Search
Content type: Long Read
The fourth edition of PI’s Guide to International Law and Surveillance provides the most hard-hitting past and recent results on international human rights law that reinforce the core human rights principles and standards on surveillance. We hope that it will continue helping researchers, activists, journalists, policymakers, and anyone else working on these issues.The new edition includes, among others, entries on (extra)territorial jurisdiction in surveillance, surveillance of public…
Content type: Advocacy
BackgroundThe Snowden revelations and subsequent litigation have repeatedly identified unlawful state surveillance by UK agencies. In response, the UK Parliament passed the highly controversial Investigatory Powers Act 2016 (IPA), which authorised massive, suspicionless surveillance on a scale never seen before, with insufficient safeguards or independent oversight.Privacy International led legal challenges to this mass surveillance regime both before and after the Act became law. The Act…
Content type: News & Analysis
As Amnesty International and Forbidden Stories continue to publish crucial information about the potential targets of NSO Group’s spyware, we know this much already: something needs to be done.
But what exactly needs to be done is less obvious. Even though this is not the first time that the world has learned about major abuses by the surveillance industry (indeed, it’s not even the first time this month), it’s difficult to know what needs to change.
So how can the proliferation and use of…
Content type: News & Analysis
In mid-2019, MI5 admitted, during a case brought by Liberty, that personal data was being held in “ungoverned spaces”. Much about these ‘ungoverned spaces’, and how they would effectively be “governed” in the future, remained unclear. At the moment, they are understood to be a ‘technical environment’ where personal data of unknown numbers of individuals was being ‘handled’. The use of ‘technical environment’ suggests something more than simply a compilation of a few datasets or databases.
The…
Content type: News & Analysis
Today Advocate General (AG) Campos Sánchez-Bordona of the Court of Justice of the European Union (CJEU), issued his opinions (C-623/17, C-511/18 and C-512/18 and C-520/18) on how he believes the Court should rule on vital questions relating to the conditions under which security and intelligence agencies in the UK, France and Belgium could have access to communications data retained by telecommunications providers.
The AG addressed two major questions:
(1) When states seek to impose…
Content type: Long Read
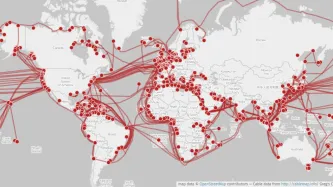
Six years after NSA contractor Edward Snowden leaked documents providing details about how states' mass surveillance programmes function, two states – the UK and South Africa – publicly admit using bulk interception capabilities.Both governments have been conducting bulk interception of internet traffic by tapping undersea fibre optic cables landing in the UK and South Africa respectively in secret for years.Both admissions came during and as a result of legal proceedings brought by Privacy…
Content type: Long Read
Imagine that every time you want to attend a march, religious event, political meeting, protest, or public rally, you must share deeply personal information with police and intelligence agencies, even when they have no reason to suspect you of wrongdoing.
First, you need to go to the police to register; have your photo taken for a biometric database; share the contacts of your family, friends, and colleagues; disclose your finances, health records, lifestyle choices, relationship status, and…
Content type: Impact Case Study
What is the problem
For over two decades we have been documenting an alarming use and spread of surveillance. It is no longer just the wars on terror or drugs or migration that is driving this trend. The management of health crises and distribution of welfare regularly are among others being used to justify this turn to increasingly invasive forms of surveillance. From country to country we see the same ideas and the same profiteers expanding their reach.
When we first released our report on…
Content type: Long Read
Privacy International is celebrating Data Privacy Week, where we’ll be talking about privacy and issues related to control, data protection, surveillance and identity. Join the conversation on Twitter using #dataprivacyweek.
Exercising the right to privacy extends to the ability of accessing and controlling our data and information, the way it is being handled, by whom, and for what purpose. This right is particularly important when it comes to control of how States perform these activities.…
Content type: Long Read
“This is my personal opinion,” concedes Branko, a taxi driver in Skopje, the Republic of Macedonia's capital. “It was done by America to stop Putin building his gas pipe line through Macedonia.”
“This is just politics,” he advises, skeptically.
It's a common reaction to the wiretapping scandal in Macedonia. Beginning in February last year when opposition leader Zoran Zaev posted a series of wiretaps online that he called 'bombs' – they seemingly showed that for years the phone calls of some…
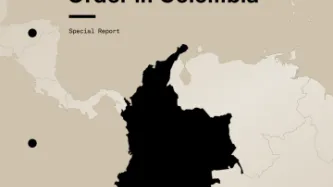
Content type: Report
For nearly two decades, the Colombian government has been expanding its capacity to spy on the private communications of its citizens. Privacy International's investigation reveals the state of Colombia's overlapping, unchecked systems of surveillance, including mass surveillance, that are vulnerable to abuse.
See the report in English and Spanish.
Content type: Press release
Governments across Central Asia have deployed advanced surveillance systems, including monitoring centres capable of spying on an entire country's communications, according to a new investigative report published today by Privacy International.
The comprehensive report, “Private Interests: Monitoring Central Asia”, contains personal accounts taken by Privacy International detailing how Central Asian governments use electronic surveillance technology to spy on activists and…
Content type: Press release
Privacy International, Reporters Without Borders, Digitale Gesellschaft, FIDH, and Human Rights Watch welcome news that the European Commission will move ahead and add specific forms of surveillance technology to the EU control list on dual use items, thus taking steps to finally hold companies to account who sell spy equipment and enable human rights abuses.
These important steps demonstrate that policymakers are beginning to wake up to the real harm that exists…
Content type: News & Analysis
Two new categories of surveillance systems were added into the dual-use goods and technologies control list of the Wassenaar Arrangement last week in Vienna, recognising for the first time the need to subject spying tools used by intelligence agencies and law enforcement to export controls.
While there are many questions that still need to be answered, Privacy International cautiously welcomes these additions to the Wassenaar Arrangement. Undoubtedly, these new…
Content type: News & Analysis
Privacy International is pleased to announce the Surveillance Industry Index, the most comprehensive publicly available database on the private surveillance sector.
Over the last four years, Privacy International has been gathering information from various sources that details how the sector sells its technologies, what the technologies are capable of and in some cases, which governments a technology has been sold to. Through our collection of materials and brochures at surveillance trade…
Content type: News & Analysis
Through our Big Brother Incorporated project, Privacy International over the past two years has been campaigning against the export of surveillance technologies by Western companies to repressive regimes. One of the seminal moments of this campaign was in 2011, when we partnered with Wikileaks to release the SpyFiles, which catalogued hundreds of brochures, presentations, marketing videos, and technical specifications exposing the inner workings of the international trade in…