Advanced Search
Content Type: Long Read
The Sustainable Development Goals (SDGs) are the United Nations-led initiative to define the development agenda. Building on the eight Millennium Development Goals, the SDG’s 17 goals – and the 169 targets – serve as an opportunity to tackle many of the most pressing issues in the world today. The SDGs are also explicitly grounded in human rights. Goal 16 on “peace, justice, and sustainable institutions” aims to “Promote peaceful and inclusive societies for sustainable development, provide…
Content Type: Long Read
Privacy International’s new report shows how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies. Driven by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, peoples’ rights, and the rule of law.To ensure that surveillance powers used by governments are used to protect rather than endanger people, it is essential that the public,…
Content Type: Long Read
The idea of a “smart city” is primarily a marketing concept, used to sell data-intensive technologies under the pretext of improving the functioning of cities. This could include injecting ‘smart’ tech into delivering services, public safety, environmental monitoring, traffic control, among other possible applications.
One in particular aspect of smart cities has been consistently problematic: how these projects are used to boost law enforcement and policing under the guise of public safety.…
Content Type: Long Read
Creative Commons Photo Credit: Source
UPDATE: 30 July 2019
Privacy International has identified the following:
Two RAB officers received approval to travel to the USA in April 2019 for training on “Location Based Social Network Monitoring System Software for RAB Intelligence Wing”
Three RAB officers received approval to travel to Russia in August 2017 to participate in user training of “Backpack IMSI Catcher (2G, 3G, 4G)” paid for by Annex SW Engineering, a…
Content Type: Long Read
Creative Commons Photo Credit: Source
In the midst of continued widespread public outrage at the US government’s brutal ‘zero-tolerance’ policy around immigration – multiple data and analytics companies have quietly avoided answering questions about their role in feeding the US Immigration and Customs Enforcement (ICE) agency’s data backbone. These companies are bidding to work with an agency that has time and time again shown itself to be a brutal and problematic.
Privacy International…
Content Type: Report
The Information Commissioner’s Office (ICO) recently issued a series of decisions in Privacy International’s long-running battle for information about UK police forces' acquisition of IMSI catchers. This case study provides an in-depth summary and analysis of this process.
We hope it is useful to both campaigners seeking greater transparency from policing bodies, and more widely to Freedom of Information campaigners who are trying to challenge 'neither confirm nor deny' responses to FOI…
Content Type: Report
Privacy International welcomes the opportunity to file these comments in advance of the Federal Trade Commission’s public hearings on competition and consumer protection in the 21st century.
Content Type: Report
Countries with powerful security agencies are spending literally billions to equip, finance and train security and surveillance agencies around the world — including authoritarian regimes. This is resulting in entrenched authoritarianism, further facilitation of abuse against people, and diversion of resources from long-term development programmes.
Privacy International's report 'Teach 'em to Phish: State Sponsors of Surveillance' examines this problem closely, providng examples from US, China…
Content Type: Long Read
Privacy International (PI) has today released a new report, 'Teach 'em to Phish: State Sponsors of Surveillance', showing how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies.
Spurred by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, rights, and the rule of law.
As well as providing a background to the issue, the report…
Content Type: Long Read
How would you feel if you were fingerprinted by the police before you were allowed to take part in a peaceful public demonstration?
As tens of thousands of people attend massive public demonstrations across the UK today against US President Donald Trump in a ‘Carnival of Resistance’, it’s a question worth asking. Why? Because the police now deploy a range of highly sophisticated surveillance tools at public events which are just as if not more intrusive. And these technologies should be even…
Content Type: Long Read
This piece was written by PI voluteer Natalie Chyi.
Transparency is necessary to ensure that those in power – including governments and companies – are not able to operate in the dark, away from publicscrutiny. That’s why calls for more transparency are routine by everyone from civil society and journalists to politicians.
The bigger picture is often lost when transparency is posed as the only solution to shadowy state and corporate powers. For one, the term is so broadly understood that it…
Content Type: Long Read
Privacy and data protection are currently being debated more intensively than ever before. In this interview, Frederike Kaltheuner from the civil rights organisation Privacy International explains why those terms have become so fundamentally important to us. The article was first published in the newly launched magazine ROM. The interview was conducted by ROM publisher Khesrau Behroz and writers Patrick Stegemann and Milosz Paul Rosinski.
Frederike Kaltheuner, you work for Privacy…
Content Type: Long Read
Yesterday the UK's Information Commissioner's Office (ICO) - which is responsible for ensuring people's personal data is protected - announced it intends to fine Facebook the maximum amount possible for its role in the Cambridge Analytica scandal.
This decision highlights of how serious and rampant misuse and exploitation of data is. Facebook is responsible and failed to comply with data protection 101: be upfront and honest about what you are doing with people's data.
Importantly, the ICO's…
Content Type: Long Read
Update 28 June 2018
Last week Privacy International wrote to Thomson Reuters Corporation asking the company to commit to ensuring the vast amounts of data they provide to US immigration agencies isn’t used to identify families for indefinite detention or separation, or for other human rights abuses.
Thomson Reuters has unfortunately ignored our specific questions and made no such commitment.
Instead, the CEO Thomson Reuters Special Services (TRSS) a subsidiary, makes clear that instead of…
Content Type: Long Read
The European Union's new data privacy law (General Data Protection Regulation, better known as GDPR) takes effect today May 25th, 2018, after a two-year transition period. Despite some companies appearing to believe otherwise, and many articles misrepresenting its contents, the GDPR will have a significative impact beyond the European Union, and it will extend many of its data privacy safeguards to users’ data globally.
There are a number of reasons that explain this impact:
Obligations…
Content Type: Long Read
We found the image here.
Open a Russian Matryoshka doll and you will find a smaller doll inside. Ask a large data company such as Acxiom and Oracle where they get their data from, and the answer will be from smaller data companies.
Data companies – a catch all term for data brokers, advertisers, marketers, web trackers, and more – facilitate a hidden data ecosystem that collects, generates and supplies data to wide variety of beneficiaries. The beneficiaries of the ecosystem can include other…
Content Type: Long Read
Privacy and data protection are fundamental rights. When respected they help improve trust and reduce power imbalances. Individuals should have rights over their personal data, regardless of who holds or processes it, and effective ways to enforce those rights, through independent bodies.
While not an ideal solution, GDPR gives individuals more control over their personal data. Rather than burdening individuals with managing and protecting their data, the onus will be on the companies to do so…
Content Type: Long Read
If you operate an internet company in Russia, you aren’t necessarily surprised to one day open the door to someone, grasping in one hand a bundle of wires and in the other a letter from a government agency demanding access to your servers, with a black box wedged under one arm.
Internet companies in Russia are required by law to store the content of users’ communications for six months and the metadata of users’ communications for three years, essentially meaning that what a person does…
Content Type: Long Read
Hasn't Facebook said it would give European data protection to all of their users?
Yes, but only in very vague language. In an initial reaction to the Cambridge Analytica scandal, Mark Zuckerberg declared that Facebook would apply the EU General Data Protection Regulation (GDPR) “in spirit” to their 2 billion users worldwide. When questioned by members of the US Congress, Zuckerberg declared that "[a]ll the same controls will be available around the world". Representative Green sought…
Content Type: Report
Artificial Intelligence (AI) is part of our daily lives. This technology shapes how people access information, interact with devices, share personal information, and even understand foreign languages. It also transforms how individuals and groups can be tracked and identified, and dramatically alters what kinds of information can be gleaned about people from their data.
AI has the potential to revolutionise societies in positive ways. However, as with any scientific or technological…
Content Type: Report
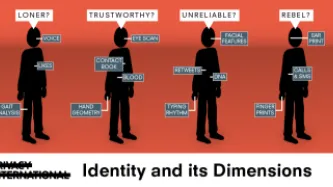
The use of biometric technology in political processes, i.e. the use of peoples’ physical and behavioural characteristics to authenticate claimed identity, has swept across the African region, with 75% of African countries adopting one form or other of biometric technology in their electoral processes. Despite high costs, the adoption of biometrics has not restored the public’s trust in the electoral process, as illustrated by post-election violence and legal challenges to the results of…
Content Type: Long Read
TO TAKE PART IN OUR CAMPAIGN, RIGHT CLICK ON THE PICTURES BELOW, SAVE THEM, AND SHARE THEM ON SOCIAL MEDIA TAGGED #SPYPOLICE
Have you ever been to a peaceful protest, demo or march? Did you assume that the police would only be identifying 'troublemakers'? How would you feel if just by turning up at a peaceful protest, the police automatically identified you, without your consent or knowledge, and stored personal information about you (including photographs of your face) in a secret database?…
Content Type: Long Read
A major new report published today by Privacy International has identified alarming weaknesses in the oversight arrangements that are supposed to govern the sharing of intelligence between state intelligence agencies.
'Secret Global Surveillance Networks: Intelligence Sharing Between Governments and the Need for Safeguards' is based on an international collaborative investigation carried out by 40 NGOs in 42 countries.
Previously undisclosed documents obtained by PI via litigation in the…
Content Type: Report
‘Secret Global Surveillance Networks’ is a major PI report, based on an unprecedented international collaborative investigation carried out by 40 NGOs in 42 countries.
Our research shows that, globally, the sharing of intelligence is alarmingly under-regulated, opening the door to human rights abuses. Intelligence sharing has evolved dramatically with the rise of new surveillance technologies, enabling governments to collect, store, and share vast troves of personal information, including data…
Content Type: Long Read
This piece was originally published in Lawfare in April 2018
The United States is party to a number of international intelligence sharing arrangements—one of the most prominent being the so-called “Five Eyes” alliance. Born from spying arrangements forged during World War II, the Five Eyes alliance facilitates the sharing of signals intelligence among the U.S., the U.K., Australia, Canada and New Zealand. The Five Eyes countries agree to exchange by default all signals intelligence…
Content Type: Long Read
We found the image here.
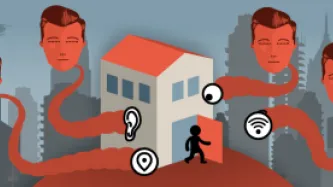
When we browse the internet, go to work, drive down the street, go shopping, interact with institutions, or simply move through the city, data is collected about us.
Advanced profiling technologies answer questions we did not raise. They generate knowledge we did not anticipate, but are eager to apply. As knowledge is power, profiling changes the power relationships between the profilers and the profiled.
In a world where everything we do becomes more and more…
Content Type: Report
In contrast to automated decision-making, profiling is a relatively novel concept in European data protection law. It is now explicitly defined in Article 4(4) of the EU General Data Protection Regulation (GDPR), and refers to the automated processing of data (personal and not) to derive, infer, predict or evaluate information about an individual (or group), in particular to analyse or predict an individual’s identity, their attributes, interests or behaviour.
Through profiling, highly…
Content Type: Report
La seguridad digital es una discusión crítica y hay que reconocer que la sociedad civil y los grupos de interés público no han sido suficientemente considerados. Como respuesta, varias organizaciones de la sociedad civil de América Latina se unieron para presentar informes que recuerdan a las entidades estatales responsables de formulación de políticas públicas que la seguridad digital debe tener en cuenta la seguridad de las personas y los derechos humanos. Presentamos la serie, Derechos…
Content Type: Long Read
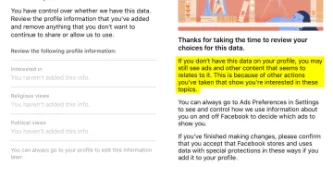
As we said before, Facebook and Cambridge Analytica scandals are a wake-up call for policy makers. And also a global issue. People around the world are concerned by the exploitation of their data. The current lack of transparency into how companies are using people’s data is unacceptable and needs to be addressed.
There is an entire hidden ecosystem of companies harvesting and sharing personal data. From credit scoring and insurance quotations to targeted political communication, this…
Content Type: Report
The ‘Digital stop and search’ report examines the use of ‘mobile phone extraction’ tools by the UK police, enabling them to download all of the content and data from people’s phones.
Privacy International have exposed a potentially unlawful regime operating with UK police forces, who are confused about the legal basis for the technology they are using. The police are acting without clear safeguards for the public, and no independent oversight to identify abuse and misuse of sensitive personal…