Advanced Search
Content Type: Video
PI's Reproductive Rights and Privacy Project speaks with Ruth Taylor, the CEO of the UK-based charity Abortion Support Network about how opposition groups are using misinformation to delay people from accessing safe abortion care.
More here: https://privacyinternational.org/taxonomy/term/677
Content Type: Key Resources
Tech companies, governments, and international agencies have all announced measures to help contain the spread of the COVID-19 virus.Some of these measures impose severe restrictions on people’s freedoms, including to their privacy and other human rights. Unprecedented levels of surveillance, data exploitation, and misinformation are being tested across the world.Many of those measures are based on extraordinary powers, only to be used temporarily in emergencies. Others use exemptions in data…
Content Type: Report
The changes discussed in this article are based on a second analysis performed in late November, 3 months after the original study Your Mental Health is for Sale and following the exact same methodology. All data collected can be found at the bottom of this page.
Change is possible
Back in September 2019 we published the report Your Mental Health is for Sale exposing how a majority of the top websites related to mental health in France, Germany and the UK share data for advertising purposes.…
Content Type: Long Read
We are excited to spotlight our Reproductive Rights and Privacy Project!
The Project is focused on researching and exposing organisations that collect and exploit the information of those seeking to exercise their reproductive rights. Working together with PI partners, other international grassroots organisations and NGOs, PI is researching and advocating against this data exploitation.
So, what are reproductive rights?
Sexual and reproductive rights, which are contained within Economic,…
Content Type: News & Analysis
Send a Freedom of Information Request to your local police for to see if they are using cloud extraction here.On 12 December 2018 a member of Lancashire Police Department UK told viewers of a Cellebrite webinar that they were using Cellebrite's Cloud Analyser to obtain cloud based 'evidence'. In response to a Freedom of Information request Hampshire Constabulary told Privacy International they were using Cellebrite Cloud Analyser. They are not alone. In Cellebrite's…
Content Type: News & Analysis
Cloud extraction allows law enforcement agencies to take huge amounts of your data from the Cloud via a legal back door. If law enforcement seize your phone or take it from a victim of crime, they can extract tokens or passwords from the device which lets them get access to data from apps such as Uber, Instagram, Slack, Gmail, Alexa and WhatsApp.
In so doing, law enforcement agencies can avoid official channels through cloud companies such as Google, Apple…
Content Type: Long Read
Mobile phones remain the most frequently used and most important digital source for law enforcement investigations. Yet it is not just what is physically stored on the phone that law enforcement are after, but what can be accessed from it, primarily data stored in the Cloud.
Cellebrite, a prominent vendor of surveillance technology used to extract data from mobile phones, notes in its Annual Trend Survey that in approximately half of all investigations, cloud data ‘appears’ and that…
Content Type: Long Read
Following a series of FOI requests from Privacy International and other organisations, the Department of Health and Social Care has now released its contract with Amazon, regarding the use of NHS content by Alexa, Amazon’s virtual assistant. The content of the contract is to a big extent redacted, and we contest the Department of Health’s take on the notion of public interest.
Remember when in July this year the UK government announced a partnership with Amazon so that people would now…
Content Type: Long Read
Miguel Morachimo, Executive Director of Hiperderecho. Hiperderecho is a non-profit Peruvian organisation dedicated to facilitating public understanding and promoting respect for rights and freedoms in digital environments.The original version of this article was published in Spanish on Hiperderecho's website.Where does our feeling of insecurity come from? As we walk around our cities, we are being observed by security cameras most of the time. Our daily movement, call logs, and internet…
Content Type: Long Read
Sitting on the ground inside an unadorned courtyard in Koira Tegui, one of Niamey’s most popular districts, Halimatou Hamadou shows a copy of what, she’s been told, is a certificate of birth.
The 33 year old woman, who’s unable to read and write, received it days earlier during a crowded public ceremony at a nearby primary school.
“It’s my first document ever,'' she says, with surprise.
Thanks to the paper, she’ll be able to take part in a crucial passage for the future of Niger: the…
Content Type: Long Read
The pressing need to fix our cybersecurity (mis)understandings
Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being different concepts, the confusion between them and the broad application of criminal statutes is still leading to the criminalise legitimate behaviour.
All of this represents a sizable challenge…
Content Type: Long Read
This research is the result of a collaboration between Grace Tillyard, a doctoral researcher in the Media, Communications and Cultural Studies department at Goldsmiths College, London, and Privacy International.
Social Protection Systems in the Digital Age
In the digital age, governments across the world are building technologically integrated programmes to allow citizens to access welfare payments. While smart and digital technologies hold the potential to streamline administrative…
Content Type: Long Read
[Photo credit: Images Money]
The global counter-terrorism agenda is driven by a group of powerful governments and industry with a vested political and economic interest in pushing for security solutions that increasingly rely on surveillance technologies at the expenses of human rights.
To facilitate the adoption of these measures, a plethora of bodies, groups and networks of governments and other interested private stakeholders develop norms, standards and ‘good practices’ which often end up…
Content Type: Long Read
In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone…
Content Type: Long Read
Photo by Nadine Shaabana on Unsplash
Digital identity providers
Around the world, we are seeing the growth of digital IDs, and companies looking to offer ways for people to prove their identity online and off. The UK is no exception; indeed, the trade body for the UK tech industry is calling for the development of a “digital identity ecosystem”, with private companies providing a key role. Having a role for private companies in this sector is not necessarily a problem: after all, …
Content Type: Long Read
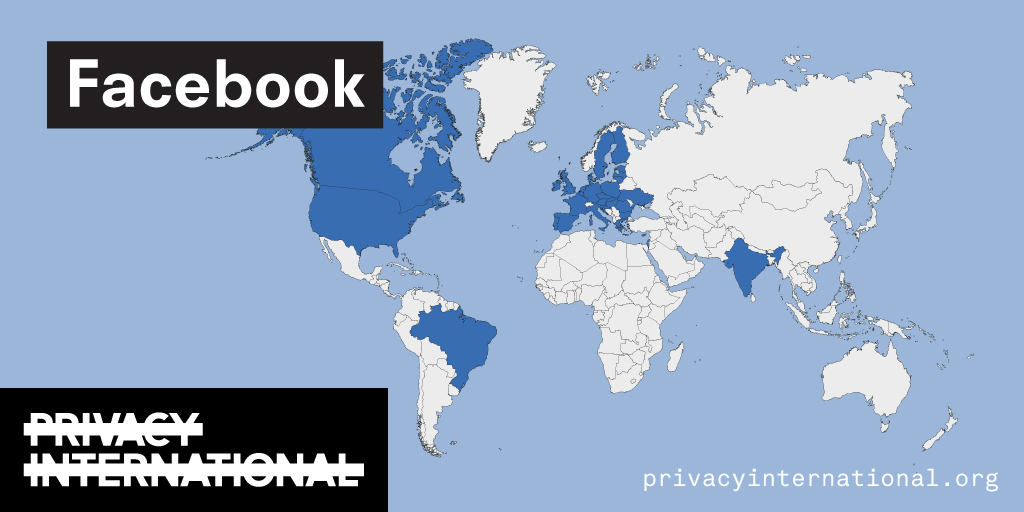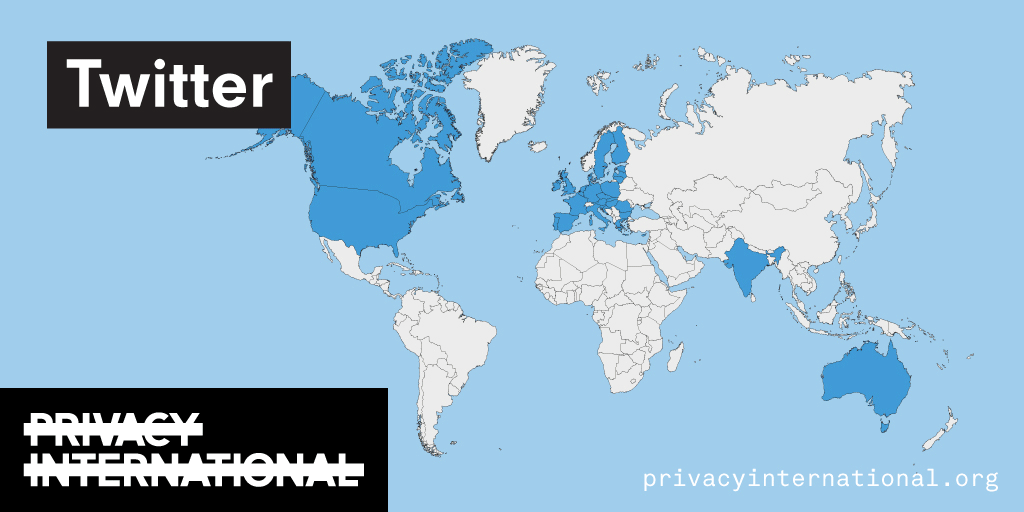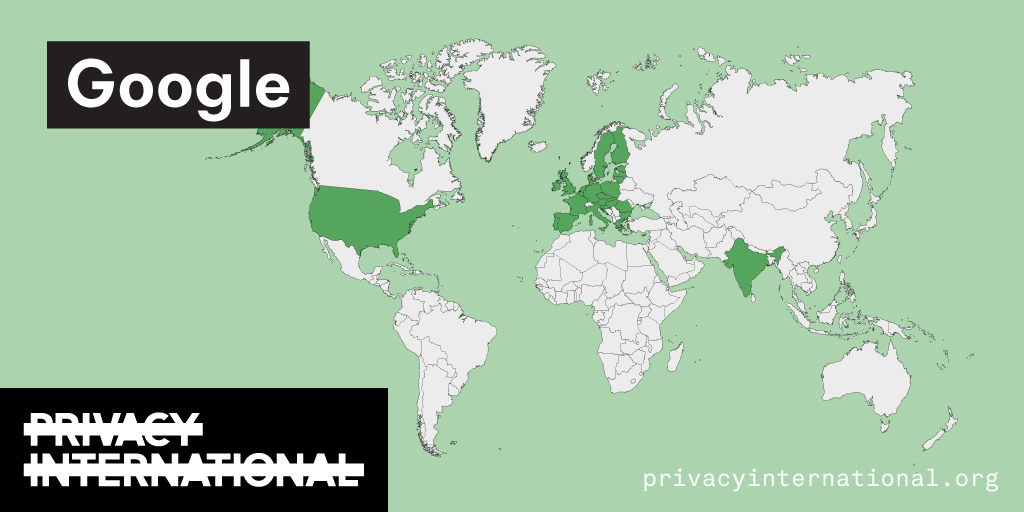
An analysis of what Facebook, Google, and Twitter have done to provide users with political ad transparency as of September 2019. Our full analysis is linked below.
Recently the role of social media and search platforms in political campaigning and elections has come under scrutiny. Concerns range from the spread of disinformation, to profiling of users without their knowledge, to micro-targeting of users with tailored messages, to interference by foreign entities, and more. Significant…
Content Type: Long Read
Content Type: Report
In September 2019, Privacy International filed 10 access to documents requests to EU bodies regarding the transfer of surveillance capabilities to non-EU countries. The requests seek documents providing information on the transfer of personal data, surveillance technology, training, financing, and legislation to non-EU countries. The requests were submitted to:
Frontex
Europol
The European Union Agency for Law Enforcement Training
The Directorate-General for Economic and…
Content Type: Long Read
Photo: Francesco Bellina
Driven by the need to never again allow organised mass murder of the type inflicted during the Second World War, the European Union has brought its citizens unprecedented levels of peace underpinned by fundamental rights and freedoms.
It plays an instrumental role in protecting people’s privacy around the world; its data protection regulation sets the bar globally, while its courts have been at the forefront of challenges to unlawful government surveillance…
Content Type: Long Read
We found this image here.
Using Facebook, Google, and Twitter’s ad libraries, PI has tried to understand how political ads are targeted in the UK. This information – which should be very clear on political ads – is instead being squirreled away under multiple clicks and confusing headings.
Importantly, in most countries around the world, users cannot understand why they’re being targeted with political ads on these platforms at all. This is because Facebook, Google, and Twitter have taken…
Content Type: Report
“...a mobile device is now a huge repository of sensitive data, which could provide a wealth of information about its owner. This has in turn led to the evolution of mobile device forensics, a branch of digital forensics, which deals with retrieving data from a mobile device.”
The situation in Scotland regarding the use of mobile phone extraction has come a long way since the secret trials were exposed. The inquiry by the Justice Sub-Committee, commenced on 10 May 2018, has brought much…
Content Type: Long Read
In December 2018, Privacy international exposed the dubious practices of some of the most popular apps in the world.Out of the 36 apps we tested, we found that 61% automatically transfer data to Facebook the moment a user opens the app. This happens whether the user has a Facebook account or not, and whether they are logged into Facebook or not. We also found that some of those apps routinely send Facebook incredibly detailed and sometimes sensitive personal data. Again, it didn’t matter if…
Content Type: Long Read
A new study by Privacy International reveals how popular websites about depression in France, Germany and the UK share user data with advertisers, data brokers and large tech companies, while some depression test websites leak answers and test results with third parties. The findings raise serious concerns about compliance with European data protection and privacy laws.
This article is part of a research led by Privacy International on mental health websites and tracking. Read our…
Content Type: Report
The full report of Privacy International's study on how popular websites about depression in France, Germany and the UK share user data with advertisers, data brokers and large tech companies, while some depression test websites leak answers and test results with third parties. The findings raise serious concerns about compliance with European data protection and privacy laws.
Content Type: Long Read
It is common ground that bulk collection of content would be a deprivation of the right to privacy. That is an inexcusable or unjustifiable step too far. Repeatedly the Government whether in litigation or legislating, has emphasised that they are not taking content in bulk. Content is the forbidden ground.
This has resulted in the Government seeking to explain, for example, what parts of an email would constitute content and meta data. Within the Investigatory Powers Act it has led to the…
Content Type: Report
To develop our framework for researching and challenging problematic aspects of social benefits systems, we sought to assemble a set of readings to provide greater context for understanding the history of surveillance and social benefits systems, the role social benefits systems play in increasing surveillance of particular communities, how to challenge problematic aspects of such systems, and how to conceive of affirmative solutions for what truly equitable and just social protection could…