Search
Content type: News & Analysis
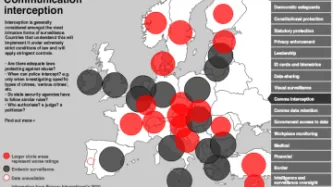
We have been fighting for transparency and stronger regulation of the use of IMSI catchers by law enforcement in the UK since 2016. The UK police forces have been very secretive about the use of IMSI catchers – maintaining a strict “neither confirm nor deny” (NCND) policy. In our efforts to seek greater clarity we wrote to the UK body which monitors the use of covert investigatory powers, the Investigatory Powers Commissioner’s Office (IPCO), asking the Commissioner to revisit this…
Content type: Explainer
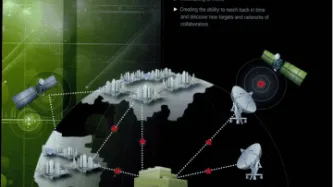
What is an IMSI catcher?
‘IMSI’ stands for ‘international mobile subscriber identity’, a number unique to your SIM card. IMSI catchers are also known as ‘Stingrays’.
An ‘IMSI catcher’ is a device that locates and then tracks all mobile phones that are connected to a phone network in its vicinity, by ‘catching’ the unique IMSI number.
It does this by pretending to be a mobile phone tower, tricking mobile phones nearby to connect to it, enabling it to then intercept the data from that phone…
Content type: Long Read
Tucked away in a discrete side street in Hungary’s capital, the European Union Agency for Law Enforcement Training (CEPOL) has since 2006 operated as an official EU agency responsible for developing, implementing, and coordinating training for law enforcement officials from across EU and non-EU countries.
Providing training to some 29,000 officials in 2018 alone, it has seen its budget rocket from €5 million in 2006 to over €9.3 million in 2019, and offers courses in everything from…
Content type: Long Read
Imagine that every time you want to attend a march, religious event, political meeting, protest, or public rally, you must share deeply personal information with police and intelligence agencies, even when they have no reason to suspect you of wrongdoing.
First, you need to go to the police to register; have your photo taken for a biometric database; share the contacts of your family, friends, and colleagues; disclose your finances, health records, lifestyle choices, relationship status, and…
Content type: Long Read
The Privacy International Network is celebrating Data Privacy Week, where we’ll be talking about how trends in surveillance and data exploitation are increasingly affecting our right to privacy. Join the conversation on Twitter using #dataprivacyweek.
In the era of smart cities, the gap between the internet and the so-called physical world is closing. Gone are the days, when the internet was limited to your activities behind a desktop screen, when nobody knew you were a dog.
Today, the…
Content type: News & Analysis
In order to uphold the law and keep us safe, the police can seriously interfere with a range of fundamental human rights. And so transparency and public scrutiny of their actions are essential to protect against misconduct and abuse.
So why is the National Police Chiefs’ Council (NPCC) now permitted to operate in secret?
We all have the right to seek information from most public bodies – including the police – under the Freedom of Information Act (FOIA) 2000. When the law was first…
Content type: Explainer
Phone networks are divided between two networks: the physical and the mobile. The physical runs on the Public Switched Telephone Network (PSTN) that serves your home phone. Mobile networks are dominant in the age of communication and are used to relay mobile communications to the PSTN. The most prominent mobile networks are GSM networks (Global System for Mobile communications) and are what we use everyday to communicate with one another. Another system is known as CDMA (Code Division Multiple…
Content type: Explainer
Video surveillance technologies are deployed in public and private areas for monitoring purposes. Closed-circuit television (CCTV)– a connected network of stationary and mobile video cameras– is increasingly used in public areas, private businesses and public institutions such as schools and hospitals. Systems incorporating video surveillance technologies have far greater powers than simply what the camera sees. Biometric technologies use the transmitted video to profile, sort and identify…
Content type: News & Analysis
Al Jazeera recently published an investigation into the shadowy trade of communications surveillance technologies. Their undercover reporter revealed four companies offering to illegally sell highly intrusive surveillance technologies to the governments of South Sudan and Iran, both of which are subject to extensive international sanctions. In the film, the four companies – two Italian, one Turkish and one Chinese – show themselves eager to employ workarounds, third parties, and shell…
Content type: Long Read
European Court of Human Rights Intervention
On 15 September 2017, Privacy International filed an intervention to the European Court of Human Rights in Association Confraternelle de la Presse Judiciare and 11 Other Applications v. France. This case challenges various surveillance powers authorised under the French Intelligence Act of 24 July 2015 as incompatible with Articles 8 and 10 of the European Convention on Human Rights, which respectively protect the right to privacy…
Content type: Long Read
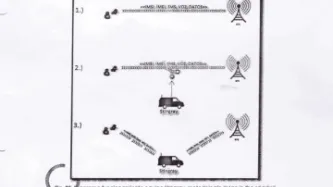
The use of IMSI catchers[1] to arrest individuals is rarely documented — as IMSI catchers are used secretively in most countries. The arrest of Colombian drug lord Henry López Londoño in Argentina is therefore a rare opportunity to understand both how IMSI catchers are used, and also the complexity of their extraterritorial use.
In October 2012, Londoño — also known as Mi Sangre (“My Blood”) — was arrested in Argentina. His arrest was the result of cooperation between the Dirección de…
Content type: Long Read
In July 2015, representatives of a private company met in a parking lot in Pretoria, South Africa to sell phone tapping technology to an interested private buyer. What they did not know was that this buyer was a police officer. The police had been tipped off that the company was looking to offload the surveillance technology, an IMSI catcher, to anyone who would buy it. It is illegal to operate such surveillance technology as a private citizen in South Africa, and illegal to buy…
Content type: Long Read
Privacy International’s case on Bulk Personal Datasets and Bulk Communications Data comes to a head with a four-day hearing in the Investigatory Powers Tribunal which commenced on 26 July 2016.
The litigation has brought to light significant revelations about the use of section 94 of the 1984 Telecommunications Act to obtain bulk communications data.
Large amounts of disclosure have shed new light on this hitherto secret power and explained confusing aspects of the Government’s Response to…
Content type: Long Read
This guest piece was written by Jessamine Pacis of the Foundation for Media Alternatives. It does not necessarily reflect the views or position of Privacy International.
Introduction
With a history immersed in years of colonialism and tainted by martial law, Philippine society is no stranger to surveillance. Even now, tales of past regimes tracking their citizens’ every move find their way into people’s everyday conversations. This, for the most part, has kept Filipinos…
Content type: News & Analysis
Over a dozen international companies are supplying powerful communications surveillance technology in Colombia, according to a Privacy International investigation released today featuring original documentation. Over the past few decades, companies primarily from Israel, the US, and the UK have worked with Colombian partners to expand the Government's surveillance capacities. This is despite evidence that the Government is undertaking unlawful surveillance of Colombians.
The…
Content type: Press release
The release of a new report by Privacy International exposes Colombia's intelligence agencies' previously unknown history of developing communications surveillance capabilities outside of lawful authority.
The report “Shadow State: Surveillance law and order in Colombia” reveals, via previously unreleased documents, the Colombian police agencies' and intelligence services' long history developing surveillance systems. Rather than building a well-regulated system of surveillance after Colombia…
Content type: News & Analysis
Here are eight things we have learned from this week's hack of some 400GB of internal company material and correspondence from Italian surveillance company Hacking Team.
The Citizen Lab was right
The Citizen Lab, who in 2014 identified some 21 countries that are potential customers of Hacking Team, were right about all of them. A 2015 report stated that there was likely to be more. In fact, at least 45 countries are purchasers of Hacking Team's…
Content type: News & Analysis
There is a common practice within the surveillance industry that makes the already murky market even harder to track: collaborating companies.
Within Privacy International's Surveillance Industry Index there are 83 documents detailing collaborations between companies involved in developing and selling surveillance technologies. These documents represent a variety of relationships – some are friendly companies, others advertise corporate partners, and some present themselves as a distributor of…
Content type: News & Analysis
Late last year, the newly-elected government of Indonesia began to take steps which are almost unheard of today: reforming government communications surveillance powers.
The much-needed development, on the back of the victory of President Joko Widodo, comes at a critical moment in the country's history as the relationships that Indonesians have with technology are changing and growing rapidly. A recent poll revealed that Indonesians consider technology to have had a mostly…
Content type: News & Analysis
Thousands of innocent people in London have had their communications spied on and collected through the use of invasive mobile phone surveillance technology, called IMSI Catchers, according to a recent report by the Times.
IMSI Catchers are no longer, and have not been for a while, a law enforcement secret. They have been featured crime dramas like the Wire and in movies such as Zero Dark Thirty. For years, the German Parliament has publicly received the number of IMSI Catcher…
Content type: News & Analysis
For some time now, Gamma International has been criticised for exporting dangerous surveillance technologies from the UK to repressive regimes. Now, we are learning that the company is taking its show on the road, as recent reports have said that Gamma are now attempting to export its products, including the spyware FinFisher, out of Switzerland.
With sales premises registered at a site just outside the Swiss capital Bern, Gamma has now applied to the Swiss Secretariat for…
Content type: News & Analysis
In a landmark report, the United Nations today has broken its long-held silence about the threat that State surveillance poses to the enjoyment of the right to privacy.
The report is clear: State surveillance of communications is ubiquitous, and such surveillance severely undermines citizens’ ability to enjoy a private life, freely express themselves and enjoy their other fundamental human rights. Presented today at the UN Human Rights Council session in Geneva, the report marks…
Content type: News & Analysis
Communications surveillance is one of the most significant threats to personal privacy posed by the state. This is why many statements of fundamental rights across the world give special regard to the privacy of communications. For example, the Universal Declaration of Human Rights states in Article 12:
No one should be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks on his honour or reputation. Everyone has the right to the protection of…