Search
Content type: Advocacy
The feedback in this document was submitted as part of an open Request for Information (RFI) process regarding the document created by The IEEE Global Initiative for Ethical Considerations in Artificial Intelligence and Autonomous Systems ("The IEEE Global Initiative") titled, Ethically Aligned Design: A Vision for Prioritizing Human Wellbeing with Artificial Intelligence and Autonomous Systems.
Content type: News & Analysis
This comment by Privacy International Executive Director Gus Hosein ran in Ciper Chile on 19 May, 2014
The economic benefits of being included in the Visa Waiver Program (VWP) with the US are remarkable. The ease of travel allows for the exchange of tourism between the countries, and other new economic opportunities through reduced friction caused by visa approval processes. Nonetheless, this program is often used as a mechanism to seek more data on the citizenry of participating…
Content type: News & Analysis
The following article written by Carly Nyst, Privacy International's Legal Director, originially appeared on the Future Tense blog on Slate:
The news that the CIA is no longer using vaccination programs as a front for spying operations may come as a relief to many humanitarian workers. Yet their fears should not be completely assuaged, because the CIA’s activities—which undoubtedly threatened the safety of humanitarian workers and those they seek to help—pale in comparison to the…
Content type: News & Analysis
17 June 2013
Below is an excerpt of an article that recently appeared in Melbourne, Australia's The Age, written by Carly Nyst, Head of International Advocacy at Privacy International:
"Mass surveillance of a country's citizens by its government can no longer be said to be the preserve of authoritarian and dictatorial states.
The publication last week by The Guardian of classified National Security Agency documents has exposed the extent of surveillance by the US government, throwing…
Content type: News & Analysis
2nd March 2015
UPDATE: Since the original publication of this post in early February, over fifty additional national and international human rights organisations have joined us and called on all governments to support the creation of a UN Special Rapporteur on the Right to Privacy.
This recent wave of support, bringing the total number up to 63, comes at a critical time. As the UN Human Rights Council begins its 28th session in Geneva today, the…
Content type: News & Analysis
30 May 2017
These days it seems that no election can go by without fears of foul play, whether it is the hacking of a candidate or party’s e-mail or the spread of fake news and other misinformation to support or discredit a particular party or politician.
Often the finger is pointed at shady individuals or rogue governments , and invariably the accusations are met with flat denial. But the accusations have attracted significant attention from governments and companies alike, with reactions…
Content type: News & Analysis
The Supreme Court has ruled that there is a fundamental right to privacy under the Indian constitution, establishing that “The right to privacy is protected as an intrinsic part of the right to life and personal liberty”. This was a unanimous ruling by a bench of nine supreme court justices, who heard the case following a decision in 2015 over whether the controversial Aadhaar biometric identity scheme was constitutional.
The judgment is clear: privacy and human dignity are intrinsically…
Content type: News & Analysis
The following op-ed appeared in openDemocracy, written by Edin Omanovic, Research Officer at Privacy International:
It's not surprising that some of the states in Central Asia spy on people. Authoritarianism across the world relies on the intrusion into, and lack thereof, of a private sphere. From the KGB to their modern incarnations, the autocracies in the region continue to rely on state surveillance and other entrenched means of political control to stay in power.
New technologies and…
Content type: News & Analysis
The following appeared in the Daily Telegraph, and was written by Carly Nyst, Legal Director of Privacy International:
"Robert Hannigan, the new head of GCHQ, announced his arrival this week with a call for “greater co-operation” with security forces by tech companies. Hannigan’s article in the Financial Times illustrated vividly the destructive ideology that has driven the infiltration by the British and American intelligence agencies into every aspects of the digital realm – an…
Content type: Case Study
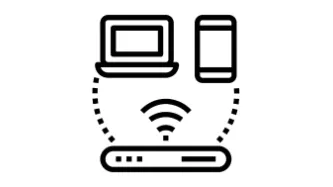
Invisible and insecure infrastructure is facilitating data exploitation
Many technologies, including those that are critical to our day-to-day lives do not protect our privacy or security. One reason for this is that the standards which govern our modern internet infrastructure do not prioritise security which is imperative to protect privacy.
What happened?
An example of this is Wi-Fi, which is now on its sixth major revision (802.11ad). Wi-Fi was always designed to be a verbose in…
Content type: News & Analysis
Al Jazeera recently published an investigation into the shadowy trade of communications surveillance technologies. Their undercover reporter revealed four companies offering to illegally sell highly intrusive surveillance technologies to the governments of South Sudan and Iran, both of which are subject to extensive international sanctions. In the film, the four companies – two Italian, one Turkish and one Chinese – show themselves eager to employ workarounds, third parties, and shell…
Content type: Press release
The release of a new report by Privacy International exposes Colombia's intelligence agencies' previously unknown history of developing communications surveillance capabilities outside of lawful authority.
The report “Shadow State: Surveillance law and order in Colombia” reveals, via previously unreleased documents, the Colombian police agencies' and intelligence services' long history developing surveillance systems. Rather than building a well-regulated system of surveillance after Colombia…
Content type: Advocacy
Este informe es presentado por la Asociación por los Derechos Civiles (ADC) y Privacy International (PI). La Asociación por los Derechos Civiles (ADC) es una organización no gubernamental, sin nes de lucro, ubicada en Buenos Aires, que promueve los derechos civiles y sociales en Argentina y otros países latinoamericanos. Fue fundada en 1995 con el objetivo de fortalecer una cultura jurídica e institucional que garantice los derechos fundamentales de la gente, basado en el respeto a la…
Content type: News & Analysis
Privacy International has today written to government ministers, members of the opposition, and oversight bodies reaffirming its call for the UK government to reveal secret intelligence sharing arrangements with the United States.
The original UKUSA agreement — drafted shortly after World War II — allows UK and US agencies to share, by default, any raw intelligence, collection equipment, decryption techniques, and translated documents.
Current arrangements also allow US intelligence agencies…
Content type: News & Analysis
The elections in our midst here, there, and everywhere are increasingly resulting in governments who introduce policies that result in leaps backwards for dignity, equality, civil liberties, and the rule of law. Whether it is Poland or the Philippines, governments are overriding essential safeguards.
This week Britain’s proposed surveillance legislation took another step toward normalising mass surveillance. The United States of America has long promoted mass surveillance and maintains its…
Content type: News & Analysis
This piece originally appeared in Open Democracy here.
As the UK Parliament returns from its summer break, everyone’s back to talking about Brexit. But there’s another policy of existential significance to our democracy that we really need to be talking about. I refer here to the innocuously named ‘Investigatory Powers Bill’. The House of Lords have been debating the ‘bulk powers’ — what we would call the mass surveillance measures — of the Bill over the recent days. We are literally…
Content type: Examples
In 2015, IBM began testing its i2 Enterprise Insight Analysis software to see if it could pick out terrorists, distinguish genuine refugees from imposters carrying fake passports, and perhaps predict bomb attacks. Using a scoring system based on several data sources and a hypothetical scenario, IBM tested the system on a fictional list of passport-carrying refugees. The score is meant to act as a single piece of data to flag individuals for further scrutiny using additional…
Content type: Press release
17 November 2015
A new Privacy International investigation reveals Microsoft's complicity in a serious case of Government persecution in Thailand. It is a shocking example of how Western companies not only work with governments that fall considerably short of international human rights standards, but can actually facilitate abuses of human rights.
In early 2014, a Thai stockbroker, Katha Pachachirayapong, was accused by the Government of spreading rumours on the ill-health of King…
Content type: News & Analysis
Below is the introduction to Privacy International's 2017 International Women's Day report, which highlights the recent work of the PI Network on privacy, surveillance, and gender.
Many of the challenges at the intersection of women’s rights and technology as it relates to privacy and surveillance, come down to control. Such challenges have come sharply into focus as societies trend toward surveillance by default and foster data exploitative ecosystem.
And whilst control, in the context of…
Content type: Examples
In 2017, the New York Times discovered that Uber had a secret internal programme known as "Greyball", which used data collected from the Uber app and other techniques to identify and bar regulators and officials from using its service. As the company expanded into new areas, its standard practice was to open up and begin offering rides without seeking regulatory approval first. The company used Greyball to prevent regulators from building a case against the company in areas where…
Content type: News & Analysis
7 July 2017
War profiteers are finding the data business easy going. The have wielded their unwarranted influence and applied their business model of causing and then profiting from insecurity and applied it to the digital age; the results have been more profit for them and less liberty for you.
When a politician riles against an evil tech giant for providing ‘safe spaces’ online, it’s a political distraction. The real battle for your data is being fought between the emergent tech…
Content type: Examples
In 2015 Hong Kong's Face of Litter campaign used DNA samples taken from street litter and collected from volunteers to create facial images that were then posted on billboards across the city. The campaign, conceived by PR firm Ogilvy & Mather and organised by online magazine Ecozine and the Nature Conservancy, was intended to give a face to anonymous Hong Kong litterbugs and raise awareness of the extent of littering in the city and encourage people to…
Content type: News & Analysis
18 October 2013
The following is an excerpt from an article written that originally was published by IFEX, and is written by Carly Nyst, Head of International Advocacy at Privacy International:
The reality of the modern world is that governments – both of our own countries, and of foreign states – have greater capabilities to carry out invasive surveillance of citizens, no matter where they reside or what flag they pledge to. And caught in the cross-fire of the expanding surveillance…
Content type: Examples
For some months in 2017, in one of a series of high-risk missteps, Uber violated Apple's privacy guidelines by tagging and identifying iPhones even after their users had deleted Uber's app. When Apple discovered the deception, CEO Tim Cook told Uber CEO Travis Kalanick to cease the practice or face having the Uber app barred from the App Store.
External Link to Story
https://www.nytimes.com/2017/04/23/technology/travis-kalabnick-pushes-uber-and-himself-to-the-precipice.html
Content type: News & Analysis
14th August 2017
We found the image here.
We work to collect the minimum amount of data that we need from you to do our jobs within the resources we have, and to protect and use that data in an ethical manner. We are expanding the ways we engage with our supporters, by rebuilding our technical services to ensure that we continue to live up to that commitment.
Here we explain what data we have access to, what we collect, and how we work to protect your data. This piece is more explanatory…
Content type: News & Analysis
There are three good reasons why security is so hard for NGOs. First, we are afraid to speak about meaningful security. Second, we focus on the wrong areas of security and in turn spend money and prioritise the wrong things. Third, we struggle to separate the world we want from the worlds we build within our own organisations. At PI we have failed and struggled with each of these for over 20 years. Out of exhaustion, we decided to do something about it: we are building an open framework, a…
Content type: News & Analysis
Early on Wednesday morning the Prevention of Electronic Crimes Bill was approved by Pakistan’s National Assembly. The Bill, which is almost universally acknowledged as “controversial” had been criticised by opposition members, industry and civil society at numerous stages. Civil society organisations from around the world released two joint statements in April and December last year expressing their concerns. Despite the chorus of criticism, very little has changed in the Bill during its…
Content type: Press release
Key points
Privacy International has obtained previously unseen government documents that reveal British spy agency GCHQ collects social media information on potentially millions of people.
GCHQ collected and accesses this information by gaining access to private companies’ databases.
Letters obtained by Privacy International reveal that the body tasked with overseeing intelligence agencies’ activities (the Investigatory Powers Commissioner) was kept in the dark as UK intelligence…
Content type: Report
Financial services are changing, with technology being a key driver. It is affecting the nature of financial services, from credit and lending through to insurance, and even the future of money itself.
The field of fintech is where the attention and investment is flowing. Within it, new sources of data are being used by existing institutions and new entrants. They are using new forms of data analysis.
These changes are significant to this sector and the lives of people it serves. This…
Content type: Press release
In today’s latest hearing in our ongoing legal challenge against the collection of massive troves of our personal data by the UK intelligence agencies, shocking new evidence has emerged about GCHQ’s attempts to yet again avoid proper independent scrutiny for its deeply intrusive surveillance activities.
In a truly breath-taking exchange of letters between the Investigatory Powers Commissioner’s Office (“IPCO”) and the Director of Legal Affairs at GCHQ, it has emerged that GCHQ have…