Advanced Search
Content Type: Advocacy
PI Opening Statement at PEGA Hearing on "Spyware and ePrivacy"
[check against delivery]
Thank you very much for offering us the opportunity to give evidence before this Committee for a second time.
Privacy International (PI) is a London-based non-profit that researches and advocates globally against government and corporate abuses of data and technology. For years we have been tracking the surveillance industry, challenging unlawful surveillance before national courts as well as the Court of…
Content Type: Report
Introduction
Several policy initiatives are in progress at the EU level. They seek to address the sustainability of connected devices such as smartphones, tablets and smart speakers. While initiatives to extend the useful life of hardware are important, software must not be ignored. Almost any digital device with which we interact today relies on software to function, which acts as a set of instructions that tells the hardware what to do. From smart thermostats to smart speakers, to our…
Content Type: Press release
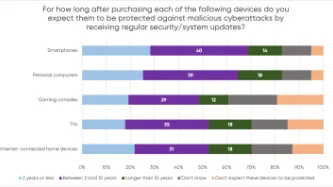
A YouGov survey commissioned by PI shows that consumers expect their smartphones, computers, smart TVs and gaming consoles to receive security updates for a much longer period than what several manufacturers actually provide, leaving consumers with expensive tech that is vulnerable to cyberattacks.
The majority of consumers in the survey assumed their devices would be protected beyond two years, but current industry practices fail to meet these expectations. PI investigated the software…
Content Type: Advocacy
On 30 March 2022, the European Commission published a proposal for a directive empowering consumers for the green transition, which is is designed to enhancing consumer rights in making informed choices in order to play an active role in the transition to a climate-neutral society. At the moment, the proposal is being discussed by the Committee on the Internal Market and Consumer Protection of the European Parliament.
PI welcomes the aim of the proposal to enhance consumer rights, particularly…
Content Type: Press release
The European Ombudswoman, Emily O’Reilly, has launched two new investigations into Frontex, the European Border and Coast Guard Agency, and into the European External Action Service (EEAS), the EU’s diplomatic agency, in relation to their support to non-EU countries to develop surveillance capabilities and, in particular, their lack of prior human rights risk and impact assessments.
The investigations, opened on 5 October 2022, come in response to complaints filed by Privacy International,…
Content Type: Advocacy
UPDATES:The Platform Work Directive (PWD) became law in October 2024. Member States have until December 2026 to implement its provisions into their national law. The final text of the PWD provides the following:A person performing platform work cannot be fired or suspended based on a decision made by an algorithm or automated decision-making systems.Platforms must provide upfront information, in "clear and plain language", about their use of automated decision-making systems.Platform workers…
Content Type: Financial Report
Audited accounts for the year ending January 31, 2022
Content Type: News & Analysis
Privacy International collaborated with the Carter Center as part of a pre-election assessment team focussing on the use of technology in the run up to and during the Kenyan election which took place 9 August.
In the context of this pre-election assessment, PI travelled to Nairobi between 4th-10th July 2022 in order take a deeper look at issues connected to voting technologies being used in the Kenyan elections with a particular focus on the implementation of the Data Protection Act.
PI first…
Content Type: Video
Please note this podcast was recorded before Sebastian and Netzpolitik were able to talk to PimEyes CEO Gobronidze in person.
Links
Find more from Sebastian
More of Netzpolitik's work on PimEyes
PI's work on facial recognition
Our work on Clearview
Content Type: Advocacy
Privacy International welcomes the opportunity to provide written input on the working draft of the WHO’s Pandemic prevention, preparedness, and response accord (“WHO CAII”) published on 13 July 2022.
This submission is based on our research and assessment of data-reliant and tech-intensive measures deployed by governments and companies in response to Covid-19 and its aftermath, which documented how these measures impacted people’s fundamental rights and freedoms, including the right to…
Content Type: Examples
Despite having opened their borders to and taking in millions of fleeing Venezuelan migrants, the Colombian government’s handling process for this population tells a story of discrimination rather than inclusion.
The 2021 issuance of the Temporary Statute for Venezuelan Migrants came with a legal framework laying out the benefits for incoming Venezuelans, but also outlined how a multibiometric system would be used for identification of this specific migrant group.
This system allows for…
Content Type: Examples
In December 2019, a Brazilian public security programme, called the Integrated Border Operations Center (CIOF) was presented. The CIOF aims to combat transnational organised crime in the region of Foz do Iguaçu and the Triple Border Area1, shared by Argentina, Brazil, and Paraguy, and integrate different public security agents through a centralised system.
It has been reported that CIOF is part of a wider digital security apparatus being deployed in the Triple Border Area, that there is…
Content Type: Examples
A vulnerability in the Bono Familiar Universal, the platform used to distribute the financial subsidy provided to households in precarious economic situation by the Peruvian government in response to the Covid-19 pandemic, enabled the subsidy to be accessed by malicious individuals.
The vulnerability was reported by Deep Security, and it was resolved but an undetermined number of malicious individuals were able to pose as beneficiaries to access the platform and collect the subsidy themselves…
Content Type: Report
End-to-end encryption (E2EE) contributes significantly to security and privacy. For that reason, PI has long been in favour of the deployment of robust E2EE.Encryption is a way of securing digital communications using mathematical algorithms that protect the content of a communication while in transmission or storage. It has become essential to our modern digital communications, from personal emails to bank transactions. End-to-end encryption is a form of encryption that is even more private.…
Content Type: Key Resources
ID systems create their own reality: they create a situation where ID is needed for more things and more actors, which only increases people’s vulnerability to their data being misused or abused.
Content Type: Key Resources
ID systems are all too often a smokescreen. They are a tool for giving unprecedented surveillance powers to the police, security services, and other actors.
Content Type: Key Resources
The fact of the matter is: your ID system will exclude, and the people it’s excluding will be the most vulnerable and marginalised.
Content Type: Advocacy
Read in English
Nosotros, las organizaciones de la sociedad civil y los individuos abajo firmantes, instamos al Banco Mundial y a otras organizaciones internacionales a que tomen medidas inmediatas para cesar las actividades que promueven modelos perjudiciales de sistemas de identificación digital (ID digital).
Los firmantes de esta carta se encuentran en diferentes países, trabajan con diversas comunidades y aportan una amplia gama de conocimientos. Entre este grupo, hay muchas…
Content Type: Advocacy
We, the undersigned civil society organizations and individuals, urge the World Bank and other international organizations to take immediate steps to cease activities that promote harmful models of digital identification systems (digital ID).
The signatories of this letter are located in different countries, work with diverse communities, and bring a wide range of expertise. Among this group, there are many shared concerns and similar experiences documenting the harmful impacts…
Content Type: Course Section
Knowledge gap?
Research finding: In 2018, a study by the NGO Doteveryone on digital understanding found a “major understanding gap” of British citizens when it comes to digital technologies. For example, they found that 83% of British don’t realise that information shared about them by others is collected, and 70% don’t realise free apps make money from data.
Finding: In 2020, another study by Doteveryone found that while the public’s understanding of data collection has increased, it still…
Content Type: Course Section
Building on our experience and research, in this chapter we introduce a number of good practices when educating about data: what we found works well and what educators should pay attention to. The chapters after this then provide advice on how to identify 'good' educational resources on data, and on creating your own resources.
Content Type: Course Section
Educators are keen to teach, learners are keen to learn. As we covered in previous chapters, the learning gaps are clear. Many citizens are unaware of the ways in which their data is used, data systems function and how they influence their lives and our societies. These aspects crucially need to be included when educating about digital technologies. But there’s another gap too: educators don’t know where to find teaching resources.
Content Type: Course Section
In this chapter, we will give a brief overview of the landscape of online ‘critical data literacy resources’, present a database that collects such resources and recommend some example resources for different types of learners. While there are also ‘traditional’ formats of teaching material available, for example textbooks or worksheets, our research and thus this chapter focusses on online resources.
Online resources can have various formats: websites, videos, games, podcasts, online courses,…
Content Type: Course Section
We often get asked by others who are interested in creating educational resources about data, what they should consider as they develop their own critical data literacy resources for sharing with others.
Content Type: Long Read
Introduction
In response to the unprecedented social, economic, and public health threats posed by the Covid-19 pandemic, the World Bank financed at least 232 "Covid-19 Response" projects. The projects were implemented across countries the World Bank classifies as middle and low-income.
This article will focus on eight (8) Covid-19 Response projects which sought to deliver social assistance to individuals and families on a "non-contributory" basis (this means that the intended beneficiaries…
Content Type: Advocacy
Today, PI filed a complaint with the Forensic Science Regulator (FSR) in relation to quality and accuracy issues in satellite-enabled Global Positioning System (GPS) tags used for Electronic Monitoring of subjects released from immigration detention (GPS tags). We are concerned there may be systemic failures in relation to the quality of data extracted from tags, processed and interpreted for use in investigations and criminal prosecutions.
The GPS tags are used by the Home Office to…
Content Type: News & Analysis
Privacy International (PI) has today filed complaints with the Information Commissioner (ICO) and Forensic Science Regulator (FSR) against the UK Home Office's use of GPS ankle tags to monitor migrants released on immigration bail. This policy and practice represents a seismic change in the surveillance of migrants in the UK. PI was first alerted to this scheme by organisations such as Bail for Immigration Detainees, an independent charity that exists to challenge immigration detention in the…