Advanced Search
Content Type: Report
Esta parte de "Las Claves para Mejorar la Protección de Datos" explica qué es la protección de datos, por qué se necesita y cómo trabajar estos temas. También describe por qué la protección de datos es esencial para el ejercicio del derecho a la privacidad.
Content Type: Long Read
The Sustainable Development Goals (SDGs) are the United Nations-led initiative to define the development agenda. Building on the eight Millennium Development Goals, the SDG’s 17 goals – and the 169 targets – serve as an opportunity to tackle many of the most pressing issues in the world today. The SDGs are also explicitly grounded in human rights. Goal 16 on “peace, justice, and sustainable institutions” aims to “Promote peaceful and inclusive societies for sustainable development, provide…
Content Type: News & Analysis
This post was written by William Marks, a former volunteer at Privacy International.
The right to privacy is central to the protection of human dignity, and supports and reinforces other rights, such as the right to freedom of expression and association. Privacy International, supported by the International Human Rights Clinic at Harvard Law School, recently submitted a joint stakeholder report to the United Nations Human Rights Council regarding New Zealand’s protection of the right to…
Content Type: News & Analysis
Around the world, from North America to Europe and Asia, governments are starting to roll out smart meters. While the technology promises increased energy efficiency through greater consumer control over energy consumption, smart meters also raise serious privacy concerns. Smart meters collect energy usage data at high frequencies - typically every five, fifteen or 30 minutes. That level of granularity reveals how much electricity is being used in a home and when, which in turn can paint an…
Content Type: News & Analysis
This month Brazil adopted a new data protection law, joining the ranks of more than 120 countries which have adopted such legislation, providing individuals with rights against the exploitation of their personal data. But after a veto from the Brazilian president, the law lacks an independent authority in charge of its application, which can severely undermine its impact.
When drafting data protection bills, one of the most important and often politically contentious issue tends to be their…
Content Type: Long Read
Privacy International’s new report shows how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies. Driven by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, peoples’ rights, and the rule of law.To ensure that surveillance powers used by governments are used to protect rather than endanger people, it is essential that the public,…
Content Type: Advocacy
This Universal Periodic Review stakeholder report is a submission by Privacy International presented to raise concerns regarding the situation of the violation of the right to privacy in New Zealand as part of the 32nd session of the Universal Periodic Review (UPR) Working Group.
Content Type: Long Read
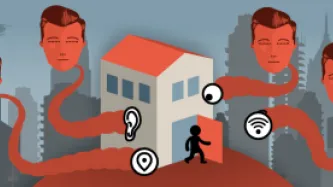
The idea of a “smart city” is primarily a marketing concept, used to sell data-intensive technologies under the pretext of improving the functioning of cities. This could include injecting ‘smart’ tech into delivering services, public safety, environmental monitoring, traffic control, among other possible applications.
One in particular aspect of smart cities has been consistently problematic: how these projects are used to boost law enforcement and policing under the guise of public safety.…
Content Type: Advocacy
We welcome the effort by the Pakistani Ministry of Information Technology and Telecommunications to regulate the processing of personal data in Pakistan, and take measures to guarantee the right to privacy as guaranteed under Article 14(1) of the Constitution: “[t]he dignity of man and, subject to law, the privacy of home, shall be inviolable.”
This legislative development is crucial and timely as Pakistan continues to embrace innovative governance initiatives and deploy data-intensive systems…
Content Type: News & Analysis
By Digital Rights Foundation, Pakistan
What is a safe city?
The answer to this question is not uniform; in fact it varies according to who you ask.
In a focus group conducted by Digital Rights Foundation in May of last year, consisting of women rights activists from across Pakistan, the answer meant imagining a city that was not only safe for women, in terms of their physical safety, but also welcoming for women and non-binary individuals in its architecture and facilities. Women expressed…
Content Type: Long Read
Creative Commons Photo Credit: Source
UPDATE: 30 July 2019
Privacy International has identified the following:
Two RAB officers received approval to travel to the USA in April 2019 for training on “Location Based Social Network Monitoring System Software for RAB Intelligence Wing”
Three RAB officers received approval to travel to Russia in August 2017 to participate in user training of “Backpack IMSI Catcher (2G, 3G, 4G)” paid for by Annex SW Engineering, a…
Content Type: News & Analysis
This piece originally appeared here.
Creative Commons Photo Credit: Source
Tech competition is being used to push a dangerous corporate agenda.
High-tech industries have become the new battlefield as the United States and China clash over tariffs and trade deficits. It’s a new truism that the two countries are locked in a race for dominance in artificial intelligence and that data could drive the outcome.
In this purported race for technological high ground, the argument often goes, China…
Content Type: Long Read
Creative Commons Photo Credit: Source
In the midst of continued widespread public outrage at the US government’s brutal ‘zero-tolerance’ policy around immigration – multiple data and analytics companies have quietly avoided answering questions about their role in feeding the US Immigration and Customs Enforcement (ICE) agency’s data backbone. These companies are bidding to work with an agency that has time and time again shown itself to be a brutal and problematic.
Privacy International…
Content Type: Examples
AirAsia engaged Palantir as a data science partner focused on “guest experience, inflight sales, route revenue, finance, security, flight operations, network planning, cargo, supply chain management, commercial and people development.”
Publication: AirAsia newsroom
Date: 8 August 2018
Content Type: News & Analysis
Our intervention comes on the back of mounting evidence that the South African state’s surveillance powers have been abused, and so-called “checks & balances” in RICA have failed to protect citizens’ constitutional right to privacy.
Among our core arguments are:
That people have a right to be notified when their communications have been intercepted so that they can take action when they believe their privacy has been unlawfully breached. Currently RICA prevents such notification, unlike…
Content Type: Press release
Privacy International, represented by Liberty, is challenging court decision allowing police to ‘neither confirm nor deny’ they hold certain information on IMSI catchers
Privacy rights organisation has fought for almost two years for public disclosure of records on how UK police purchase and use mobile phone surveillance technology
Privacy International has today filed an appeal challenging police forces’ refusal to disclose information on their purchase and use of IMSI catchers.
IMSI…
Content Type: News & Analysis
Photo was found here
This essay was published in The Sur International Journal of Human Rights, Issue 27, July 2018.
Abstract:
This essay focuses on elections in Kenya and analyses the use of technology and the exploitation of personal data in both the electoral process and campaigning. We only need to look to Kenya’s election history to understand why it is important. The 2007/2008 election resulted in violence that killed over 1,000 people and displaced over 600,000. The 2013 election was…
Content Type: Report
The Information Commissioner’s Office (ICO) recently issued a series of decisions in Privacy International’s long-running battle for information about UK police forces' acquisition of IMSI catchers. This case study provides an in-depth summary and analysis of this process.
We hope it is useful to both campaigners seeking greater transparency from policing bodies, and more widely to Freedom of Information campaigners who are trying to challenge 'neither confirm nor deny' responses to FOI…
Content Type: News & Analysis
Create Commons Photo Credit: Source
Privacy International has achieved an important victory for government transparency and information access rights. This victory stems from a long-running battle with the government to obtain information about the UK police’s purchase and use of IMSI catchers. The Information Commissioner’s Office (ICO) recently issued a series of decisions, which agree with Privacy International that police forces cannot rely on a position of “neither confirm nor deny” (NCND…
Content Type: Explainer
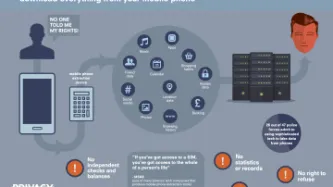
What is an IMSI catcher?
An IMSI catcher is an intrusive piece of technology that can be used to locate and track all mobile phones that are switched on in a certain area.
An IMSI catcher does this by ‘pretending’ to be a mobile phone tower - tricking your phone into connecting to the IMSI-catcher, and then revealing your personal details without your knowledge.
IMSI catchers are indiscriminate surveillance tools that could be used to track who attends a political demonstration or a…
Content Type: Advocacy
This report is presented by Red en Defensa de los Derechos Digitales (R3D) and Privacy International (PI). La Red en Defensa de los Derechos Digitales (R3D) is a non-governmental, non-profit organisation located in Mexico, dedicated to the defence of human rights in the digital environment. Privacy International (PI) is a non-governmental, non-profit organisation located in London, focused on the defence, promotion and protection of the right to privacy around the world.
PI and R3D wish to…
Content Type: Press release
Creative Commons Photo Credit: Source
Have the police been unlawfully hacking our phones? Privacy International refers this question to Lord Justice Sir Adrian Fulford, the Investigatory Powers Commissioner
Privacy International has formally written to the UK's Investigatory Powers Commissioner about the police's use of intrusive 'mobile phone extraction' (MPE) technology, raising concerns about whether in some, or indeed in all circumstances, its use constitutes either an interception…
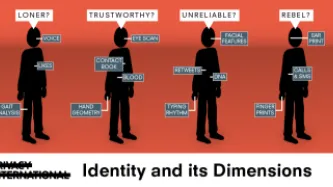
Content Type: Explainer graphic
Content Type: Report
Privacy International welcomes the opportunity to file these comments in advance of the Federal Trade Commission’s public hearings on competition and consumer protection in the 21st century.
Content Type: News & Analysis
Last year Privacy International conducted research into information left on rental cars after they are returned. Every car we rented contained readily apparent personal information about past drivers and other passengers, including information such as their past locations, smart phone identifier, and entered locations, including a school.
Off the back of the research, PI wrote to rental companies and car-share schemes in continental Europe, the UK, and the US to enquire about the companies’…
Content Type: Press release
We found this image here.
The National Police Chiefs’ Council (NPCC) will no longer be able to operate in secret after human rights campaign organisations Liberty and Privacy International demanded it be subject to Freedom of Information laws.
The Government has now informed the organisations that it has started a process to designate the law enforcement policy-making body as a public authority subject to the Freedom of Information Act (FOIA) – meaning it will be open to public scrutiny.…