Search
Content type: Examples
Hong Kong authorities seeking to ensure the complete removal of the popular pro-democracy protest song "Glory to Hong Kong" from search results got an injunction against Google after the technology giant refused to remove it without a court order. The authorities say in the writ that they are seeking to stop anyone with seditious intent from publishing or distributing the song in any media. After a hearing, the court denied the authorities' request.
https://www.scmp.com/news/hong-kong/politics…
Content type: Examples
Police have closely monitored the first protest in Hong Kong since 2020, limiting attendees to 100 and requiring them to wear number tags and submit their banners for prior inspection. Police also set up a cordon to keep protesters separated from the media. The protest opposed a land reclamation plan on the city's east side.
https://www.bbc.co.uk/news/world-asia-65080083
Publication: BBC
Writer: BBC
Publication date: 2023-03-26
Content type: Examples
Video footage shows that security agents linked to London mayor Sadiq Khan spied on the environmental activist group Green New Deal Rising and blocked members from participating in a public debate. Information about the campaigners and their plans appears to have been shared in advance between the Greater London Authority, the O2 venue, and ISG Commercial, which provides security services to the O2. The environmental group has been opposing the tunnel in progress linking the boroughs of…
Content type: Examples
London's Metropolitan Police announced it would use facial recognition to scan the crowds attending the May 2023 coronation of King Charles III. The hundreds of thousands of people expected to line the streets was an entirely new scale of use for the technology in Britain. Critics such as Liberty and Big Brother Watch opposed the usage, fearing the police would use it to chill protest, already under threat from recent UK legislation granting police new powers.
https://www.theguardian.com/uk-…
Content type: Examples
Human rights lawyers allege that during protests in March 2023 police arbitrarily arrested numerous protesters with the goal of chilling protests. In similar cases during the 2018 "yellow vest" protests, only 5,000 of 11,000 people arrested were eventually prosecuted, according to the government's own figures. The arrests are supported by laws including a prohibition on participating in crowds preparing acts of violence or that have the potential to trouble public order. During visits by…
Content type: Examples
In a case brought by NGOs before the 2023 May Day marches, administrative courts ruled that police may use drones to patrol the crowds and rejected the argument that the drones pose a serious attack to fundamental freedoms. However, a court in Rouen suspended parts of a decree that would have allowed police to use drones at a protest in Le Havre even though the judge agreed the drones would probably improve security.
https://www.rfi.fr/en/france/20230501-french-courts-uphold-use-of-police-…
Content type: News & Analysis
Privacy International (PI) is concerned by developments in Pakistan regarding the enactment of the Draft Personal Data Protection Bill, 2023 and the opaque process which will see the bill become law.
The Bill was published on 19 May 2023 by the Ministry of Information Technology and Telecommunication ('MITT'). However no open and inclusive consultation was open for comments to be submitted to the MITT. In a concerning development it was reported that the Bill was approved by the Federal…
Content type: Advocacy
We are responding to the UK Government's consultation to expand its powers around Technical Capabilities Notices and National Security Notices.
Background
Following Edward Snowden's revelations about the illegal and expansive secret powers of the US and UK intelligence agencies, the UK Government took the opportunity to, rather than reflect on what powers are proportionate in the modern era, to expand its arsenal of surveillance powers.
One of the powers it added was the ability to issue…
Content type: Video
Additional audio from The Guardian and from Channel 4 News via the Guardian
Links
What is Tempora?
Taking angle grinders to the Guardian's hard drives
PI's legal cases
The ACLU's case challenging upsteam surveillance
The White House review of the NSA post Snowden
Hear from Ed Snowden directly
Content type: Advocacy
Our submission focused on (1) the ways in which states are adopting data-intensive ID systems; (2) the adoption by national immigration enforcement agencies of other privacy-intrusive modes of surveillance and control, including tracking by way of 24/7 Global Positioning System (GPS) technology and mobile device data extraction; (3) how the intensification of border surveillance technologies facilitates further human rights violations; (4) the impact of border externalisation and transfer of…
Content type: Advocacy
On the 17 January 2023, the UK Home Secretary appointed Lord David Anderson KBE KC to carry out an independent review of the Investigatory Powers Act 2016.The Investigatory Powers Act 2016 provides a legal framework for the use of investigatory powers by the UK security and intelligence agencies, law enforcement and other relevant public bodies. These powers include the interception of communications; the retention and acquisition of communications data and; equipment interference for obtaining…
Content type: People
Karla currently leads Privacy International's Protecting People's Dignity strategic area, which is dedicated to strengthening frameworks and mechanisms that ensure individuals affected by exclusion, discrimination, and unlawful surveillance can safely and equitably access and enjoy their fundamental rights. Karla has extensive experience in the regulatory sector, having served as a Senior Legal Advisor at the Federal Telecommunications Institute of Mexico and as Head of the Office of…
Content type: Advocacy
This was submitted by PI and EFF for the sixth session of the Ad Hoc Committee, which is due to consider the text in August 2023.
Our submission covers provisions in the chapters related to procedural measures and law enforcement, as well as international cooperation of the proposed UN Cybercrime treaty (full title: Comprehensive international convention on countering the use of information and communications technologies for criminal purposes). We also provide general comments on Article 54…
Content type: Key Resources
Content type: Advocacy
In June 2023, we made a submission to the Human Rights Committee ahead of its 138th Session in relation to Colombia’s compliance with the International Covenant on Civil and Political Rights (ICCPR).
We called on the UN Human Rights Committee to make the following recommendations to Colombia:
The Electoral Law should ensure that the electoral register does not include personal data other than what is required to establish eligibility to vote. The law should define the minimum…
Content type: People
Julie is responsible for coordinating Privacy International’s global network of partner organisations. Privacy International works with civil society organisations from around the world to generate strategies to develop and sustain a global movement. Julie coordinates the joint research, advocacy, communication, campaigning and learning tactics with Privacy International’s partners in order to formulate new ways to demand change globally.
Before joining Privacy International, Julie worked at…
Content type: Long Read
Why does this decision matter?
Our complaint against Criteo formed part of a larger set of coordinated complaints we filed in 2018 against 7 data brokers (Acxiom, Oracle), AdTech companies (Criteo, Quantcast, Tapad), and credit referencing agencies (Equifax, Experian) with data protection authorities in France (CNIL), Ireland, (DPC) and the UK (ICO). The EU General Data Protection Regulation (GDPR) had recently come into force, and the AdTech industry was (and still is) a prime affront to the…
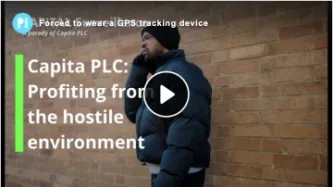
Content type: Video
Links
Send Capita an email
Find out more about the campaign
Watch the full video testimonies
Video 1
Video 2
Content type: Press release
La CNIL a aujourd'hui prononcé une sévère sanction contre Criteo, une des plus grandes sociétés françaises de pistage et publicité en ligne. Le montant de l'amende a été réduit de 60 à 40 millions d'euros depuis l'audience qui s'est tenue à la CNIL en Mars 2023, durant laquelle Criteo avait mis en avant son bénéfice net de 10 millions d'euros en 2022 pour plaider en faveur d'une réduction de sa peine. La CNIL semble avoir entendu ces arguments, mais a heureusement maintenu une amende…
Content type: Press release
French data regulator CNIL announced today a strong sanction against Criteo, one of the world's largest AdTech companies. Although close to the maximum GDPR fine, the amount of the fine was reduced from 60 to 40 million following a hearing at CNIL's offices in March 2023, during which Criteo pleaded for a reduced fine in light of its 10 million euros profit in 2022. CNIL seems to have acknowledged this argument but maintained a significant fine. This sanction follows a Privacy International…
Content type: Advocacy
Privacy International contributed to the UNSR's report by submitting information on the work we have done as well as our Network of partners as we’ve monitored and responded to developments associated with the use of data and technology in the health care sector by governments and companies.
Content type: Advocacy
Privacy International (PI) notes the Bureau’s text of the WHO convention, agreement or other international instrument on pandemic prevention, preparedness and response (“WHO CA+”).
PI has sought to closely follow and engage with the discussions leading up to the draft treaty, despite the significant limitations to civil society participation in the process. In February 2023, we intervened during the briefing organised by the INB bureau and published our comments on the zero draft of the WHO CA…
Content type: Advocacy
Background
In August 2022, Amazon announced that they had entered into a definitive merger agreement to acquire iRobot, a company that specialises in designing and building consumer robots. The transaction was formally notified to the European Commission on 1 June 2023, while the UK Competition and Markets Authority (CMA) has already launched an investigation into the transaction since April 2023.
We believe that this acquisition is likely to significantly impede effective competition in and…
Content type: People
Tom joined Privacy International as a Legal Officer in May 2023. His work primarily relates to the impact of big tech and new tech on privacy, in particular in relation to health, employment and data brokerage. Prior to PI, Tom has worked within the environmental law sector, at NGO ClientEarth and in the Secretariat of the UNECE Aarhus Convention, and on legislative processes at the Hansard Society for parliamentary democracy.His education includes a PhD in International Environmental and Human…
Content type: Key Resources