Search
Content type: Report
In Afghanistan and Iraq, the U.S. Department of Defense developed its biometric program in confluence with US military operations in. Its expansion was tightly linked to the goals of military commanders during the “War on Terror”: to distinguish insurgents and terrorists from the local civilian population. This research shows how the DOD’s biometric programme was developed and implemented without prior assessment of its human rights impact and without the safeguards necessary to prevent its…
Content type: Long Read
Image courtesy of Michael Coghlan
The long-speculated Facebook cryptocurrency is finally here! Libra!
Libra Association, an entity co-founded by Facebook, has announced the creation of a new cryptocurrency, Libra, "a simple global currency and financial infrastructure that empowers billions of people".
The white paper that outlines the rationale for the new currency makes a number of heady statements, some which anyone who cares about rights should commend -- and some which should…
Content type: Long Read
During the last World Economic Forum in Davos, the CEO of Microsoft joined the chorus of voices calling for new global privacy rules, saying the following in regard to the new European General Data Protection Regulation (GDPR):
“My own point of view is that it's a fantastic start in treating privacy as a human right. I hope that in the United States we do something similar, and that the world converges on a common standard."
We have come a long way. From tech companies fighting and…
Content type: Long Read
Creative Commons Photo Credit: Source
In the midst of continued widespread public outrage at the US government’s brutal ‘zero-tolerance’ policy around immigration – multiple data and analytics companies have quietly avoided answering questions about their role in feeding the US Immigration and Customs Enforcement (ICE) agency’s data backbone. These companies are bidding to work with an agency that has time and time again shown itself to be a brutal and problematic.
Privacy International…
Content type: Report
Privacy International welcomes the opportunity to file these comments in advance of the Federal Trade Commission’s public hearings on competition and consumer protection in the 21st century.
Content type: Report
Countries with powerful security agencies are spending literally billions to equip, finance and train security and surveillance agencies around the world — including authoritarian regimes. This is resulting in entrenched authoritarianism, further facilitation of abuse against people, and diversion of resources from long-term development programmes.
Privacy International's report 'Teach 'em to Phish: State Sponsors of Surveillance' examines this problem closely, providng examples from US, China…
Content type: Long Read
Privacy International (PI) has today released a new report, 'Teach 'em to Phish: State Sponsors of Surveillance', showing how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies.
Spurred by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, rights, and the rule of law.
As well as providing a background to the issue, the report…
Content type: Long Read
This piece was originally published in Lawfare in April 2018
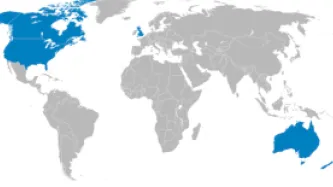
The United States is party to a number of international intelligence sharing arrangements—one of the most prominent being the so-called “Five Eyes” alliance. Born from spying arrangements forged during World War II, the Five Eyes alliance facilitates the sharing of signals intelligence among the U.S., the U.K., Australia, Canada and New Zealand. The Five Eyes countries agree to exchange by default all signals intelligence…
Content type: Long Read
“FISA section 702 reauthorisation” might not sound like it matters very much to very many people, but it’s pretty dramatic: in short, last month US lawmakers rejected a bill which would have provided protections for US citizens – constitutionally protected against being spied on by US spy agencies – from being spied on, and instead voted to extend their powers to do so.
In the fall out, it’s worth considering just why such mass surveillance powers are such a big issue, how the promise of…
Content type: Long Read
This piece was originally published in Just Security in November 2017.
The upcoming expiration of Section 702 of the Foreign Intelligence Surveillance Act (FISA) has launched a fresh wave of debate on how the statute’s “backdoor search loophole” allows the U.S. government to access Americans’ communications by searching information gathered on foreign intelligence grounds without a warrant. But while discussion about domestic information sharing is important, a critical…
Content type: Long Read
This piece was originally published in Just Security in August 2017
We recently published an analysis in Lawfare of the United Kingdom’s surveillance framework as it relates to the proposed U.S.-U.K. agreement for cross-border law enforcement data requests. Implementing the U.S.-U.K. agreement is subject to passage of draft legislation proposed by the Justice Department to Congress in July 2016 (“U.S. DOJ legislation”), which will set standards that approved partners like the U.K.…
Content type: Long Read
This piece was originally published in Lawfare in July 2017.
The United Kingdom has been a key partner in the United States’ efforts to reform the process that law enforcement officials use to make cross-border requests for data. These efforts address both foreign governments’ requests for data stored in the U.S. and reciprocal requests by the U.S. government for data stored abroad. As part of these efforts, the U.S. and the U.K. have negotiated a draft bilateral agreement (“U…
Content type: Long Read
This piece was originally published in Lawfare in May 2017.
This post is part of a series written by participants of a conference at Georgia Tech in Surveillance, Privacy, and Data Across Borders: Trans-Atlantic Perspectives.
Cross-border law enforcement demands have become increasingly important to law enforcement in the digital age. Digital evidence in one jurisdiction—such as the United States—is often necessary to investigate a crime that has effects in another jurisdiction…
Content type: Long Read
Disclaimer: This piece was written in April 2017. Since publishing, further information has come out about Cambridge Analytica and the company's involvement in elections.
Recently, the data mining firm Cambridge Analytica has been the centre of tons of debate around the use of profiling and micro-targeting in political elections. We’ve written this analysis to explain what it all means, and the consequences of becoming predictable to companies and political campaigns.
What does…
Content type: Long Read
Introduction
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. Yet hacking presents unique and grave threats to our privacy and security. It is far more intrusive than any other surveillance technique, capable of accessing information sufficient to build a detailed profile of a person, as well as altering or deleting that information. At the same time, hacking not only undermines the security of targeted systems, but also has…
Content type: Long Read
This piece was orignally published in Slate in February 2017
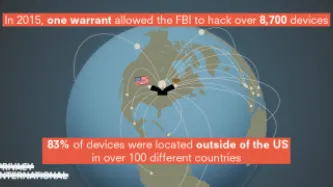
In 2015, the FBI obtained a warrant to hack the devices of every visitor to a child pornography website. On the basis of this single warrant, the FBI ultimately hacked more than 8,700 computers, resulting in a wave of federal prosecutions. The vast majority of these devices—over 83 percent—were located outside the United States, in more than 100 different countries. Now, we are in the midst of the first cases…
Content type: Long Read
This piece was written by Ashley Gorski, who is an attorney at the American Civil Liberties Union, and PI legal officer Scarlet Kim and originally appeared in The Guardian here.
In recent weeks, the Hollywood film about Edward Snowden and the movement to pardon the NSA whistleblower have renewed worldwide attention on the scope and substance of government surveillance programs. In the United States, however, the debate has often been a narrow one, focused on the…
Content type: Long Read
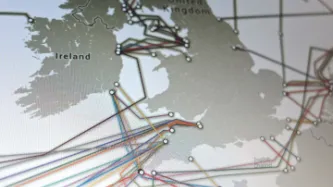
This week, Privacy International, together with nine other international human rights NGOs, filed submissions with the European Court of Human Rights. Our case challenges the UK government’s bulk interception of internet traffic transiting fiber optic cables landing in the UK and its access to information similarly intercepted in bulk by the US government, which were revealed by the Snowden disclosures. To accompany our filing, we have produced two infographics to illustrate the…
Content type: Long Read
This piece originally appeared here.
On both sides of the Atlantic, we are witnessing the dramatic expansion of government hacking powers. In the United States, a proposed amendment to Rule 41 of the Federal Rules of Criminal Procedure would permit the government to obtain a warrant, in certain circumstances, to hack unspecified numbers of electronic devices anywhere in the world. Meanwhile, across the pond, the British Parliament is currently debating the Investigatory…
Content type: Long Read
The recent back and forth between Apple and the FBI over security measures in place to prevent unauthorised access to data has highlighted the gulf in understanding of security between technologists and law enforcement. Modern debates around security do not just involve the state and the individual, the private sector plays a very real role too. There are worrying implications for the safety and security of our devices. Today, a new company stepped in to this discussion -- though it had been…
Content type: Long Read
Few revelations have been been as troubling for the right to privacy as uncovering the scope of the Five Eyes alliance. The intelligence club made up of Australia, Canada, New Zealand, the United Kingdom and the United States has integrated its collection efforts, staff, bases, and analysis programs. Yet the legal rulebook governing how the agencies ensure the most comprehensive joint surveillance effort in the history of mankind remains secret.
The little that is known suggests a…
Content type: Long Read
Modern day government surveillance is based on the simple concept of “more is more” and “bigger is better”. More emails, more text messages, more phone calls, more screenshots from Skype calls. The bigger the haystack, the more needles we can find.
Thanks to Edward Snowden, we know that this fundamental idea drives intelligence agencies like the NSA and GCHQ - the desire to collect it all, to generate gigantic haystacks through which to trawl. In the almost two years since the first of Snowden…
Content type: Long Read
Many people imagine intelligence sharing to be a practice whereby men in trench coats silently slide manilla envelopes containing anonymous tip-offs or intelligence reports marked TOP SECRET across tables in smoke-filled rooms.
While such practices certainly exist, they represent only a tiny slice of intelligence sharing activities, and are vastly overshadowed by the massive exchange of bulk unanlysed (raw) intelligence data that takes place between the UK and its Five Eyes allies.…
Content type: Long Read
The recent revelations, made possible by NSA-whistleblower Edward Snowden, of the reach and scope of global surveillance practices have prompted a fundamental re- examination of the role of intelligence services in conducting coordinated cross-border surveillance.
The Five Eyes alliance of States – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the…
Content type: Report
The recent revelations, made possible by NSA-whistleblower Edward Snowden, of the reach and scope of global surveillance practices have prompted a fundamental re-examination of the role of intelligence services in conducting coordinated cross-border surveillance.
The Five Eyes alliance of States – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the…
Content type: Long Read
Britain's spy agency, GCHQ, is secretly conducting mass surveillance by tapping fibre optic cables, giving it access to huge amounts of data on both innocent citizens and targeted suspects, according to a report in the Guardian.
Mass, indiscriminate surveillance of this kind goes against an individual's fundamental human right to privacy. The scope and scale of this program, which monitors the entire British public and much of the world, is neither necessary nor proportionate and thus,…
Content type: Long Read
Spy agencies have long sought to turn the technologies that improve all our lives against us. From some of the very first forms of remote communications such as telegraph cables, to modern-day means like Skype: if the spies can exploit it, they will.
And, as we’ve learnt over the last few months, the computer and mobile devices that millions of us own and carry around with us every day are no exception to this rule.
The smart phones, laptops, and devices that have changed how we communicate…
Content type: Report
The US does not have a general overarching privacy law like European Data Directive or the sweeping privacy protections contained in the European declarations of rights. The EU-US accord cites several laws, which it claims, give privacy rights to non-US persons. None of the cited laws offer any real substantive or procedural protections for Europeans. As explained below, the one law – the Privacy Act 5 U.S.C 552a – that could offer some modest protections is tellingly not even mentioned.
But…
Content type: Report
This is a memo prepared by Barry Steinhardt of Friends of Privacy USA for Members of the European Parliament regarding the proposed EU-US Agreement PNR.
The proposed agreement regarding Passenger Name Records (PNR) between the United States and the European Union is riddled with faulty assertions and assumptions about US law and the actual operations of the US government.
These faulty assertions and assumptions go to the heart of the agreement and undercut the claims of protections for…