Search
Content type: Examples
As governments look into surveillance, geolocation and biometric facial recognition to contain the coronavirus, even if they violate user data privacy, the controversial facial recognition company Clearview AI is allegedly negotiating a partnership with state agencies to monitor infected people and the individuals with whom they have interacted. The data mining company Palantir is already collaborating with the CDC and NIH, while the White House convened a task force of technology companies to…
Content type: Case Study
In 2015, a man in Connecticut was charged with murdering his wife based on evidence from her Fitbit. Richard Dabate, the accused, told the police that a masked assailant came into the couple’s suburban home at around 9am on 23 December 2015, overpowering Dabate then shooting his wife as she returned through the garage.
However, the victim’s fitness tracker told a different story. According to data from the device, which uses a digital pedometer to track the wearer’s steps, Dabate’s wife was…
Content type: Case Study
In early May 2019, it was revealed that a spyware, exploiting a vulnerability in Facebook’s WhatsApp messaging app, had been installed onto Android and iOS phones. The spyware could be used to turn on the camera and mic of the targeted phones and collect emails, messages, and location data. Citizen Lab, the organization that discovered the vulnerability, said that the spyware was being used to target journalists and human rights advocates in different countries around the world. The spyware…
Content type: News & Analysis
Maddie Stone, formally a Senior reverse engineer and tech lead on the Android security team, shockingly revealed a number of examples of how pre-installed apps on Android devices can undermine users privacy and security in her BlackHat USA talk in August 2019. The video of the talk only recently became available to the public in late December 2019.
The apps in question come preloaded on a device when it is purchased and often can't be removed. Stone reveals a litany of abuses carried out by…
Content type: Case Study
Slavery, servitude, and forced labour are absolutely forbidden today, as is anything that seeks to undermine or limit that restriction. The horrific reality, however, is that modern slavery remains a significant global issue.
Human trafficking is one form of modern slavery. It involves the recruitment, harbouring or transporting of people into a situation of exploitation through the use of violence, deception or coercion and forcing them to work against their will.
Human traffickers do…
Content type: Examples
Bethany Christian Services, an international pregnancy support and adoption agency, is launching a programme with Copley Advertising to send targeted ads to individuals visiting Planned Parenthood clinics, abortion clinics, methadone clinics and high-risk areas (AHPA). The targeting will be done through the use of geo fencing based on smartphones located within the selected locations.
Source: https://www.liveaction.org/news//adoption-agency-send-pro-life-ads-smartphones-inside-abortion-…
Content type: Examples
In 2018, Brian Hofer, the chair of Oakland's Privacy Advisory Commission, filed suit after police wrongfully stopped him at gunpoint because their automated license plate recognition system, supplied by Vigilant Solutions, indicated that the rental car he was driving had been stolen. The car had in fact been stolen some months earlier, but been recovered. Despite such errors, police claim that the technology has helped reduce crime, identify stolen vehicles, and identify and arrest suspects.…
Content type: Examples
New workplace technologies are generating mountains of data on workers despite a lack of clarity over how the data is used and who owns it. In offices, smart badges track interactions and sensors track fitness and health; in trucks sensors monitor drivers' performance in the name of safety. In the US state of Illinois, between July and October 2017 26 lawsuits were filed by employees alleging that their employers had violated the state's Biometric Information Privacy Act, which requires a…
Content type: Examples
After four years of negotiation, in 2017 Google began paying Mastercard millions of dollars for access to the latter's piles of transaction data as part of its "Stores Sales Measurement" service. Google, which claimed to have access to 70% of US credit and debit cards through partners, said that double-blind encryption prevents both partners from seeing the other's users' personally identifiable information. Mastercard said the company shares transaction trends with merchants and their service…
Content type: Examples
In November 2018, 112 civil liberties, immigrant rights groups, child welfare advocates, and privacy activists wrote a letter to the heads of the US Department of Health and Human Services and the Department of Homeland Security demanding an immediate halt to the HHS Office for Refugee Resettlement's practice of using information given them by detained migrant children to arrest and deport their US-based relatives and other sponsors. The policy began in April 2018, and the result has been that…
Content type: News & Analysis
Picture Credit: US AID
US President Trump has been cutting aid to Central America, including a surprise cut of approximately $500m in aid to the “Northern Triangle” countries of El Salvador, Guatemala, and Honduras, apparently as punishment for “doing absolutely nothing” to prevent emigration to the US.
What remains of the funds is largely and deliberately being repurposed for spending on the US’s own security interests: indeed, one area which his…
Content type: News & Analysis
Foto: US AID
El presidente estadounidense Trump ha estado recortando la ayuda a Centroamérica, incluyendo un recorte sorpresivo de aproximadamente 500 millones de dólares a los países del “Triángulo del Norte” (El Salvador, Guatemala y Honduras), al parecer como castigo por “no haber hecho absolutamente nada” para impedir la emigración hacia los Estados Unidos.
Los fondos restantes están siendo reorientados,en su gran mayoría y deliberadamente, al gasto para…
Content type: Long Read
Image courtesy of Michael Coghlan
The long-speculated Facebook cryptocurrency is finally here! Libra!
Libra Association, an entity co-founded by Facebook, has announced the creation of a new cryptocurrency, Libra, "a simple global currency and financial infrastructure that empowers billions of people".
The white paper that outlines the rationale for the new currency makes a number of heady statements, some which anyone who cares about rights should commend -- and some which should…
Content type: Advocacy
Privacy International has today sent letters to leading social media platforms to ask what they're doing to protect their users' from dangerous surveillance by government immigration authorities.
The letter comes following the implementation of plans by US authorities to require nearly all visa applicants to hand over identifiers of all social media accounts they have used in the previous five years, or face “serious immigration consequences”.
The move not only represents…
Content type: News & Analysis
US Immigration and Customs Enforcement (ICE), the agency at the centre of carrying out President Trump’s “zero tolerance” approach to immigration enforcement and family separation, has for years been contracting a US surveillance company to intercept peoples’ communications across the United States. The wide potential scope for the use of the powers raises concerns about their use for the real-time surveillance of people, families, and communities caught up in Trump’s immigration crackdown…
Content type: Examples
Virginia Eubanks explains what we can draw from understanding the experience of surveillance of marginalised groups: it is a civil rights issue, technologies carry the bias of those who design them, people are resisting and why we need to move away from the privacy rights discourse.
https://prospect.org/article/want-predict-future-surveillance-ask-poor-communities
Author: Virginia Eubanks
Publication: The American Prospect
Content type: News & Analysis
The first half of 2018 saw two major privacy moments: in March, the Facebook/ Cambridge Analytica scandal broke, followed in May by the EU General Data Protection Regulation ("GDPR") taking effect. The Cambridge Analytica scandal, as it has become known, grabbed the attention and outrage of the media, the public, parliamentarians and regulators around the world - demonstrating that yes, people do care about violations of their privacy and abuse of power. This scandal has been one of…
Content type: Advocacy
Consultation Submission
In March 2019, Privacy International submitted a response to a consultation on Disinformation in Electoral Contexts, led by the Office of the Special Rapporteur for Freedom of Expression of the Inter-American Commission on Human Rights together with the Department of Electoral Cooperation and Observation (DECO) and the Department of International Law (DIL) of the Organisation of American States (OAS).
In our submission we highlighted the importance of minmising data…
Content type: Examples
Facebook's latest tool for inspecting political ads showed that in the run-up to the US mid-term elections in November 2018, many of the same politicians who had been questioning Facebook about privacy and leaked user data were spending campaign funds on advertisements on the service. Between 2014 and 2018, the digital percentage of political spending rose from 1% to 22% (or about $1.9 billion); between May and November 2018 political spending on Facebook and its subsidiaries came to nearly $…
Content type: Long Read
During the last World Economic Forum in Davos, the CEO of Microsoft joined the chorus of voices calling for new global privacy rules, saying the following in regard to the new European General Data Protection Regulation (GDPR):
“My own point of view is that it's a fantastic start in treating privacy as a human right. I hope that in the United States we do something similar, and that the world converges on a common standard."
We have come a long way. From tech companies fighting and…
Content type: News & Analysis
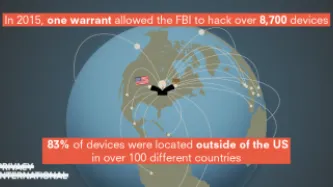
Federal law enforcement is deploying powerful computer hacking tools to conduct domestic criminal and immigration investigations.
By Alex Betschen, Student Attorney, Civil Liberties & Transparency Clinic, University at Buffalo School of Law
Hacking by the government raises grave privacy concerns, creating surveillance possibilities that were previously the stuff of science fiction. It also poses a security risk, because hacking takes advantage of unpatched vulnerabilities in our…
Content type: Press release
FOR IMMEDIATE RELEASE
December 21, 2018
CONTACTS:
Alex Betschen, Civil Liberties & Transparency Clinic, [email protected], 716–531–6649
Colton Kells, Civil Liberties & Transparency Clinic, [email protected], 585–766–5119
Abdullah Hasan, ACLU, [email protected], 646–905–8879
NEW YORK — Privacy International, the American Civil Liberties Union, and the Civil Liberties & Transparency Clinic of the University at Buffalo School of Law filed a lawsuit today…
Content type: News & Analysis
Photo credit: US Immigration and Customs Enforcement
The trial of Mexican drug lord Joaquin “El Chapo” Guzman started in New York back in November 2018. But last week, the jurors were presented with a trove of new key evidence: dozens of text messages exchanged between Guzman, his wife, and his mistresses.
The reason behind this set of revelations? Guzman had been spying on his wife and mistresses, using publicly-available surveillance software called FlexiSpy. Once installed on his targets…
Content type: Examples
In the months leading up to the US 2018 midterm elections, Republican officials in Georgia, Texas, and North Carolina made moves they described as ensuring voting integrity but which critics saw as blocking voter access. In Georgia, where Secretary of State Brian Kemp is charged with enforcing election law and was simultaneously running for governor, election officials blocked 53,000 applications to register, 70% of which are those of African-Americans, under a law requiring personal…
Content type: News & Analysis
Taylor Swift may be tracking you, particularly if you were at her Rose Bowl show in May.
According to an article published by Vanity Fair, at Swift’s concert at the California stadium, fans were drawn to a kiosk where they could watch rehearsal clips. At the same time – and without their knowledge - facial-recognition cameras were scanning them, and the scans were then reportedly sent to a “command post” in Nashville, where they were compared to photos of people who are known…
Content type: Advocacy
Consumers benefit from the existence of competitive markets, in which they can freely choose among a wide range of products and services. Competition policy plays an important role in this regard by ensuring that competition is not disrupted in a way that can harm consumers directly (e.g. leading to price increases or less choice) or indirectly (e.g. weakening competition as a process by hampering the ability of firms to compete on the merits).
Content type: News & Analysis
Our team wanted to see how data companies that are not used to being in the public spotlight would respond to people exercising their data rights. You have the right under the EU General Data Protection Regulation ("GDPR") to demand that companies operating in the European Union (either because they are based here or target their products or services to individuals in the EU) delete your data within one month. We wrote to seven companies and requested that they delete our data, and we've made…
Content type: Advocacy
Today, Privacy International has filed complaints against seven data brokers (Acxiom, Oracle), ad-tech companies (Criteo, Quantcast, Tapad), and credit referencing agencies (Equifax, Experian) with data protection authorities in France, Ireland, and the UK.
It’s been more than five months since the EU’s General Data Protection Regulation (GDPR) came into effect. Fundamentally, the GDPR strengthens rights of individuals with regard to the protection of their data, imposes more…
Content type: News & Analysis
Image Source
On 10 October 2018, the US Senate Committee on Commerce, Science, and Transportation, will convene a hearing titled “Consumer Data Privacy: Examining Lessons From the European Union’s General Data Protection Regulation and the California Consumer Privacy Act".
The Senate will hear from:
Dr. Andrea Jelinek, Chair, European Data Protection Board
Mr. Alastair Mactaggart, Board Chair, Californians for Consumer Privacy
Ms. Laura Moy, Executive Director and Adjunct…
Content type: News & Analysis
This piece was originally published on Just Security.
Ten years ago, an FBI official impersonated an Associated Press reporter to lure and track a teenager suspected of sending in prank bomb threats to his school. To find him, the FBI agent, posing as a reporter, sent the teenager links to a supposed story he was working on, but the links were infested with malware that once clicked on quickly exposed the teen’s location. More recently, the FBI has seized and modified websites so…