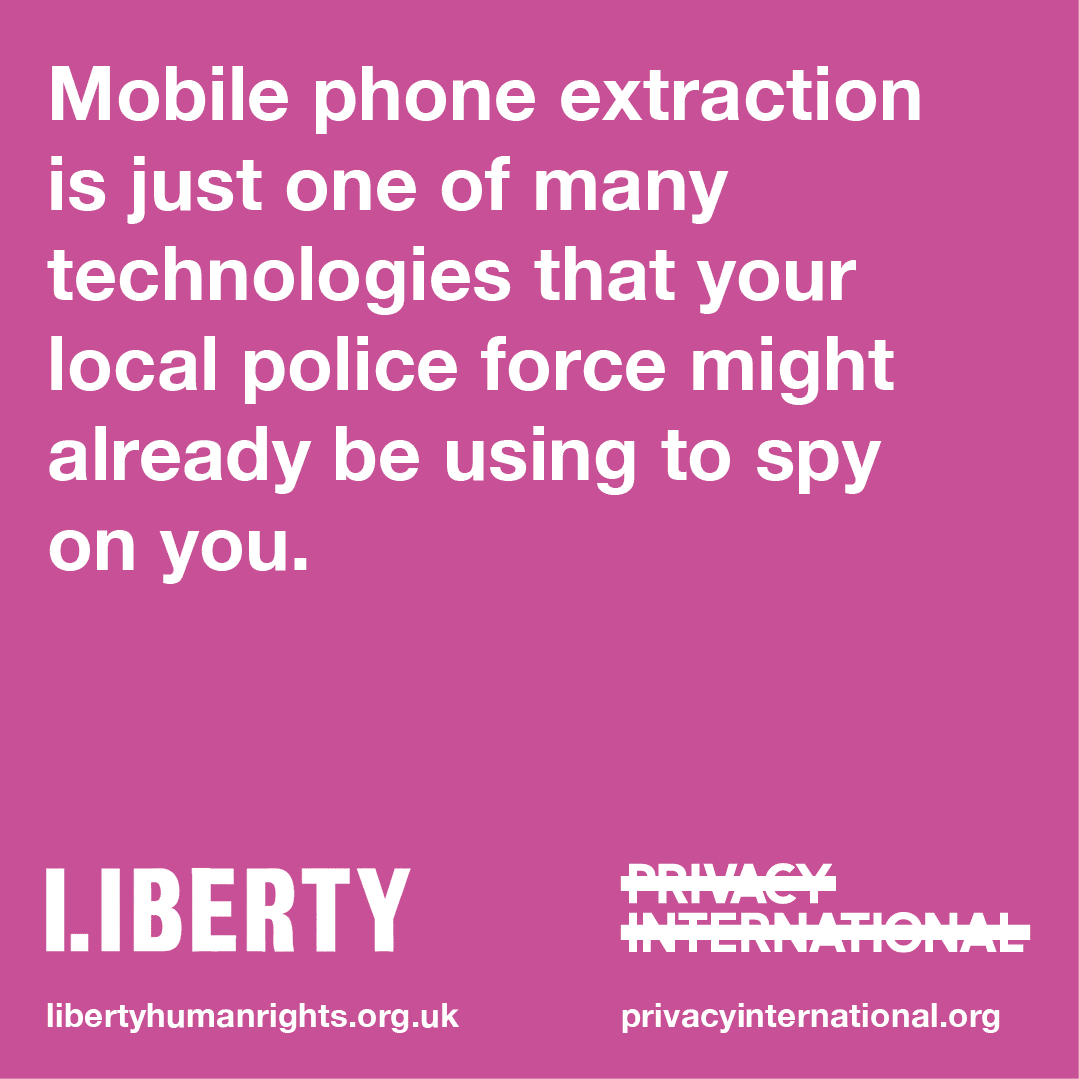
A mobile device is a huge repository of sensitive data, which could provide a wealth of information about its owner and many others with whom the user interacts.
Companies like Cellebrite, MSAB and Oxygen Forensics sell software and hardware to law enforcement. Once your phone is connected to one of these mobile phone extraction tools, the device extracts, analyses and presents the data contained on the phone.
What data these tools can extract and what method is used will…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: Explainer graphic
You can also read a more detailed explainer about mobile phone extraction here.
Content type: Examples
In 2018 a report from the Royal United Services Institute found that UK police were testing automated facial recognition, crime location prediction, and decision-making systems but offering little transparency in evaluating them. An automated facial recognition system trialled by the South Wales Police incorrectly identified 2,279 of 2,470 potential matches. In London, where the Metropolitan Police used facial recognition systems at the Notting Hill Carnival, in 2017 the system was wrong 98% of…
Content type: Long Read
TO TAKE PART IN OUR CAMPAIGN, RIGHT CLICK ON THE PICTURES BELOW, SAVE THEM, AND SHARE THEM ON SOCIAL MEDIA TAGGED #SPYPOLICE
Have you ever been to a peaceful protest, demo or march? Did you assume that the police would only be identifying 'troublemakers'? How would you feel if just by turning up at a peaceful protest, the police automatically identified you, without your consent or knowledge, and stored personal information about you (including photographs of your face) in a secret database?…
Content type: Press release
We found this picture here.
Privacy International has today a issued a formal complaint to the UK Information Commissioner about the police’s use of intrusive ‘mobile phone extraction’ technology, enabling them to download all of the content from a person’s phone — without a warrant, and whether they are suspect, witness or even victim of a crime. Further complaints have also been sent to the Home Office and the Independent Office for Police Conduct, calling for urgent reforms to a totally…
Content type: News & Analysis
This op-ed originally appeared in the New Statesman.
Imagine the police searching your home without good reason, without a warrant, without your knowledge. For good measure let’s also imagine that they take a full inventory of all of your possessions and store this in a secret database indefinitely.
A peculiar feature of modernity is that what we would find dystopian in the real world is banal in our virtual world. And the irony is that this can be a greater violation of our privacy and…