Advanced Search
Content Type: Long Read
The UK border authority is using money ring-fenced for aid to train, finance, and provide equipment to foreign border control agencies in a bid to “export the border” to countries around the world.
Under the UK Border Force’s “Project Hunter”, the agency works with foreign security authorities to bolster their “border intelligence and targeting” capabilities with UK know-how and equipment.
As well as the provision of equipment and training, the Border Force is also advising countries on…
Content Type: Long Read
Cellebrite, a surveillance firm marketing itself as the “global leader in digital intelligence”, is marketing its digital extraction devices at a new target: authorities interrogating people seeking asylum.
Israel-based Cellebrite, a subsidiary of Japan’s Sun Corporation, markets forensic tools which empower authorities to bypass passwords on digital devices, allowing them to download, analyse, and visualise data.
Its products are in wide use across the world: a 2019 marketing…
Content Type: News & Analysis
Palantir and the UN’s World Food Programme (WFP) are partnering for a reported $45 million. Palantir, a US-based company that sells data software and has been the centre of numerous scandals.
The World Food Programme provides assistance in food and nutrition to around 92 million people each year. Systems that are produced in agreements such as the one between WFP and Palantir increase risks to the people the they are attempting to help. There are risks to both individuals and whole populations…
Content Type: News & Analysis
European leaders met last week in Brussels to discuss what is supposed to be two separate issues, the next trillion euro-plus budget and migration. In truth, no such separation exists: driven by nationalists and a political mainstream unable to offer any alternative but to implement their ideas, the next budget is in fact all about migration.
This strategy contained within the budget will get the approval of Hilary Clinton, who recently told the Guardian that ‘Europe needs to get a handle on…
Content Type: Advocacy
Image source
The EU extensively bolsters the surveillance and border control capabilities of governments around the world – and is set to dramatically increase such support. Below, we look at how some of these existing funds are being used, how their proposed expansion will undermine people’s privacy around the world for decades to come, and what needs to be done about it.
Migration has dominated the recent EU agenda and will once again be central during this week’s European Council meeting…
Content Type: Long Read
Privacy International’s new report shows how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies. Driven by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, peoples’ rights, and the rule of law.To ensure that surveillance powers used by governments are used to protect rather than endanger people, it is essential that the public,…
Content Type: Long Read
Privacy International (PI) has today released a new report, 'Teach 'em to Phish: State Sponsors of Surveillance', showing how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies.
Spurred by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, rights, and the rule of law.
As well as providing a background to the issue, the report…
Content Type: Advocacy
A new Privacy International report, based on an international collaborative investigation carried out by 40 NGOs in 42 countries, has found alarming weaknesses in the oversight arrangements that are supposed to govern the sharing of intelligence between state intelligence agencies. Privacy International urges governments to enact urgent reforms and improve public understanding about the scope of intelligence sharing and the safeguards and oversight currently in place.
Content Type: Report
‘Secret Global Surveillance Networks’ is a major PI report, based on an unprecedented international collaborative investigation carried out by 40 NGOs in 42 countries.
Our research shows that, globally, the sharing of intelligence is alarmingly under-regulated, opening the door to human rights abuses. Intelligence sharing has evolved dramatically with the rise of new surveillance technologies, enabling governments to collect, store, and share vast troves of personal information, including data…
Content Type: Long Read
This piece was originally published in Lawfare in April 2018
The United States is party to a number of international intelligence sharing arrangements—one of the most prominent being the so-called “Five Eyes” alliance. Born from spying arrangements forged during World War II, the Five Eyes alliance facilitates the sharing of signals intelligence among the U.S., the U.K., Australia, Canada and New Zealand. The Five Eyes countries agree to exchange by default all signals intelligence…
Content Type: Explainer
What is the Global Surveillance Industry?
Today, a global industry consisting of hundreds of companies develops and sells surveillance technology to government agencies around the world. Together, these companies sell a wide range of systems used to identify, track, and monitor individuals and their communications for spying and policing purposes. The advanced powers available to the best equipped spy agencies in the world are being traded around the world. It is a…
Content Type: Advocacy
Privacy International has responded to the European Commission’s consultation on the interoperability of EU information systems for borders and security.
The Commission is currently looking at ways in which various border control and policing EU databases and IT systems can be connected to share and exchange more data.
The plans raise a number of concerns as highlighted by Privacy International in our response. These relate to significant potential harms associated with…
Content Type: News & Analysis
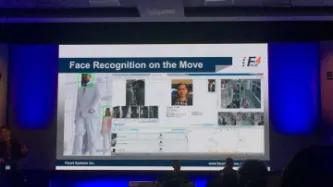
From unlocking a smartphone or getting through an airport, the use of an iris, fingerprint, or your face for identity verification is already widespread, and the market for it is set to rocket. While the technology is not new, its capability and uses are. As people, biometrics offers us much, but risks ultimately only serve data-hungry industries and government agencies: in the name of efficiency and security, it has the potential to bring chaos and vulnerability.
Obtaining reliable…
Content Type: News & Analysis
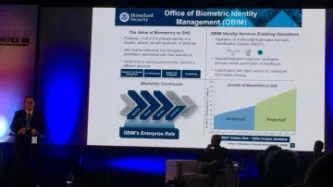
The United States Department of Homeland Security (DHS) has contracted one of the world’s largest arms companies to manage a huge expansion of its biometric surveillance programme.
According to a presentation seen by Privacy International, the new system, known as Homeland Advanced Recognition Technology (HART), will scoop up a whopping 180 million new biometric transactions per year by 2022.
It will replace the Automated Biometric Identification System (IDENT), which currently stores…
Content Type: Report
The report “The Global Surveillance Industry" charts the development of the industry since the earliest reports in the 70s that wiretapping equipment was being exported by Western countries and used by authoritarian regimes. It provides an accessible introduction into the types of the technologies currently on offer, and uses a combination of export data, company data and analysis of surveillance technologies to assess the current industry. The report presents an analysis of the…
Content Type: Report
Over a dozen international companies are supplying powerful communications surveillance technology in Colombia. Privacy International examines the actors across the world involved in facilitating state surveillance.
The report is available in English and Spanish.
Content Type: Report
“Private Interests: Monitoring Central Asia” is a 96-page report detailing its findings from an extensive investigation into electronic surveillance technologies in Kazakhstan, Kyrgyzstan, Tajikistan, Turkmenistan, and Uzbekistan.
The report brings together the findings of PI's team of investigative researchers, consultants, and technical, legal and policy experts, and is the outcome of consultations with confidential sources, regional experts, individuals who have been targeted by…